Configure Secure Local Branch Connectivity
Now that you've verified the LAN/WAN connectivity, you're ready to use the Junos CLI to deploy VLANs and related policies to secure LAN and WAN connectivity.
SRX platforms are all about security. It's what they do. Securing local and Internet connectivity in this modern age is critically important. We'll show you how to configure the SRX to meet your security needs.
Configure VLANs and Security Policies
Local Branch Connectivity Goals
Figure 1 details the local branch office connectivity goals used in these procedures.
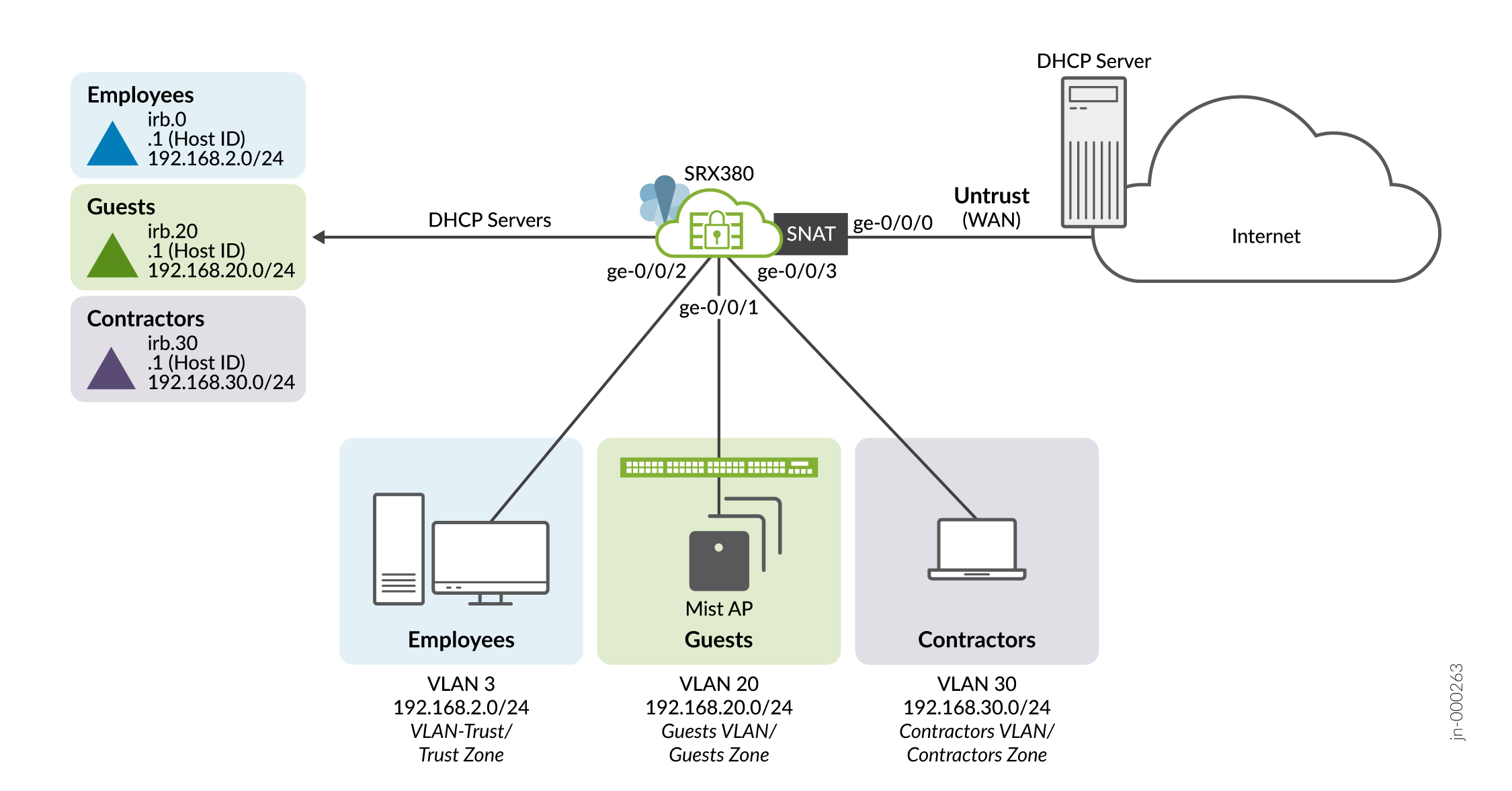
Here's how we'll achieve these goals:
- Place employees in the Trust VLAN (vlan-trust)/trust zone. Allow them full Internet access and the ability to initiate specific connectivity to devices in the contractors zone.
