ON THIS PAGE
Example: Configure and Apply a Firewall Filter for a Multifield Classifier
This example shows how to configure a firewall filter to classify traffic using a multifield classifier. The classifier detects packets of interest to CoS as the packets arrive on an interface. Use multifield classifiers when a simple BA classifier is insufficient to classify a packet, when peering routers do not have CoS bits marked, or when the peering router’s marking is untrusted.
Requirements
To verify this procedure, this example uses a traffic generator. The traffic generator can be hardware-based, or it can be software running on a server or host machine.
The functionality in this procedure is widely supported on devices that run Junos. The example shown here was tested and verified on MX Series routers running Junos OS Release 10.4.
Overview
A classifier is a software operation that inspects a packet as it enters the router or switch. The packet header contents are examined, and this examination determines how the packet is treated when the network becomes too busy to handle all of the packets and you want your devices to drop packets intelligently, instead of dropping packets indiscriminately. One common way to detect packets of interest is by source port number. The TCP port numbers 80 and 12345 are used in this example, but many other matching criteria for packet detection are available to multifield classifiers, using firewall filter match conditions. The configuration in this example specifies that TCP packets with source port 80 are classified into the BE-data forwarding class and queue number 0. TCP packets with source port 12345 are classified into the Premium-data forwarding class and queue number 1.
You typically use multifield classifiers at the network edge as packets enter an autonomous system (AS).
In this example, you configure the firewall filter mf-classifier and specify some custom forwarding classes on Device R1. In specifying the custom forwarding classes, you also associate each class with a queue.
The classifier operation is shown in Figure 1.
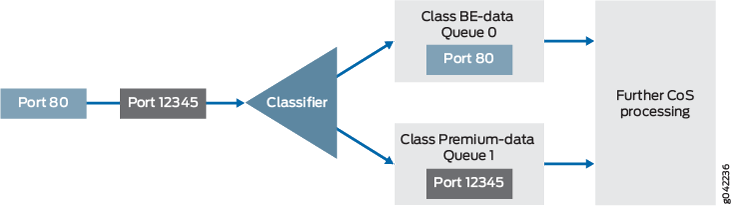
You apply the multifield classifier’s firewall filter as an input filter on each customer-facing or host-facing interface that needs the filter. The incoming interface is ge-1/0/1 on Device R1. The classification and queue assignment is verified on the outgoing interface. The outgoing interface is Device R1’s ge-1/0/9 interface.
Topology
Figure 2 shows the sample network.
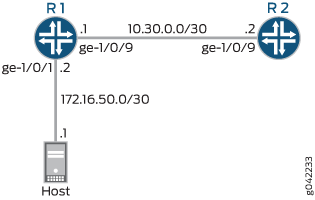
CLI Quick Configuration shows the configuration for all of the Juniper Networks devices in Figure 2.
Step-by-Step Procedure describes the steps on Device R1.
Classifiers are described in more detail in the following Juniper Networks Learning Byte video.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, copy and paste the commands into the CLI at the [edit] hierarchy level, and then enter commit from the configuration mode.
Device R1
set interfaces ge-1/0/1 description to-host set interfaces ge-1/0/1 unit 0 family inet filter input mf-classifier set interfaces ge-1/0/1 unit 0 family inet address 172.16.50.2/30 set interfaces ge-1/0/9 description to-R2 set interfaces ge-1/0/9 unit 0 family inet address 10.30.0.1/30 set class-of-service forwarding-classes class BE-data queue-num 0 set class-of-service forwarding-classes class Premium-data queue-num 1 set class-of-service forwarding-classes class Voice queue-num 2 set class-of-service forwarding-classes class NC queue-num 3 set firewall family inet filter mf-classifier term BE-data from protocol tcp set firewall family inet filter mf-classifier term BE-data from port 80 set firewall family inet filter mf-classifier term BE-data then forwarding-class BE-data set firewall family inet filter mf-classifier term Premium-data from protocol tcp set firewall family inet filter mf-classifier term Premium-data from port 12345 set firewall family inet filter mf-classifier term Premium-data then forwarding-class Premium-data set firewall family inet filter mf-classifier term accept-all-else then accept
Device R2
set interfaces ge-1/0/9 description to-R1 set interfaces ge-1/0/9 unit 0 family inet address 10.30.0.2/30
Step-by-Step Procedure
The following example requires that you navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure Device R1:
-
Configure the device interfaces.
