cSRX Container Firewall with Kubernetes
Overview
Containerized SRX (cSRX) Container Firewall is a virtual security solution based on CRI-O or Podman container to deliver agile, elastic and cost-saving security services for comprehensive L7 security protection.
Kubernetes (K8s) is an open-source system for automating deployment, scaling, and management of containerized applications. It groups containers that make up an application into logical units for easy management and discovery. With Kubernetes support, cSRX can scale out in a cluster running as elastic firewall service with smaller footprint when compared to virtual machines.
Containerized SRX firewall (cSRX) is designed to run in container orchestration environments like Kubernetes, originally based on Docker containers. However, as Kubernetes is deprecating Docker support starting from version 1.22, we now support deploying cSRX using container runtimes compatible with Kubernetes such as CRI-O or Podman. These runtimes are compatible with platforms like OpenShift 4 and RHEL 8, ensuring that cSRX continues to function seamlessly. Also, maintains compatibility and security functionality in Kubernetes environments without Docker.
The cSRX provides advanced Layer 4 through Layer 7 security services in a container form factor, enabling microsegmentation, application protection, and threat detection within Kubernetes clusters. It integrates with Kubernetes networking through CNIs like Flannel and Weave and supports management through Junos OS CLI, NETCONF, and Security Director. This containerized firewall offers a small footprint, scalability, and automation benefits suitable for dynamic cloud-native deployments.
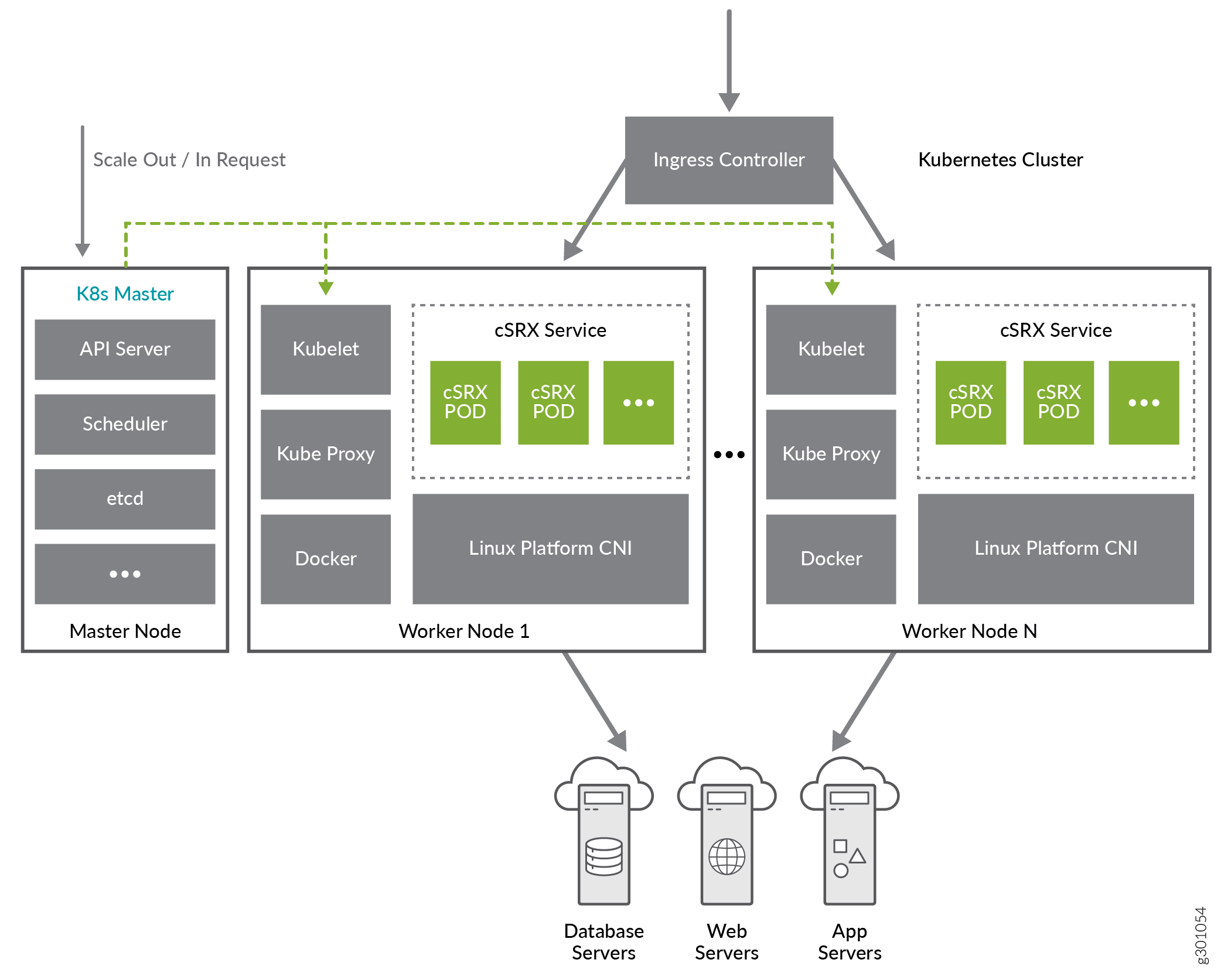
In a Kubernetes deployment, you can use Multus with both flannel and Weave Container Network Interfaces (CNIs).
To support the Kubernetes node port or the ingress controller with the cSRX, the
environment variable CSRX_MGMT_PORT_REORDER allows the cSRX to use a container
management interface. The Kubernetes node port or the ingress controller feature
with cSRX is only supported with Flannel/Weave CNI. With CSRX_MGMT_PORT_REORDER set
to yes, you can explicitly control the reconfiguration of the
management port behavior. For example, you can control access to the cSRX shell or
SD discovery on to the interface attached to the cSRX using Multus CNI.
For example, if you bring up cSRX with eth0, eth1, or eth2 with CSRX_MGMT_PORT_REORDER=yes, you can use eth2 as the new management interface.
The traffic forwarding to this eth2 has to be done through the iptables rules defined explicitly by you.
Kubernetes defines a set of building objects that collectively provide mechanisms that orchestrate containerized applications across a distributed cluster of nodes, based on system resources (CPU, memory, or other custom metrics). Kubernetes masks the complexity of managing a group of containers by providing REST APIs for the required functionalities.
A node refers to a logical unit in a cluster, like a server, which can either be physical or virtual. In context of Kubernetes clusters, a node usually refers specifically to a worker node. Kubernetes nodes in a cluster are the machines that run the end user applications.
There are two type of nodes in a Kubernetes cluster, and each one runs a well-defined set of processes:
-
Head node: also called primary, or primary node, it is the head and brain that does all the thinking and makes all the decisions; all of the intelligence is located here.
-
Worker node: also called node, or minion, it’s the hands and feet that conducts the workforce.
The nodes are controlled by the primary in most cases. The interfaces between the cluster and you is the command-line tool kubectl. It is installed as a client application, either in the same primary node or in a separate machine.
Kubernetes’s objects are Pod, Service, Volume, Namespace, Replication, Controller, ReplicaSet, Deployment, StatefulSet, DaemonSet, and Job
See Junos OS Feature Supported on cSRX Container Firewall for a summary of the features supported on cSRX.
Benefits
A cSRX running in a Kubernetes cluster provides the following benefits:
-
Operates services with a reduced footprint.
-
Facilitates quicker scale out and sacle in of the cSRX.
-
Automates management and regulation of workflow processes.
