ON THIS PAGE
JSA Architecture Overview
When you plan or create your JSA deployment, it's helpful to have a good awareness of JSA architecture to assess how JSA components might function in your network, and then to plan and create your JSA deployment.
JSA collects, processes, aggregates, and stores network data in real time. JSA uses that data to manage network security by providing real-time information and monitoring, alerts and offenses, and responses to network threats.
JSA is a modular architecture that provides real-time visibility of your IT infrastructure, which you can use for threat detection and prioritization. You can scale JSA to meet your log and flow collection, and analysis needs. You can add integrated modules to your JSA platform, such as JSA Risk Manager, and JSA Vulnerability Manager.
The operation of the JSA security intelligence platform consists of three layers, and applies to any JSA deployment structure, regardless of its size and complexity. The following diagram shows the layers that make up the JSA architecture.
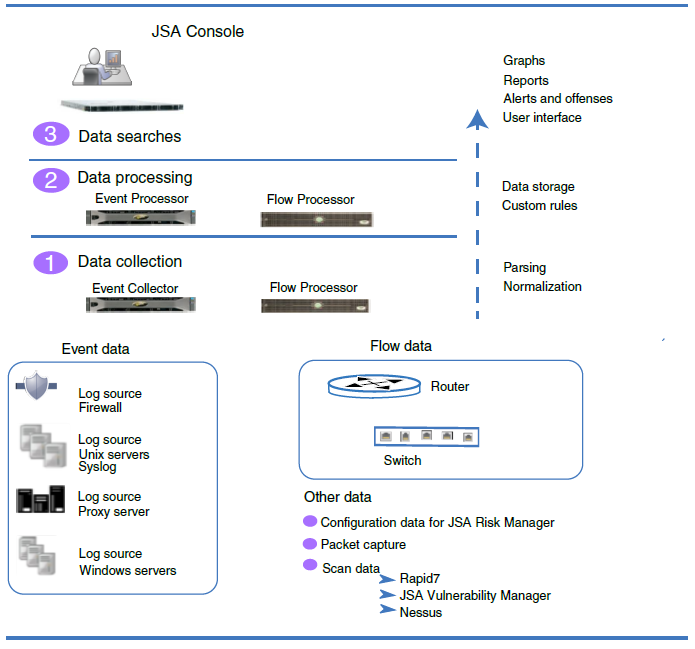
The JSA architecture functions the same way regardless of the size or number of components in a deployment. The following three layers that are represented in the diagram represent the core functionality of any JSA system.
Data Collection
Data collection is the first layer, where data such as events or flows is collected from your network. The All-in-One appliance can be used to collect the data directly from your network or you can use collectors such as JSA Event Collectors or JSA Flow Processor to collect event or flow data. The data is parsed and normalized before it passed to the processing layer. When the raw data is parsed, it is normalized to present it in a structured and usable format.
The core functionality of JSA is focused on event data collection, and flow collection.
Event data represents events that occur at a point in time in the user's environment such as user logins, email, VPN connections, firewall denys, proxy connections, and any other events that you might want to log in your device logs.
Flow data is network activity information or session information between two hosts on a network, which JSA translates in to flow records. JSA translates or normalizes raw data in to IP addresses, ports, byte and packet counts, and other information into flow records, which effectively represents a session between two hosts.
Data Processing
After data collection, the second layer or data processing layer is where event data and flow data are run through the Custom Rules Engine (CRE), which generates offenses and alerts, and then the data is written to storage.
Event data, and flow data can be processed by an All-in-One appliance without the need for adding Event Processors or Flow Processors. If the processing capacity of the All-in-One appliance is exceeded, then you might need to add Event Processors, Flow Processors or any other processing appliance to handle the additional requirements. You might also need more storage capacity, which can be handled by adding Data Nodes.
Other features such as JSA Risk Manager, JSA Vulnerability Manager collect different types of data and provide more functions.
JSA Risk Manager collects network infrastructure configuration, and provides a map of your network topology. You can use the data to manage risk by simulating various network scenarios through altering configurations and implementing rules in your network.
Use JSA Vulnerability Manager to scan your network and process the vulnerability data or manage the vulnerability data that is collected from other scanners such as Nessus, and Rapid7. The vulnerability data that is collected is used to identify various security risks in your network.
Data Searches
In the third or top layer, data that is collected and processed by JSA is available to users for searches, analysis, reporting, and alerts or offense investigation. Users can search, and manage the security admin tasks for their network from the user interface on the JSA console.
In an All-in-One system, all data is collected, processed, and stored on the All-in-One appliance.
In distributed environments, the JSA console does not perform event and flow processing, or storage. Instead, the JSA console is used primarily as the user interface where users can use it for searches, reports, alerts, and investigations.
