What Is Containerized RPD?
cRPD provides cloud-native routing to the network. We package the cRPD software as a Docker container image. cRPD supports router functionality using IS-IS, OSPF, and BGP on the device as shown in Figure 3.
Benefits of cRPD
-
Reduced deployment time—Speed up deployment by using containers to reduce the service's boot time from several minutes to a few seconds.
-
Seamless upgrade—Upgrade software with minimal service disruption.
-
Flexibility—Launch multiple cRPD instances with minimum resource requirements to support the target scale.
-
Stability—Provide a stable routing software on Linux.
Overview of rpd on Linux
The Junos routing protocol process (rpd) is a software process within the Routing Engine software. The rpd controls the routing protocols that run on the device.
As a software process, the rpd:
-
Operates from the center of a routing protocol stack based on Linux.
-
Maintains one or more routing tables, which consolidate the routing information learned from all routing protocols.
-
Manages all protocol messages, routing table updates, and implements routing policies.
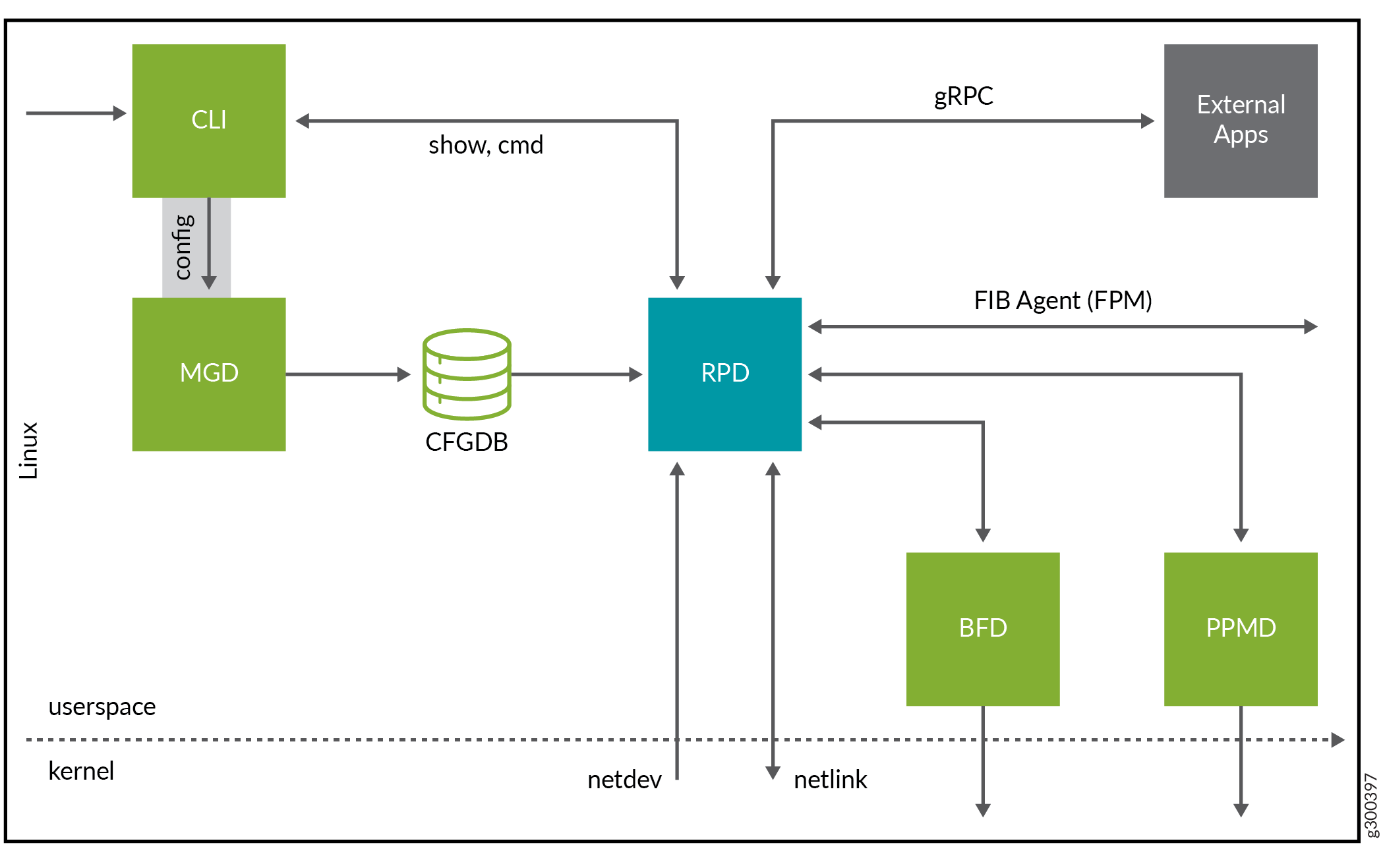
You can use the rpd application to:
-
Run on software containers. The cRPD application enables routing solutions such as containerized Route Reflector (cRR). The cRR service must work independently.
