BGP Error Messages
Understanding Error Handling for BGP Update Messages
A BGP message is considered to be malformed when any one of the message attributes is malformed. When a router participating in a BGP session receives a malformed update message, the entire session is reset by default. This is undesirable because update messages with valid routes are also affected. To avoid this undesirable behavior, the error handling for BGP update messages needs to be modified.
To configure error handling for BGP update messages, configure the
bgp-error-tolerance statement at the [edit protocols
bgp], [edit protocols bgp group
group-name], or [edit protocols bgp group
group-name neighbor address]
hierarchy level.
bgp-error-tolerance { malformed-route-limit number; malformed-update-log-interval seconds; no-malformed-route-limit; }
If an attribute contains attribute flags that conflict with the value of the Attribute Type field, the attribute flags are reset to the correct value and the update message is processed. The value of the Extended Length bit in the attribute flags is unchanged because this value defines whether the attribute length is one or two octets. Hence, the value of the attribute flag affects how the BGP update packet is parsed.
There is no explicit specification for the attribute flag value for the path attributes.
Starting in Junos OS Release 24.2R1, BGP error handling is enabled by default. You can
still configure sub-options such as, malformed-route-limit,
malformed-update-log-interval, and
no-malformed-route-limit under this configuration statement. Note
that If you delete the bgp-error-tolerance statement, the feature still
remains enabled and the sub-options are reset to their default
values.
Malformed update messages are treated on a case by case basis, depending on the values of the attributes contained in the messages. There are three ways of handling malformed BGP update messages, listed in the decreasing order of severity.
Notification message approach—The malformed message error is logged locally, an error code update message is sent to the administration of the peer, and the entire BGP session is reset.
This approach is chosen when:
The BGP update message contains the MP reach attribute or the MP unreach attribute.
The NLRI field or the BGP update message cannot be parsed correctly because of a mismatch between the attribute length and the value of the attribute length field.
Treat-as-withdraw approach—All routes within the malformed update message are treated as hidden routes, unless the
keep nonestatement is configured, in which case the routes are discarded. In the absence of thekeep nonestatement, the number of hidden malformed routes are configured with a limit, which when exceeded discards the routes and prevents any further malformed routes from being hidden. Junos OS removes the newly received malformed routes when the malformed route limit is reached.Attribute discard approach—The malformed attributes in the update message are discarded; however, the message is processed. We do not recommend using this approach if the attributes to be discarded can affect route selection or installation.
Note:If an attribute appears more than once in an update message, all occurrences of the attribute, other than the first, will be discarded and the message will be processed.
The BGP update messages are scanned for the following attributes and are treated as malformed based on the values of these attributes:
-
The origin attribute—Handled by the treat-as-withdraw approach.
-
The AS path attribute—Handled by the treat-as-withdraw approach.
-
The AS 4 path attribute—Handled by the attribute discard approach.
-
The aggregator attribute—Handled by the attribute discard approach.
-
The aggregator 4 attribute—Handled by the attribute discard approach.
-
The next-hop attribute—Handled by the treat-as-withdraw approach.
-
The multiple exit discriminator attribute—Handled by the treat-as-withdraw approach.
-
The local preference attribute—Handled by the treat-as-withdraw approach.
-
The atomic aggregate attribute—Handled by the attribute discard approach.
-
The community attribute—Handled by the treat-as-withdraw approach.
-
The extended community attribute—Handled by the treat-as-withdraw approach.
-
The originator attribute—Handled by the treat-as-withdraw approach.
-
The cluster attribute—Handled by the treat-as-withdraw approach.
-
The PMSI attribute—Handled by the treat-as-withdraw approach.
-
The MP reach attribute—Handled by the notification message approach.
-
The MP unreach attribute—Handled by the notification message approach.
-
The attribute set attribute—Handled by the treat-as-withdraw approach.
-
The AIGP attribute—Handled by the treat-as-withdraw approach.
-
Unknown attribute—If the BGP flag does not indicate that this is an optional attribute, this malformed attribute is handled by the notification message approach.
When a BGP update message contains multiple malformed attributes, the most severe approach triggered by one of the attributes is followed.
Here's a sample of the BGP Error Message output:
user@R1> show log messages Sep 18 17:54:13 R1 rpd[86600]: Received malformed update from 10.10.10.2 (External AS 64511) Sep 18 17:54:13 R1 rpd[86600]: Family inet-unicast, prefix 100.1.1.0/24 Sep 18 17:54:13 R1 rpd[86600]: Malformed Attribute ORIGIN(1) flag 0x40 length 1 error 6 (Unrecognized ORIGIN attribute). Sep 18 17:54:13 R1 rpd[86600]: Malformed Attribute LOCAL_PREF(5) flag 0x40 length 6 error 5 (Attribute length error).
In this example, you see the origin (ORIGIN) and local preference (LOCAL_PREF) malformed attributes.
See Also
Example: Configuring Error Handling for BGP Update Messages
This example shows how to configure BGP error handling.
Requirements
Before you begin:
-
Configure router interfaces.
-
Configure an interior gateway protocol (IGP).
-
Configure BGP.
-
Configure routing policies.
Overview
When a routing device receives an update message with a malformed attribute, the router is required to reset the session. This is specified in RFC 4271, A Border Gateway Protocol 4 (BGP-4). Session resets impact not only routes with the offending attribute, but also other valid routes exchanged over the session. Moreover, this behavior can present a potential security vulnerability in the case of optional transitive attributes. To minimize the impact on routing made by malformed update messages, the Internet draft draft-ietf-idr-error-handling-01.txt, Revised Error Handling for BGP UPDATE Messages specifies modifications for handling BGP update message with malformed attributes. The new error handling allows for maintaining the established session and keeping the valid routes exchanged, while removing the routes carried in the malformed UPDATE message.
Topology
In Figure 1, Device R1 has an internal BGP peering session with Device R0, and an external BGP peering session with Device R2.
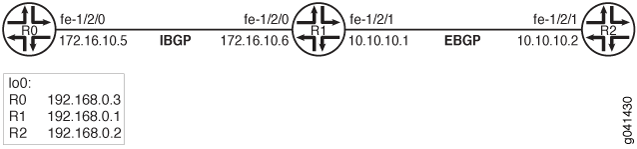
To protect against malformed update messages causing network instability, Device R1 has BGP error handling configured, as shown here:
bgp-error-tolerance {
malformed-update-log-interval 10;
malformed-route-limit 5;
}By default, a BGP message is considered to be malformed when
any one of the message attributes is malformed. When a router participating
in a BGP session receives a malformed update message, the entire session
is reset. The bgp-error-tolerance statement overrides this
behavior so that the following BGP error handling is in effect:
-
For fatal errors, Junos OS sends a notification message titled Error Code Update Message and resets the BGP session. An error in the MP_{UN}REACH attribute is considered to be fatal. The presence of multiple MP_{UN}REACH attributes in one BGP update is also considered to be a fatal error. Junos OS resets the BGP session if it cannot parse the NLRI field or the BGP update correctly. Failure to parse the BGP update packet can happen when the attribute length does not match the length of the attribute value.
-
For some nonfatal errors, Junos OS treats all the routes contained in the malformed BGP update message as withdrawn routes and installs them as hidden, unless the
keep nonestatement is included in the BGP is configuration. Junos OS uses this error handling approach for the cases that involve any of the following attributes: ORIGIN, AS_PATH, NEXT_HOP, MULTI_EXIT_DISC, LOCAL_PREF, ORIGINATOR, CLUSTER, ATTRSET, PMSI, Community, and Extended Community. In addition, if any of the mandatory well-known path attributes is missing, Junos OS treats the BGP update as malformed. To limit the memory usage of these malformed hidden routes, Junos OS stops installing new malformed hidden routes after the maximum number of such malformed hidden routes is reached. In this example, the maximum number is set to 5, using themalformed-route-limitstatement. The default value is 1000. Optionally, you can allow an unlimited number of routes hidden due to malformed attributes. Do this by including theno-malformed-route-limitstatement. -
For other nonfatal errors, Junos OS discards the malformed path attributes and continues to process the BGP update message. It is unsafe to use this approach on the path attributes that might affect route selection or installation. Junos OS uses this error handling approach for the cases that involve any of the following attributes: ATOMIC_AGGREGATE, AGGREGATOR, AGGREGATOR4, and AS4PATH.
