Creating a Secure Logging Channel
This section describes how to place the device in an evaluated configuration to provide an encrypted communication channel over an IPsec VPN tunnel, between a device running Junos OS and a remote external storage server (syslog server).
The ssh-rsa authentication method is one of the allowed algorithms in FIPS mode.
Table 1 lists all the supported algorithms for the IPsec VPN tunnel.
|
IKE Phase1 Proposal |
|||
|---|---|---|---|
|
Authentication Method |
Authentication Algorithm |
DH Group |
Encryption Algorithm |
|
pre-shared-keys rsa-signatures-2048 ecdsa-signatures-256 ecdsa-signatures-384 |
sha-256 sha-384 |
group14 group19 group20 group24 |
aes-128-cbc aes-128-gcm aes-192-cbc aes-256-cbc aes-256-gcm |
|
IPSec Phase2 Proposal |
|||
|---|---|---|---|
|
Authentication Algorithm |
DH Group (PFS) |
Encryption Method |
Encryption Algorithm |
|
hmac-sha1-96 hmac-sha-256-128 |
group14 group19 group20 group24 |
ESP |
aes-128-cbc aes-128-gcm aes-192-cbc aes-192-gcm aes-256-cbc aes-256-gcm |
Configuring a Trusted Path or Channel Between a Device Running Junos OS and a Remote External Storage Server
This section describes the configuration details required to provide an encrypted communication channel between a device running Junos OS and the remote external storage server through an IPsec VPN tunnel.
The remote external storage server is a Linux-based syslog server on which the IPsec VPN Tunnel is terminated at the outbound interface Eth1. The log data transferred from the device is sent to the syslog termination interface Eth2 and the StrongSwan application to provide the IPsec VPN capability.
Table 2 lists the IPsec VPN tunnel details used in this example.
|
Phase 1 Proposal (P1, IKE) |
Phase 2 Proposal (P2, IPSec) |
||||||
|---|---|---|---|---|---|---|---|
|
Authentication Method |
Authentication Algorithm |
DH Group |
Encryption Algorithm |
Authentication Algorithm |
DH Group (PFS) |
Encryption Method |
Encryption Algorithm |
|
pre-shared-keys |
sha-256 |
group14 |
aes-128-cbc |
hmac-sha1-96 |
group14 |
ESP |
aes-128-cbc |
Figure 1 illustrates the encrypted communication channel between a device running Junos OS and a remote external storage server. An IPsec tunnel is established between a devices egress interface (Intf-1) and a remote syslog server outbound interface (Eth1). Data is then forwarded internally on the remote external storage server from its outbound interface Eth1; that is, the VPN endpoint to Eth2.
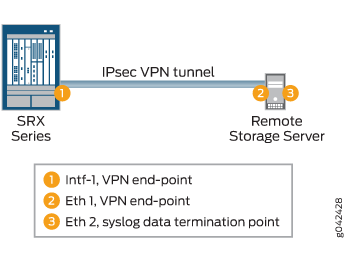
Table 3 provides the interface and IP configuration details used in this example.
|
Device Running Junos OS |
Remote Storage Server |
|---|---|
|
IP Address: “Intf-2” interface: GE-0/0/1 – IP Address: 198.51.100.2 “Intf-1” interface: GE-0/0/2 - IP Address: 198.51.100.1 Enable: Syslog logging to remote syslog server |
IP Address: Eth1: 198.51.100.3 Eth2: 203.0.113.1 Gateway Eth1: 198.51.100.1 Tools: SSH and Strongswan (for IPsec VPN) |
To configure the trusted path or channel between a device running Junos OS and a remote external storage server:
-
Enable stream logging for traffic logs.
[edit security] user@host#set log cache user@host#set log mode event user@host#set log source-address 198.51.100.2 user@host#set log stream STREAM category all user@host#set log stream STREAM host 203.0.113.1
Note:192.168.2.1is the IP address of the syslog server outbound interface at which the IPsec VPN tunnel is terminated, and20.20.20.2is the IP address of the syslog server interface for which log data is destined. -
Enable syslog on the device.
