Unified Access Policy
Unified access policy extends GBP support to Mist access points (APs).
Starting in Junos OS Release 25.4R1, we support unified access policy for wired and wireless clients on the EX4100, EX4400, EX4650, and QFX5120 switches listed in Supported Platforms.
Unified access policy enables supported switches to learn GBP tags from Mist APs, allowing both wired and wireless clients to participate in GBP microsegmentation.
GBP Messages
When you enable unified access policy on a supported switch, the switch learns GBP tag assignments from attached Mist APs through proprietary GBP messages.
Table 1 shows the two types of GBP messages:
| GBP Message Type | Description |
|---|---|
| GBP update |
A GBP update message contains the mapping between a MAC address and a GBP tag. This can be a solicited or unsolicited message from the sender to convey a tag assignment to the receiver. This can be a unicast or multicast message. |
| GBP lookup |
A GBP lookup message is a request by the sender to obtain the GBP tag assignment from the receiver for the MAC address specified within the message. This is a unicast message. |
|
Note: GBP update messages contain MAC-based
GBP tag assignments only and GBP lookup messages request
MAC-based GBP tag assignments only.
|
|
Figure 1 shows the format of the GBP messages. The messages are signed with a key to detect tampering.
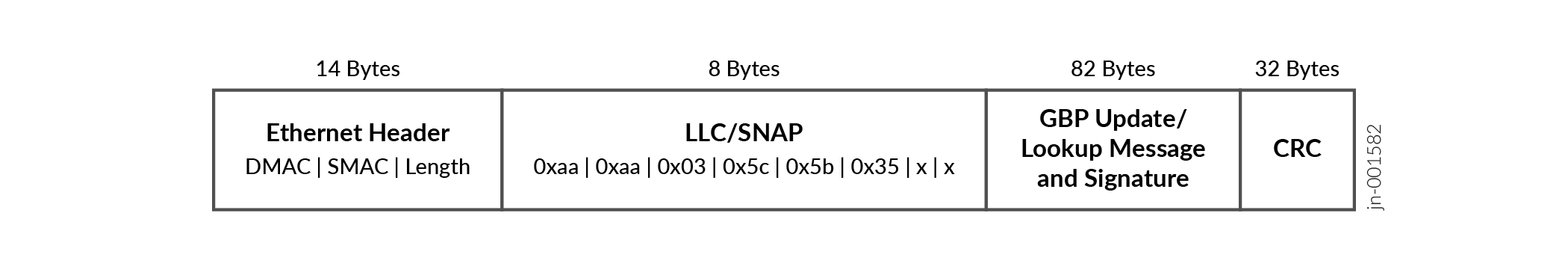
The following sections describe how these messages are used.
UAP Access Links
A UAP access link refers to the link that connects a UAP-enabled access switch directly or indirectly to a Mist AP. The Mist AP conveys GBP tag assignments across this link to the access switch through a GBP message exchange.
Specifically, the Mist AP and the access switch behave as follows:
-
If a wireless client is assigned a GBP tag during authentication, the Mist AP sends a multicast GBP update message containing the MAC-based GBP tag assignment to the upstream access switch. The destination multicast MAC address in the message is set to
5d:5b:35:ff:ff:01and the source MAC address is set to the MAC address of the Mist AP.When the access switch receives this GBP update message, the switch updates its MAC address tables and internal data structures with the specified MAC-based tag assignment.
-
If the GBP update message is dropped or if the access switch reboots, the tag assignment is lost. In this situation, if the access switch receives a client data frame with a source MAC address that has no GBP tag assigned, the access switch sends a GBP lookup message to the Mist AP asking for the missing tag assignment. The destination MAC address in the GBP lookup message is set to the MAC address of the Mist AP. The source MAC address is set to a derivation of the chassis MAC address of the access switch.
When the Mist AP receives this GBP lookup message, the Mist AP looks up the specified MAC address to obtain the GBP tag. If the GBP tag exists, the Mist AP responds to the GBP lookup message with a unicast GBP update message containing the tag assignment. The destination unicast MAC address in the response is set to the MAC address of the access switch (a derivation of the chassis MAC address). The source MAC address is set to the MAC address of the Mist AP.
