Suspect Content Descriptions Derived from X-Force
The IBM X-Force signature library includes descriptions for thousands of signatures.
At the enriched and advanced inspection level, Network Insights can detect suspicious content by using the X-Force signature library.
The signatures and issues are reported as suspect content on the Network Activity tab. The format for suspect content description depends on the information that is available.
-
If the name of the detected issue ID is known, the suspect content description appears in the XForceIssue <Name> format.
For example, a named issue might appear as XForceIssue Land_Attack.
-
If the name cannot be resolved for the detected issue, the issue ID appears in the suspect content description.
For example, if the name cannot be identified, the issue might appear as XForceIssueID 2000001.
To learn more about the suspicious content, some fields on the Flow information window include direct links to view more information in X-Force Exchange.
To view a complete list of issues that are supported for the current deployment, view the /opt/ibm/xforce/metadata/issues.csv file on the Network Insights appliance.
Suspect content descriptions in rules
For signatures that present a greater risk to your environment, create rules and offense notifications to help you detect and investigate these threats.
To determine which signatures to prioritize in your own environment, consider the following information:
-
The use cases that are most relevant to your own environment.
-
The signature priority as determined by IBM X-Force
-
The moderate, aggressive, and paranoid issue policies that are defined in the /opt/ibm/xforce/metadata directory after the upgrade is complete.
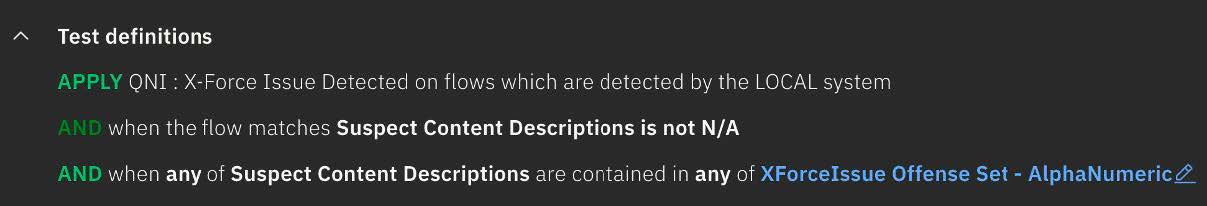
When you use suspect content descriptions in rules, be specific with the signatures that you want to detect. This image shows an example rule that uses a suspect content description in the test criteria:
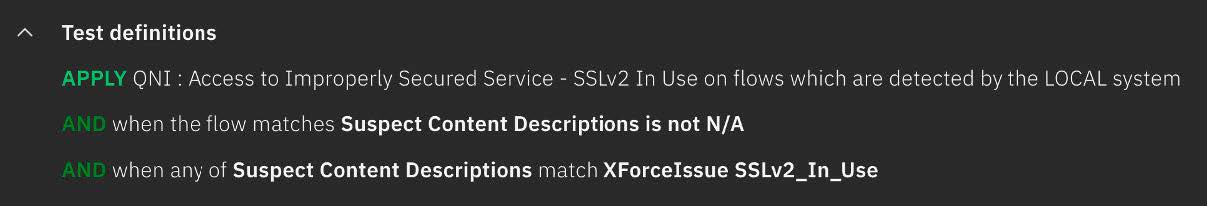
If you want to detect multiple signatures with a single rule, consider using a reference set.