cSRX Deployment in Kubernetes
Install cSRX in Kubernetes Linux Server
Prerequisites
Following are the prerequisites required for installing cSRX Container Firewall on one primary node and ’n’ number of worker nodes. Before you begin the installation:
Install kubeadm tool on both primary and worker nodes to create a cluster. See Install Kubeadm
Install and configure CRI-O or Podman runtime on Linux host platform to implement the Linux container environment.
Verify the system requirement specifications for the Linux server to deploy the cSRX Container Firewall, see Requirements for Deploying cSRX in Kubernetes.
Download cSRX Container Firewall software, see Download cSRX Software.
Deploy cSRX Pods in Kubernetes Linux Server
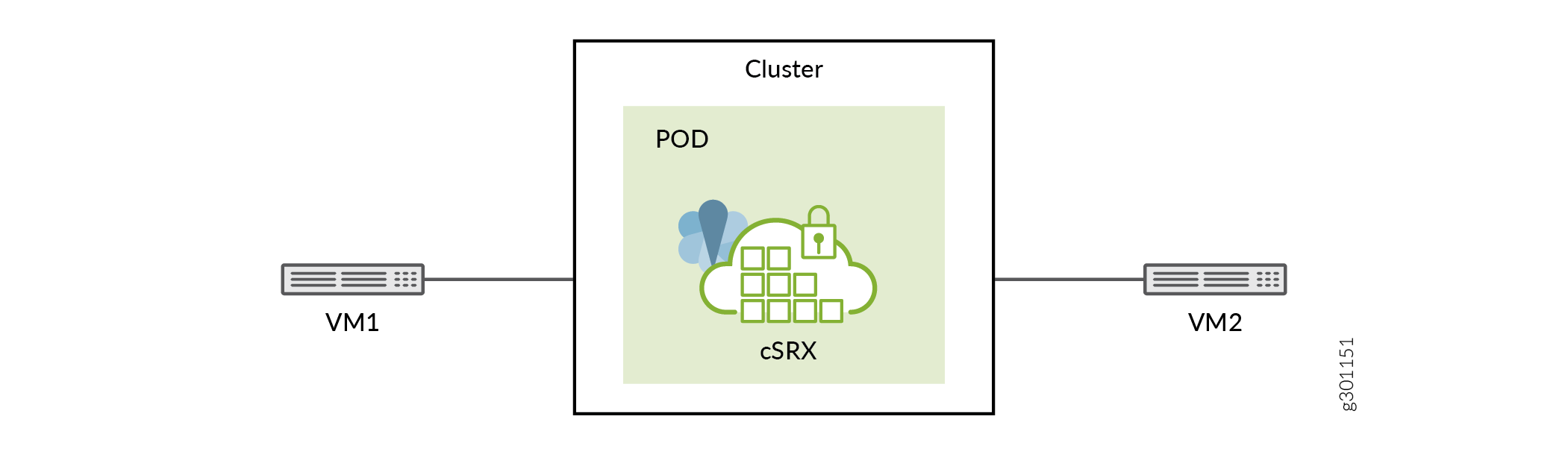
You can create cSRX Container Firewall as a Pod in routing mode and secure-wire mode to send traffic from one virtual machine to another virtual machine. You can define multiple virtual networks and connect cSRX Container Firewall interfaces to those virtual networks.
The network attachment definition is created with plugin ipam type as
host-local which allocates IPv4 and IPv6 addresses out of a specified
address range to ensure the uniqueness of IP addresses on a single host. The
ipam type as static assigns IPv4 and IPv6 addresses
statically to container.
To deploy cSRX Container Firewall with Kubernetes:
Upgrade cSRX Image Using Deployment Rollout
You can upgrade the cSRX Container Firewall software image using Kubernetes Deployment rollout.
cSRX Image Rollback
The cSRX Container Firewall image can be rolled back to previous version using Kubernetes Deployment rollout components.
Scale cSRX Deployment
To scale the cSRX Container Firewall deployment:
