Firewall Rule Event Counts of Check Point Devices
SUMMARY In JSA Risk Manager, you can monitor the firewall rule event counts of your Check Point devices by integrating with the Check Point SMS. You can view these rule interactions in JSA Risk Manager, and use rule reports to manage the rule policy effectiveness of your network.
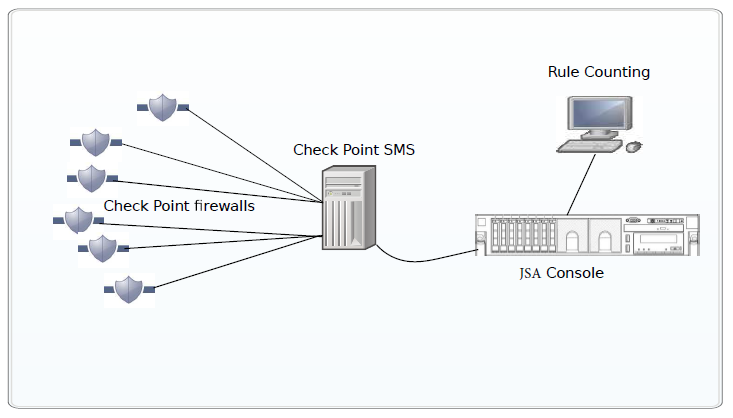
In the following image, JSA receives and processes rule event logs from Check Point firewall devices through the SMS.
Scenario - Implementing Check Point firewall rule monitoring in JSA
You are a network systems administrator with responsibility for network security in an organization that uses Check Point to implement its network security policies. The network includes several Check Point firewalls that are managed from a Check Point Security Management Server (SMS).
You want to view reports on rule usage daily so that you have more visibility on your rule implementation.
You need to configure a connection between your Check Point SMS and JSA so that JSA receives rule event logs from Check Point firewall devices. JSA processes this rule event log information and displays rule event information for all devices that are managed by Check Point firewalls. From the JSA rules table, you can analyze the usage and effectiveness of the firewall rules by monitoring event counts, and fine-tune your rules for optimal performance.
Use the rule information to do the following tasks:
-
View most and least used rules.
-
Assess the practicality of rules that are triggered infrequently.
-
View rules that might be blocking network access unnecessarily.
-
View rules that are triggered excessively, and place a load on your network bandwidth.
-
View detailed events.
-
Schedule reports.
