Active Directory as Identity Source
Learn about Active Directory as an identity source, its benefits, and how an Active Directory works as an identity source.
An identity source stores user information in a database. You can use this information for user authentication. Active Directory as an identity source defines integration of firewall with Microsoft Windows Active Directory.
Active Directory as identity source was previously known as Integrated User Firewall.
Overview of Active Directory as Identity Source
Figure 1 illustrates a typical scenario where the Active Directory as identity source is deployed. Users inside and outside the Active Directory domain need to access the Internet through a device.
Benefits
-
Simplifies configuration steps and provides best-effort security to access the device.
-
Ideal for medium businesses and up to medium-scale deployments.
-
Supports high availability (HA).
-
Configuration of captive portal is optional for users who do not authenticate.
How does Active Directory as Identity Source Work?
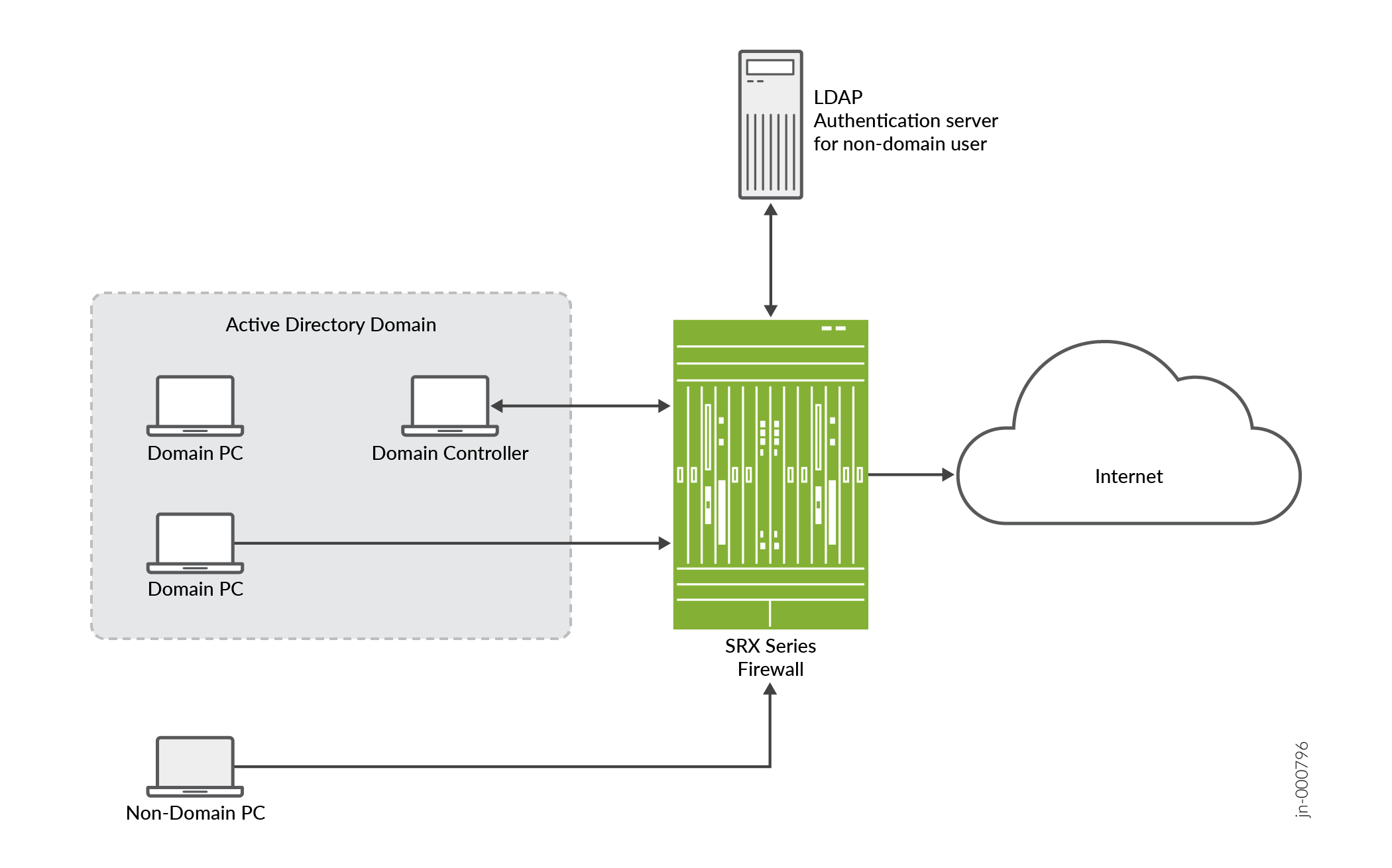
|
Components |
Description |
|---|---|
|
Domain Controller |
Domain controller helps to apply security policies for request access to user authentication resources. The domain controller might also act as the LDAP server. |
|
Domain PC |
Connected windows computers group that share user account information and a security policy. |
|
Non-domain PC |
Users can access Windows desktop enviroment from any location using a device with internet connectivity. |
|
LDAP authentication server for non-domain user |
LDAP protocol helps identify the groups to which users belong. The username and group information are queried from the LDAP service in the Active Directory controller. |
-
The device reads and analyzes the Windows event log of the active directory controller and generates an authentication table.
-
The Active Directory as identity source is aware of any domain user via the authentication table.
-
The device configures a policy that enforces the required user-based or group-based access control.
-
For any non-domain user or domain user on a non-domain machine, the administrator specifies a captive portal to force the user to authenticate (if the device supports captive portal for the traffic type).
-
After users enter their names and passwords and authenticate, the device gets user/group information and enforces the policy.
