ON THIS PAGE
RADIUS Provider
Remote Authentication Dial-In User Service (RADIUS). See below for limitations.
RADIUS Limitations
- All password changes should be done on the RADIUS server. You cannot change the user’s password from Apstra once you enable the External Provider.
- RADIUS authentication does not control Linux user login via SSH.
- If the user group is changed on the RADIUS server, you will need to change role-mapping in Apstra accordingly.
- Nested groups are not allowed. You must explicitly assign each group to a role.
- When a user logs in, only username and password are required for authenticating against the remote RADIUS server. Log in credentials are not cached. Therefore, when a user logs in, a connection between Apstra and the remote RADIUS server is required.
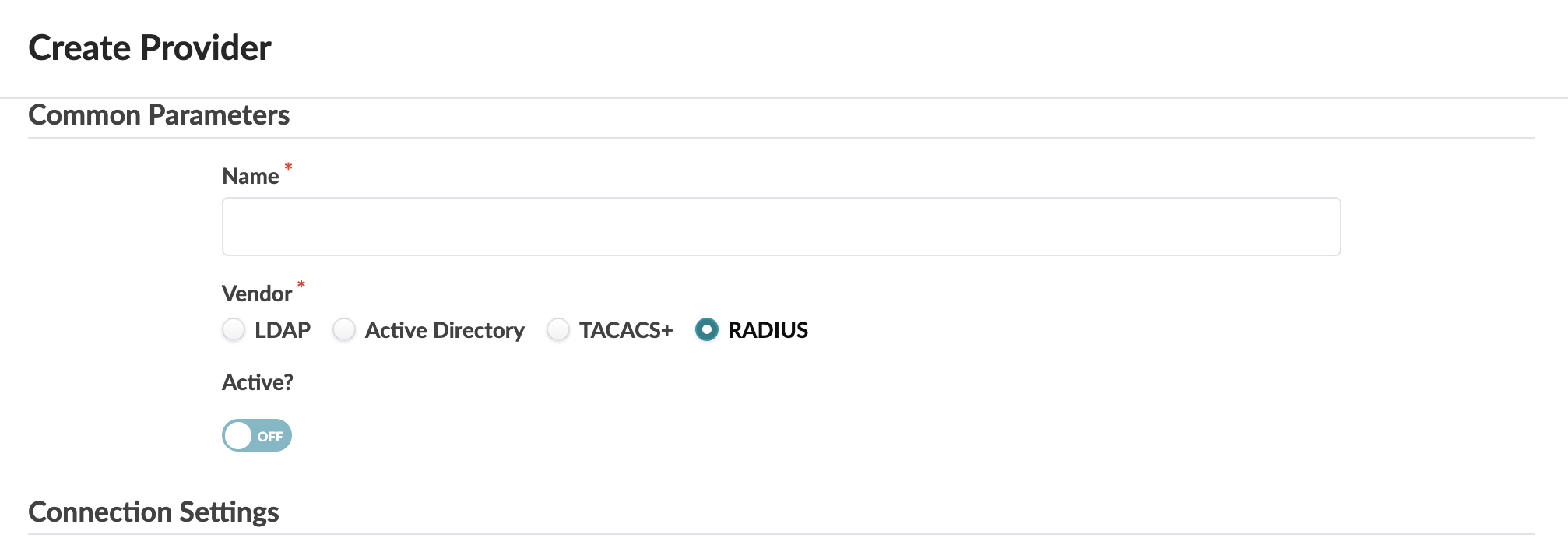
Create RADIUS Provider
After configuring and activating a provider, you must map that provider to one or more user roles to give permissions to users with those roles.