Example: Using GBP to Segment Traffic
This basic example shows how you can use GBP filters and policies to segment traffic.
This example shows how to configure a pair of switches for GBP-based microsegmentation. The switches (Leaf 1 and Leaf 2) control access for the following users and equipment, as shown in Figure 1:
-
2 Engineering Staff (ENG)
-
1 Contractor (CON)
-
2 Security Staff (SS)
-
1 Engineering Server (ES)
-
1 Security Camera (CAM)
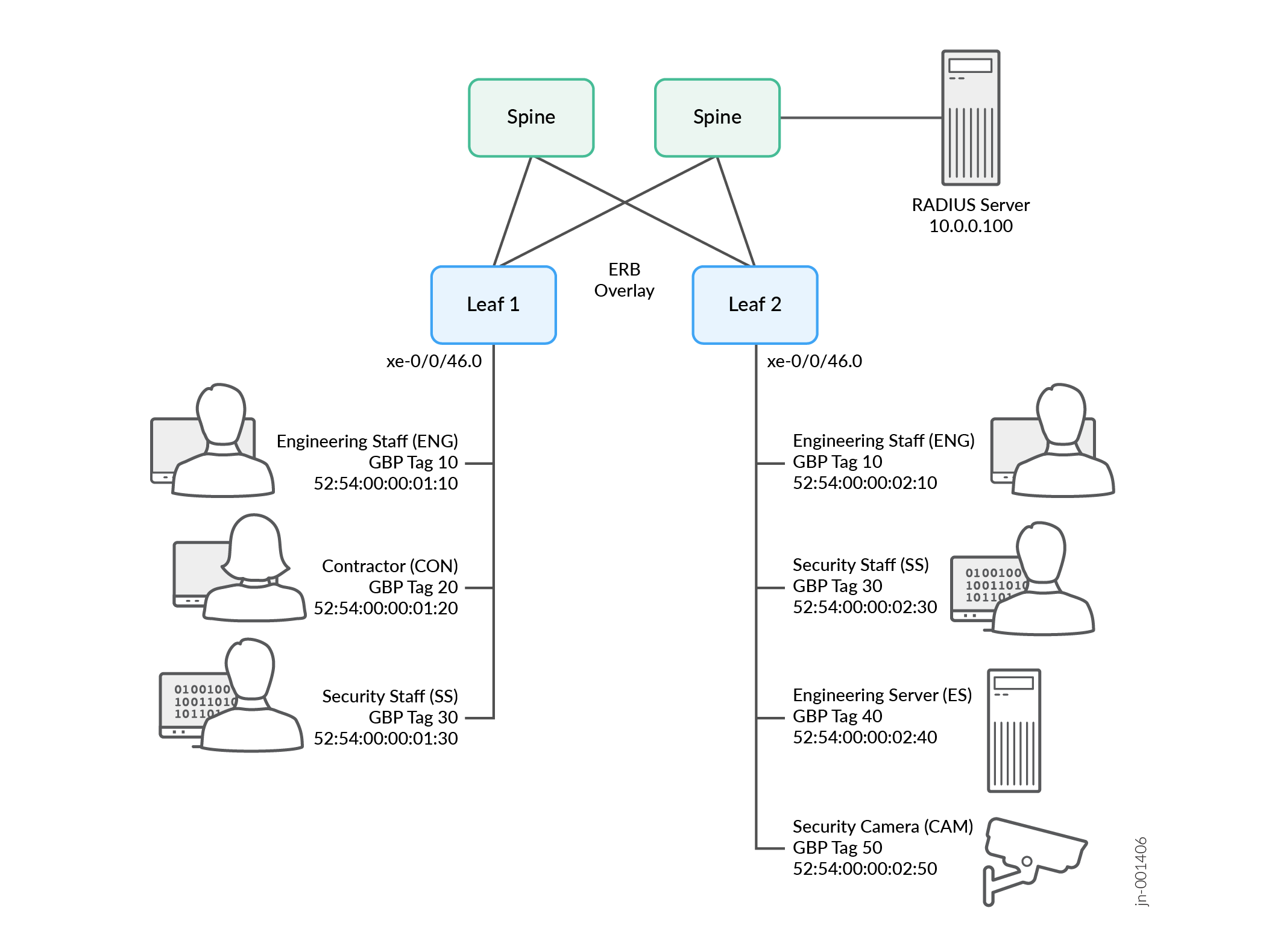
Table 1 shows the GBP tag values that we'll assign. We'll show how to assign these tags using both the CLI and RADIUS.
|
Endpoint |
GBP Tag |
|---|---|
|
Engineering Staff (ENG) |
10 |
|
Contractor (CON) |
20 |
|
Security Staff (SS) |
30 |
|
Engineering Server (ES) |
40 |
|
Security Cam (CAM) |
50 |
Table 2 shows the microsegmentation policies that we'll apply. We use Y to indicate where access is permitted, N to indicate where access is blocked, and - to indicate not applicable (since there is only one contractor, one engineering server, and one security camera).
| ENG (Tag 10) | CON (Tag 20) | SS (Tag 30) | ES (Tag 40) | CAM (Tag 50) | |
|---|---|---|---|---|---|
| ENG (Tag 10) | Y | Y | N | Y | N |
| CON (Tag 20) | Y | - | N | N | N |
| SS (Tag 30) | N | N | Y | N | Y |
| ES (Tag 40) | Y | N | N | - | N |
| CAM (Tag 50) | N | N | Y | N | - |