-
In addition to captive portal, if the IP address or user information is not available from the event log, users can again log in to the Windows PC to generate an event log entry. Then, the system generates the user authentication entry.
Windows Management Instrumentation Client (WMIC)
- What is Windows Management Instrumentation Client (WMIC)?
- How WMIC reads the Event Log on the Domain Controller?
- Specify IP Filters to Limit IP-to-User Mapping
- Windows Event Log Verification and Statistics
- Firewall Authentication as backup to WMIC
What is Windows Management Instrumentation Client (WMIC)?
When you configure the Active Directory as identity source, the device establishes a Windows Management Instrumentation (WMI)/Distributed Component Object Module (DCOM) connection with the domain controller. The device acts as a WMI client (WMIC). The device reads and monitors the security event log on the domain controller. The device analyzes the event messages to generate IP address-to-user mapping information.
Use Feature Explorer to confirm platform and release support for specific features.
Review the Platform-Specific WMIC Behavior section for notes related to your platform.
How WMIC reads the Event Log on the Domain Controller?
WMIC reads the event log on the domain controller in following manner:
-
The device monitors the event log at a configurable interval, which defaults to 10 seconds.
-
The device reads the event log for a certain timespan, which you can configure. The default timespan is one hour.
-
Each time at WMIC starts up, the device checks the last timestamp and the current timespan. If the last timestamp is older than the current timespan, then the current timespan takes effect.
-
The device can read the event log to obtain both IPv4 and IPv6 addresses.
-
When WMIC starts up, the firewall has a maximum count of events that it can read from the event log. You cannot configure the maximum count of events.
When WMIC starts up, the WMIC uses the maximum count with the timespan setting. When the limit is reached, the WMIC stops reading the event log.
-
After a failover, the device reads the event log from the latest event log timestamp.
Specify IP Filters to Limit IP-to-User Mapping
You can specify the IP filters to limit the IP address-to-user mapping information that the device generates from the event log.
To understand when a filter is useful for such mapping, consider the following scenario. A customer deploys 10 devices in one domain, and each device controls a branch. All 10 devices read all 10 branch user login event logs in the domain controller. However, the device is configured to detect only whether the user is authenticated on the branch it controls. By configuring an IP filter on the device, the device reads only the IP event log under its control.
You can configure a filter to include or exclude IP addresses or prefixes. You can specify a maximum of 20 addresses for each filter.
Windows Event Log Verification and Statistics
You can verify that the authentication table is getting IP address and user information
by issuing the show services user-identification active-directory-access
active-directory-authentication-table all command. A list of IP address-to-user
mappings is displayed for each domain. The table contains no group information until LDAP
is running.
You can see statistics about reading the event log by issuing the show services
user-identification active-directory-access ip-user-mapping statistics domain
command.
Firewall Authentication as backup to WMIC
The primary method for the Active Directory as identity source to get IP address-to-user mapping information is for the device to act as a WMI client (WMIC). However, the event-log-reading and PC probe functions both use WMI, and using a global policy to disable the WMI-to-PC probe affects event log reading. These might result in the failure of the PC probe, and a backup method for getting IP address-to-user mappings is needed. That method is to use firewall authentication to identify users.
See Domain PC Probing.
If a domain is configured in that statement, fwauth recognizes that the
domain is for a domain authentication entry, and will send the domain name to the
fwauth process along with the authentication request. After it receives
the authentication response, fwauth deletes that domain authentication
entry. The fwauth process sends the source IP address, username, domain,
and other information to the UserID process, which verifies that it is a valid domain user
entry. The subsequent traffic will hit this user firewall entry.
Domain PC Probing
- What is Domain PC Probing?
- Domain PC Probing User Information
- How to Configure Probe?
- Probe Rate and Statistics
What is Domain PC Probing?
Domain PC probing acts as a supplement of event log reading. When a user logs in to the domain, the event log contains that information. The PC probe is triggered only when there is no IP-to-address mapping from the event log.
Domain information constantly changes as users log in and out of domain PCs. The Active Directory as identity source probe functionality provides a mechanism for tracking and verifying information in the authentication tables by directly probing domain PCs for IP address-to-user mapping information. New and changed information identified by the probe serves to update Active Directory authentication table entries, which is critical to maintaining firewall integrity.
The IP address filter also impacts the PC probe. Once you configure the IP address filter, only the IP address specified in the filter is probed.
Use Feature Explorer to confirm platform and release support for specific features.
Review the Platform-Specific Probe Rate Behavior section for notes related to your platform.
Domain PC Probing User Information
The Active Directory as identity source tracks the online status of users by probing domain PCs. If a user is not online or is not an expected user, the Active Directory authentication table is updated as appropriate. The following probe behaviors apply:
| On-demand probing |
On-demand probing occurs when a packet is dropped due to a missing entry in the Active Directory authentication table. In this case, an entry is added in pending state to the authentication table, and the domain PC identified by the source IP field of the dropped packet is probed for IP address and user information. The entry remains in pending state until a response is received from the probe. |
| Manual probing |
Manual probing is used to verify and troubleshoot the online status of a user or a range of users, and is at the discretion of the system administrator. Note:
Manual probing can cause entries to be removed from the Active Directory authentication table. For example, if there is no response from your PC due to a network issue, such as when the PC is too busy, the IP address entry of the PC is marked as invalid and your access is blocked. |
Based on the domain PC probe response, updates are made to the Active Directory authentication table, and associated firewall policies take effect. If no response is received from the probe after 90 seconds, the authentication entry times out. The timed-out authentication entry is the pending state authentication entry, which is generated when you start the PC probe.
If the probe is successful, the state of the authentication entry is updated from pending to valid. If the probe is unsuccessful, the state of the authentication entry is marked as invalid. The invalid entry has the same lifetime as a valid entry and is overwritten by upcoming fwauth (firewall authentication process) authentication results or by the event log.
If the device cannot access a domain PC for some reason, such as a network configuration or Windows firewall issue, the probe fails.
For more probe responses and corresponding authentication table actions, see Table 2.
|
Probe Response from Domain PC |
Active Directory Authentication Table Action |
|---|---|
|
Valid IP address and username |
Add IP-related entry. |
|
Logged on user changed |
Update IP-related entry. |
|
Connection timeout |
Update IP-related entry as invalid. |
|
Access denied |
Update IP-related entry as invalid. |
|
Connection refused |
Update IP-related entry as invalid. |
|
Authentication failed (The configured username and password have no privilege to probe the domain PC.) |
Update IP-related entry as invalid. |
How to Configure Probe?
On-demand probing is enabled by default. To disable on-demand probing, you can use the
set services user-identification active-directory-access
no-on-demand-probe statement. Delete this statement to reenable probing. When
on-demand probing is disabled, manual probing is available.
To initiate a manual probe, you can use the request services user-identification
active-directory-access ip-user-probe address ip-address address
domain domain-name
command. If a domain name is not
specified, the probe looks at the first configured domain for the IP address. To specify a
range, use the appropriate network address.
The probe timeout value is configurable. If no response is received from the domain PC
within the wmi-timeout interval, the probe fails and the system either
creates an invalid authentication entry or updates the existing authentication entry as
invalid. If an authentication table entry already exists for the probed IP address, and no
response is received from the domain PC within the wmi-timeout interval,
the probe fails and that entry is deleted from the table.
See Configure Active Directory as Identity Source on SRX Series Firewall.
Probe Rate and Statistics
The maximum probe rate for the Active Directory as identity source is set by default and cannot be changed. Probe functionality supports 5000 users, or up to 10 percent of the total supported authentication entries, whichever is smaller. Supporting 10 percent means that at any time, the number of IP addresses waiting to be probed cannot exceed 10 percent.
LDAP for Active Directory as Identity Source
- What is the use of LDAP for Active Directory as Identity Source?
- How LDAP for Active Directory as Identity Source Work?
What is the use of LDAP for Active Directory as Identity Source?
The use of LDAP in this section applies specifically to LDAP functionality within the Active Directory as identity source.
In order to get the user and group information necessary to implement the Active Directory as identity source, the device uses the Lightweight Directory Access Protocol (LDAP). The device acts as an LDAP client communicating with an LDAP server. In a common implementation scenario of the Active Directory as identity source, the domain controller acts as the LDAP server. The LDAP module in the device, by default, queries the Active Directory in the domain controller.
The device downloads user and group lists from the LDAP server. The device also queries the LDAP server for user and group updates. The device downloads a first-level, user-to-group mapping relationship and then calculates a full user-to-group mapping.
How LDAP for Active Directory as Identity Source Work?
The LDAP server’s username, password, IP address, and port are all optional, but they can be configured.
-
If the username and password are not configured, the system uses the configured domain controller’s username and password.
-
If the LDAP server’s IP address is not configured, the system uses the address of one of the configured Active Directory domain controllers.
-
If the port is not configured, the system uses port 389 for plaintext or port 636 for encrypted text.
By default, the LDAP authentication method uses simple authentication. The client’s username and password are sent to the LDAP server in plaintext. Keep in mind that the password is clear and can be read from the network.
To avoid exposing the password, you can use simple authentication within an encrypted
channel [namely Secure Sockets layer (SSL)], as long as the LDAP server supports LDAP over
SSL (LDAPS). After enabling SSL, the data sent from the LDAP server to the device is
encrypted. To enable SSL, see the user-group-mapping statement.
Device Identity
You can use the Active Directory as identity source device identity authentication feature to control access to network resources based on the attributes, or characteristics, of the device used. After you configure device identity authentication feature, you can configure security polices that allow or deny traffic from the identified device based on the policy action.
For more information, see Example: Configure the Device Identity Authentication Feature.
- Why Use Device Identity to Control Access to Your Network
- Device Identity Attributes and Profiles
- Device Identity Authentication Table
- Device Identity Information from Windows Active Directory for Network Access Control
- Device Identity XML Solution for Third-Party NAC Authentication Systems
Why Use Device Identity to Control Access to Your Network
For various reasons, you might want to control access to your network resources based on the identity of the user’s device rather than on the identity of the user. The Active Directory as identity source device identity authentication feature was designed to offer a solution to these and other similar situations by enabling you to control network access based on attributes of the user’s device.
The device receives or obtains the device identity information from the authentication source in the same manner that it obtains the user identity information, depending on the authentication source. The process in which the device identity information is obtained and stored in the device identity information table entails the following actions on the part of the device:
-
Getting the device identity information.
Depending on the authentication source, the device uses one of the following two methods to obtain the device identity information:
-
Microsoft Active Directory as identity source—If your environment is set up to use Microsoft Active Directory, the firewall obtains the device IP address and groups from the Active Directory domain controller and LDAP service. The device can extract the device information from the domain controller’s event log and then connect to the Active Directory LDAP server to obtain the names of the groups that the device belongs to. The device uses the information that it obtained from the event log to locate the device’s information in the LDAP directory.
-
Third-party Network Access Control (NAC) systems—If your network environment is configured for a NAC solution and you decide to take this approach, the NAC system sends the device identity information to the firewall. These authentication systems use the POST service of the RESTful Web services API, called Web API. The device implements the API and exposes to the authentication systems to allow them to send the device identity information to the firewall. The API has a formal XML structure and restrictions that the authentication source must adhere to in sending this information to the device.
Warning:If you take this approach, you must verify that your NAC solution works with the device.