-
Interact with mgd processes for management, CLI for configuration, BFD for detecting liveness of links, periodic packet management process (PPMD), and update protocol sessions.
-
Learn the route state using various routing protocols.
-
Maintain the complete set of routing information in the routing information base (RIB), also known as the routing table.
-
Start all configured routing protocols and handle all routing messages. The rpd maintains one or more routing tables, which consolidate the routing information that the router learns from all routing protocols.
-
Implement a routing policy with which you control the routing information that moves between the routing protocols and the routing table. Using the routing policy, you can filter and limit the transfer of information as well as set properties associated with specific routes.
-
Download the routes that meet the local selection criteria into the forwarding information base (FIB), also known as the forwarding table.
-
Determine the active routes for the network destinations from the routing information and program these routes into the Routing Engine’s forwarding table.
-
Learn the interface attributes such as names, addresses, maximum transmission unit (MTU) settings, and link status through Netlink messages.
Docker Overview
cRPD runs on any Linux distribution system that supports Docker.
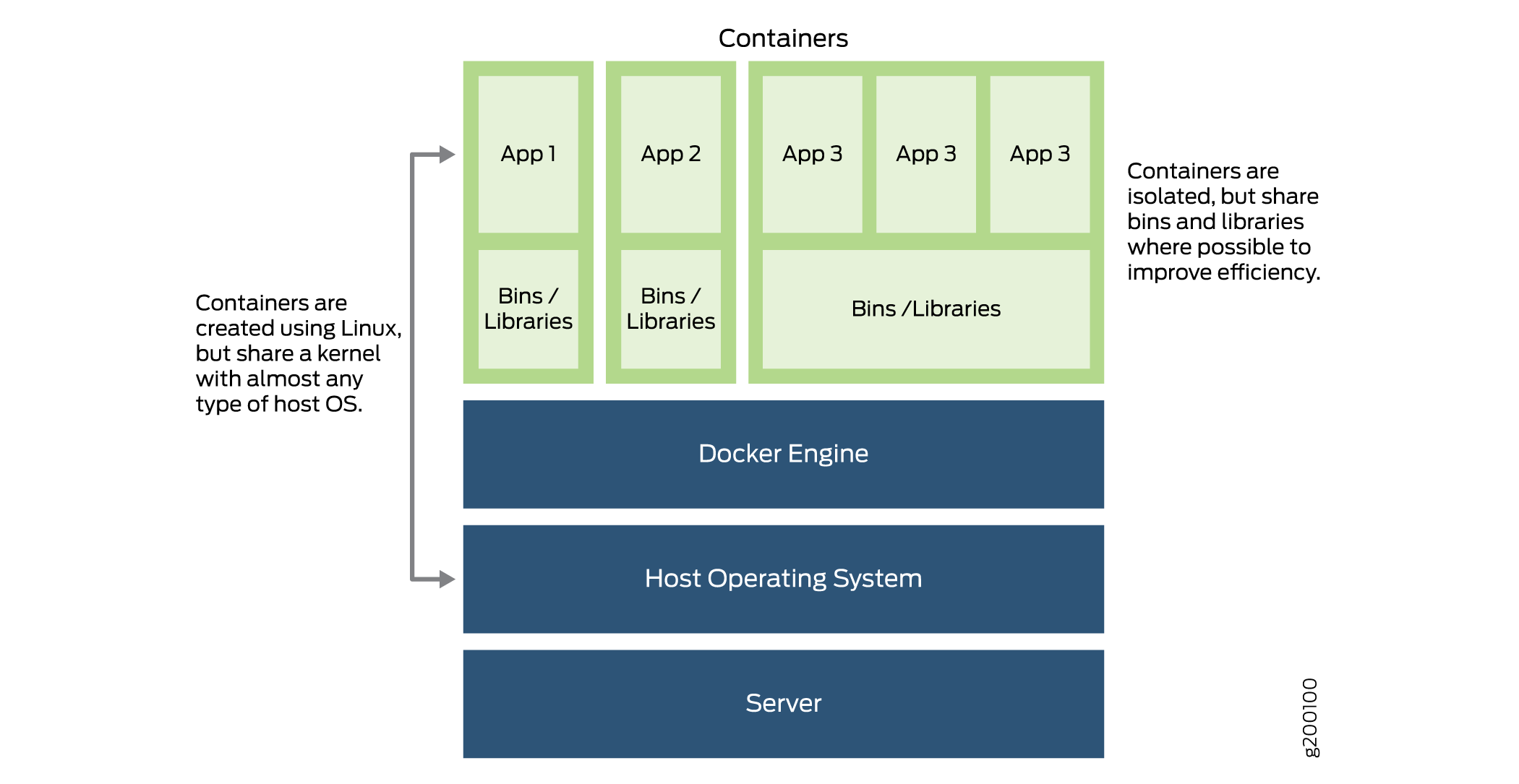
Docker is an open-source software platform that you can use to create, manage, and disassemble a virtual container that can run on any Linux server. Docker packages applications in containers. You can port and use these containers on any Linux OS. A container provides OS-level virtualization for an application.
Containers aren't virtual machines (VMs). They isolate environments with dedicated CPU, memory, I/O, and networking.
Benefits of Containers
-
