Introduction to GPRS
GPRS Overview
General Packet Radio Service (GPRS) networks connect to several external networks including those of roaming partners, corporate customers, GPRS Roaming Exchange (GRX) providers, and the public Internet. GPRS network operators face the challenge of protecting their network while providing and controlling access to and from these external networks. Juniper Networks provides solutions to many of the security problems plaguing GPRS network operators.
In the GPRS architecture, the fundamental cause of security threats to an operator’s network is the inherent lack of security in the GPRS tunneling protocol (GTP). GTP is the protocol used between GPRS support nodes (GSNs). GTP is used to establish a GTP tunnel for individual user endpoints (UEs) and between a Service Gateway (S-GW) and a PDN Gateway (P-GW) in 4G. A GTP tunnel is a channel between GSNs through which two hosts exchange data. The SGSN (S-GW ) receives packets from the user endpoints and encapsulates them within a GTP header before forwarding them to the GGSN through the GTP tunnel. When the GGSN receives the packets, it decapsulates them and forwards them to the external host.
Communication between different GPRS networks is not secure because GTP does not provide any authentication, data integrity, or confidentiality protection. Implementing IP Security (IPsec) for connections between roaming partners, setting traffic rate limits, and using stateful inspection can eliminate a majority of the GTP’s security risks. The GTP firewall features in Junos OS address key security issues in mobile operators’ networks.
Juniper Networks security devices mitigate a wide variety of attacks on the following types of GPRS interfaces:
Gn—The Gn interface is the connection between an SGSN (S-GW ) and a GGSN within the same public land mobile network (PLMN).
S5 - The S5 interface is the connection between a S-GW and P-GW within the PLMN in 4G networks.
Gp—The Gp interface is the connection between two PLMNs.
S8 -The S8 interface is the bearer plane connection between home and visited PLMNs in 4G networks.
Gi—The Gi interface is the connection between a GGSN and the Internet or destination networks connected to a PLMN.
SGi - The SGi interface is the connection between a P-GW and the Internet or destination networks connected to a PLMN in 4G networks.
The term interface has different meanings in Junos OS and in GPRS technology. In Junos OS, an interface is a doorway to a security zone that allows traffic to enter and exit the zone. In GPRS, an interface is a connection, or a reference point, between two components of a GPRS infrastructure, for example, an SGSN (S-GW) and a GGSN (P-GW).
Starting in Junos OS Release 18.4R1, GPRS tunneling protocol (GTP) traffic security inspection is supported on IPv6 addresses along with existing IPv4 support. With this enhancement, a GTP tunnel using either IPv4 and IPv6 addresses is established for individual user endpoints (UEs) between a Serving GPRS Support Node (SGSN) in 3G or a Service Gateway (S-GW) and a Gateway GPRS Support Node (GGSN) in 3G or a PDN Gateway (P-GW) in 4G. With IPv6 support, GTP Application Layer Gateway (ALG) inspects or ignores IPv6 GTP sessions according to the policy configurations. All ALG functions on IPv4 are supported on IPv6. You can Inspect GTP signaling or data messages transmitted over IPv6 based on the policy configurations.
This topic contains the following sections:
Gp and Gn Interfaces
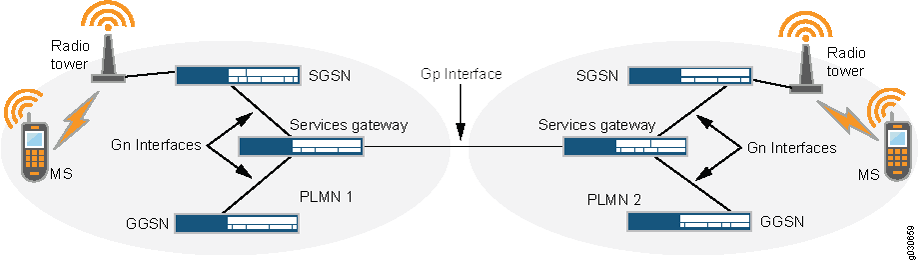
You implement a security device on the Gn interface to protect core network assets such as the SGSN (S-GW) and GGSN (P-GW). To secure GTP tunnels on the Gn interface, you place the security device between SGSNs (S-GW) and GGSNs (P-GW) within a common PLMN.