-
-
Creating an entry for the device in the device identity authentication table.
-
After the firewall obtains the device identity information, it creates an entry for it in the device identity authentication table. The device identify authentication table is separate from the Active Directory authentication table or any of the other local authentication tables used for third party authentication sources.
-
Too, unlike local user authentication tables which are particular to an authentication source or feature, the device identity authentication table holds device identity information for all authentication sources. However, only one authentication source, such as Active Directory, can be active at a time. The firewall allows only authentication source to be used at a time to constrain the demand on the system to process information.
-
The purpose of obtaining the device information and entering it into the device identity authentication table is to control user access to network resources based on the device’s identity. For this to occur, you must also configure security policies that identify the device, based on the specified device identity profile, and specify the action to be taken on traffic that issues from that device.
-
The device identity authentication feature provides a generic solution that stores device identity information in the same table regardless of the authentication source.
-
Device Identity Attributes and Profiles
The device identity profile, referred to in the CLI as the
end-user-profile
, is a key component of the Active Directory
as identity source device identity authentication feature. It identifies the device and
specifies its attributes.
Device Identity
The device identity essentially consists of the IP address of the device, its name, its domain, and the groups that the device belongs to.
For example, the following output shows information about the device, which is referred to from the device identity profile. This example shows that the device identity authentication table contains entries for two devices. For each entry, it shows the IP address of the device, the name assigned to the device, and the groups that the device belongs to. Note that both devices belong to the group grp4.
Source IP Device ID Device-Groups 192.0.2.1 lab-computer1 grp1, grp3, grp4 198.51.100.1 dev-computer2 grp5, grp6, grp4
Device Identity Profile
A device identity profile specifies the name of the device and information that includes the IP address of the device, groups to which the device belongs, and attributes of the device which are collectively referred to as the host attributes. The Packet Forwarding Engine of the device maps the IP address of a device to the device identity profile.
When traffic from a device arrives at the firewall,
the device obtains the IP address of the device from the first packet of the
traffic and uses it to search the device identity authentication table for a
matching device identity entry. Then it matches that device identity profile
with a security policy whose source-end-user-profile field
specifies the device identity profile name. If a match is found, the security
policy is applied to traffic issuing from the device.
The same device identity profile can also apply to other devices sharing the same attributes. However, for the same security policy to apply, the device and its traffic must match all other fields in the security policy.
A device identity profile must contain the domain name. It might contain more than one set of attributes, but it must contain at least one. Consider the following two sets of attributes that belong to the profile called marketing-main-alice. The profile contains the following set of attributes:
-
alice-T430, as the name of the device.
-
MARKETING and WEST-COAST, as the groups that the device belongs to.
-
example.net as the name of the domain that it belongs to.
The profile also the following attributes that characterize the device:
-
laptop, as the category of the device (device-category)
-
Lenovo, as the device vendor (device-vendor)
-
ThinkPad T430, as the type of device (device-type)
In cases such as the marketing-main-alice profile that includes the name given to the device, the profile applies exclusively to that device.
However, now suppose that another profile called marketing-west-coast-T430 was configured and that it contains the same attributes as the marketing-main-alice profile with one exception: the name given to the device in the marketing-main-alice profile was not included as an attribute in the marketing-west-coast-T430 profile. In this case, the attributes contained in the profile now make up a group profile. Application of the profile is widened to include all Lenovo ThinkPad T430 devices (which are laptops) that fit the rest of the characteristics, or attributes, defined in the profile.
Devices are covered by the profile if all other attributes match: devices that belong to either the MARKETING or WEST-COAST groups, which the marketing-west-coast-T430 profile specifies as its groups, or to both groups, match the profile.
As mentioned previously, a device identity profile can contain more than one group. A device can also belong to more than one group.
To illustrate further, note that the group device identity profile called marketing-west-coast-T430 also applies to the device called alice-T430 because that device belongs to both the MARKETING and the WEST-COAST groups and it matches all other attributes defined in the profile. Of course, the marketing-main-alice device identity profile still applies to the device called alice-T430. Therefore, the device called alice-T430 belongs to at least two groups, and it is covered by at least two device identity profiles.
Suppose that another profile called marketing-human-resources was defined with all of the attributes of the marketing-west-coast-T430 device identity profile but with these differences: the new device identity profile includes a group called HUMAN-RESOURCES and it does not include the group called WEST-COAST. However, it does contain the MARKETING group.
Because the device called alice-T430 belongs to the MARKETING group, which remains as a group in marketing-human-resources profile, the alice-T430 device also matches the marketing-human-resources device identity profile. Now the alice-T430 device matches three profiles. If the names of any of these profiles is specified in a security policy’s source-end-user-profile and the alice-T430 device matches all of the other fields in the security profile, then that profile’s action is applied to traffic from that device.
The previous examples of device identity profiles illustrate the following points:
-
A profile can be defined to identify only one device or it can be defined to apply to many devices.
-
A device identity profile can contain more than one group to which a given device belongs.
-
A device can match more than one device identity profile by matching the characteristics, or attributes, including at least one of the groups, configured for the profile.
The flexible use of device identity profiles will become evident when you configure security policies that are designed to include the source-end-user-profile field, in particular when you want the policy’s action to be applied to a number of devices.
Security Policy Matching and Device Identity Profiles
The device follows the standard rules for matching traffic against security policies. The following behavior pertains to the use of a device identity profile in a security policy for determining a match:
-
Use of a device identity profile in a security policy is optional.
-
If no device identity profile is specified in the source-end-user-profile field,
anyprofile is assumed. -
You cannot use the keyword
anyin thesource-end-user-profilefield of a security policy.If you use the source-end-user-profile field in a security policy, you must reference a specific profile. The device from which the access attempt is issued must match the profile’s attributes.
