Overview
Use group based policies (GBP) to support microsegmentation.
Microsegmentation, in the context of networking, refers to the support of granular network access policy and fine-grained network access controls. It subdivides a network into smaller isolated segments that you control through individual security policies. Microsegmentation augments the perimeter security provided by firewalls and presents a particularly useful technique in containing lateral threats in your network.
Juniper Networks Group Based Policy (GBP) implementation supports microsegmentation for wired and wireless clients by allowing you to conceptually separate clients into groups. You then create different policies to apply to the different groups of clients. Policy enforcement is not tied to traditional networking constructs used in ACLs such as MAC or IP addresses. You can apply the same security policy to users from within the same VLAN or across VLANs, or from within the same switch or across switches, all without reference to network location. Policy enforcement with GBP is truly location agnostic, untethered to where clients reside in the physical network.
GBP enforces policy based on Scalable Group Tags (SGTs), which you assign to individual clients statically through CLI configuration or dynamically through RADIUS authentication. Creating policies based on tags decouples the client from their network location. This means that unlike ACLs and firewall rules, SGTs are location-agnostic and provide natural support for mobility. A GBP policy doesn't change simply because a client has changed to a different network attachment point. This simplifies network security management, allowing seamless connectivity and consistent application of policy no matter where the client is. Moreover, GBP-based microsegmentation is highly scalable because GBP policy is applied to groups instead of to individual clients and their myriad connections.
Although you can enable GBP on different network infrastructure, you'll achieve the most benefit when running on an EVPN-VXLAN network. That's because the GBP tag (shown as the Group Policy ID in Figure 1) is carried inband alongside data in the VXLAN frame. This allows the switch at the remote end to see the GBP tag associated with the user data and apply policy based on this tag. (See I-D.draft-smith-vxlan-group-policy for more information on the VXLAN header structure when using GBP.)
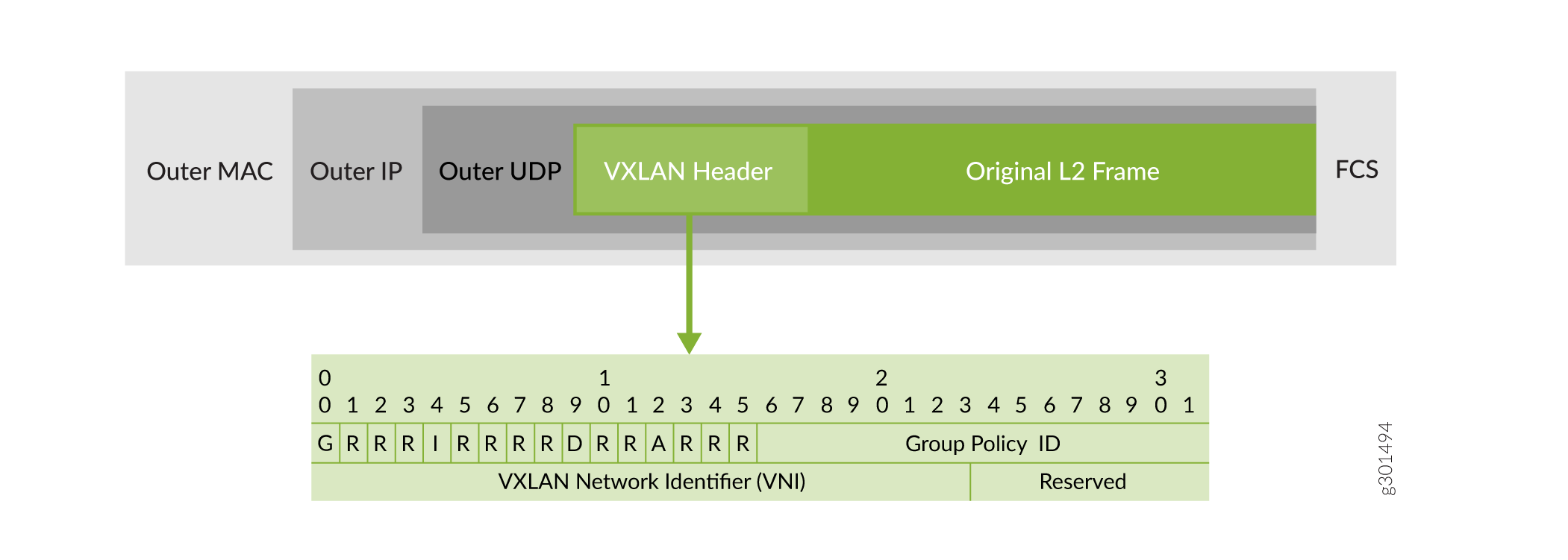
When a GBP-enabled EVPN-VXLAN switch receives a packet from a client, the switch classifies the packet to obtain the GBP tag. Then the switch encapsulates the entire packet in VXLAN and inserts the GBP tag into the VXLAN header prior to forwarding the packet through the appropriate VXLAN tunnel.
When the packet exits the other end of the tunnel, the GBP-enabled switch at the far end extracts the tag and makes a policy decision based on the extracted tag and on the tag associated with the destination. The policy itself is based purely on GBP tags, which are associated with clients and not network location.
In the event that your network is sufficiently small that it doesn't warrant running EVPN-VXLAN, you can still take advantage of GBP capabilities. In this situation, there is no VXLAN tunnel to carry the GBP tag. Therefore you have to enforce policy locally at the ingress. As before, the GBP-enabled switch at the access receives the packet from the client and classifies it to retrieve the assigned tag. The same switch then enforces policy locally based on this tag along with other packet header information.
Whether you run with EVPN-VXLAN or not, there are three distinct aspects to GBP support:
-
Tag assignment configures the mapping between the client and the group.
-
Packet classification classifies the incoming packet in the dataplane to obtain the GBP tags (source tag at ingress, destination tag at egress).
-
Policy enforcement enforces policy based on the GBP tags.
We cover all three aspects in GBP Processing.