To facilitate troubleshooting of malformed packets, Junos OS
logs the error listing the malformed path attribute code, flag, length,
information about the peer and family, and the first prefix from the
malformed BGP update. Logging of the malformed packets might slow
Junos OS performance if a significant number of malformed packets
is received in a short time. To limit the performance impact, Junos
OS implements an algorithm to log a malformed update, suppress logging
for an interval, and log a summary. When the logging suppression timer
expires, the software logs the total number of malformed attributes
received during the interval. In this example, the timer is set to
10 seconds, using the malformed-update-log-interval statement.
The default value is 300 seconds(5 minutes).
CLI Quick Configuration shows the configuration for all of the devices in Figure 1.
The section #d101e193__d101e403 describes the steps on Device R1.
Configuration
CLI Quick Configuration
To quickly configure
this example, copy the following commands, paste them into a text
file, remove any line breaks, change any details necessary to match
your network configuration, and then copy and paste the commands into
the CLI at the [edit] hierarchy level.
Device R0
set interfaces fe-1/2/0 unit 0 description to-R1 set interfaces fe-1/2/0 unit 0 family inet address 172.16.10.5/30 set interfaces lo0 unit 0 family inet address 192.168.0.3/32 set protocols bgp group internal-peers type internal set protocols bgp group internal-peers local-address 192.168.0.3 set protocols bgp group internal-peers export local-direct set protocols bgp group internal-peers neighbor 192.168.0.1 set protocols ospf area 0.0.0.0 interface fe-1/2/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 passive set policy-options policy-statement local-direct from protocol [local direct] set policy-options policy-statement local-direct then accept set routing-options autonomous-system 64510 set routing-options router-id 192.168.0.3
Device R1
set interfaces fe-1/2/1 unit 0 description to-R2 set interfaces fe-1/2/1 unit 0 family inet address 10.10.10.1/30 set interfaces fe-1/2/0 unit 0 description to-R0 set interfaces fe-1/2/0 unit 0 family inet address 172.16.10.6/30 set interfaces lo0 unit 0 family inet address 192.168.0.1/32 set protocols bgp bgp-error-tolerance malformed-update-log-interval 10 set protocols bgp bgp-error-tolerance malformed-route-limit 5 set protocols bgp group internal-peers type internal set protocols bgp group internal-peers local-address 192.168.0.1 set protocols bgp group internal-peers export local-direct set protocols bgp group internal-peers neighbor 192.168.0.3 set protocols bgp group external-peers type external set protocols bgp group external-peers export local-direct set protocols bgp group external-peers peer-as 64511 set protocols bgp group external-peers neighbor 10.10.10.2 set protocols ospf area 0.0.0.0 interface fe-1/2/1.0 set protocols ospf area 0.0.0.0 interface fe-1/2/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 passive set policy-options policy-statement local-direct from protocol [local direct] set policy-options policy-statement local-direct then accept set routing-options autonomous-system 64510 set routing-options router-id 192.168.0.1
Device R2
set interfaces fe-1/2/1 unit 0 description to-R1 set interfaces fe-1/2/1 unit 0 family inet address 10.10.10.2/30 set interfaces lo0 unit 0 family inet address 192.168.0.2/32 set protocols bgp group external-peers type external set protocols bgp group external-peers export local-direct set protocols bgp group external-peers peer-as 64510 set protocols bgp group external-peers neighbor 10.10.10.1 set protocols ospf area 0.0.0.0 interface fe-1/2/1.0 set protocols ospf area 0.0.0.0 interface lo0.0 passive set policy-options policy-statement local-direct from protocol [local direct] set policy-options policy-statement local-direct then accept set routing-options autonomous-system 64511 set routing-options router-id 192.168.10.2
Procedure
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure the BGP error handling:
-
Configure the router interfaces.
[edit interfaces] user@R1# set fe-1/2/1 unit 0 description to-R2 user@R1# set fe-1/2/1 unit 0 family inet address 10.10.10.1/30 user@R1# set fe-1/2/0 unit 0 description to-R0 user@R1# set fe-1/2/0 unit 0 family inet address 172.16.10.6/30 user@R1# set lo0 unit 0 family inet address 192.168.0.1/32
-
Configure an interior gateway protocol (IGP), such as OSPF or IS-IS.
[edit protocols ospf area 0.0.0.0] user@R1# set interface fe-1/2/1.0 user@R1# set interface fe-1/2/0.0 user@R1# set interface lo0.0 passive
-
Configure the autonomous system (AS) number and router ID.