-
-
Only one device identity profile can be specified in a single security policy.
-
A security policy rematch is triggered when the
source-end-user-profilefield value of the security policy is changed. No rematch is triggered when an attribute value of a profile is changed.
Predefined Device Identity Attributes
The firewall provides the predefined device identity policy attributes that are configured using the third-party RESTful web services API, which is used by NAC systems or Active Directory LDAP.
-
device-identity
-
device-category
-
device-vendor
-
device-type
-
device-os
-
device-os-version
You specify values for these attributes in a device identity profile.
Characteristics of Device Identity Profiles, and Attributes and Target Scaling
This section describes how the firewall treat device identity attributes and profiles. It also gives device-independent and device-dependent scaling numbers for these entities.
The following attribute and profile characteristics apply to their use on all supported firewalls.
-
The maximum length of the following entities is 64 bytes: device identity profile names (referred to in the CLI as
end-user-profile) attribute names, attribute-values. -
You can not overlap values in a range if you configure more than one digital value range for the same attribute.
-
When the device matches a device identity profile to a security policy, all of the attributes in the profile are taken into account. Here is how they are treated:
-
If the device identity profile contains multiple values for an attribute, the values of that attribute are treated individually. It is said that they are ORed.
For the security policy to be applied to the device, the following conditions must be met. The device must match:
-
One of the values for each attribute that has multiple values.
-
The rest of the attribute values specified in the device identity profile.
-
The security policy field values.
-
-
All individual attributes that have a single value are treated separately and considered together as a collection of values—that is, the AND operation is applied to them. The device uses its standard policy-matching criteria in handling these attributes.
-
Table 3 shows the platform-independent scaling values used in the device identity authentication feature.
|
Item |
Maximum |
|---|---|
|
Values per attribute |
20 |
|
Attributes per profile |
100 |
|
Device identity profile specification per security policy (source-end-user-profile) |
1 |
Table 4 shows the platform-dependent scaling values used in the device identity authentication feature..
|
Platform |
Maximum Number of Profiles |
Maximum Total Number of Attribute Values |
|---|---|---|
|
SRX5000 line |
4000 |
32000 |
|
SRX1500 |
1000 |
8000 |
|
SRX300, SRX320 |
100 |
1000 |
|
SRX340, SRX345 |
100 |
1000 |
|
vSRX Virtual Firewall |
500 |
4000 |
|
NFX150 |
100 |
1000 |
The following changes to device identity profiles and their use in security policies do not cause the device to perform a session scan:
-
Updates to a profile which is referenced in a security policy.
-
Updates to the profile configuration.
-
Updates to attributes that are made through the RESTful web services API, which is used by NAC systems, or Active Directory LDAP.
Device Identity Authentication Table
When you configure the device to use the device identity authentication feature for authentication based on the device identity and its attributes, the device creates a new table called the device identity authentication table. Unlike other local authentication tables, the device identity authentication table does not contain information about a user but rather about the user’s device. The device identity authentication table serves as a repository for device identity information for all devices regardless of their authentication source. For example, it might contain entries for devices authenticated by Active Directory or third-party NAC authentication sources.
A device identity authentication table entry contains the following parts:
-
The IP address of the device.
-
The name of the domain that the device belongs to.
-
The groups with which the device is associated.
-
The device identity.
The device identity is actually that of a device identity profile (referred to in the CLI as
end-user-profile). This type of profile contains a group of attributes that characterize a specific individual device or a specific group of devices, for example, a specific type of laptop.
IPv6 addresses for user firewall module (UserFW) authentication allows IPv6 traffic to match any security policy configured for source identity. IPv6 addresses are supported for the following authentication sources:
-
Active directory authentication table
-
Device identity with Active Directory authentication
-
Local authentication table
-
Firewall authentication table
Why the Device Identity Authentication Table Content Changes
The device identity entries in the device identity authentication table are changed when certain events occur: when the user authentication entry with which the device identity entry is associated expires, when security policy changes occur in regard to referencing a group that the device belongs to, when the device is added to or removed from groups, or when groups that it belongs to are deleted and that change is made to the Windows Active Directory LDAP server.
-
When the User Identity Entry with Which a Device Identity Entry Is Associated Expires
When the device generates an entry for a device in the device identity authentication table, it associates that entry with a user identity entry in a local authentication table for the specific authentication source that authenticated the user of the device, such as Active Directory. That is, it ties the device identity entry in the device identity authentication table to the entry for the user of the device in the user authentication table.
When the user authentication entry with which the device identity entry is associated expires and is deleted from the user authentication table, the device identity entry is deleted silently from the device identity authentication table. That is, no message is issued to inform you of this event.
-
When Security Policy Changes Occur in Regard to Referencing a Group to Which the Device Belongs
To control access to network resources based on device identity, you create a device identity profile that you can refer to in a security policy. In addition to other attributes, a device identity profile contains the names of groups. When a device identity profile is referenced by a security policy, the groups that it contains are referred to as interested groups.
A group qualifies as an interested group if it is referenced by a security policy—that is, if it is included in a device identity profile that is specified in the
source-end-user-device field of a security policy. If a group is included in a device identity profile that is not currently used in a security policy, it is not included in the list of interested groups. A group can move in and out of the list of groups referenced by security policies. -
When a Device Is Added to or Removed from a Group or a Group Is Deleted
To keep the device identity entries in the local device identity authentication table current, the firewall monitors the Active Directory event log for changes. In addition to determining whether a device has logged out of or in to the network, it can determine changes to any groups that the device might belong to. When changes occur to the groups that a device belongs to—that is, when a device is added to or removed from a group or the group is deleted—the device modifies the contents of the affected device entries in its own device identity authentication table to reflect the changes made in the Microsoft Windows Active Directory LDAP server.
The device identity authentication table is updated according to changes to groups with which the device is associated in the LDAP server, as illustrated in Table 5.
|
Changes Made to LDAP |
Firewall LDAP Message and UserID Daemon Action |
|---|---|
|
Group information for a device has changed. The device has been added to or removed from a group, or a group that the device belongs to has been deleted. |
The Active Directory LDAP module sends notification of the change to the firewall UserID daemon, directing it to revise information in its local device identity authentication table. The device processes these messages every 2 minutes. |
|
The device entry in LDAP is deleted. |
The Active Directory LDAP module sends notification of the change to the UserID daemon, directing it to revise information in its local device identity authentication table. The device processes these messages every 2 minutes. |
The firewall or NFX Series device UserID daemon is informed of the changes. Whether or not a group that a device belongs to is specified in a security policy has bearing on what information is stored in device identity authentication table entries for the affected device. Table 6 shows the activity that occurs when a group is added to or deleted from the Active Directory LDAP.
|
Device Identity Profile Changes |
Device-Group Mapping Behavior |
Firewall UserID Daemon Response |
|---|---|---|
|
A new group that was added to the Active Directory LDAP is added to the Firewall identity profile. |
The device gets the list of devices that belong to the new group and its subgroups from the Active Directory LDAP server. It adds the list to its local LDAP directory. |
The UserID daemon determines whether the device identity authentication table includes entries for the set of affected devices. If so, it updates the group information for these entries. For example, here is the entry for device1 before it was updated to include the new group and after the group was added:
|
|
A group is deleted from the Active Directory LDAP. The device deletes the group from the device identity profile. |
The device gets the list of devices that belong to the deleted group from its local LDAP database. It deletes the device-group mapping from the local LDAP directory. |
The UserID daemon checks the device identity authentication table for entries that belong to the group. It removes the group from affected entries. For example, here is the entry for device1 before the group was deleted and after the group was deleted:
|
Table 7 elaborates on the contents of device authentication entries for several devices that are affected by deletion of a group.
|
IP Address |
Device Information |
Group |
|---|---|---|
|
Original Entries |
||
|
192.0.2.10 |
device1 |
group1, group2 |
|
192.0.2.11 |
device2 |
group3, group4 |
|
192.0.2.12 |
device3 |
group2 |
|
Same Entries After group2 Is Deleted |
||
|
192.0.2.10 |
device1 |
group1 |
|
192.0.2.11 |
device2 |
group3, group4 |
|
192.0.2.12 |
device3 |
This entry no longer contains groups. |
Device Identity Information from Windows Active Directory for Network Access Control
You can use the device identity authentication feature to control access to your network resources based on the identity and attributes of the device used rather than the user identity. Information about a device is stored in the device identity authentication table. You can specify the name of a device identity profile that contains the device attributes in the source-end-user-profile field of a security policy. If all conditions are met, the security policy’s actions are applied to traffic issuing from that device.
For you to be able to use device identity profiles in security policies, the firewall must obtain the device identity information for authenticated devices. The device creates the device identity authentication table to use to store device identity entries. It searches the table for a device match when traffic arrives from a device. This topic considers the process followed when Active Directory is used as the authentication source.
An Active Directory domain controller authenticates users when they log in to the domain, and it writes a record of that event to the Windows event log. It also writes a record to the event log when a user logs out of the domain. The domain controller event log provides the device with information about authenticated devices that are currently active in the domain and when those devices are logged out from it.
The UserID daemon takes the following actions:
-
It reads the Active Directory domain controller event logs to obtain the IP addresses of devices logged into the domain and authenticated by Windows.
The UserID daemon in the device Routing Engine implements a Windows Management Instrumentation (WMI) client with Microsoft Distributed COM/Microsoft RPC stacks and an authentication mechanism to communicate with a Windows Active Directory domain controller in an Active Directory domain. Using event log information retrieved from the Active Directory controller, the process obtains the IP addresses of active Active Directory devices. The process monitors Active Directory event log changes using the same WMI DCOM interface to adjust its device identity information in its local authentication table to reflect any changes made to the Active Directory server.
-
It uses the device IP addresses that it obtained from the event log to obtain information about the groups that a device belongs to. To obtain this group information, the device connects to the LDAP service in the Active Directory controller using the LDAP protocol for this purpose.
As a result of this process, the device is able to generate entries for the devices in the device identity authentication table. After it generates an entry for a device in the device identity authentication table, the device associates that entry with the appropriate user entry in its local Active Directory authentication table. You can then reference the device identity profile entries in security policies to control access to resources.
Behavior and Constraints
-
The process of reading the event log consumes domain controller CPU resources which may lead to high CPU usage in the domain controller. For this reason, the Active Directory domain controller should have a high-performance configuration of at least 4 cores and 8 gigabytes of memory.
-
The domain controller event log records a maximum length of 16 bytes of the device ID, including a null terminator. Therefore, the maximum length of the device ID that the device obtains from the domain controller is 15 bytes.
-
If the domain controller clears the event log or if the data written to the event log is missing or delayed, the device identity mapping information might be inaccurate. If the firewall is unable to read the event log or if it contains null data, the device reports an error condition in its own log.
-
If the device identity information table reaches capacity, it cannot add new device identity entries. In that case, traffic from the device is dropped.
Device Identity XML Solution for Third-Party NAC Authentication Systems
Figure 2 shows the communication between the firewall and a third-party NAC authentication source that is used for device identity authentication. The firewall receives the device identity information from the NAC system and stores it in its local device identity authentication table. A security policy that specifies a device identity profile is applicable to one or more devices. If a device matches the device identity profile and other parts of the security policy, the security policy is applied to traffic issuing from that device.
