ON THIS PAGE
JIMS Architecture, Workflow and Functionalities
SUMMARY Read this section to learn about the JIMS workflow, architecture, and functionalities.
JIMS Workflow
Juniper Identity Management Service (JIMS) enables you to apply policies on the SRX Series Firewalls (including Juniper Networks® vSRX Virtual Firewall Virtual Firewall) based on user identity information such as usernames and user groups in addition to IP addresses. The service maps IP addresses to users and devices based on groups membership and provides this mapping information to the SRX Series Firewalls. (User groups for the SRX Series Firewalls are also known as user roles.) SRX Series Firewalls use the mapping information to generate entries for their authentication tables that you can use to enforce user/device-based security policy control based on group membership.
To support identity-aware firewall policies, JIMS performs these steps:
-
Communicates with Microsoft Active Directory to retrieve the username-to-group mapping information and uses this information to identify the group to which each user belongs.
-
Communicates with the Microsoft Domain Controllers or Microsoft Exchange Servers in the Active Directory domains to collect event log information, which contains the IP address-to-username mapping information. The service uses the mapping information to determine the IP addresses of users in Active Directory and Exchange Servers.
-
Stores IP address, username, and group-relationship information in its cache. The service then generates a report using the stored information and makes it available to the enforcement points (SRX Series Firewalls).
-
Generates authentication entries which are used to enforce device and user-based or group-based access control applied in the rule base for the SRX Series firewalls.
Figure 1: JIMS Architecture
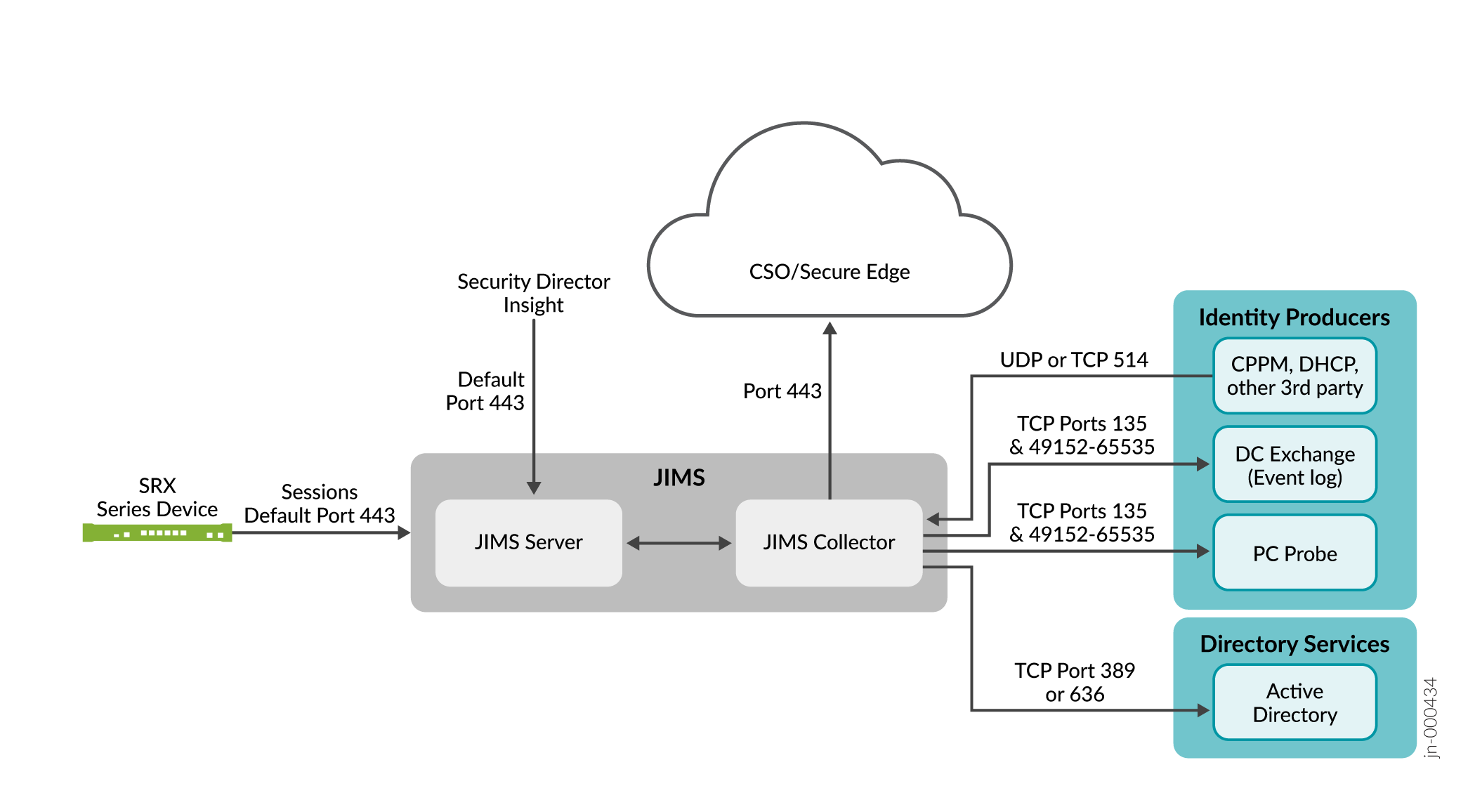
The JIMS collector uses the Active Directory to monitor state changes of users, devices, and group memberships and collects this information. After each instance of data collection, the collector automatically sends this data to the JIMS server. This data is required to update the enforcement points.
