Example: Configuring IPv6 Support for FlowTapLite on an M120 Router With Enhanced III FPCs
This example describes how to configure IPv6
support for FlowTapLite on an M120 router with Enhanced III FPCs.
The configuration of FlowTapLite is similar on an M320 router and
an MX Series router with Enhanced III FPCs. However, because the MX
Series routers do not support Tunnel Services PICs, you configure
a DPC and the corresponding Packet Forwarding Engine to use tunneling
services at the [edit chassis] hierarchy level.
With Junos OS Release 10.1, the FlowTapLite service supports lawful interception of IPv6 packets; previously only interception of IPv4 packets was supported. The intercepted packets are sent to a content destination, while the flow of original packets to the actual destination is unaffected.
A mediation device installs dynamic filters on the router (or server) by sending DTCP requests. These filters include the quintuple information (source address, destination address, source port, destination port, and protocol) about the intercepted flows and the details (IP addresses and port information) of the content destination.
Below is an example of such a filter:
ADD DTCP/0.8 Csource-ID: ftap Cdest-ID: cd1 Source-Address: 2001:db8:abcd:ef12:3456:78ab:abc8:1235/112 Dest-Address: 2001:db8:affe::1:1 Source-Port: 1234 Dest-Port: 2345 Protocol: * Priority: 2 X-JTap-Input-Interface: ge-2/0/1 X-JTap-Cdest-Dest-Address: 192.0.2.5 X-JTap-Cdest-Dest-Port: 2300 X-JTap-Cdest-Source-Address: 198.51.100.9 X-JTap-Cdest-Source-Port: 65535 X-JTap-Cdest-TTL: 255 X-JTap-IP-Version: ipv6 Flags: STATIC
Following are descriptions of the parameters in the dynamic filter:
Csource-ID—The username configured in the router at the [edit system login user]hierarchy level.Cdest-ID—The content destination identifier.Source-Address,Dest-AddressSource-Port,Dest-Port,Protocol—Parameters that determine which packet flows need to be intercepted.X-JTap-Input-Interface—The interface through which the actual flows are coming into the router. Depending on the type of filters installed, the value in this field can include the following:X-JTap-Output-Interfaceto install output interface filters;X-JTap-VRF-NAMEto install VRF filters; and to install global filters, no parameters are specified.X-JTap-Cdest-Dest—All parameters that start with this string specify different parameters associated with the content destination.X-JTap-IP-Version–Differentiates between IPv6 and IPv4 filters.
From the Packet Forwarding Engine console, you can verify that the filters are installed and working correctly.
Requirements
This example uses the following hardware and software components:
Junos OS Release 10.1 or later
M120 router with a tunnel (
vt) interface
Before you configure IPv6 FlowTapLite on your router, be sure you have:
A tunnel PIC that is up
A connection from the router to the mediation device and the content destination
Traffic flow to and from the router
Overview and Topology
Figure 1 shows the FlowTapLite configuration for one M120 router to lawfully intercept packets.
Topology
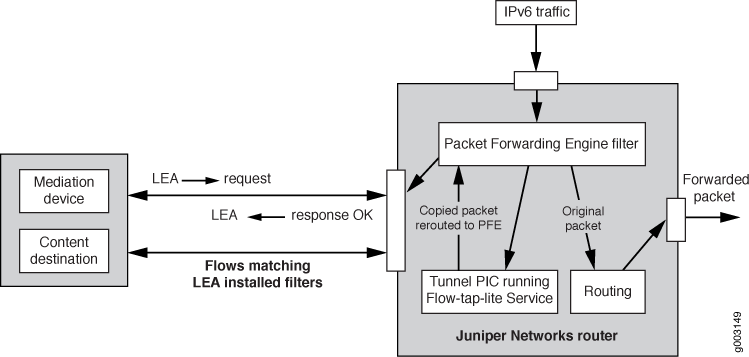
In this example, the IPv6 packets enter the Packet Forwarding Engine and, depending on the filters installed, a new flow is created for the intercepted packets while the original packets are forwarded normally. The new flow is rerouted through the tunnel PIC back to the Packet Forwarding Engine for a route lookup, and then on to the content destination.