Use of a device identity profile in a security policy is optional. If no device identity profile is specified in the security policy’s source-end-user-profile field, “any” profile is assumed. However, you can not use the keyword “any” in the source-end-user-profile field of a security policy. It is a reserved keyword.
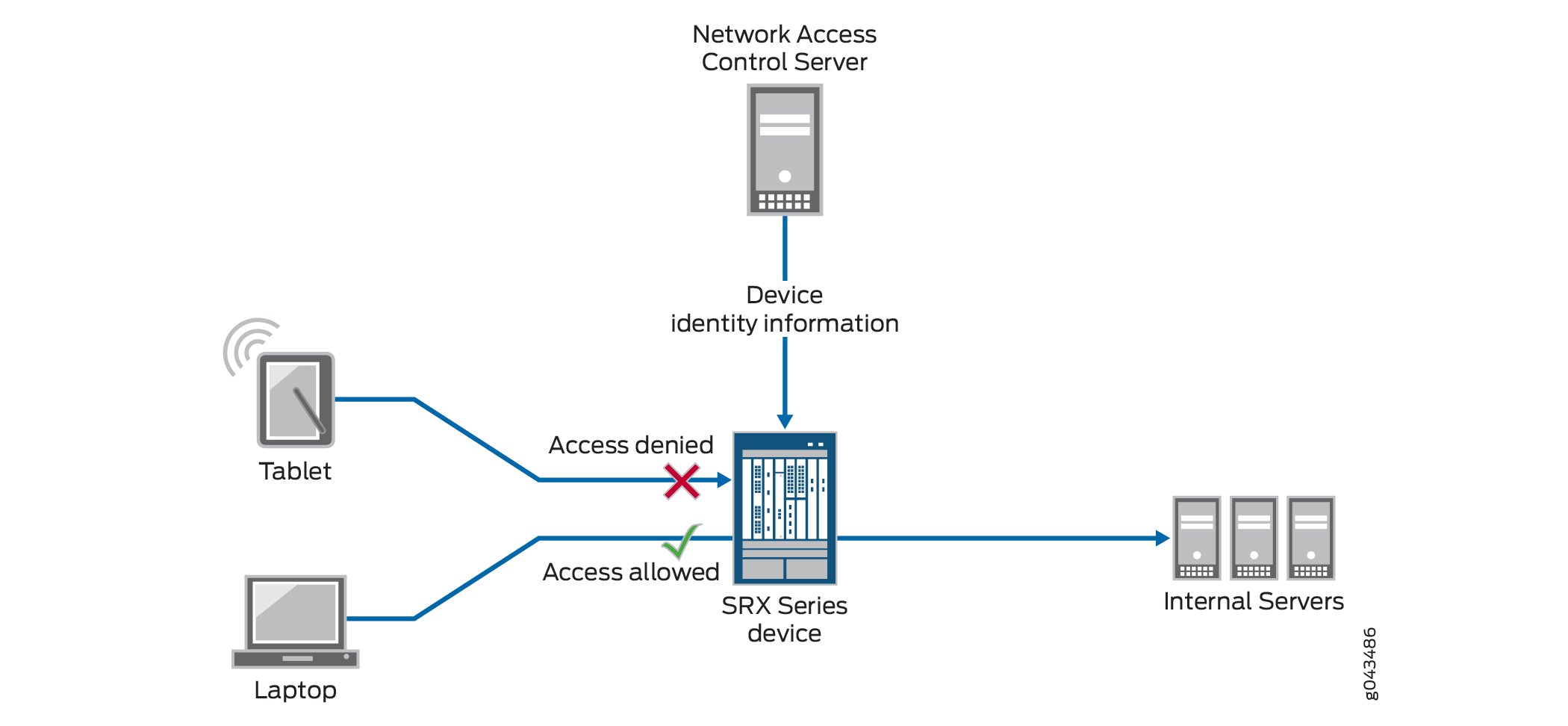
XML Web API Implementation on Firewall
The RESTful Web services API enables you to send the device identity information to the firewall in a formal XML structure. It allows your NAC solution to integrate with the device and efficiently send the device information to it. You must adhere to the formal structure and restrictions in sending information to the device using the API.
Ensure the Integrity of Data Sent from NAC Service to the Firewall
The following requirements ensure that the data sent from the NAC service is not compromised:
-
The API implementation is restricted to processing only HTTP/HTTPS POST requests. Any other type of request that it receives generates an error message.
-
The API daemon analyzes and processes HTTP/HTTPS requests from only the following dedicated URL:
/api/userfw/v1/post-entry
-
The HTTP/HTTPS content that your NAC solution posts to the firewall must be consistently formatted correctly. The correct XML format indicates a lack of compromise, and it ensures that user identity information is not lost.
Data Size Restrictions and Other Constraints
The following data size restrictions and limitations apply to the data posted to the firewall:
-
The NAC authentication system must control the size of the data that it posts. Otherwise, the Web API daemon is unable to process it. The Web API daemon can process a maximum of 2 megabytes of data.
-
The following limitations apply to XML data for role and device posture information. The Web API daemon discards XML data sent to it that exceeds these amounts (that is, the overflow data):
-
The device can process a maximum of 209 roles.
-
The device supports only one type of posture with six possible posture tokens, or values. Identity information for an individual user can have only one posture token.
-
User Identity Information in the Session Log File
The Active Directory as identity source allows you to configure the system to write to the session log the user’s identity by user name or group name without having to use the source identity (source-identity) tuple in the security policy. Knowing the user’s identity by name, as written to the log, not just by the IP address of the user’s device, gives you clearer visibility into their activity and allows you to resolve security problems faster and more easily. Relying on the source zone (from-zone) to trigger user identity logging rather than on the source identity widens the scope of users whose source identity is logged.
