Secure OAM Network Overview
The management and control plane traffic between a customer premises equipment (CPE) device associated with an SD-WAN branch site and Contrail Service Orchestration (CSO) consists of the following:
SSH and HTTPS sessions between the CPE device and CSO.
BGP session between the CPE device and a virtual route reflector (VRR).
System log traffic between the CPE device and CSO.
This traffic must be carried across the network through a secure and redundant communication channel. To provide such a secure and redundant communication channel, you must configure a secure Operation, Administration, and Maintenance (OAM) network between the SD-WAN branch sites and CSO.
This topic provides an overview of the secure OAM network, explains the workflow for configuring a secure OAM network, and benefits of a secure OAM network in an SD-WAN deployment.
Topology of a Secure OAM Network
CSO uses the provider hub devices as SD-WAN hubs to set up IPsec tunnels and provision site-to-site or site-to-hub traffic. The provider hub acts as a concentrator for terminating the IPsec tunnels from SD-WAN branch sites. The provider hub device is located in the service provider’s point of presence (POP). A provider hub device can be a SRX Series services gateway, or a vSRX instance. In CSO Release 5.0, provider hub devices are owned and managed by the Juniper Network team that hosts the cloud-based CSO.
In CSO Release 5.0, the OAM hub is instantiated within the CSO. You do not need a provider hub for OAM network.
Figure 1 shows the connections between the SD-WAN branch site, provider hub, and CSO.
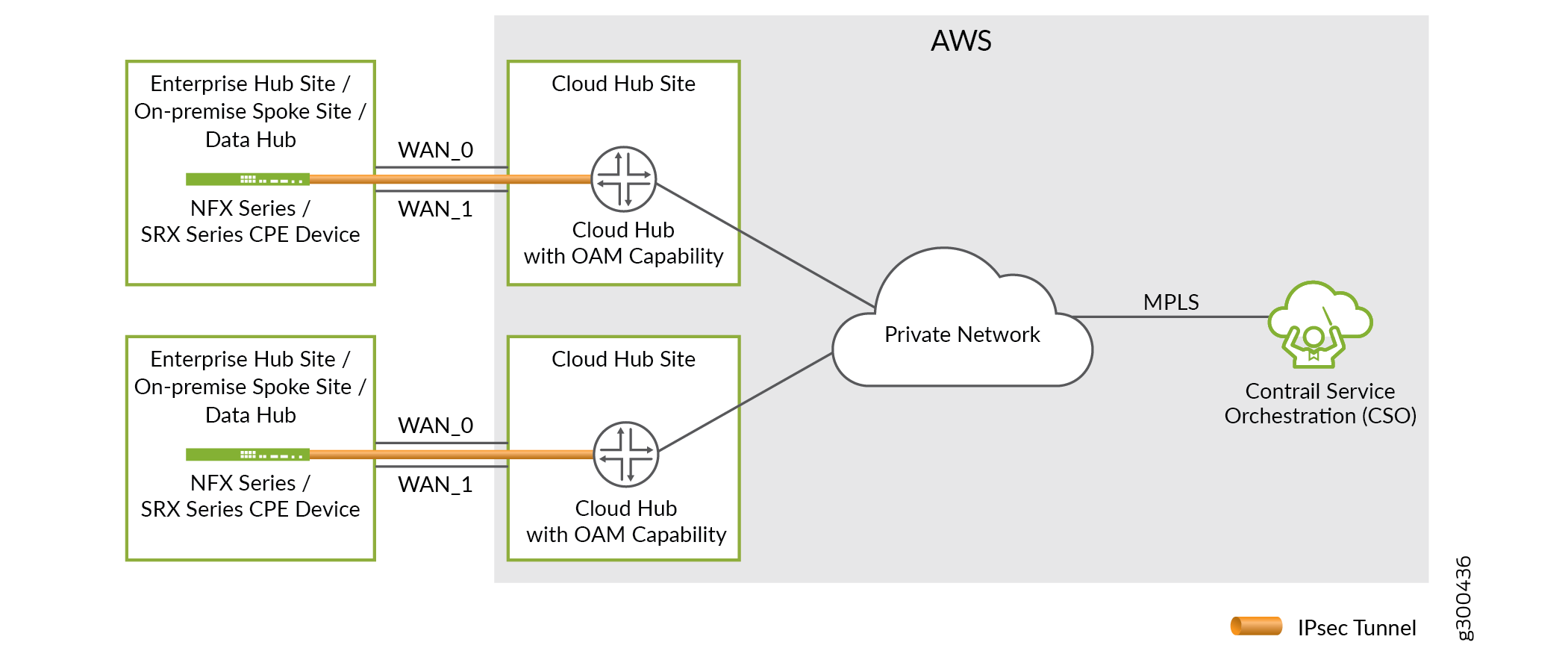
The secure OAM network is built using a dedicated IPsec tunnel (overlay connection) that is established between the CPE device associated with the SD-WAN branch site and a provider hub with OAM capability. The provider hub is connected to CSO through a secure private network (underlay connection) that is owned by the service provider.
Because the loopback IP address of the CPE device is used for OAM communication, it is fixed and unique across the entire deployment, and is always reachable from CSO over the IPsec tunnel. Even if the WAN interfaces are behind NAT and are assigned private IP addresses (by using DHCP), the OAM connectivity between the SD-WAN branch site and the provider hub is not impacted. The IPsec tunnel can still be established over the Internet WAN link including the LTE access type.
The secure OAM network is supported on both hub-and-spoke and full-mesh topologies.
Workflow for Establishing a Secure OAM Network
Use the following workflow to establish a secure OAM network between the SD-WAN branch site and the provider hub. As the provider hub is located in the service provider’s POP, it has a private and secure connectivity to CSO.
To establish a secure OAM network between SD-WAN sites and the provider hub:
Log in to Customer Portal, and add a provider hub site. Associate the provider hub site with one of the available provider hub devices.
In Customer Portal, add a branch site for the CPE device in SD-WAN deployment.
When you create the site, specify the IP address prefix for the site and select at least one WAN link for OAM traffic. The WAN link with the Use for OAM traffic option enabled is used to set up the secure OAM tunnel to the provider hub device.
Note:For an NFX250 CPE device, specify at least one WAN link with traffic type as OAM and Data. If device redundancy is enabled, then specify one WAN link for each CPE device with the traffic type as OAM and Data.
The CPE device is detected and activated. The Zero Touch Provisioning (ZTP) process is triggered over the secure OAM tunnel and the device is moved to provisioned state. The management and control plane traffic is carried across the secure OAM tunnel.
Benefits of Secure OAM Network
IPsec tunnel redundancy—The secure OAM network supports a maximum of two IPsec tunnels between each SD-WAN branch site and the provider hub, thus providing redundancy and ensuring that OAM traffic is not lost even in the case of a WAN link failure.
Hub device redundancy—In case of multihoming at the branch sites, each CPE device at the site is connected to two provider hubs, and the IPsec tunnels are established from the SD-WAN branch site to both the primary and secondary provider hub devices. This hub device redundancy ensures that the OAM traffic is not lost even if a hub fails.
Note:Sites with SD-WAN Essentials service do not support multihoming.
