System behavior differs depending on whether you select remote
authentication only or remote-local authentication as the authentication
mode for Junos Space Platform. Differences occur when a remote authentication
server does not authenticate a user. There are also differences in
the source of authorization depending on what answer the remote server
returns.
Figure 1 shows the
decision tree underlying system behavior when either remote authentication
only or remote-local authentication is chosen and a remote authentication
server accepts the user.
Figure 1: Remote Authentication
Server Accepts User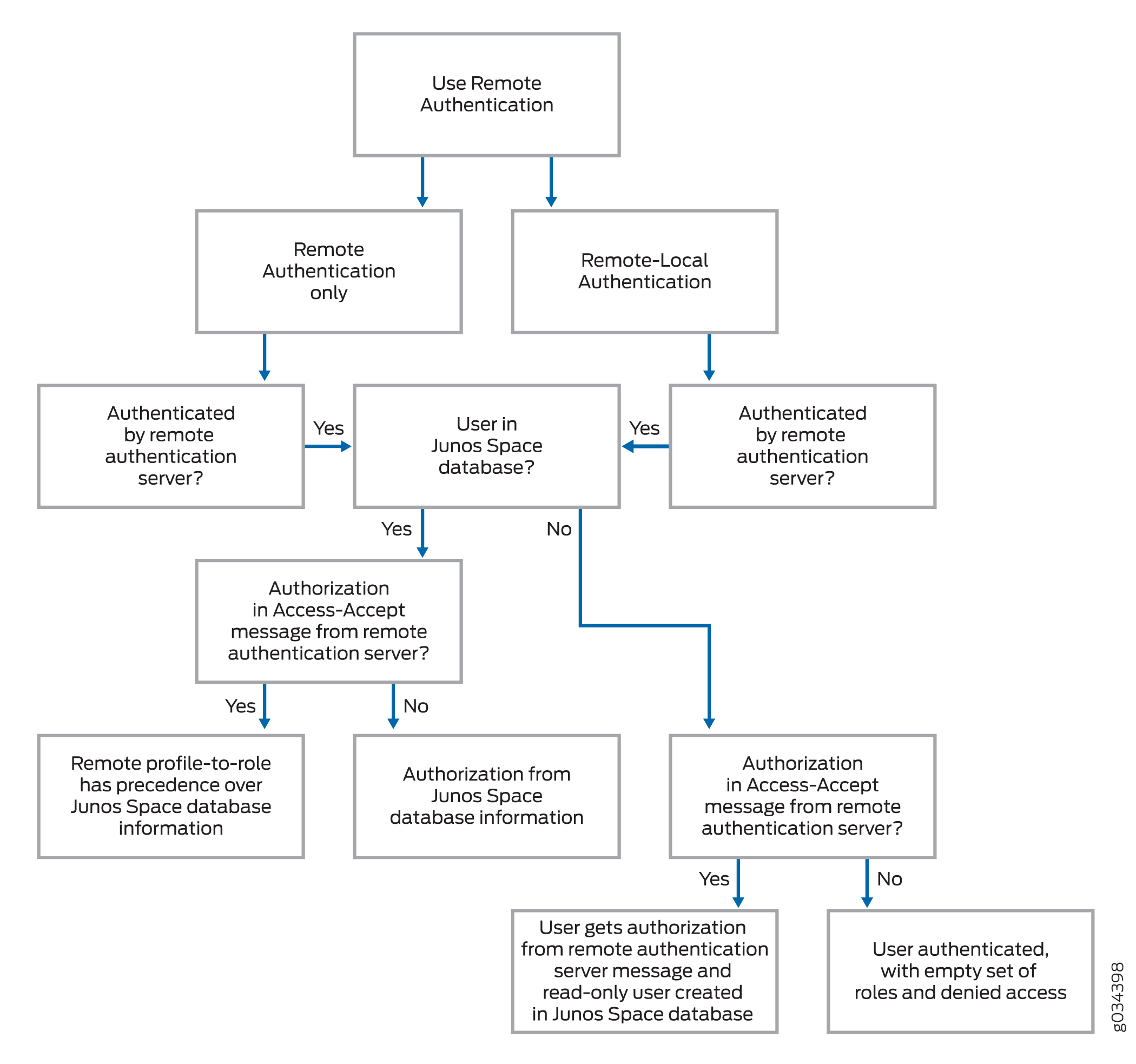
Figure 2 shows the
decision tree when a remote authentication server either rejects the
user or does not respond at all.