For more information, see Example: Configure User Identity Information to Session Log Based On Source Zone.
Typically, for each security policy, you must specify in the policy the source and destination IP addresses and the zones against which traffic is matched. You must also specify an application that the traffic is matched to. If traffic matches these criteria, then the security policy’s action is applied to the traffic issued from the user’s device. However, no user identity information is written to the session log.
Optionally, instead of relying exclusively on the IP address of the user’s device to identify the source of the traffic, you can specify the user identity—that is, the user name or the group name—in the source-identity tuple of a security policy. This approach gives you greater control over resource access by narrowing down application of the security policy’s actions to a single, identified user or a group of users, if other security policy matching conditions are met. However, use of the source-identity tuple constrains application of the policy to traffic from a single user or user group.
It may happen that you want the system to write to the session log the user identity for all users from whom traffic originated based on the zone to which they belong (from-zone). In this case, you do not want to narrow the traffic match and security policy application to a single user or a user group, which configuring the source-identity tuple would do.
The zone-based user identity feature allows you to direct the system to write to the log user identity information for any user who belongs to a zone that is configured with the source-identity-log statement when that zone is used as the source zone in a matching security policy.
For the source-identity-log feature to take effect, you must also configure logging of the session initialize (session-init) and session end (session-close) events as part of the security policy’s actions.
Table 8 identifies the platforms that support this feature.
|
Supported Firewall Platforms |
|---|
|
SRX320 |
|
SRX380 |
|
SRX1500 series |
Active Directory as Identity Source Authentication Table
The Active Directory as identity source will manage up to 2048 sessions for each user for whom there is a user identity and authentication entry in the authentication table. There might be additional sessions associated with a user beyond the 2048 supported sessions, but they are not managed by Active Directory as identity source. When an authentication entry in an authentication table is deleted, Active Directory as identity source only closes sessions that are associated with that entry. It will not close sessions that it does not manage.
Table 9 lists Active Directory as identity source authentication table device support that depends on the Junos OS release in your installation.
|
Devices |
Identity Source Authentication Table Entries |
Domains |
Controllers |
|---|---|---|---|
|
SRX300, SRX320 |
500 |
1 |
5 |
|
SRX340, SRX345, SRX380 |
1000 |
1 |
5 |
|
SRX1500, SRX1600, SRX2300, SRX4120 |
20,000 |
2 |
10 |
|
SRX4000 line |
50,000 |
2 |
10 |
|
SRX5000 line |
The user entries are as follows:
|
2 |
10 |
|
vSRX Virtual Firewall (2 vCPUs and 4 GB vRAM, 5 vCPUs and 8 GB vRAM ) |
5000 |
2 |
10 |
|
vSRX Virtual Firewall (9 vCPUs and 16 GB vRAM, 17 vCPUs and 32 GB vRAM ) |
10,000 |
2 |
10 |
|
NFX150 |
500 |
1 |
5 |
Active Directory as Identity Source Timeout Setting
Here timeout setting refers to firewall authentication forced timeout as it applies to active directory authentication entries for users who authenticate through captive portal.
When a user authenticates through captive portal, an authentication table entry is generated for that user based on the information that the firewall obtains from the firewall authentication module. At that point, the default traffic-based authentication timeout logic is applied to the entry.
As an administrator, it is important for you to have control over how long non-domain users who authenticate through captive portal remain authenticated. The timeout feature gives you that control. Use of it ensures that non-domain users do not remain authenticated indefinitely. For example, assume that the flow of traffic is continuous to and from the device of a non-domain user authenticated through captive portal. Given the behavior of the default traffic-based authentication timeout, the non-domain user would remain authenticated indefinitely.
When the timeout value is configured, it is used in conjunction with the traffic-based timeout logic. Here is how timeout settings affect active directory authentication entries for users authenticated through captive portal. In all of the following instances, an authentication entry was generated for a user based on firewall authentication information after the user authenticated through captive portal.
-
The timeout is set for 3 hours.
Traffic continues to be received and generated by a device associated with an authentication entry for a user. After 3 hours the authentication entry expires, although at that time there are sessions anchored in Packet Forwarding Engine for the authentication entry.
-
If set, the timeout has no effect.
An authentication entry does not have sessions anchored to it. It expires after the time set for the authentication entry timeout, for example, 30 minutes.
-
The timeout configuration is deleted.
Timeout has no effect on new authentication entries. Timeout remains enforced for existing authentication entries to which it applied before it was deleted. That is, for those authentication entries, the original timeout setting remains in effect.
-
The timeout configuration setting is changed.
The new time-out setting is applied to new incoming authentication entries. Existing entries keep the original, former setting.
-
The timeout is set to 0, disabling it.
If the timeout is set to a new value, that value is assigned to all incoming authentication entries. There is no timeout setting for existing authentication entries.
-
The timeout value is not configured.
-
The firewall generates an authentication entry for a user. The default traffic-based timeout logic is applied to the authentication entry.
-
The active directory timeout value is configured for 50 minutes. A traffic-based timeout of 50 minutes is applied to an authentication entry.
-
The active directory timeout is not configured. The default traffic-based timeout of 30 minutes is applied to an authentication entry.
-
Platform-Specific Active Directory as Identity Source Behavior
Use Feature Explorer to confirm platform and release support for Active Directory as identity source.
Use the following table to review platform-specific behaviors for your platform:
Platform-Specific WMIC Behavior
| Platform | Difference |
|---|---|
| SRX Series Firewall |
|
Platform-Specific Probe Rate Behavior
| Platform | Difference |
|---|---|
| SRX Series Firewall |
|
