cSRX in Contrail Host-Based Firewall
Containerized SRX (cSRX Container Firewall) is a virtual security solution, which is integrated into a Contrail networking as distributed host-based firewall (HBF) service. cSRX is built based on Docker container to deliver agile, elastic, and cost-saving security services.
cSRX Container Firewall on Contrail Host-Based Firewall Overview
The cSRX deploys as a single container on a Docker Engine compute node running in a Contrail cluster. The cSRX runs on a Linux bare-metal server as the hosting platform for the Docker container environment. The cSRX container packages all the dependent processes and libraries to support the different Linux host distribution methods (Ubuntu, Red Hat Enterprise Linux, or CentOS).
Several processes inside the Docker container launch automatically when the cSRX becomes active. Some processes support Linux features, providing the same service that they provide when running on a Linux host (for example, sshd, rsyslogd, and monit). Other processes are compiled and ported from Junos OS to perform configuration and control jobs for the security service. For example, MGD, NSD, Content Security, IDP, and AppID). srxpfe is the data plane daemon that receives and sends packets from the revenue ports of a cSRX container. cSRX uses srxpfe for Layer 2 (L2) to Layer 3 (L3) forwarding functions as well as for Layer 4 through Layer 7 network security services.
The distributed software security solution is built on top of Contrail Networking using Contrail Controller and Contrail vRouter to prevent threats in a customer’s multicloud environment.
When cSRX acts as distributed firewall service on Contrail, Kubernetes is used to orchestrate cSRX instances on compute nodes. The Kubernetes API server can respond to Contrail Controller after you've configured host-based firewall (HBF) policies on the Contrail user interface. A cSRX image is pulled from the Docker registry to compute nodes after the instances are provisioned.
You can deploy the cSRX as Contrail microsegmentation–Within a Contrail environment running mixed workloads of VMs and containers, cSRX can provide security for Layer 4 through 7 traffic, managed by Security Director.
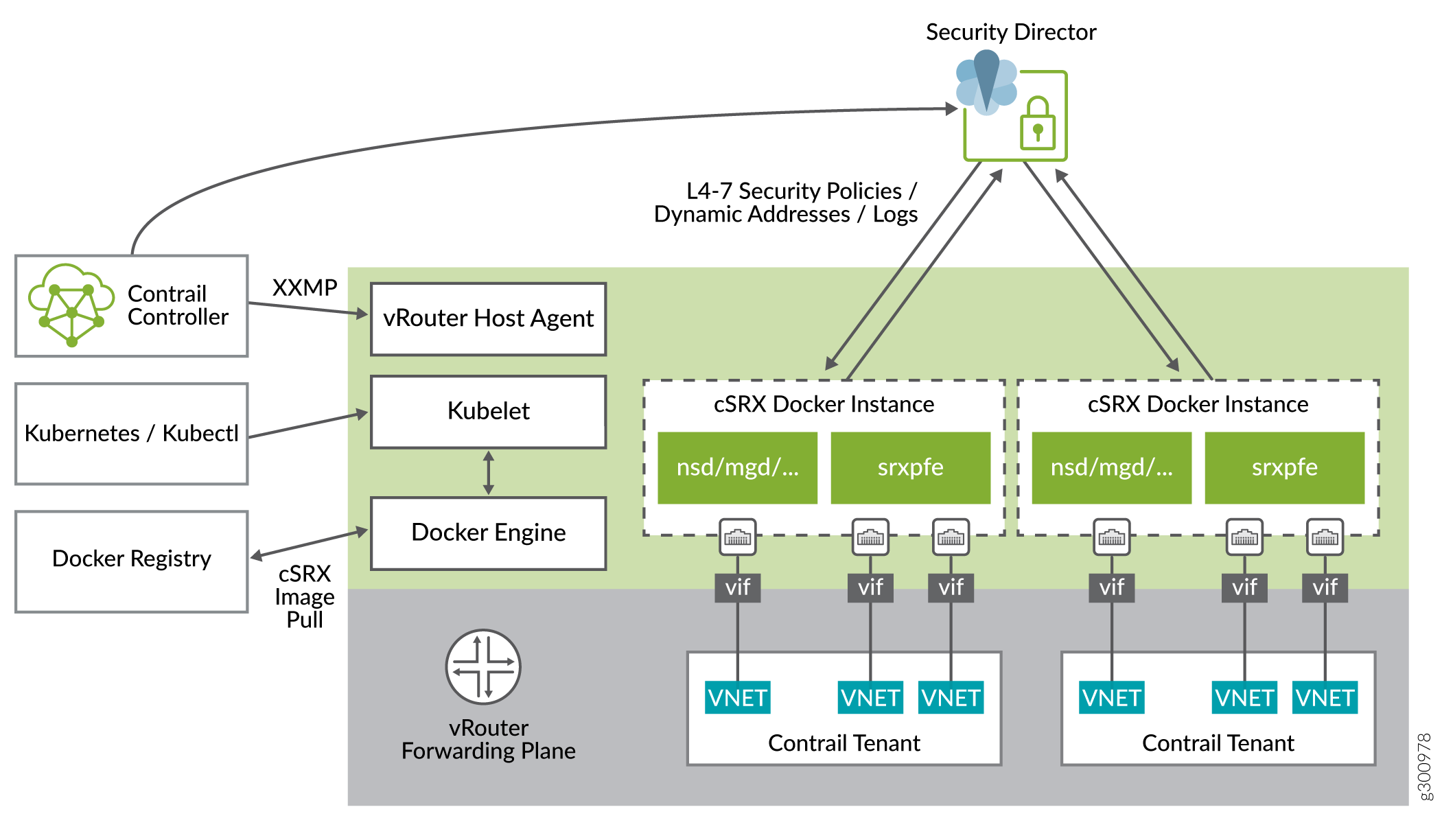
This figure illustrates the integration of cSRX with the Contrail HBF using a Docker container. Contrail Security includes an integrated virtual router (vRouter) that acts as a distributed element on every host where a cSRX application is created. The vRouter enforces security at Layers 4 through 7 by monitoring traffic flows and redirecting suspicious traffic to next-generation firewalls.
After you provision the cSRX instances:
Three vRouter interfaces (VIFs) connect the cSRX instance to the vRouter.
The management interface is connected to the management virtual network.