Improved efficiency through isolation—Containers use the host OS Linux kernel features, such as the isolation of groups and namespaces, to enable multiple containers to run in isolation on the same Linux host OS. An application in a container has less memory because it shares the kernel of its Linux host’s OS.
-
Increased spin-up (boot) speed—Containers take less time to boot as compared with VMs. Thus, you can use containers to install, run, and upgrade applications quickly and efficiently.
Figure 2 provides an overview of a typical Docker container environment.
How Does cRPD Work?
When you start Docker, a default bridge network (also called bridge) is created automatically, and containers connect to it unless otherwise specified. You can use this bridge network to run multiple containers on the same host without having to assign dynamic ports.
A bridge enables containers connected to the same bridge network to communicate, while providing isolation from containers that are not connected to the bridge network.
In bridge mode:
-
Containers connect to the host network stack through bridges.
-
Multiple containers connect to the same bridge and communicate with one another.
-
The bridges enable external communication by connecting to the host OS network interfaces.
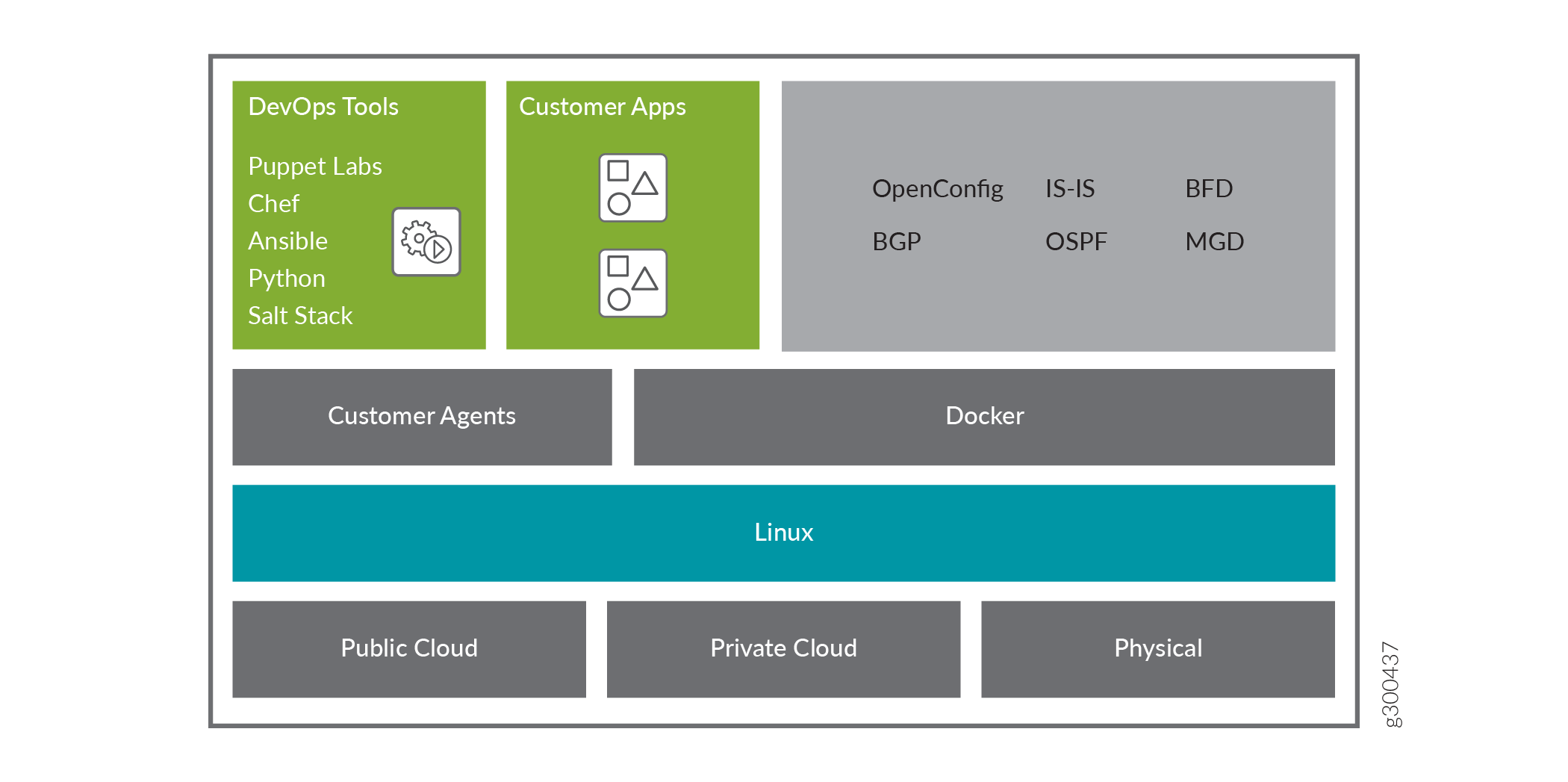
When you deploy the RPD application using a container, FIB exposes the network interfaces learned by the underlying OS kernel are sent to the RPD in the Linux container. RPD learns about all the network interfaces and adds the route state for all the network interfaces. If additional Docker containers are running in the system, then all the containers and the applications running directly on the host can access the same set of network interfaces and state. cRPD forwards the routes that meet the local route selection criteria into the FIB.
Route Reflector
You can deploy cRPD to provide control plane-only services such as BGP route reflection.
