NAT Traffic Flow in a Single MX Series Router (ECMP-Based Consistent Hashing) and Scaled-Out SRX Series Firewalls (Standalone)
In this topic, you’ll see how NAT traffic flows in a topology that includes a single MX Series router with ECMP-based Consistent Hashing load balancing and standalone SRX Series Firewalls.
See Figure 1 for the topology. In this topology, you must:
- Configure a single MX Series router with two interfaces for the TRUST and UNTRUST routing instances.
- Configure external BGP (EBGP) or Bidirectional Forwarding Detection (BFD) on each interface.
- Configure the load balancing policy with source hash for route 0/0 in the forwarding table.
- Configure a unique NAT pool IP address range for each SRX Series Firewall.
Figure 1 illustrates the step-by-step traffic flow.
Figure 1: NAT Traffic Flow with
a
Single MX Series
Router
(ECMP-based
Consistent Hashing) and Scaled-Out SRX Series Firewalls (Standalone)
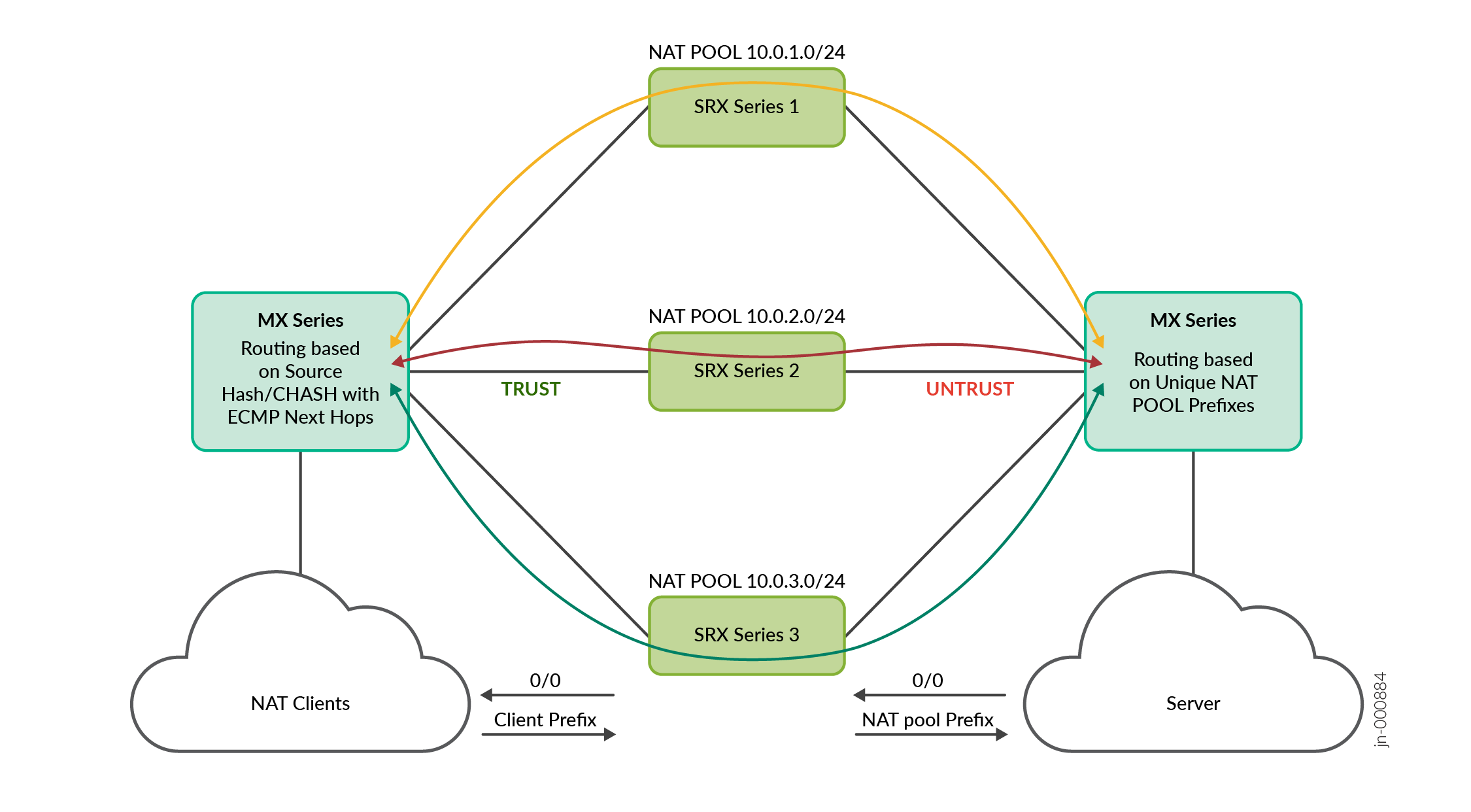

The MX Series router is a single device that is setup with multiple logical interfaces toward scaled-out SRX Series Firewalls on the TRUST and UNTRUST direction.
- The SRX Series Firewalls receive 0/0 route on the UNTRUST side and advertises using EBGP to the MX Series routers on the TRUST side. The MX Series router imports these routes on the TRUST side using the ECMP-based Consistent Hashing policy.
- The SRX Series Firewalls receive the client prefix route on the TRUST side and advertises the NAT pool route prefix using EBGP to the MX Series router on the UNTRUST side.
- The MX Series router on the TRUST side has the ECMP routes for 0/0 route, and the router on the UNTRUST side has unique route for the NAT pool route prefix.
- The forward traffic flow from the client to the server reaches the MX Series router on the TRUST instance and matches 0/0 route and takes any one ECMP next-hop to the SRX Series Firewall based on the source IP address hash value.
- The SRX Series Firewall creates a NAT flow session and routes the packet to the MX Series router on the UNTRUST direction towards the server.
- The reverse traffic flow from the server to the client reaches the MX Series router on the UNTRUST instance and matches unique NAT pool prefix route and takes the same SRX Series Firewall where the forward flow is anchored. This ensures symmetricity is maintained in the SRX Series Firewalls.
- When an SRX Series Firewall is down, Consistent Hashing on the MX Series router ensures that the sessions on the other SRX Series Firewall are not disturbed and only sessions on the impacted SRX Series Firewalls are redistributed. The redistributed sessions get an IP address from different NAT pool for source NAT and hence the application restarts its TCP/UDP session.