Two secure data interfaces are connected to the left and right virtual networks, receiving packets steered from the vRouter and sending packets to vRouter after security check.
Security Director updates L7 security policies and dynamic addresses to the cSRX instances.
The cSRX instances send security logs to Security Director.
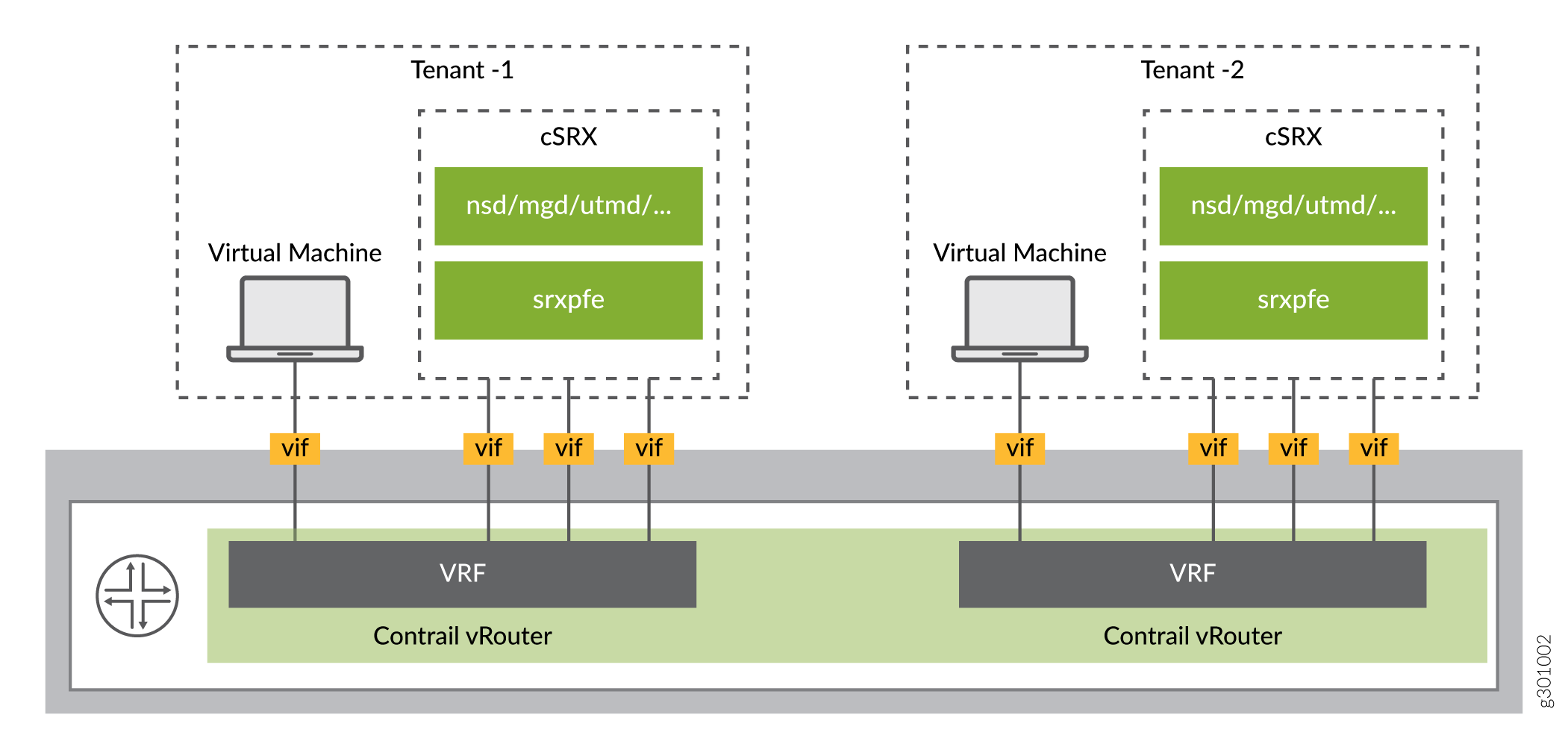
Each tenant that needs the HBF service starts a private cSRX instance on the compute node.
With Contrail Security, you can define policies and automatically distribute them across all deployments. You can also monitor and troubleshoot traffic flows inside each cSRX instance and across cSRX instances.
Contrail HBF supports the cSRX only in secure-wire mode. The secure-wire mode enables advanced security at the network edge in a multitenant virtualized environment. The cSRX provides Layer 4 through Layer 7 advanced security features such as firewall, IPS, and AppSecure. The cSRX container also provides an additional interface to manage the cSRX. When the cSRX operates in Layer 2 mode, the incoming Layer 2 frames from one interface go through Layer 4-Layer 7 processing based on the configured cSRX services. The cSRX then sends the frames out of the other interface. The cSRX container either allows the frames to pass through unaltered or drops the frames, based on the configured security policies.
Figure 2 illustrates the cSRX operating in secure-wire mode.