Configuration
- CLI Quick Configuration
- Configuring User Credentials
- Configuring the Tunnel Interface for FlowTapLite
- Configuring the Logical Tunnel Interface
- Configuring FlowTapLite
- Results
CLI Quick Configuration
To quickly configure IPv6 FlowTapLite, copy the following commands and paste them into the CLI:
set system login class flowtap permissions flow-tap-operation set system login user ftap uid 2000 set system login user ftap class flowtap set system login user ftap authentication encrypted-password "$ABC123" set system services flow-tap-dtcp ssh set interfaces vt-4/0/0 unit 0 family inet set interfaces vt-4/0/0 unit 0 family inet6 set services flow-tap tunnel-interface vt-4/0/0.0
Configuring User Credentials
Step-by-Step Procedure
The username and password configured here are used by the mediation device when connecting and sending out DTCP requests.
Define a login class called
flowtap:[edit system] user@router# set login class flowtap permissions flow-tap-operation
For the meditation device, configure a user called
ftapwith a unique identifier (UID):[edit system] user@router# set login user ftap uid 2000
Apply the
flowtapclass to theftapuser:[edit system] user@router# set login user ftap class flowtap
-
Configure the encrypted password used by the mediation device:
[edit system] user@router# set login user ftap authentication encrypted-password $ABC123
Commit the configuration:
[edit system] user@router# commit
Configuring the Tunnel Interface for FlowTapLite
Step-by-Step Procedure
You can add an extra level of security to DTCP transactions between the mediation device and the router by enabling DTCP sessions on top of the SSH layer.
Configure SSH from the
[edit system]hierarchy level:[edit system] user@router# set services flow-tap-dtcp ssh
Commit the configuration:
[edit system] user@router# commit
Configuring the Logical Tunnel Interface
Step-by-Step Procedure
Configure the logical interface and assign it to the dynamic flow control process (dfcd) at the
[edit interfaces]hierarchy level:[edit interfaces] user@router# set vt-4/0/0 unit 0 family inet
Include the mandatory
inet6statement:[edit interfaces] user@router# set vt-4/0/0 unit 0 family inet6
Commit the configuration:
[edit interfaces] user@router# commit
Configuring FlowTapLite
Step-by-Step Procedure
Include the
flow-tapstatement and the tunnel interface at the[edit services]hierarchy level:[edit services] user@router# set flow-tap tunnel-interface vt-4/0/0.0
Commit the configuration:
[edit services] user@router# commit
Results
Check the results of the configuration:
[edit]
user@router# show
system {
[...Output Truncated...]
login {
class flowtap {
permissions flow-tap-operation;
}
user ftap {
uid 2000;
class flowtap;
authentication {
encrypted-password "$ABC123"; ## SECRET-DATA
}
}
}
services {
telnet;
flow-tap-dtcp {
ssh;
}
}
}
interfaces {
vt-4/0/0 {
unit 0 {
family inet;
family inet6;
}
}
}
[...Output Truncated...]
services {
flow-tap {
tunnel-interface vt-4/0/0.0;
}
}Verification
To confirm that the configuration is working properly, perform the following tasks:
- Verifying That the Router Received the Filter Request
- Checking That Filters Are Installed and Working on the Router
- Sending a List Request
Verifying That the Router Received the Filter Request
Purpose
After the mediation device sends the filters to the router, the mediation device must receive a message from the router confirming that the router has received the filter request.
Action
Check that the mediation device has received a message similar to the one below:
DTCP/0.8 200 OK SEQ: 1 CRITERIA-ID: 1 TIMESTAMP: 2009-09-29 06:12:05.725 AUTHENTICATION-INFO: 55f9dc3debd3c7356951410f165f2a9cc5606063
Meaning
The message above is an example of a successfully received filter request.