When you implement a security device to the Gp interface, you protect a PLMN from another PLMN. To secure GTP tunnels on the Gp interface, you place the SGSNs (S-GW) and GGSNs(P-GW) of a PLMN behind the security device so that all traffic, incoming and outgoing, goes through the firewall.
Figure 1 illustrates the placement of Juniper Networks SRX Series devices used to protect PLMNs on the Gp and Gn interfaces.
Gi Interface
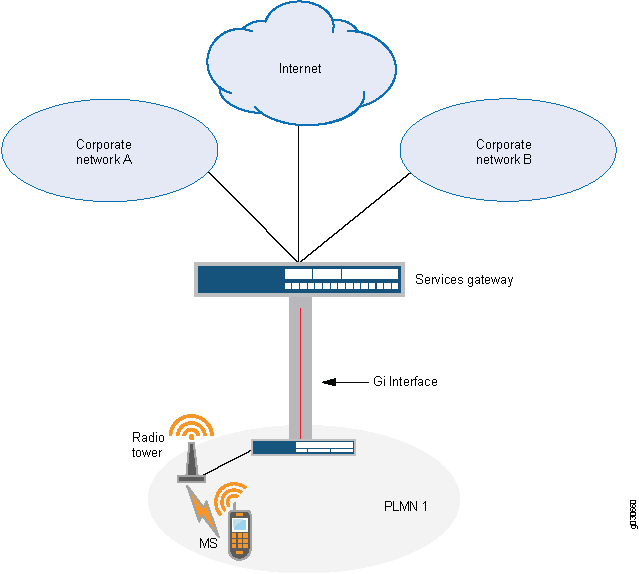
When you implement a security device on the Gi interface, you can simultaneously control traffic for multiple networks, protect a PLMN against the Internet and external networks, and protect mobile users from the Internet and other networks. Junos OS provides a great number of virtual routers, making it possible for you to use one virtual router per customer network and thereby allow the separation of traffic for each customer network.
The security device can securely forward packets to the Internet or destination networks using the Layer 2 Tunneling Protocol (L2TP) for IPsec virtual private network (VPN) tunnels.
SRX Series devices do not support full L2TP.
Figure 2 illustrates the implementation of a security device to protect a PLMN on the Gi interface.
Operational Modes
Junos OS supports two interface operational modes with GTP: transparent mode and route mode. If you want the security device to participate in the routing infrastructure of your network, you can run it in route mode. This requires a certain amount of network redesign. Alternatively, you can implement the security device into your existing network in transparent mode without having to reconfigure the entire network. In transparent mode, the security device functions as a Layer 2 switch or bridge, and the IP addresses of interfaces are set at 0.0.0.0, making the presence of the security device invisible, or transparent, to users.
Junos OS supports NAT on interfaces and policies that do not have GTP inspection enabled.
Currently in Junos OS, route mode supports active/passive, and active/active chassis cluster. Transparent mode supports active/passive only.
GTP In-Service Software Upgrade
GTP supports unified in-service software upgrade (ISSU) between two SRX Series devices running two different Junos OS releases. Unified ISSU is performed on a chassis cluster, enabling a software upgrade between two different Junos OS releases with no disruption on the control plane and with minimal disruption of traffic.
On SRX5400, SRX5600, and SRX5800 devices, ISSU is supported from Junos OS Release 12.1X45 through Junos OS Release 12.1X46 and from Junos OS Release 12.1X46 through Junos OS Release 12.3X48-D10. ISSU is not supported from Junos OS Release 12.1X45 through Junos OS Release 12.3X48-D10.
Understanding GTP Support for Central Point Architecture
User equipment (for example, a cellphone) attaches to a Serving GPRS Support Node (SGSN) or S-GW (Serving Gateway) for General Packet Radio Service (GPRS) data service. The SGSN (S-GW) connects to a gateway GPRS support node to access the Internet. The user equipment requests the SGSN to create one or multiple GPRS tunneling protocol (GTP) tunnels to the GGSN or P-GW (PDN Gateway) for Internet access. In situations where the user equipment moves to a new location, the user equipment has to attach to another SGSN. The new SGSN notifies the GGSN to update the new SGSN information in the original tunnel.
The GTP Application Layer Gateway (ALG) maintains the status of the tunnels and permits tunnel update request packets only for the existing tunnels. When the user equipment moves to a new location and attaches to another SGSN, the new SGSN information must be updated in the original tunnel. Because few GTP-C messages are bidirectional, and messages can be sent either sent by the SGSN or the GGSN, correct session distribution is not guaranteed. That is, the GTP ALG stops creating a session if the first packet originates from an unknown direction. In this case, the first packet and the other pending packets are dropped.