- The branch handles retail sales and provides free Wi-Fi to patrons. Place the guests VLAN in the guests zone and allow limited Internet access.
- Contractors are working on a new web-based business application in the local branch. Place the contractors in the contractors VLAN/zone and don't allow them Internet access. Contractors can't initiate communications to either the trust or guests zones.
The following table summarizes the VLAN connectivity requirements:
| VLAN ID | Name/Zone | Subnet | Internet Access? | Security Policy |
|---|---|---|---|---|
| 3 * | vlan-trust/trust * | 192.168.2.0/24 * | Full * |
|
| 20 | guests | 192.168.20.0/24 | HTTP and HTTPS only |
|
| 30 | contractors | 192.168.30.0/24 | No |
|
The entries in the table marked with an "*" for vlan-trust are already in place through the factory-default configuration. We told you this would be easy! All that is needed for the factory-default trust zone is to add a security policy that permits the specified protocols from the trust zone to the contractors zone.
Permit Trust to Contractors Zone Traffic
To meet the stated connectivity goals, create a security policy to allow specific traffic (HTTP/HTTPS and ping) from the trust zone to the contractors zone. As a security appliance, the SRX has a default deny-all policy for inter-zone traffic. In the factory-default configuration, traffic is permitted from the trust to untrust zones only.
set security policies from-zone trust to-zone contractors policy trust-to-contractors match source-address any set security policies from-zone trust to-zone contractors policy trust-to-contractors match destination-address any set security policies from-zone trust to-zone contractors policy trust-to-contractors match application junos-http set security policies from-zone trust to-zone contractors policy trust-to-contractors match application junos-https set security policies from-zone trust to-zone contractors policy trust-to-contractors match application junos-ping set security policies from-zone trust to-zone contractors policy trust-to-contractors then permit
In this example, we keep it simple and match on any source or destination IP
address. Here, we simply match on the source and destination zone for policy
control. For better security, consider defining address book entries for the
trust and contractors subnet,
which are 192.168.2.0/24 and 192.168.30.0/24 prefixes in this branch office.
With an address book entry, you can match on source-address
trust and destination-address
contractors.
Further, you can add host-specific address book entries to control the specific IP addresses that are allowed to communicate between zones. If you use a host-specific IP address in your policy, be sure you assign a static IP address to related hosts. If you recall, we use DHCP in this example. So, if a lease times out or a client machine reboots, the client machines will automatically be assigned a new IP address unless you've assigned static IP addresses to the related hosts.
Configure a Guests VLAN, Security Zone, and Security Policies
Let's get those guests up and running. After all, they have web shopping to do! At a high level, this task involves these key parts:
- Define the guest VLAN and associate it with one or more LAN interfaces
- Define the VLAN's integrated routing and bridging (IRB) interface
- Configure a DHCP server to assign IP addresses to members of the VLAN
- Define a security zone and policy in accordance with the connectivity needs for the VLAN
- Log in as root to
the
SRX device. You can use console or SSH access. Start the CLI, and enter
configuration
mode.
login: branch_SRX (ttyu0) root@branch_SRX% cli root@branch_SRX> configure Entering configuration mode [edit] root@branch_SRX#
- Define the guests VLAN and associate it with an IRB
interface. This IRB interface serves as the default gateway for the devices
on the
VLAN.
[edit] root@branch_SRX# set vlans guests vlan-id 20 root@branch_SRX# set vlans guests l3-interface irb.20
- Place the ge-0/0/1 interface into the guests VLAN. In the
default configuration, this interface, like most, belongs to the
trust VLAN. You begin by deleting the interface's
current VLAN association so you can replace it with the updated
guests
VLAN.
[edit] root@branch_SRX# delete interfaces ge-0/0/1 unit 0 root@branch_SRX# set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members guests
- Configure the IRB interface for the guests VLAN. This
step assigns an IP subnet to the VLAN. In this example, you match the VLAN
ID to the IRB unit number to make things easier to remember. This
association is for convenience only. You can use any unused unit number for
this
step.