cRR is hosted on a different on-network server hardware. Applications use the reachability information learned by using the route reflection service. The route reflection networking service must work independently, without depending on the same hardware or the controllers that host the applications.
Routing Engine Kernel
The Routing Engine software consists of several software processes that control router functionality and a kernel that enables communication among all the processes.
The Routing Engine kernel provides:
-
Link between the routing tables and the Routing Engine’s forwarding table.
-
Communication with the Packet Forwarding Engine. The kernel synchronizes the Packet Forwarding Engine’s copy of the forwarding table with the primary copy in the Routing Engine.
The host Linux kernel stores the FIB. It contains all the routes and next-hop information for packet forwarding.
The rpd runs natively on Linux and uses Netlink to share program route information with the Linux kernel. Netlink facilitates communication between the kernel and user-space processes, such as cRPD.
You can use Netlink messages to:
-
Program or install the FIB state generated by the rpd in the Linux kernel.
-
Interact with mgd and CLI for configuration and management.
-
Maintain protocol sessions using ppmd.
-
Detect liveness using BFD.
Supported Features on cRPD
cRPD supports the following features:
-
BGP route reflector in the Linux Containers (LXC)
-
BGP add-path, multipath, graceful restart helper mode
-
BGP, OSPF, OSPFv3, IS-IS, and static protocols
-
BMP, BFD, and Linux FIB
-
Equal-cost multipath (ECMP)
-
Juniper extension toolkit (JET) for programmable RPD (PRPD)
-
Junos OS CLI
-
Management using open-interfaces NETCONF and SSH
-
IPv4 and IPv6 routing
-
MPLS routing
Licensing
You need a license to activate cRPD software features. To understand more about cRPD licenses, see Supported Features on cRPD, Flex Licenses for cRPD, and Managing cRPD Licenses.