[edit interfaces] user@R1# set ge-1/0/1 description to-host user@R1# set ge-1/0/1 unit 0 family inet address 172.16.50.2/30 user@R1# set ge-1/0/9 description to-R2 user@R1# set ge-1/0/9 unit 0 family inet address 10.30.0.1/30
-
Configure the custom forwarding classes and associated queue numbers.
[edit class-of-service forwarding-classes] user@R1# set BE-data queue-num 0 user@R1# set Premium-data queue-num 1 user@R1# set Voice queue-num 2 user@R1# set NC queue-num 3
-
Configure the firewall filter term that places TCP traffic with a source port of 80 (HTTP traffic) into the BE-data forwarding class, associated with queue 0.
[edit firewall family inet filter mf-classifier] user@R1# set term BE-data from protocol tcp user@R1# set term BE-data from port 80 user@R1# set term BE-data then forwarding-class BE-data
-
Configure the firewall filter term that places TCP traffic with a source port of 12345 into the Premium-data forwarding class, associated with queue 1.
[edit firewall family inet filter mf-classifier] user@R1# set term Premium-data from protocol tcp user@R1# set term Premium-data from port 12345 user@R1# set term Premium-data then forwarding-class Premium-data
-
At the end of your firewall filter, configure a default term that accepts all other traffic.
Otherwise, all traffic that arrives on the interface and is not explicitly accepted by the firewall filter is discarded.
[edit firewall family inet filter mf-classifier] user@R1# set term accept-all-else then accept
-
Apply the firewall filter to the ge-1/0/1 interface as an input filter.
[edit interfaces] user@R1# set ge-1/0/1 unit 0 family inet filter input mf-classifier
Results
From configuration mode, confirm your configuration by entering the show interfaces, show class-of-service, show firewall commands. If the output does not display the intended configuration, repeat the instructions in this example to correct the configuration.
user@R1# show interfaces
ge-1/0/1 {
description to-host;
unit 0 {
family inet {
filter {
input mf-classifier;
}
address 172.16.50.2/30;
}
}
}
ge-1/0/9 {
description to-R2;
unit 0 {
family inet {
address 10.30.0.1/30;
}
}
}
user@R1# show class-of-service
forwarding-classes {
class BE-data queue-num 0;
class Premium-data queue-num 1;
class Voice queue-num 2;
class NC queue-num 3;
}
user@R1# show firewall
family inet {
filter mf-classifier {
term BE-data {
from {
protocol tcp;
port 80;
}
then forwarding-class BE-data;
}
term Premium-data {
from {
protocol tcp;
port 12345;
}
then forwarding-class Premium-data;
}
term accept-all-else {
then accept;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Checking the CoS Settings
Purpose
Confirm that the forwarding classes are configured correctly.
Action
From Device R1, run the show class-of-service forwardng-classes command.
user@R1> show class-of-service forwarding-class Forwarding class ID Queue Restricted queue Fabric priority Policing priority SPU priority BE-data 0 0 0 low normal low Premium-data 1 1 1 low normal low Voice 2 2 2 low normal low NC 3 3 3 low normal low
Meaning
The output shows the configured custom classifier settings.
Sending TCP Traffic into the Network and Monitoring the Queue Placement
Purpose
Make sure that the traffic of interest is sent out the expected queue.
Action
Clear the interface statistics on Device R1’s outgoing interface.
user@R1> clear interfaces statistics ge-1/0/9
Use a traffic generator to send 50 TCP port 80 packets to Device R2 or to some other downstream device.
On Device R1, check the queue counters.
Notice that you check the queue counters on the downstream output interface, not on the incoming interface.
user@R1> show interfaces extensive ge-1/0/9 | find "Queue counters" Queue counters: Queued packets Transmitted packets Dropped packets 0 50 50 0 1 0 57 0 2 0 0 0 3 0 0 0Use a traffic generator to send 50 TCP port 12345 packets to Device R2 or to some other downstream device.
[root@host]# hping 172.16.60.1 -c 50 -s 12345 -k
On Device R1, check the queue counters.
user@R1> show interfaces extensive ge-1/0/9 | find "Queue counters" Queue counters: Queued packets Transmitted packets Dropped packets 0 50 50 0 1 50 57 0 2 0 0 0 3 0 0 0
Meaning
The output shows that the packets are classified correctly. When port 80 is used in the TCP packets, queue 0 is incremented. When port 12345 is used, queue 1 is incremented.