Figure 2: Remote Authentication
Server Not Reachable or Rejects User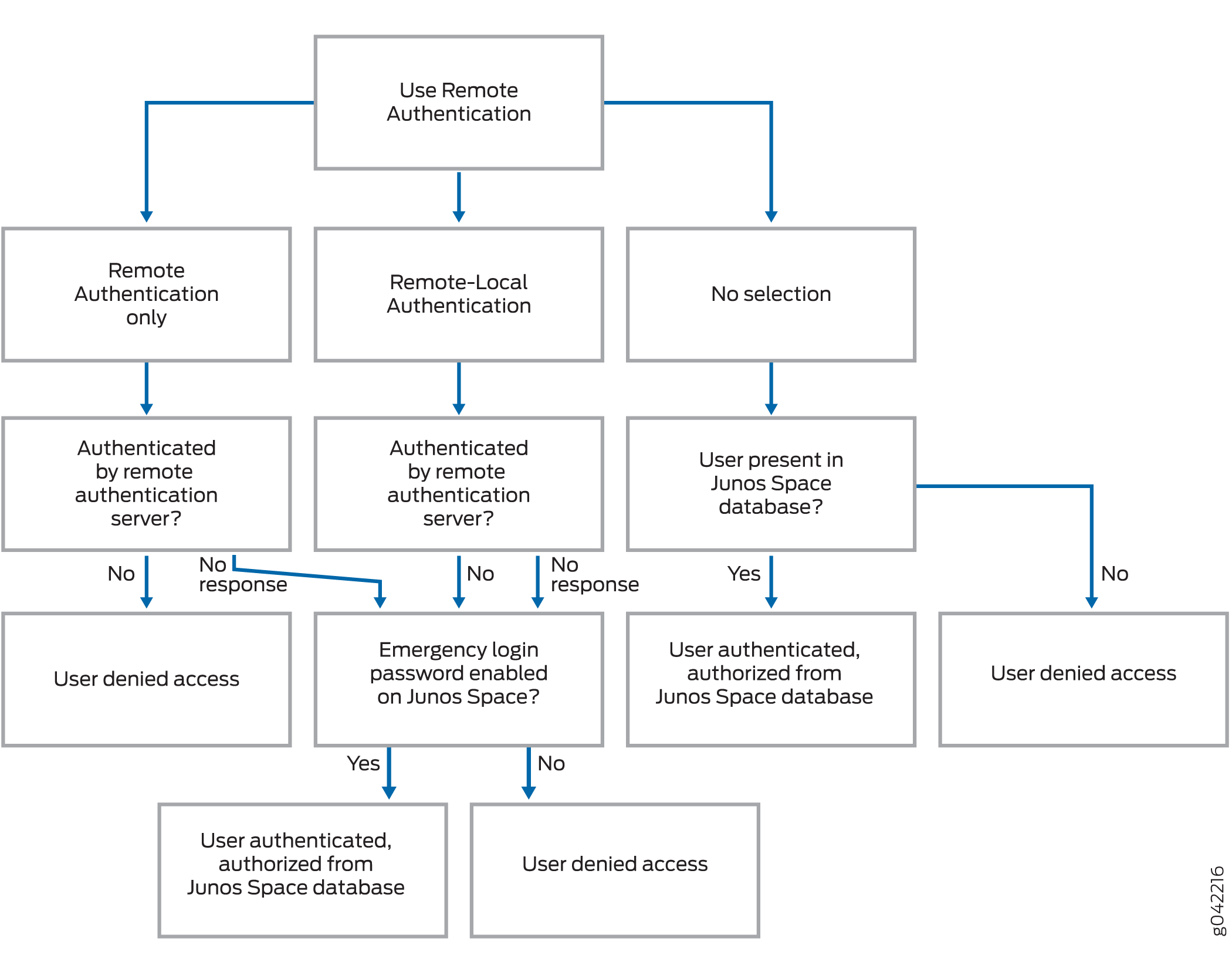
The following sections describe the login behavior when remote
authentication only or remote-local authentication mode is enabled.
Note: When remote users log in with usernames that contain an
@ symbol or a backslash (\) character, Junos Space Platform ignores
the part of the username that follows the @ symbol or the part that
precedes the backslash character and authenticates with the rest of
the username. For example, if a remote user uses abc@domain, abc@domain.com, or domain\abc as the username, Junos Space Platform uses only abc to authenticate the user. If there is an entry for abc in the database, the corresponding remote profile is applied to
the user. If the database does not have an entry that corresponds
to the username, abc in the given example, Junos
Space Platform creates a read-only user account with the name abc
and assigns a remote profile.