Figure 2 shows unified access policy in an EVPN-VXLAN network connecting wired and wireless clients. GBP tags for wired clients are assigned through GBP filters or RADIUS authentication as is usual. GBP tags for wireless clients are assigned through RADIUS authentication and the tag assignments are communicated to upstream switches in GBP update messages. The switch receiving the GBP update messages configures its MAC address tables and internal data structures with the GBP tag assignments as if the GBP tags were assigned through the CLI or learned locally. Regular GBP tag processing then occurs. There is no restriction or limitation in functionality due to the tag being assigned through a GBP message instead of the CLI.
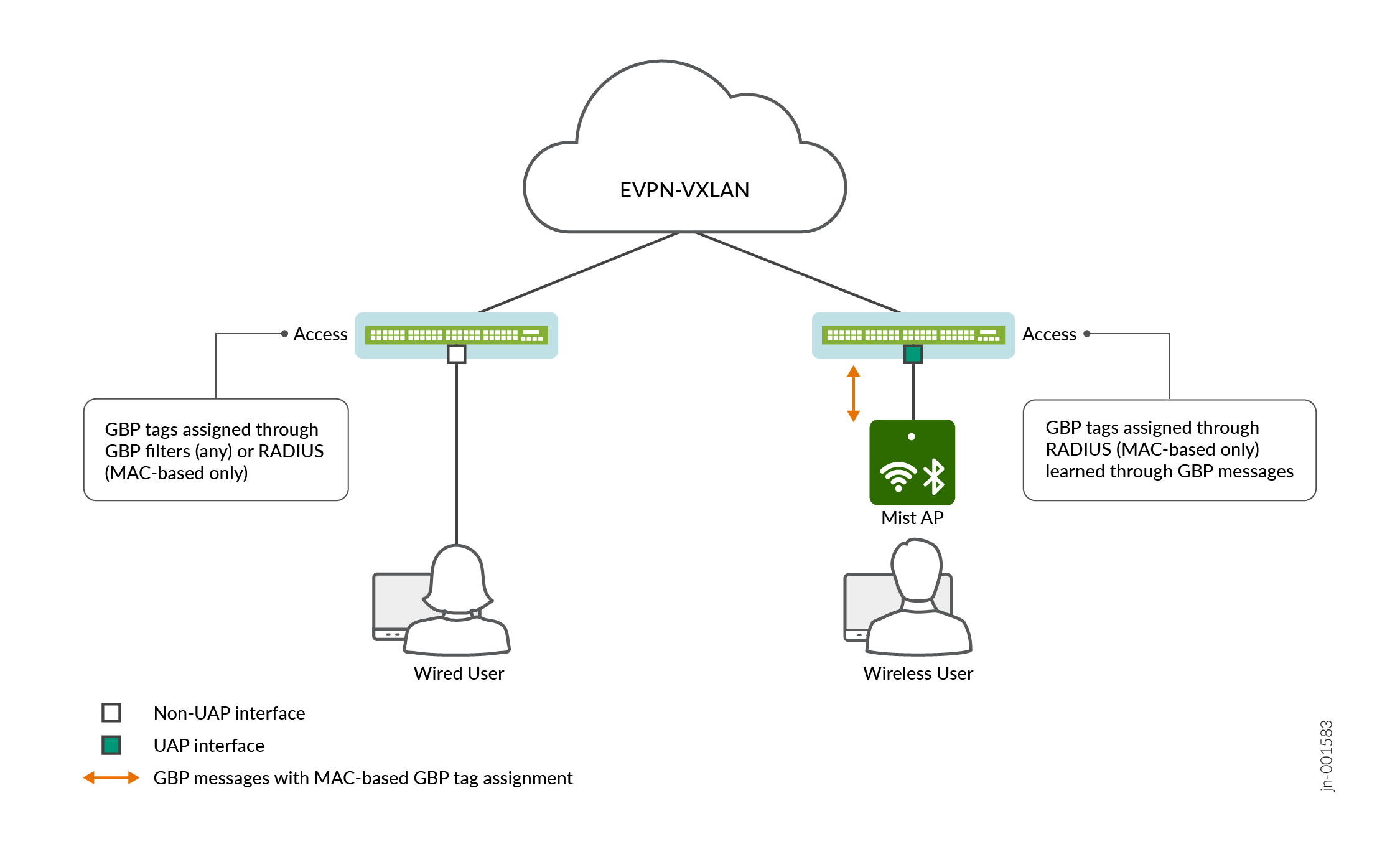
Although the above example shows UAP in an EVPN-VXLAN network, you can configure UAP in a pure L2 network as well. The UAP capability works independently from the underlying infrastructure.
