TWAMP ALG
The Two-Way Active Measurement Protocol (TWAMP) is an open protocol for measuring network performance between any two devices in a network that supports the protocols in the TWAMP framework. The TWAMP Application Layer Gateway (ALG) extracts the IP addresses and the port details from messages between the control client and the TWAMP server and performs the IP address translation and gate opening to permit test sessions.
Understanding the Two-Way Active Measurement Protocol (TWAMP) Application Layer Gateway (ALG)
The Two-Way Active Measurement Protocol (TWAMP) is an open protocol for measuring network performance between any two devices in a network that supports the protocols in the TWAMP framework.
Starting from Junos OS Release 18.2R1, the TWAMP ALG is supported to enable the TWAMP data traffic to pass through the NFX Series or SRX Series Firewall without needing a predefined policy permission.
An Application Layer Gateway (ALG) is a software component that is designed to manage the specific protocols such as Session Initiation Protocol (SIP) or FTP on Juniper Networks devices running Junos OS. The ALG module is responsible for application layer aware packet processing.
The TWAMP ALG is located between the control client and the TWAMP server. The TWAMP ALG extracts the IP addresses and the port details from messages between the control client and the TWAMP server and performs the IP address translation and gate opening to permit test sessions. The TWAMP ALG performs the following functions:
-
Decoding all the TWAMP control messages.
-
Performing the TWAMP message sanity checks and decoding.
-
Performing the IP address translation when the device is configured with NAT.
Understanding TWAMP ALG
The TWAMP consists of the following inter-related protocols:
-
The TWAMP-Control is used to initiate, start and stop the test sessions between the control client and the TWAMP server.
-
The TWAMP-Test is used to exchange the test packets between the session sender and the session reflector.
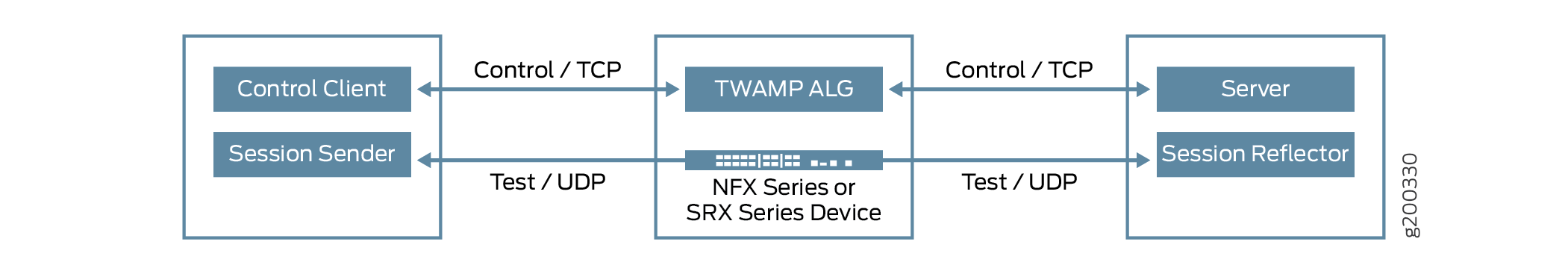
As shown in Figure 1, the control client initiates all requested test sessions with the TWAMP server through control connection. Meantime, the TWAMP ALG extracts the IP addresses and the port details in the messages from both sides to open a pinhole to permit the test sessions. During this stage, the TWAMP ALG might bypass the packets if the TWAMP server and the TWAMP client support unauthenticated mode.
In this case, the session sender and the reflector can exchange the test packets according to the TWAMP-Test protocol for each active test session.
Limitations for TWAMP ALG
The following are the limitations for the TWAMP ALG:
-
For the TWAMP connections, the TWAMP client and the TWAMP server must re-initiate a new control connection for test in case of failover.
-
During the control connection negotiation, if the servers rejects the client request, the client or the server must close the connection.
-
The TWAMP ALG has a timeout period of four seconds to establish the session.
-
The TWAMP ALG requires that the sender address, receiver address, and the header destination IP from the same interface to translate the IP address in the payload.
See Also
Enabling the Two-Way Active Measurement Protocol (TWAMP) Application Layer Gateway (ALG)
The Application Layer Gateway (ALG) Two-Way Active Measurement Protocol (TWAMP) is supported to enable the TWAMP data traffic to pass through the NFX Series or SRX Series Firewall without needing a predefined policy permission. By default, the ALG TWAMP is disabled.
To enable the TWAMP ALG and traceoptions:
Use the show security alg status command to verify
the status of the TWAMP ALG.
user@host> show security alg status DNS : Enabled FTP : Enabled H323 : Disabled MGCP : Disabled MSRPC : Enabled PPTP : Enabled RSH : Disabled RTSP : Disabled SCCP : Disabled SIP : Disabled SQL : Disabled SUNRPC : Enabled TALK : Enabled TFTP : Enabled IKE-ESP : Disabled TWAMP : Disabled
See Also
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
