DNS DGA Detection Overview
Domain Name System (DNS) Domain Generation Algorithm (DGA) generates seemingly random domain names that are used as rendezvous points with potential C&C servers. DNS DGA detection uses machine learning (ML) models as well as known pre-computed DGA domain names and provides domain verdicts, which helps inline blocking and sinkholing of DNS queries on SRX Series Firewalls.
Juniper ATP Cloud provides a machine learning-based DGA detection model. SRX Series Firewall acts as a collector of security metadata and streams the metadata to Juniper ATP Cloud for DGA analysis. We use both ATP Cloud service and security-metadata-streaming framework to conduct DGA Inspection in the cloud.
DNS DGA detection is available only with Juniper ATP Cloud license. For feature specific licensing information, see Software Licenses for ATP Cloud.
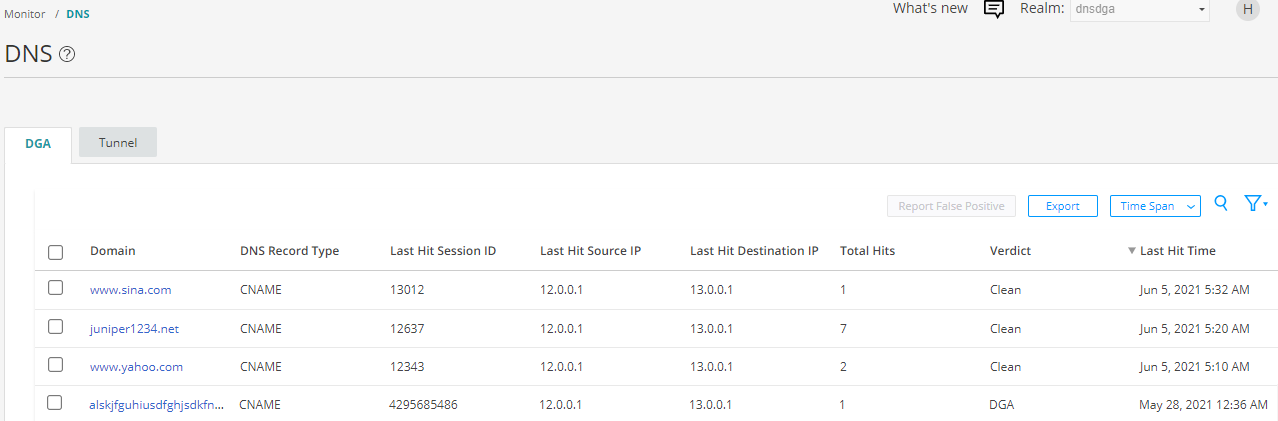
To view DNS DGA detections, log in to Juniper ATP Cloud Web portal and navigate to Monitor > DNS. The DGA detections are displayed as shown in Figure 1.
DGA Detection Procedure
The procedure for DNS DGA detection is as follows:
- The Client generates a DNS request and forwards it to the corporate DNS server.
- The Corporate DNS server checks its local cache and finds that it has no matching record. A cache-miss occurs and the corporate DNS server attempts to query a public DNS server.
- The SRX Series device receives a DNS requests with record type A/AAAA/CNAME/MX, and so on.
- Once SRX Series device receives the DNS query, it will consult its local DNS cache.
- If the domain is not present in the cache (cache miss), SRX sends the domain to Juniper ATP Cloud for analysis.
- Juniper ATP Cloud service runs rapid DGA machine learning model and responds to SRX
Series device with the following verdicts.
-
Clean
-
DGA
-
Suspicious
-
- If domain is present in the cache (cache hit), the SRX Series device consults the
verdict.
- If the domain is clean, the SRX Series device forwards the query and ignores the rest of the session.
- If the domain is marked as DGA, the SRX Series device takes the action defined in the policy (permit/drop/sinkhole/log, and so on)
- If the domain is not present in the cache, the SRX Series device
- Copies the domain and sends it to the Juniper ATP cloud for DGA analysis.
- Forwards the query to its original destination and requests the appropriate context (query type) from the pending response packet.
Only SecIntel has the ability to check its allowlist, blocklist, and C&C. The security-metadata-streaming CLI configuration does not perform matching against this list. Both features must be enabled on the policy to detect C&C and DGA/Tunnels.