UAP Inter-Switch Links
While a UAP access link connects an access switch to a Mist AP, a UAP inter-switch link connects UAP-enabled switches with each other in a pure layer 2 network. When you configure an interface for a UAP inter-switch link, you're allowing GBP messages to be exchanged on that interface. In this way, MAC-based GBP tags are propagated across the network to all UAP-enabled switches.
Specifically, the UAP-enabled switches behave as follows:
-
Wireless - If an access switch receives a GBP update message from a Mist AP, the access switch processes the message as described in UAP Access Links and passes this multicast message out all inter-switch link interfaces. This message then propagates across all UAP-enabled switches where this tag assignment is learned.
-
Wired - If an access switch learns of a GBP tag assignment for a wired user (for example, through CLI configuration or RADIUS authentication), it creates a unicast GBP update message containing that tag assignment and sends it to its UAP-enabled neighbors across the inter-switch links.
Passing GBP update messages across the network in this manner allows access switches to enforce policy on both the source and destination GBP tags at the ingress. This feature, however, is limited to UAP-enabled switches in a pure L2 network.
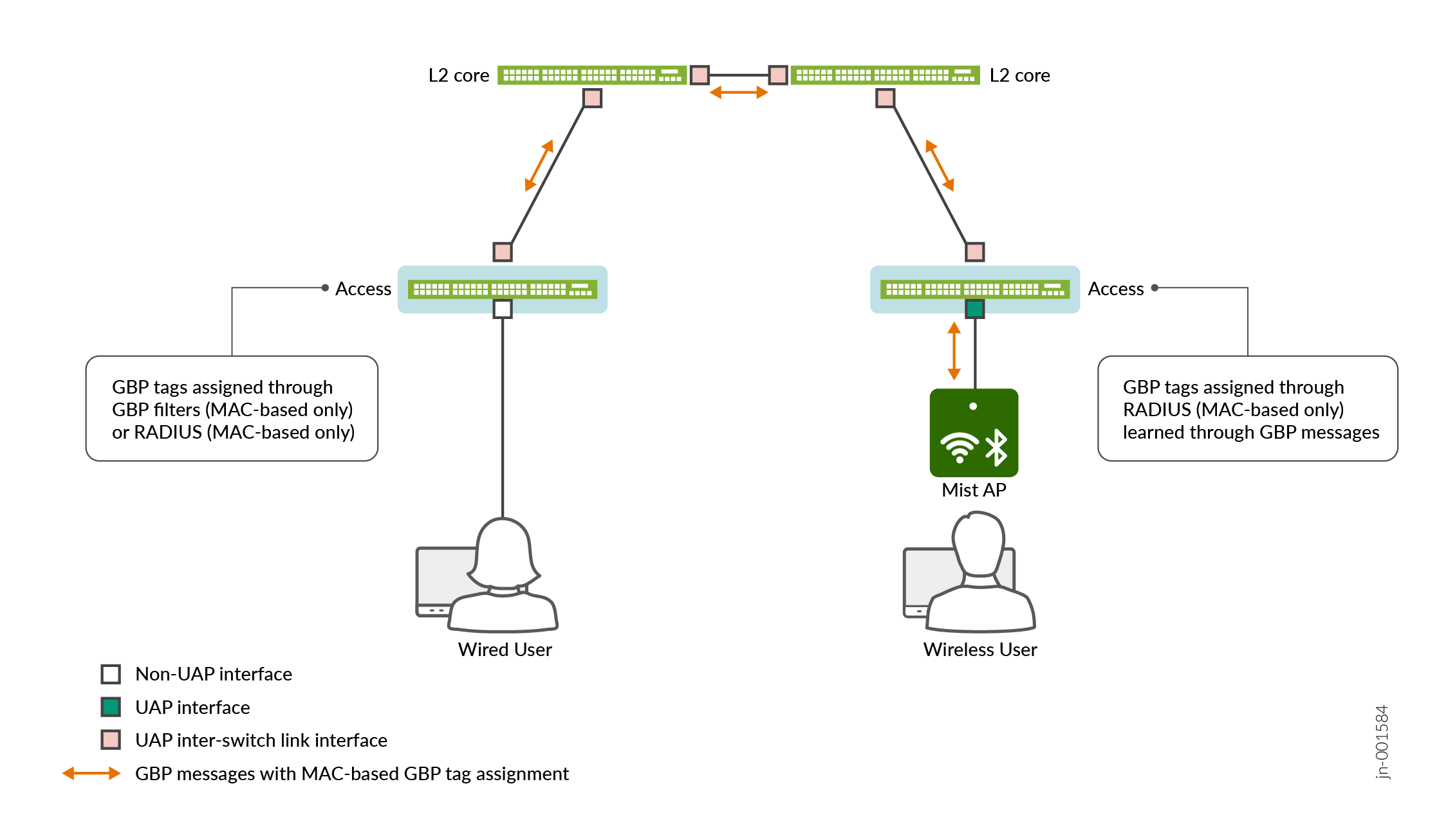
Figure 3 shows how GBP messages propagate over inter-switch links across a pure layer 2 network. GBP tags from both wired and wireless clients are propagated in this manner.
UAP Configuration
Using the GBP Pure L2 Profile
In some deployments, you may want to perform policy enforcement on access switches that are not L3 gateways. Perhaps you want to keep your access switches at layer 2 for simplicity and move the routing and gateway responsibility to a WAN router. This means that the access switches do not perform IP route lookups and cannot participate in L3 segmentation.
In this situation, if you enable the gbp-pure-l2-profile, we
allow you to add a destination IP address/subnet match to your policy. This
gives you the ability to support both L2 and L3 segmentation even on a pure L2
access switch.
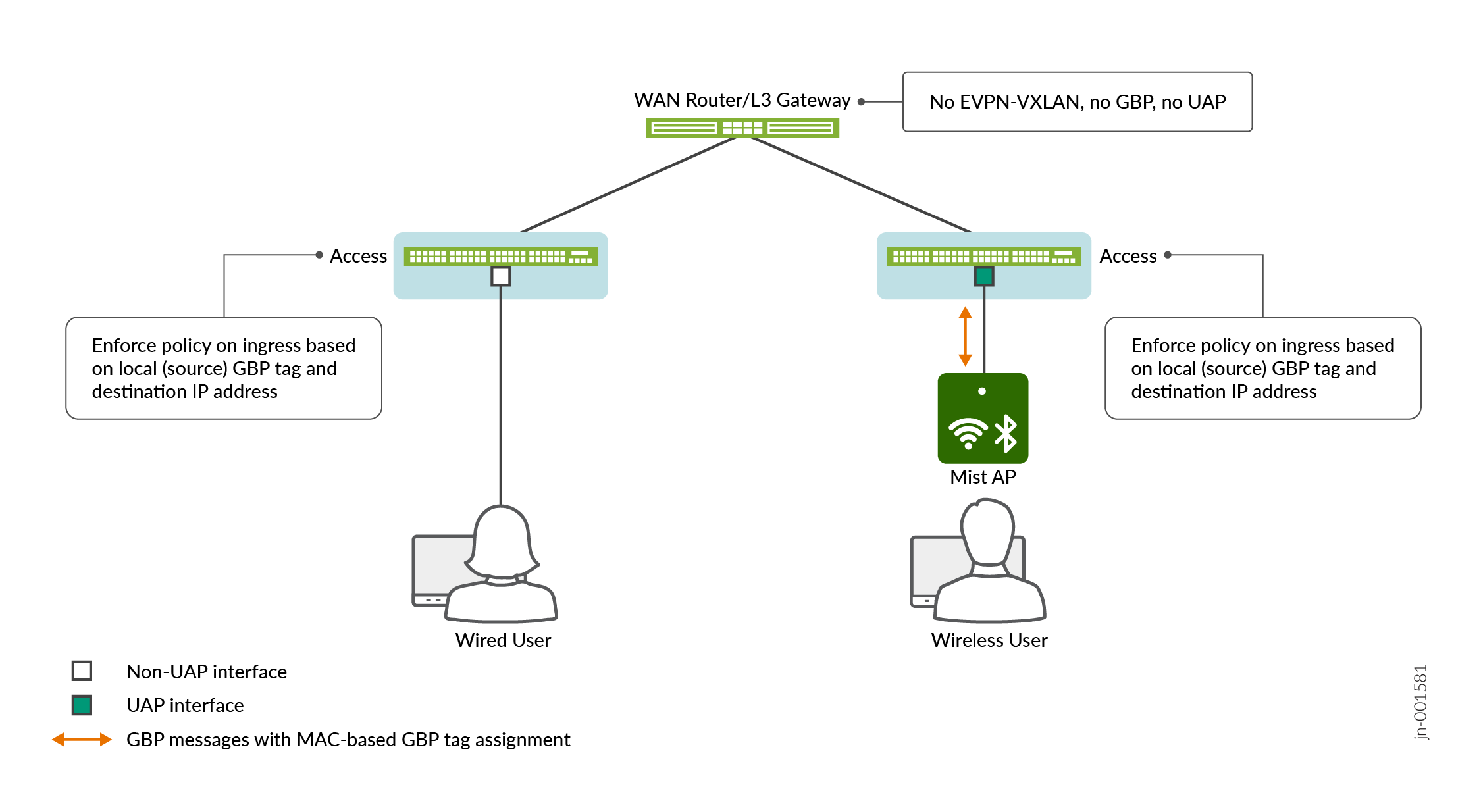
Figure 4 shows GBP-enabled layer 2 access
switches connected to a WAN router. The WAN router does not support EVPN-VXLAN
and does not support GBP. However, even in this scenario, the access switch can
still participate in L2 and L3 segmentation if you enable the
gbp-pure-l2-profile and enforce policy on the combination
of a local (source) GBP tag and a destination IP address/subnet.
This feature allows you to incorporate third-party WAN and core/distribution routers into your network and continue to support GBP microsegmentation. This is ideal for smaller sites where policy enforcement at the access layer simplifies design and reduces dependency on core infrastructure.
Table 2 and Table 3 show the supported GBP tag
assignment and policy enforcement features with the
gbp-pure-l2-profile. A pure layer 2 device only supports a
subset of the tagging and enforcement features.
| Tag Assignment Based On ... | Support |
|---|---|
|
MAC address only |
Yes |
|
Interface only |
Yes |
|
VLAN only |
Yes1 |
|
Interface and VLAN |
Yes1 |
|
IP address |
No |
|
IEEE 802.1X |
Yes |
| 1Not supported on EX4100 switches. | |
| Enforcement | Support |
|---|---|
|
Egress |
Yes, with destination GBP tag |
|
Ingress |
Yes, with source GBP tag and destination IP address |
|
L4 fields |
Yes |
|
Ingress with Tag Propagation |
No |
|
Explicit Default Discard |
No |
|
MAC/IP Inter-tagging |
No |
|
Filter-Based Forwarding |
No |
Below is an example of configuring GBP with the
gbp-pure-l2-profile.
set routing-options router-id 10.1.2.3 set interfaces lo0 unit 0 family inet address 10.1.2.3/32 set protocols evpn encapsulation vxlan set protocols evpn extended-vni-list all set switch-options vtep-source-interface lo0.0 set switch-options route-distinguisher 10.1.2.3:100 set switch-options vrf-target target:1:100
set vlans default vxlan vni 100001 set vlans default no-arp-suppression set vlans vlan1099 vxlan vni 101099 set vlans vlan1099 no-arp-suppression etc.