[edit routing-options] user@R1# set autonomous-system 64510 user@R1# set router-id 192.168.0.1
-
Configure the routing policy.
[edit policy-options policy-statement local-direct] user@R1# set from protocol [local direct] user@R1# set then accept
-
Configure the EBGP session.
[edit protocols bgp group external-peers] user@R1# set type external user@R1# set export local-direct user@R1# set peer-as 64511 user@R1# set neighbor 10.10.10.2
-
Configure the IBGP sessions.
[edit protocols bgp group internal-peers] user@R1# set type internal user@R1# set local-address 192.168.0.1 user@R1# set export local-direct user@R1# set neighbor 192.168.0.3
-
Enable BGP error tolerance.
[edit protocols bgp] user@R1# set bgp-error-tolerance
-
(Optional) Configure the log interval.
[edit protocols bgp bgp-error-tolerance] user@R1# set malformed-update-log-interval 10
-
(Optional) Configure a limit for the number of hidden routes to store.
[edit protocols bgp bgp-error-tolerance] user@R1# set malformed-route-limit 5
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show protocols, show policy-options, and show routing-options, commands. If the output does not display the intended configuration,
repeat the instructions in this example to correct the configuration.
user@R1#
show interfaces
fe-1/2/0 {
unit 0 {
description to-R0;
family inet {
address 172.16.10.6/30;
}
}
}
fe-1/2/1 {
unit 0 {
description to-R2;
family inet {
address 10.10.10.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 192.168.0.1/32;
}
}
}user@R1# show protocols
bgp {
bgp-error-tolerance {
malformed-update-log-interval 10;
malformed-route-limit 5;
}
group internal-peers {
type internal;
local-address 192.168.0.1;
export local-direct;
neighbor 192.168.0.3;
}
group external-peers {
type external;
export local-direct;
peer-as 64511;
neighbor 10.10.10.2;
}
}
ospf {
area 0.0.0.0 {
interface fe-1/2/1.0;
interface fe-1/2/0.0;
interface lo0.0 {
passive;
}
}
}user@R1#
show policy-options
policy-statement local-direct {
from protocol [local direct];
then accept;
}user@R1#
show routing-options
router-id 192.168.0.1;
autonomous-system 64510;If you are done configuring the devices, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Checking the BGP Neighbor Sessions
Purpose
Verify that BGP error tolerance is enabled, and display the counters related to malformed path attributes.
Action
user@R1# show bgp neighbor
Peer: 10.10.10.2+50058 AS 64511 Local: 10.10.10.1+179 AS 64510
Type: External State: Established Flags: <Sync>
Last State: OpenConfirm Last Event: RecvKeepAlive
Last Error: None
Export: [ local-direct ]
Options: <Preference PeerAS Refresh>
Holdtime: 90 Preference: 170
Number of flaps: 0
Malformed attributes log interval: 10 route limit: 5
Attribute: ORIGIN(1) Last Received: 0 Total Received: 3
Attribute: LOCAL_PREF(5) Last Received: 0 Total Received: 2
Peer ID: 192.168.10.2 Local ID: 192.168.10.1 Active Holdtime: 90
Keepalive Interval: 30 Group index: 0 Peer index: 0
BFD: disabled, down
Local Interface: fe-1/2/1.0
NLRI for restart configured on peer: inet-unicast
NLRI advertised by peer: inet-unicast
NLRI for this session: inet-unicast
Peer supports Refresh capability (2)
Stale routes from peer are kept for: 300
Peer does not support Restarter functionality
NLRI that restart is negotiated for: inet-unicast
NLRI of received end-of-rib markers: inet-unicast
NLRI of all end-of-rib markers sent: inet-unicast
Peer supports 4 byte AS extension (peer-as 64511)
Peer does not support Addpath
Table inet.0 Bit: 10000
RIB State: BGP restart is complete
Send state: in sync
Active prefixes: 0
Received prefixes: 3
Accepted prefixes: 0
Suppressed due to damping: 0
Advertised prefixes: 2
Last traffic (seconds): Received 25 Sent 17 Checked 73