[edit system] user@host#set syslog user * any emergency user@host#set syslog host 203.0.113.1 any any user@host#set syslog file SYSLOG any any user@host#set syslog file SYSLOG authorization info user@host#set syslog file SYSLOG_COMMANDS interactive-commands error user@host#set syslog file traffic-log any any user@host#set syslog file traffic-log match RT_FLOW_SESSION user@host#set syslog source-address 198.51.100.2
-
Enable VPN on the device.
IKE setup:
[edit security] user@host#set ike proposal IKE_Proposal authentication-method pre-shared-keys user@host#set ike proposal IKE_Proposal dh-group group14 user@host#set ike proposal IKE_Proposal authentication-algorithm sha-256 user@host#set ike proposal IKE_Proposal encryption-algorithm aes-128-cbc user@host#set ike policy IKE_Policy mode main user@host#set ike policy IKE_Policy proposals IKE_Proposal user@host#set ike policy IKE_Policy pre-shared-key ascii-text 12345 user@host#set ike gateway GW ike-policy IKE_Policy user@host#set ike gateway GW address 198.51.100.3 user@host#set ike gateway GW local-identity inet 198.51.100.1 user@host#set ike gateway GW external-interface ge-0/0/2 user@host#set ike gateway GW version v2-only
IPsec setup:
[edit security ipsec] user@host#set proposal IPsec_Proposal protocol esp root@host#set proposal IPsec_Proposal authentication-algorithm hmac-sha1-96 root@host#set proposal IPsec_Proposal encryption-algorithm aes-128-cbc root@host#set policy IPsec_Policy perfect-forward-secrecy keys group14 root@host#set policy IPsec_Policy proposals IPsec_Proposal root@host#set vpn VPN bind-interface st0.0 root@host#set vpn VPN ike gateway GW root@host#set vpn VPN ike ipsec-policy IPsec_Policy root@host#set vpn VPN establish-tunnels immediately
-
Perform the following additional configurations on the device.
IKE trace log:
[edit security ike] root@host#set traceoptions file IKE_Trace root@host#set traceoptions file size 10000000 root@host#set ike traceoptions flag all
Flow trace:
[edit security flow ] root@host#set traceoptions file DEBUG root@host#set traceoptions file size 1000000 root@host#set traceoptions flag all
Route options:
[edit ] root@host#set routing-options static route 203.0.113.2/24 qualified-next-hop st0.0 preference 1
Address book configuration:
[edit security address-book] root@host#set global address trustLAN 198.51.100.0/24 root@host#set global address unTrustLAN 198.51.100.3/24
Zone configuration:
[edit security zones] root@host#set security-zone trustZone host-inbound-traffic system-services all root@host#set security-zone trustZone host-inbound-traffic protocols all root@host#set security-zone trustZone interfaces ge-0/0/1.0 root@host#set security-zone unTrustZone host-inbound-traffic system-services all root@host#set security-zone unTrustZone host-inbound-traffic protocols all root@host#set security-zone unTrustZone interfaces st0.0 root@host#set security-zone unTrustZone interfaces ge-0/0/2.0
Policy configuration:
[edit security policies] root@host#set from-zone trustZone to-zone unTrustZone policy Policy1 match source-address trustLAN root@host#set from-zone trustZone to-zone unTrustZone policy Policy1 match destination-address unTrustLAN root@host#set from-zone trustZone to-zone unTrustZone policy Policy1 match application any root@host#set from-zone trustZone to-zone unTrustZone policy Policy1 then permit root@host#set from-zone trustZone to-zone unTrustZone policy Policy1 then log session-init root@host#set from-zone trustZone to-zone unTrustZone policy Policy1 then log session-close root@host#set from-zone unTrustZone to-zone trustZone policy Policy1 match source-address unTrustLAN root@host#set from-zone unTrustZone to-zone trustZone policy Policy1 match destination-address trustLAN root@host#set from-zone unTrustZone to-zone trustZone policy Policy1 match application any root@host#set from-zone unTrustZone to-zone trustZone policy Policy1 then permit root@host#set from-zone unTrustZone to-zone trustZone policy Policy1 then log session-init root@host#set from-zone unTrustZone to-zone trustZone policy Policy1 then log session-close