Login Behavior
with Remote Authentication Only Enabled
Table 1 lists the
various scenarios and the authentication and authorization behavior
for each scenario when remote authentication only mode is enabled.
Table 1: Login Behavior with
Remote Authentication Only EnabledScenario
|
Login Behavior
|
|---|
User logs in with the correct credentials
|
If the user’s password is on the remote server and
there is a corresponding remote profile in Junos Space Platform, the
user logs in with the roles assigned by the remote profile.
If the user’s password is on the remote server but
there is no equivalent remote profile in Junos Space Platform, the
user logs in with roles assigned from the Junos Space database user
information if the corresponding user account exists in the Junos
Space database. If there is no equivalent remote profile or user account
in Junos Space Platform, the user is denied access.
If the first remote authentication server is present,
only that server is contacted and login success or failure solely
depends on the password stored there. If the first authentication
server is not reachable, the other servers are contacted in the specified
order. If no authentication server is reachable, the local password
in the Junos Space Platform database is checked. If the emergency
password is configured in Junos Space and the credentials match, the
user logs in successfully with roles assigned from the Junos Space
database user information. Otherwise, the user is denied access.
Note: For remote authentication and authorization, most users
do not need a local password. The local password in this case is only
for emergency purposes, when the remote authentication servers are
unreachable.
|
User logs in with incorrect credentials or the user does
not exist on the remote authentication server
|
Access to Junos Space Platform is denied.
Note: Authentication servers, for security purposes, do not
distinguish between these two cases (that is, a user is logging in
with incorrect credentials or a user does not exist on the remote
authentication server). Therefore, Junos Space Platform must always
treat these type of logins as an authentication failure.
If no authentication servers are reachable, Junos Space
Platform tries the local password. If the emergency password is configured
in Junos Space and the credentials match, the user logs in successfully
with roles assigned from the Junos Space database user information.
Otherwise, the user is denied access.
|
User attempts to log in when the remote authentication
server is configured for Challenge/Response
|
If the remote authentication server indicates that a challenge
is required, it provides the challenge question. Junos Space Platform
displays the challenge question to the user on the Junos Space login
page and waits for the user’s response.
If the challenge question is answered correctly, it is
possible that the authentication server may pose additional challenge
questions.
If the challenge question is answered incorrectly, it
is possible that the authentication server may rechallenge the user
with the same challenge question, use a different challenge question,
or fail the login attempt completely. The remote authentication server
configuration determines the behavior.
If the final challenge question is answered correctly,
the user logs in successfully.
|
Login Behavior with Remote-Local Authentication Enabled
Table 2 lists the
various scenarios and the authentication and authorization behavior
for each scenario when the remote-local authentication mode is enabled.
Table 2: Login Behavior with
Remote-Local Authentication EnabledScenario
|
Login Behavior
|
|---|
User logs in with the correct credentials
|
If the user’s password is on the remote server and
there is a corresponding remote profile in Junos Space Platform, the
user logs in with the roles assigned by the remote profile.
If the user’s password is on the remote server,
but there is no equivalent remote profile in Junos Space database,
then Junos Space Platform checks whether the user account exists in
the Junos Space database. If the user account exists, the user logs
in successfully with the roles assigned from the Junos Space database
user information. Otherwise, the user is denied access.
If the remote servers are not reachable, Junos Space Platform
tries to authenticate the user locally. If a Junos Space Platform
user account and local password exist, and the credentials match,
the user logs in successfully with the roles assigned from the Junos
Space database user information. Otherwise, the user is denied access.
|
User logs in with incorrect credentials or the user does
not exist on the remote authentication server
|
Junos Space Platform checks the remote authentication
servers first. If authentication fails or if a server is not reachable,
Junos Space Platform tries to authenticate the user locally. If a
Junos Space Platform user account and local password exist, and the
credentials match, the user logs in successfully with the roles assigned
from the Junos Space database user information. Otherwise, the user
is denied access.
|
User attempts to log in when the remote authentication
server is configured for Challenge/Response
|
If the remote authentication server indicates that a challenge
is required, it provides the challenge question. Junos Space Platform
displays the challenge question to the user on the Junos Space login
page and waits for the user’s response.
If the challenge question is answered correctly, it is
possible that the authentication server may pose additional challenge
questions.
If the challenge question is answered incorrectly, it
is possible that the authentication server may rechallenge the user
with the same challenge question, use a different challenge question,
or fail the login attempt completely. The remote authentication server
configuration determines the behavior.
If the final challenge question is answered correctly,
the user logs in successfully.
|