Input messages: Total 2702 Updates 10 Refreshes 0 Octets 51652
Output messages: Total 2701 Updates 6 Refreshes 0 Octets 51571
Output Queue[0]: 0
Peer: 192.168.10.3+179 AS 64510 Local: 192.168.10.1+51127 AS 64510
Type: Internal State: Established Flags: <Sync>
Last State: OpenConfirm Last Event: RecvKeepAlive
Last Error: None
Export: [ local-direct ]
Options: <Preference LocalAddress Refresh>
Local Address: 192.168.10.1 Holdtime: 90 Preference: 170
Number of flaps: 0
Malformed attributes log interval: 10 route limit: 5
Peer ID: 192.168.10.3 Local ID: 192.168.10.1 Active Holdtime: 90
Keepalive Interval: 30 Group index: 1 Peer index: 0
BFD: disabled, down
NLRI for restart configured on peer: inet-unicast
NLRI advertised by peer: inet-unicast
NLRI for this session: inet-unicast
Peer supports Refresh capability (2)
Stale routes from peer are kept for: 300
Peer does not support Restarter functionality
NLRI that restart is negotiated for: inet-unicast
NLRI of received end-of-rib markers: inet-unicast
NLRI of all end-of-rib markers sent: inet-unicast
Peer supports 4 byte AS extension (peer-as 64510)
Peer does not support Addpath
Table inet.0 Bit: 10001
RIB State: BGP restart is complete
Send state: in sync
Active prefixes: 0
Received prefixes: 3
Accepted prefixes: 0
Suppressed due to damping: 0
Advertised prefixes: 2
Last traffic (seconds): Received 5 Sent 24 Checked 51
Input messages: Total 417 Updates 3 Refreshes 0 Octets 8006
Output messages: Total 421 Updates 2 Refreshes 0 Octets 8136
Output Queue[0]: 0Meaning
The Malformed attributes field shows that error tolerance is enabled. The log interval and route limit fields display the configured values.
The attribute counters show that on the EBGP connection, several malformed attributes were received from Device R2.
Checking Hidden Routes
Purpose
View information about hidden routes and learn why they are hidden.
Action
user@R1> show route hidden detail
inet.0: 42 destinations, 45 routes (36 active, 0 holddown, 6 hidden)
10.0.0.0/32 (1 entry, 0 announced)
BGP
Next hop type: Router
Address: 0x93d8b0c
Next-hop reference count: 5
Source: 10.10.10.2
Next hop type: Router, Next hop index: 782
Next hop: via fe-1/2/1.0, selected
Session Id: 0x1
State: <Hidden Ext>
Local AS: 1 Peer AS: 1
Age: 5:32 Metric2: 1
Validation State: unverified
Task: BGP_1.10.10.5.62+56218
AS path: I (MalformedAttr)
Router ID: 192.168.0.2
10.0.0.1/32 (1 entry, 0 announced)
BGP
Next hop type: Router
Address: 0x93d8b0c
Next-hop reference count: 5
Source: 10.10.10.2
Next hop type: Router, Next hop index: 782
Next hop: via fe-1/2/1.0, selected
Session Id: 0x1
Indirect next hop: 953c000 - INH Session ID: 0x3
State: <Hidden Int Ext>
Local AS: 1 Peer AS: 1
Age: 5:32 Metric2: 1
Validation State: unverified
Task: BGP_1.10.10.5.62+56218
AS path: I (MalformedAttr)
Router ID: 192.168.0.2Meaning
The malformed hidden routes are marked with MalformedAttr in the AS path field.
You can remove the hidden routes by running the
clear bgp neighbor 10.10.10.2 malformed-route command.
Verifying the Source of the Hidden Routes
Purpose
View information about hidden routes and learn why they are hidden.
Action
user@R1> show route receive-protocol bgp 10.10.10.2 detail hidden
inet.0: 42 destinations, 45 routes (36 active, 0 holddown, 6 hidden)
10.0.0.0/32 (1 entry, 0 announced)
Nexthop: 10.10.10.2
Localpref: 100
AS path: I (MalformedAttr)
10.0.0.1/32 (1 entry, 0 announced)
Nexthop: 10.10.10.2
Localpref: 100
AS path: I (MalformedAttr)Meaning
Junos OS displays MalformedAttr in the AS path field
in the output of the show route receive-protocol bgp 10.10.10.2
detail hidden command.
You can remove the hidden routes by running the clear bgp
neighbor 10.10.10.2 malformed-route command.