To prevent GTP-C packets from being dropped, a new flow session is created and the GTP-C traffic is allowed to pass even if the GGSN or SGSN direction is not determined. Later, the GGSN IP is determined using the correct SPU to create the flow session; otherwise, the session is migrated to the designated SPU.
Starting from Junos OS Release 18.4R1, the GTP-C tunnel is enhanced to support the tunnel-based
session distribution to speed up the tunnel set up process and load balance the sessions
between the SPUs. The tunnel-based session guarantees that the GTP-C tunnel messages
reach the control tunnel and finish the stateful inspection. If the GTP-C distribution
is enabled, the GTP-C tunnels and the GTP-C tunnel sessions are distributed by the SGSN
tunnel endpoint identifier (TEID) of the tunnel. Use the set security
forwarding-process application-services enable-gtpu-distribution command to
enable the tunnel-based session distribution where the GTP-C traffic of different
tunnels are spread across different SPUs.
This command is
mandatory. If it's missing from the configuration, the GTP ALG will stop working and
will not inspect GTP packets.
Starting in Junos OS Release 15.1X49-D40 and Junos OS Release 17.3R1, the central point architecture is enhanced. Enhancements are as follows:
Prevent GTP-C packet drop issues during the SGSN handover.
Support the GTP-C message rate-limiting to protect the GGSN from flooding of GTP-C messages.
Distribute GTP-C and GTP-U traffic handled by a GGSN and SGSN pair on all SPUs by switching to tunnel-based session distribution in which the GTP-C and GTP-U traffic of different tunnels is spread across different SPUs. Use the
enable-gtpu-distributioncommand to enable GTP-C or GTP-U session distribution.
GTP Tunnel Management
GTP is used to establish a GTP tunnel for individual user endpoints (UEs) and between a Serving GPRS Support Node (SGSN) and a Gateway GPRS Support Node (GGSN). A GTP tunnel is a channel between GSNs through which two hosts exchange data. The SGSN receives packets from the user endpoints (UEs) and encapsulates them within a GTP header before forwarding them to the GGSN through the GTP tunnel. When the GGSN receives the packets, it decapsulates them and forwards them to the external host.
Tunnel Object: The Client endpoints contain information for downstream GSN (SGSN), the Server endpoints hold information for upstream GSN (GGSN). Each tunnel endpoint reserves the fields one for IPv4 address and one for IPv6 address. The tunnel endpoint saves the addresses learned in the tunnel creation or update messages.
Redirect Entry: Redirect entries (also called redirect tunnels) are installed to help finding the anchor SPU. Redirect endpoints are created by means of the creation of normal GTP tunnels. A redirect entry is mapped to one tunnel endpoint and it copies IP address(es), TEID value, and the anchor SPU ID from the tunnel. With IPv6 tunnel support, redirect entry is expanded like tunnel object.
GSN
The gateway GPRS support node (GGSN) or P-GW (PDN Gateway) converts the incoming data traffic coming from the mobile users through the Service gateway GPRS support node (SGSN) and forwards it to the relevant network, and vice versa. The GGSN and the SGSN together form the GPRS support nodes (GSN).
GSN Object: The GTP ALG maintains a GSN table. Each GSN node in a GSN table will record one GSN IP address, (IPv4 or IPv6), GSN restart counter, and GSN-based rate-limiting counter, and so on. If a GSN node has both IPv4 and IPv6 address, The GTP ALG will generate two GSN entries, one for IPv4 address and the other for IPv6 address and the two GSN entries in the same GSN node counts the rate-limit signaling messages independently, and ages out separately.
GSN Reboot: If a GSN reboots, the restart counter changes and the related tunnels will get deleted. For example, if a GSN node is enabled with two IP addresses on tunnels. then the GSN restart is found by only one IP address (IPv4 or IPv6). The tunnels with both IP addresses are removed, and vice versa.
Path Object Management
A path object contains two GSN address and it supports both IPv4 and IPv6 addresses. A path object records the information between the GSN addresses such as message counter, the last time, and so on. For a GSN that has both IPv4 and IPv6 address, the two addresses have their separated paths. Each path performs its own rate-limitation, and ages out separately.
