Creating a Secure Logging Channel
This section describes how to place the device in an evaluated configuration to provide an encrypted communication channel over an IPsec VPN tunnel, between a device running Junos OS and a remote external storage server (syslog server).
The ssh-rsa authentication method is one of the allowed algorithms in FIPS mode.
Table 1 lists all the supported algorithms for the IPsec VPN tunnel.
IKE Phase1 Proposal |
|||
|---|---|---|---|
Authentication Method |
Authentication Algorithm |
DH Group |
Encryption Algorithm |
pre-shared-keys rsa-signatures-2048 ecdsa-signatures-256 ecdsa-signatures-384 |
sha-256 sha-384 |
group14 group19 group20 group24 |
aes-128-cbc aes-128-gcm aes-192-cbc aes-256-cbc aes-256-gcm |
IPSec Phase2 Proposal |
|||
|---|---|---|---|
Authentication Algorithm |
DH Group (PFS) |
Encryption Method |
Encryption Algorithm |
hmac-sha1-96 hmac-sha-256-128 |
group14 group19 group20 group24 |
ESP |
aes-128-cbc aes-128-gcm aes-192-cbc aes-192-gcm aes-256-cbc aes-256-gcm |
Configuring a Trusted Path or Channel Between a Device Running Junos OS and a Remote External Storage Server
This section describes the configuration details required to provide an encrypted communication channel between a device running Junos OS and the remote external storage server through an IPsec VPN tunnel.
The remote external storage server is a Linux-based syslog server on which the IPsec VPN Tunnel is terminated at the outbound interface Eth1. The log data transferred from the device is sent to the syslog termination interface Eth2 and the StrongSwan application to provide the IPsec VPN capability.
Table 2 lists the IPsec VPN tunnel details used in this example.
Phase 1 Proposal (P1, IKE) |
Phase 2 Proposal (P2, IPSec) |
||||||
|---|---|---|---|---|---|---|---|
Authenticat ion Method |
Authenticat ion Algorithm |
DH Group |
Encryption Algorithm |
Authenticat ion Algorithm |
DH Group (PFS) |
Encryption Method |
Encryption Algorithm |
pre- shared-keys |
sha-256 |
group14 |
aes-128-cbc |
hmac-sha1 -96 |
group14 |
ESP |
aes-128-cbc |
Figure 1 illustrates the encrypted communication channel between a device running Junos OS and a remote external storage server. An IPsec tunnel is established between a devices egress interface (Intf-1) and a remote syslog server outbound interface (Eth1). Data is then forwarded internally on the remote external storage server from its outbound interface Eth1; that is, the VPN endpoint to Eth2.
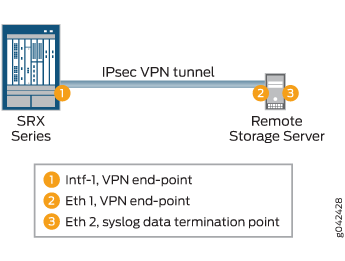
Table 3 provides the interface and IP configuration details used in this example.
Device Running Junos OS |
Remote Storage Server |
|---|---|
IP Address: “Intf-2” interface: GE-0/0/1 – IP Address: 198.51.100.2 “Intf-1” interface: GE-0/0/2 - IP Address: 198.51.100.1 Enable: Syslog logging to remote syslog server |
IP Address: Eth1: 198.51.100.3 Eth2: 203.0.113.1 Gateway Eth1: 198.51.100.1 Tools: SSH and Strongswan (for IPsec VPN) |
To configure the trusted path or channel between a device running Junos OS and a remote external storage server:
