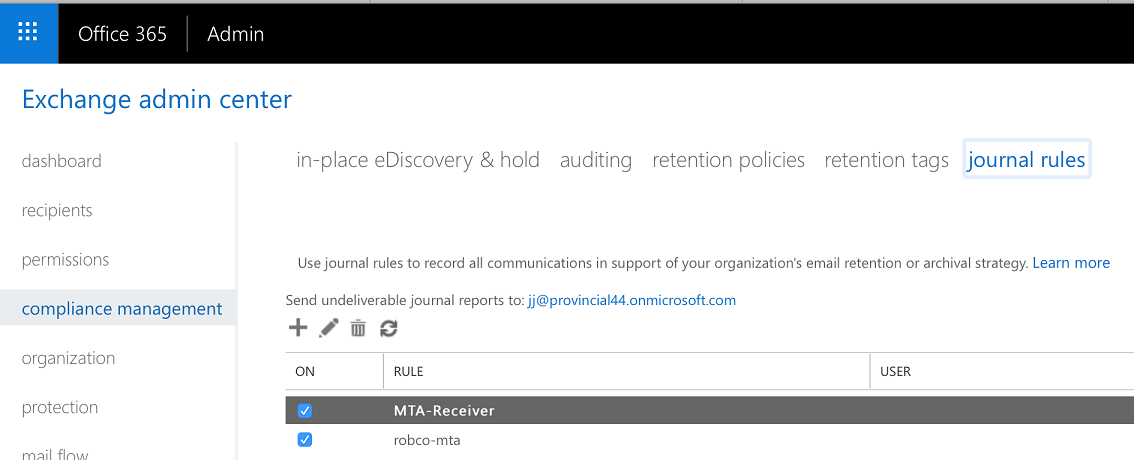
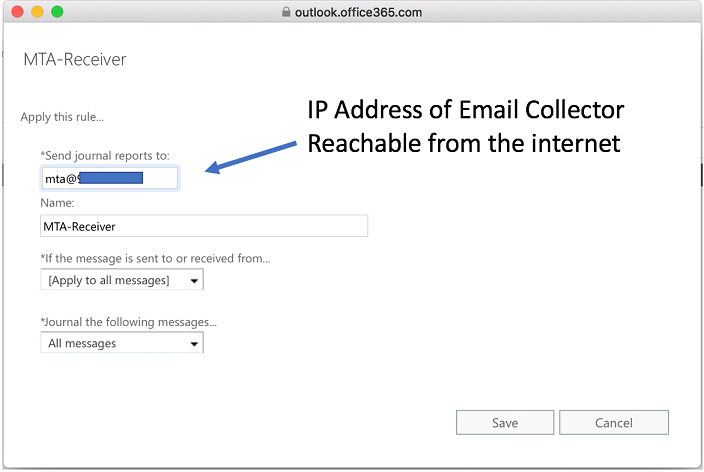
Appendix A: Deploy ATP Appliance Email Threat Mitigation for Office 365 (A Start to Finish Example)
This section provides a start to finish configuration of ATP Appliance email threat mitigation for Microsoft Office 365 using Azure.
Overview
The administrator must configure supported servers to direct the email stream to the ATP Appliance MTA Receiver using the email address setup on the MTA Receiver (for example: CustomerX@MTA-IP or CustomerX@DomainName. When using a domain name, the MX records should be resolvable by the servers). The ATP Appliance Appliance’s On-Premise MTA Receiver extracts objects/URL links and submits them to the ATP Appliance Appliance Core for analysis.
Prerequisites:
ATP Appliance SmartCore running CyOS version 5.0.4.27
ATP Appliance SmartCore licensed for Enterprise Feature Set
ATP Appliance SmartCore administrator account privileges
See Also
Register a New Application in the Azure Portal
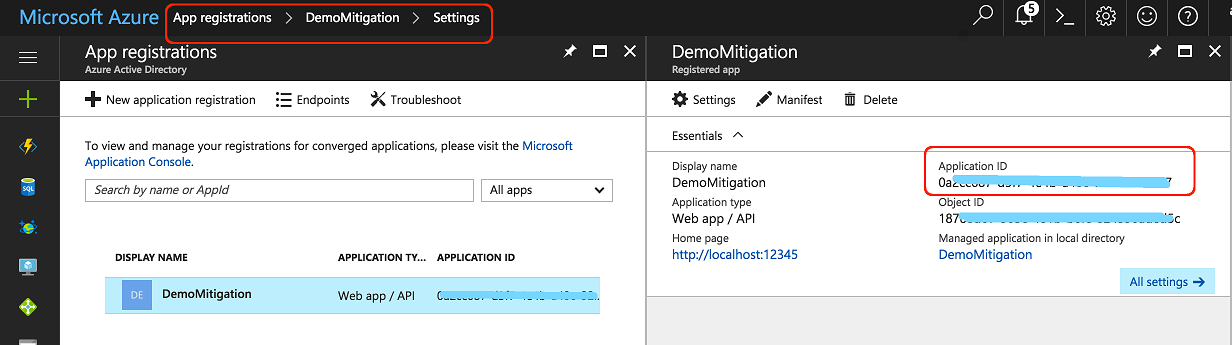
Obtain the Application ID and Object ID
Once you've completed the registration process, Azure AD assigns your application a unique client identifier—the Application ID. Go to the App registrations page, select the application you just created, and save the Application ID and Object ID as shown below.
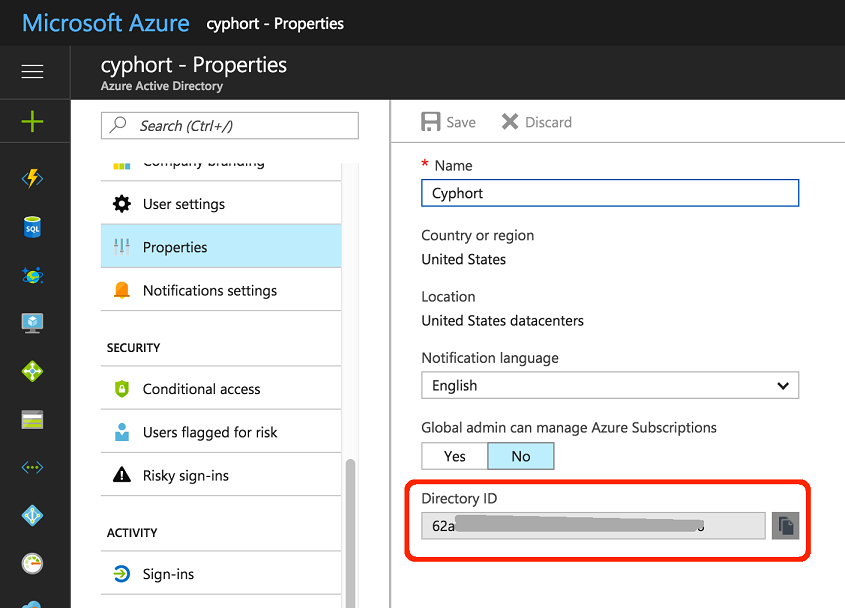
Obtain the Directory ID
In Azure, navigate to DashboardActive Directory>Properties. Copy the Directory ID and save it for later use.
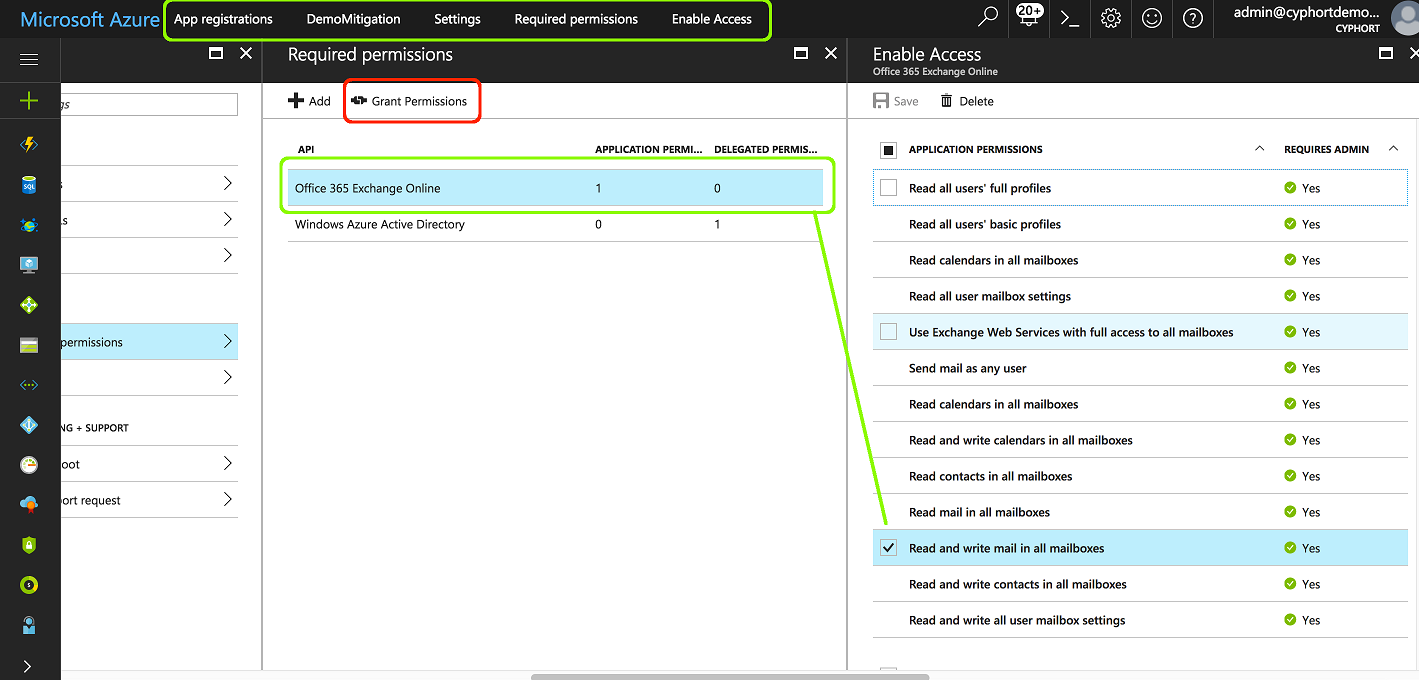
Provide API Access Permissions
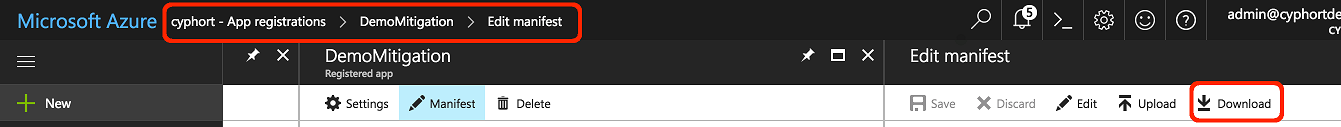
Download the Manifest File
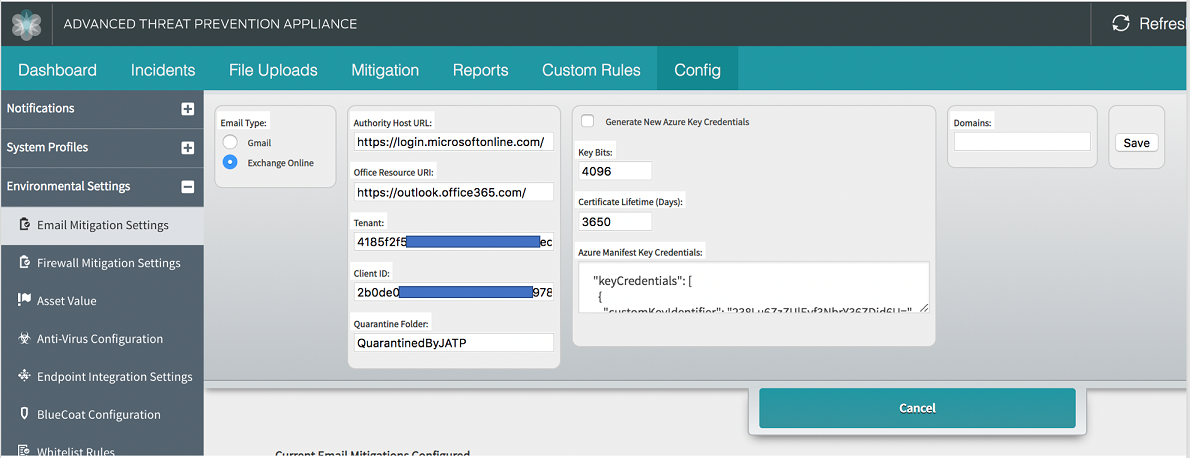
Configure Email Mitigation Settings in ATP Appliance
Upload the Manifest File
- Go to your App registrations in the Azure Portal.
- From your app, click the Manifest button located between the “Settings” and “Delete” buttons.
- Upload the manifest json file you updated with ‘keyCredentials’ from the ATP Appliance section.
Configure Office 365 Journaling for ATP Appliance Mitigation
Create an administrator user in Office 365 who is configured as the journal email sender:
Configure the Email Collector on ATP Appliance
Test the Configuration
- Login to the ATP Appliance Web UI.
- Navigate to Config>Environmental Settings>Email Mitigation Settings.
- Click the Test link.
- Verify that the test is successful.
- If you see Unable to obtain access token, the manifest file’s key credentials are not correct. This may be caused by a lack of API access permissions, an incorrect Client ID, or an incorrect Tenant Id. Please refer to the above sections again to verify that all configurations are correct and that they match on both Azure and ATP Appliance.