Checking That Filters Are Installed and Working on the Router
Purpose
Action
Use the show filter and the show filter
index commands to check that filters are installed:
user@router# show filter
Program Filters:
---------------
Index Dir Cnt Text Bss Name
-------- ------ ------ ------ ------ --------
1 104 0 20 20 __default_bpdu_filter__
17000 52 0 4 4 __default_arp_policer__
57007 104 144 16 16 __flowtap_inet__
65280 52 0 4 4 __auto_policer_template__
65281 104 0 16 16 __auto_policer_template_1__
65282 156 0 32 32 __auto_policer_template_2__
65283 208 0 48 48 __auto_policer_template_3__
65284 260 0 64 64 __auto_policer_template_4__
65285 312 0 80 80 __auto_policer_template_5__
65286 364 0 96 96 __auto_policer_template_6__
65287 416 0 112 112 __auto_policer_template_7__
65288 468 0 128 128 __auto_policer_template_8__
37748736 156 144 80 80 __ftaplite_filter__ifl__70__out__ipv6_
37748737 156 144 80 80 __ftaplite_filter__vrf__4__in__ipv6_
37748738 156 144 80 80 __ftaplite_filter__ifl__71__in__ipv6_
37748739 156 144 80 80 __ftaplite_filter__vrf__0__in__ipv6_
user@router# show filter index 37748738 counters
Filter Counters/Policers:
Index Packets Bytes Name
-------- -------------------- -------------------- --------
37748738 8851815 601923420 __ftaplite_term_ftap_3___counter
Meaning
The last four filters in the output for the show
filter command above are the filters installed on the Packet
Forwarding Engine. The show filter index command shows
a non-zero packet count, indicating that the packets are hitting the
filter.
Sending a List Request
Purpose
To verify that the correct filters are installed in the Packet Forwarding Engine.
Action
Use client software to send a list request to the Packet
Forwarding Engine. In your list request, you can include the following
three parameters individually or together: CSource-Id, CDest-ID, and Criteria-ID. With all requests, you must include the CSource-Id. Below is an example of a list request using the CSource-Id:
LIST DTCP/0.8 Csource-ID: ftap1 Flags: Both
Below is an example of a response:
DTCP/0.8 200 OK SEQ: 51 TIMESTAMP: 2009-10-04 07:56:43.003 CRITERIA-ID: 1 CSOURCE-ID: ftap1 CDEST-ID: cd1 CSOURCE-ADDRESS: 10.209.152.15 FLAGS: Static AVERAGE-BANDWIDTH: 0 MATCHING-PACKETS: 0 MATCHING-BYTES: 0 NUM-REFRESH: 0 LAST-REFRESH: 2009-10-04 07:54:30.870 X-JTAP-INPUT-INTERFACE: ge-2/1/1.0,ge-2/1/1.1,ge-2/1/1.2 SOURCE-ADDRESS: 203.0.113.1 DEST-ADDRESS: 192.168.0.1/32 SOURCE-PORT: 1000 DEST-PORT: 2000 PROTOCOL: 17 X-JTAP-CDEST-DEST-ADDRESS: 192.168.99.81 X-JTAP-CDEST-DEST-PORT: 8001 X-JTAP-CDEST-SOURCE-ADDRESS: 192.168.208.9 X-JTAP-CDEST-SOURCE-PORT: 34675 X-JTAP-CDEST-TTL: 64 CRITERIA-NUM: 1 CRITERIA-COUNT: 1 AUTHENTICATION-INFO: 0f49ff600a3d8d7d312c5031f74cc17540bc9200
You can also delete the request. Below is an example of a delete request:
DELETE DTCP/0.8 Csource-ID: ftap CDest-ID: cd1 Flags: STATIC