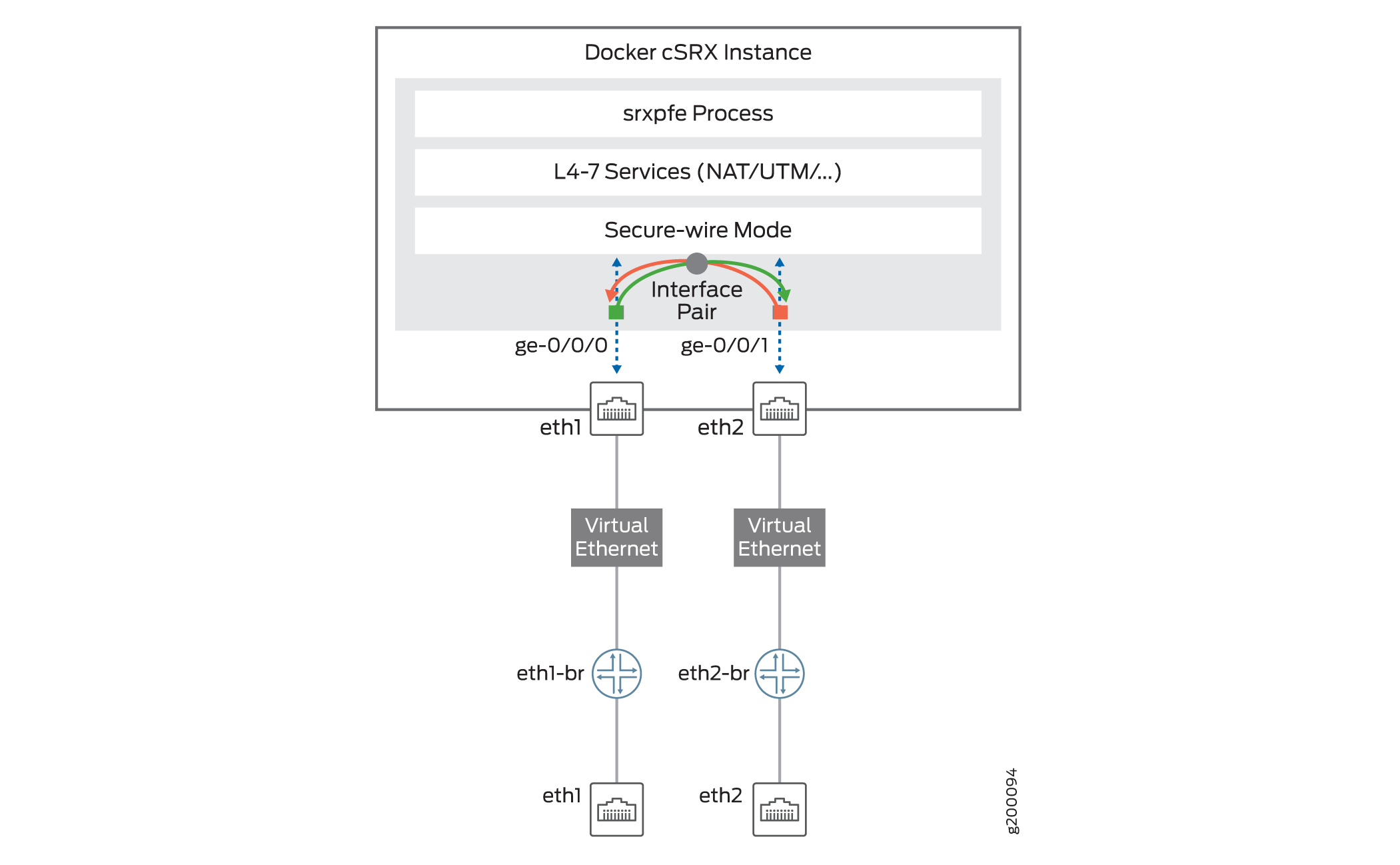
cSRX Container Firewall Deployment Modes
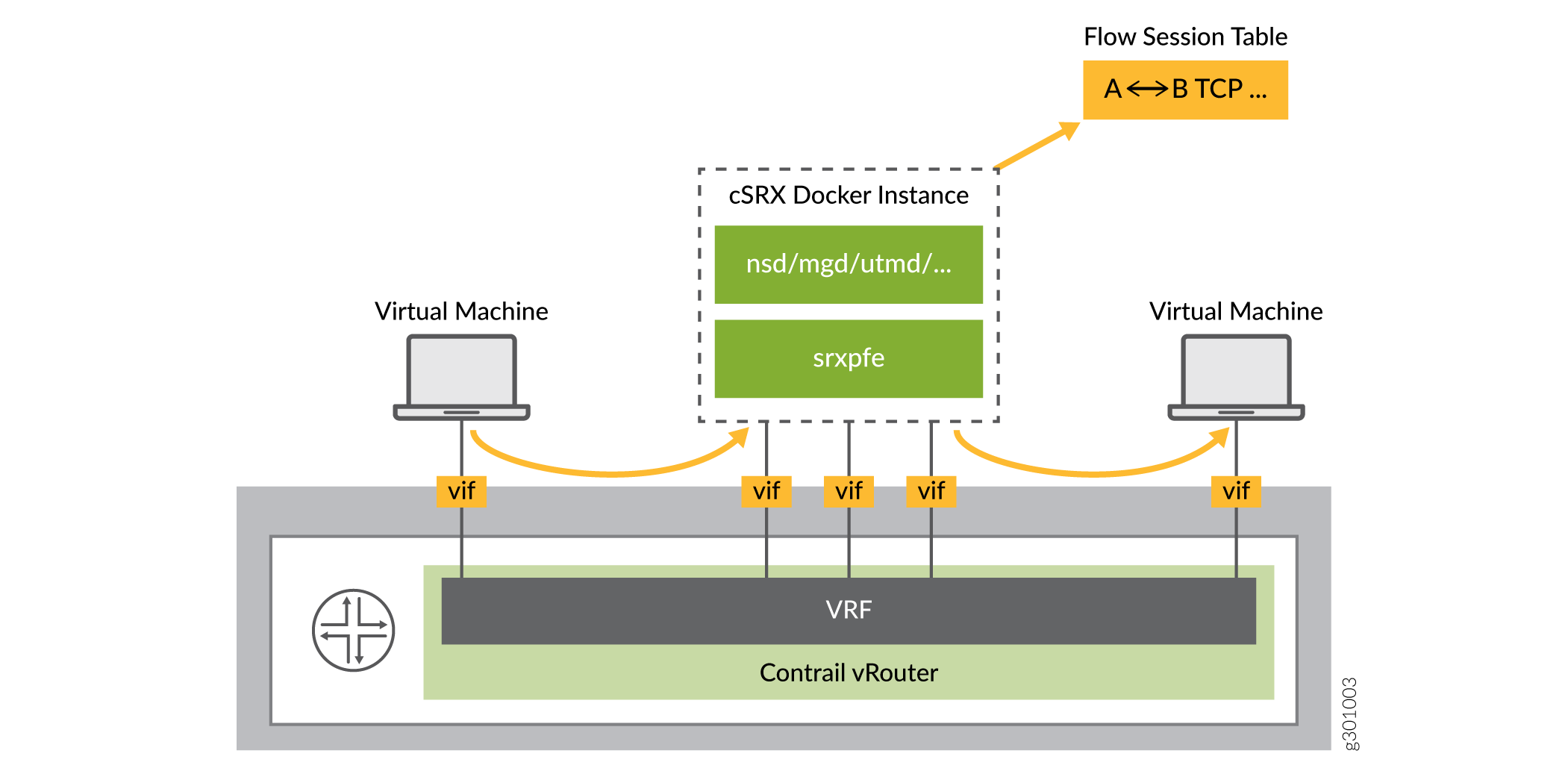
Secure Traffic Inside Compute Node
When the cSRX secures traffic inside a compute node, the vRouter steers the traffic that matches the HBF filter to the cSRX. Flow sessions are created for the traffic sent from the vRouter to the cSRX. After the cSRX completes the L7 security check, it sends the traffic back to the vRouter, which then forwards the traffic to the destination as shown in Figure 3.
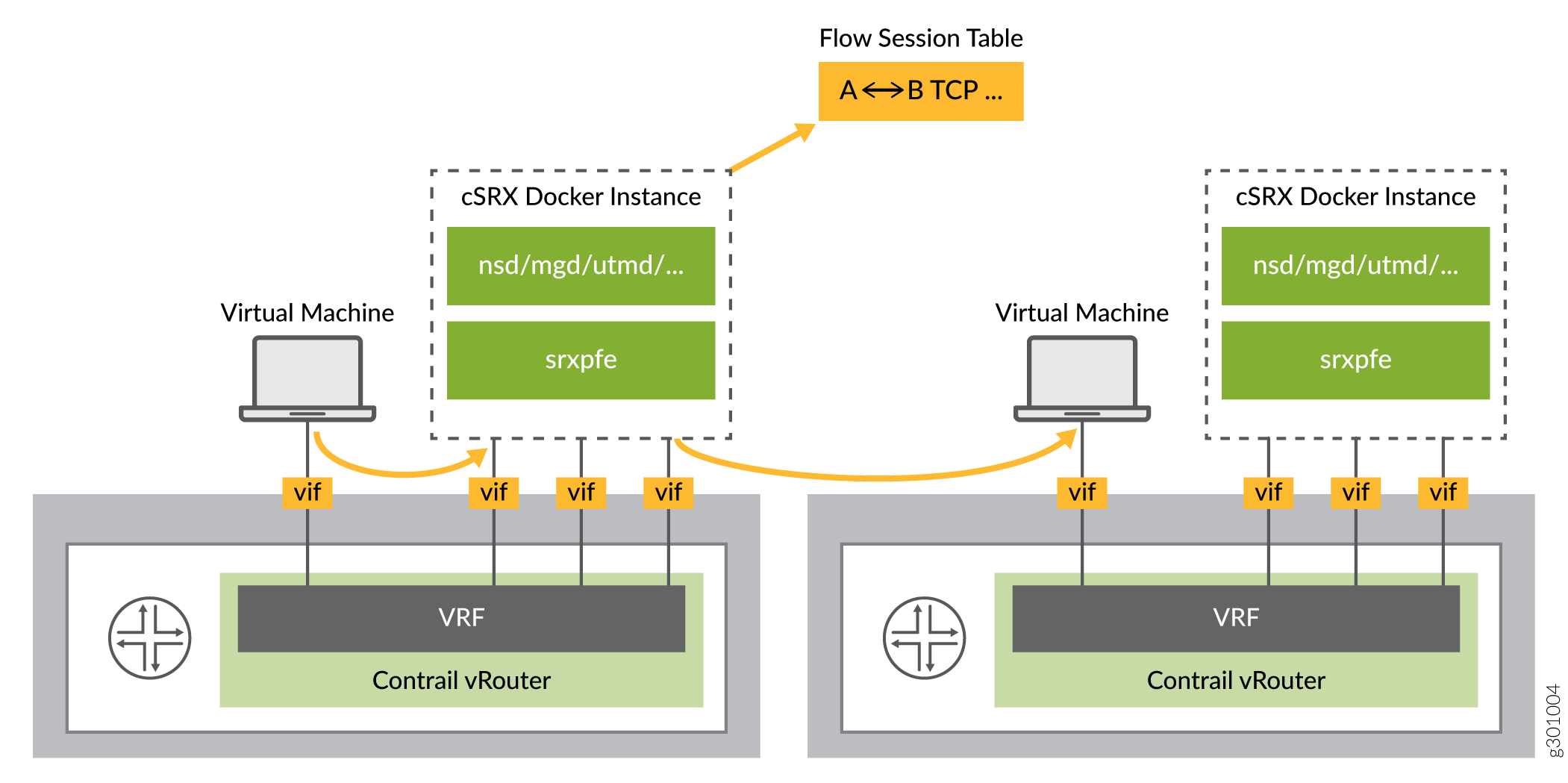
Secure Traffic Cross Compute Nodes
In this mode, the cSRX works in the same way as when it is securing the traffic inside the compute node. However, in this case the difference is, vRouter needs to guarantee that traffic is steered to the same cSRX instance when traffic is crossing different compute nodes. This mode ensures that the cSRX flow sessions are created and matched in the same cSRX instance in both directions.
Multitenant Support
For supporting multitenancy, there is separate cSRX instance started for each tenant on same compute node.
Figure 5 shows the multitenancy support.
License for cSRX Container Firewall
You need a license to activate the cSRX software features. To understand more about cSRX software feature licenses, see cSRX Flex Software Subscription Model.