The JIMS collector performs the following actions:
-
It connects to:
-
Directory services (Microsoft Active Directory) using Lightweight Directory Access Protocol (LDAP) over (TCP port 389) or LDAP over Secure Sockets Layer (LDAPS) over (TCP port 636).
-
Identity providers (Microsoft Domain Controllers or Exchange Server) using Microsoft Remote Procedure Call (RPC) over (TCP port 135 and dynamic ports 49152 through 65535).
Note:Microsoft Exchange Server is also known as Exchange Server.
-
Identity providers (ClearPass Policy Manager or CPPM, Dynamic Host Configuration Protocol or DHCP, and syslog server) using internal communication. The syslog server listens to TCP and UDP ports 514 for incoming syslog messages.
-
An identity provider (PC probe) using internal communication. PC probe sends outbound Windows Management Instrumentation (WMI) request to devices using TCP port 135 and dynamic ports 49152 through 65535.
-
-
Sends data to JIMS servers using Transport Layer Security (TLS) over TCP port 443. (TCP ports are configurable.)
Enforcement points (SRX Series Firewalls) use TLS over TCP ports 443 and 591 (default port) to send queries to the JIMS server.
JIMS Architecture
JIMS Service Types
The JIMS consists of two services:
-
Collector—Maps users and devices to IP addresses.
-
Server—Serves the enforcement points with the mapping information.
Currently, these two services run on the same server as a single application.
JIMS Server
The JIMS server provides all your enforcement points (SRX Series firewalls) with high-scale identity data without consuming unnecessary CPU cycles on your directory services. The server provides the identity information in a JIMS report that includes user, device, IP address, and group mapping information. Each SRX Series Firewall uses this information to make policy decisions in the user firewall feature.
JIMS Collector
The JIMS collector communicates with your Active Directory to collect user, device, and group membership information. The collector also maps each active user and device to an IP address.
The collector can also connect to a syslog server and act on incoming data from a different system of interest, such as network access control (NAC), Dynamic Host Configuration Protocol (DHCP), VPN gateways, or a captive portal to record login and logout events .
Identity Data Collection
JIMS is scalable and can take over user identity data collection from Microsoft Active Directory, Domain Controllers, Microsoft Exchange Servers, and syslog servers. JIMS serves as a single centralized data collection source for the SRX Series Firewalls.
The service generates reports that contain the IP address, username, device, and group relationship information that the service collects from the user-identity data sources.
JIMS uses the following directory services and identity producers to collect identity data.
-
Directory Services—Data Collection from Microsoft Active Directory
JIMS communicates with each Active Directory to collect group information for users and devices. The service queries each configured Active Directory for user and device information. It queries the appropriate user information source each time it receives a login event for a user.
-
Identity Producers—Data Collection from Event Log Sources
JIMS connects to event log sources to collect user and device status events and provides IP address-to-username mapping information to the SRX Series Firewalls. For user login events, JIMS collects the domain name, username, and IP address. For device login events, JIMS collects the domain name, machine name, and IP address.
Event log sources can be one or more Active Directory Domain Controllers or one or more Exchange Servers. JIMS gives you the option to configure event log sources that can be a combination of the Active Directory Domain Controllers and Exchange Servers.
-
Identity Producers—Data Collection from Syslog Sources
JIMS allows syslog clients to send event data such as user and device information from an event source such as a DHCP server. You have to define the IP address and port of the remote syslog client to which the JIMS server permits a connection. You must configure the JIMS server to collect syslog data whenever it detects a logout event, login event, or a change in data value. The JIMS collector extracts the device, username, and IP address information from the syslog messages and maps this information to group memberships. The collector then turns the mapping information into JIMS reports.
-
Identity Producers—Data Collection Using Domain PC Probing
PC Probe
To initiate a domain PC probe of a device in a customer’s domain, JIMS needs administrative credentials to access the device. For a PC probe to a new IP address, JIMS uses each set of configured credentials in the order in which they appear in the list.
Domain PC probing acts as a supplement to event log reading. When a user is logged in to a domain, the event log contains all the information that JIMS requires. When IP address-to-username mapping information is not available from the event log, JIMS initiates a domain PC probe to the device to get the username and domain of the current active user. You can use domain PC probes to also determine a device status after its logged-in state has expired. When using a PC probe, you should ensure that your firewall blocks outgoing PC probe requests to the Internet and potentially spoofed IP addresses by blocking outbound Windows Management Instrumentation (WMI) packets from your JIMS servers.
Enforcement Points
When a previous batch query fails to retrieve IP address-to-username mapping information, enforcement points (SRX Series firewalls) again send batch queries (reports) or IP queries to extract information about users, devices, and group membership from the JIMS server. When the JIMS server does not have the IP address about which an endpoint has queried, the server requests the JIMS collector for this data. The JIMS collector queries the Domain Controller and the Exchange Server for the corresponding record. When such a record does not exist, JIMS performs a PC probe to the IP address. You can run a PC probe only on Microsoft Windows.