[edit] root@branch_SRX# set interfaces irb unit 20 family inet address 192.168.20.1/24
- Configure the DHCP server for the guests VLAN. Note that
the VLAN's IRB interface is configured as the DHCP server interface. This
configuration assigns IP addresses from the specified range, and also
assigns the client a default route and a public DNS server address. The
default route points to the VLAN's IRB as the next hop for all non-local
(inter-VLAN and LAN to WAN)
traffic.
[edit] root@branch_SRX# set system services dhcp-local-server group GUEST-POOL interface irb.20 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet network 192.168.20.0/24 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet range GUEST-POOL-IP-RANGE low 192.168.20.10 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet range GUEST-POOL-IP-RANGE high 192.168.20.100 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet dhcp-attributes domain-name srx-branch.com root@branch_SRX# set access address-assignment pool GUEST-POOL family inet dhcp-attributes name-server 8.8.8.8 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet dhcp-attributes router 192.168.20.1
- Members of the guests VLAN are provided with Internet
access. Because the local branch is using local-use only RFC-1918 IP
addresses, Internet access requires that the SRX perform source NAT to the
WAN interface IP address. Only globally-routable IP addresses can be used
over the Internet. Here's how to define a source NAT policy for the
guests
VLAN:
[edit] root@branch_SRX# set security nat source rule-set guests-to-untrust from zone guests root@branch_SRX# set security nat source rule-set guests-to-untrust to zone untrust root@branch_SRX# set security nat source rule-set guests-to-untrust rule guest-nat-rule match source-address 0.0.0.0/0 root@branch_SRX# set security nat source rule-set guests-to-untrust rule guest-nat-rule then source-nat interface
- Almost done. Next, you create the guests security zone.
As part of this process, you place the related VLAN's IRB into the new zone.
Part of a zone's definition is to specify the protocols and services that
are allowed to flow from that zone to the SRX device's control plane.
For this example, you allow users in the guests VLAN to initiate DHCP and ping traffic to the local control plane. This allows the guest to request an IP address using DHCP, and to ping their VLAN's IRB for debugging purposes, while blocking all other services and protocols to the local host. As a result, users in the guest zone are blocked from initiating Telnet or SSH to the branch SRX. In contrast, users in the trust zone are allowed to initiate SSH connections to the SRX.
[edit] root@branch_SRX# set security zones security-zone guests interfaces irb.20 root@branch_SRX# set security zones security-zone guests host-inbound-traffic system-services dhcp root@branch_SRX# set security zones security-zone guests host-inbound-traffic system-services ping
- The last step is to define the security policies for the
guests VLAN. To keep the configuration statements
shorter, we "park" ourselves at the
[edit security policies]hierarchy. To limit Internet access, your policy provides support only for HTTP, HTTPS, DNS, and ping.[edit security policies ] root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match source-address any root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match destination-address any root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-http root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-https root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-ping root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-dns-udp root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust then permit
Quick Configurations
Guests VLAN Quick Configuration
Here's the complete configuration for defining the guests VLAN and its security policies in set format. To get up and running quickly, simply edit the configuration statements as needed for your environment and paste them into your SRX.
set vlans guests vlan-id 20 set vlans guests l3-interface irb.20 delete interfaces ge-0/0/1 unit 0 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members guests set interfaces irb unit 20 family inet address 192.168.20.1/24 set system services dhcp-local-server group GUEST-POOL interface irb.20 set access address-assignment pool GUEST-POOL family inet network 192.168.20.0/24 set access address-assignment pool GUEST-POOL family inet range GUEST-POOL---IP-RANGE low 192.168.20.10 set access address-assignment pool GUEST-POOL family inet range GUEST-POOL---IP-RANGE high 192.168.20.100 set access address-assignment pool GUEST-POOL family inet dhcp-attributes domain-name srx-branch.com set access address-assignment pool GUEST-POOL family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool GUEST-POOL family inet dhcp-attributes router 192.168.20.1 set security nat source rule-set guests-to-untrust from zone guests set security nat source rule-set guests-to-untrust to zone untrust set security nat source rule-set guests-to-untrust rule guest-nat-rule match source-address 0.0.0.0/0 set security nat source rule-set guests-to-untrust rule guest-nat-rule then source-nat interface set security zones security-zone guests interfaces irb.20 set security zones security-zone guests host-inbound-traffic system-services dhcp set security zones security-zone guests host-inbound-traffic system-services ping set security policies from-zone guests to-zone untrust policy guests-to-untrust match source-address any set security policies from-zone guests to-zone untrust policy guests-to-untrust match destination-address any set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-http set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-https set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-ping set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-dns-udp set security policies from-zone guests to-zone untrust policy guests-to-untrust then permit
Contractors VLAN Quick Configuration
The contractors VLAN and related security zone is similar to that detailed above for the guests VLAN. We save some paper by jumping straight to the Quick Configuration for the contractors VLAN.
The lack of security policy definition for the contractors zone is significant. With out an explicit policy, the default deny all policy is in full effect for any inter-zone traffic initiated from this zone! The result is that all traffic that initiates in the contractors zone is blocked from entering all other zones.
set vlans contractors vlan-id 30 set vlans contractors l3-interface irb.30 delete interfaces ge-0/0/3 unit 0 set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members contractors set interfaces irb unit 30 family inet address 192.168.30.1/24 set system services dhcp-local-server group CONTRACTORS-POOL interface irb.30 set access address-assignment pool CONTRACTORS-POOL family inet network 192.168.30.0/24 set access address-assignment pool CONTRACTORS-POOL family inet range CONTRACTORS-POOL-IP-RANGE low 192.168.30.10 set access address-assignment pool CONTRACTORS-POOL family inet range CONTRACTORS-POOL-IP-RANGE high 192.168.30.100 set access address-assignment pool CONTRACTORS-POOL family inet dhcp-attributes domain-name srx-branch.com set access address-assignment pool CONTRACTORS-POOL family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool CONTRACTORS-POOL family inet dhcp-attributes router 192.168.30.1 set security zones security-zone contractors interfaces irb.30 set security zones security-zone contractors host-inbound-traffic system-services dhcp set security zones security-zone contractors host-inbound-traffic system-services ping
Be sure to commit your configuration to activate the changes on the SRX device.
Results
The results of your secure VLAN configuration are displayed in Junos curly brace format. We've omitted the factory-default configuration from the below for brevity.
root@branch_SRX# [edit]
root@branch-srx# show interfaces irb
. . .
unit 20 {
family inet {
address 192.168.20.1/24;
}
}
unit 30 {
family inet {
address 192.168.30.1/24;
}
}
[edit]
root@branch-srx# show vlans
contractors {
vlan-id 30;
l3-interface irb.30;
}
guests {
vlan-id 20;
l3-interface irb.20;
}
. . .
group CONTRACTORS-POOL {
interface irb.30;
}
group GUEST-POOL {
interface irb.20;
}
[edit]
root@branch-srx# show access address-assignment
. . .
pool CONTRACTORS-POOL {
family inet {
network 192.168.30.0/24;
range CONTRACTORS-POOL-IP-RANGE {
low 192.168.30.10;
high 192.168.30.100;
}
dhcp-attributes {
domain-name srx-branch.com;
name-server {
8.8.8.8;
}
router {
192.168.30.1;
}
}
}
}
pool GUEST-POOL {
family inet {
network 192.168.20.0/24;
range GUEST-POOL---IP-RANGE {
low 192.168.20.10;
high 192.168.20.100;
}
dhcp-attributes {
domain-name srx-branch.com;
name-server {
8.8.8.8;
}
router {
192.168.20.1;
}
}
}
}
. . .
nat {
source {
rule-set guests-to-untrust {
from zone guests;
to zone untrust;
rule guest-nat-rule {
match {
source-address 0.0.0.0/0;
}
then {
source-nat {
interface;
}
}
}
}
}
}
policies {
. . .
from-zone guests to-zone untrust {
policy guests-to-untrust {
match {
source-address any;
destination-address any;
application [ junos-http junos-https junos-ping junos-dns-udp ];
}
then {
permit;
}
}
}
}
zones {
. . .
security-zone contractors {
host-inbound-traffic {
system-services {
dhcp;
ping;
}
}
interfaces {
irb.30;
}
}
security-zone guests {
host-inbound-traffic {
system-services {
dhcp;
ping;
}
}
interfaces {
irb.20;
}
}
}Next, we'll show you how to verify that your configuration is working as expected to secure local branch communications.
