User / Role Management Introduction
Overview
You need a user (profile) to work in the Apstra GUI environment. The areas in the environment that you can access and/or change are determined by the roles assigned to you as a user. Apstra ships with one predefined user called admin that's assigned the administrator role. The administrator role is one of the five predefined roles as shown in the table below:
|
Role |
Permissions |
|---|---|
|
administrator |
Includes all permissions. |
|
device_ztp |
Includes one permission, to edit ZTP. For setting up Apstra ZTP server, We recommend creating a dedicated user and assigning only this role. |
|
License_reader |
Includes one permission, to read Juniper Apstra Licenses. |
|
user |
Includes permission to view and edit various elements including permission to create users. |
|
viewer |
Includes permission to only view various elements. |
You can't modify predefined roles, but you can create custom roles if you have Write/Read Roles permission. The admin user has this permission; you can also create a user and assign it with the Write/Read Roles permission.
You can't modify the predefined admin user, but you can create custom users if you have Read/Write Users permission. The admin and user users have this permission; you can also create a user and assign it with the Read/Write Users permission
Each role applies to one of three different permission types, as shown in the table below.
|
Permission Type |
Permissions |
|---|---|
|
Global |
Includes general blueprint permissions (not blueprint-specific) as well as areas outside of blueprints, such as for devices, design, resources, AAA, Analytics, External Systems, Platform and others. |
|
Granular |
Includes blueprint-related permissions for all blueprints or for selected blueprints. |
|
Tenant |
Includes permissions based on routing zones. (new in Apstra version 5.0.0) |
See sections below for more details about each permission type.
Global Permissions
Blueprints
Includes permissions for the following:
-
Allow overriding other users staged changes (write only)
-
Blueprints (read, write, commit, delete)
-
Connectivity Templates (read only)
-
Show information about user who locked blueprint (read only)
Devices
Includes permissions for the following:
-
Agents (read, write)
-
Chassis Profiles (read, write)
-
Device Profiles (read, write)
-
Devices (read, write)
-
Linecard Profiles (read, write)
-
ZTP (read, write)
Design
Includes permissions for the following:
-
Config Templates (read, write)
-
Configlets (read, write)
-
Interface Maps (read, write)
-
Logical Devices (read, write)
-
Port Aliases (read, write)
-
Property Sets (read, write)
-
Rack Types (read, write)
-
Tags (read, write)
-
Templates (read, write)
Resources
Includes permissions for the following:
-
ASN Pools (read, write)
-
Integer Pools (read, write)
-
IP Pools (read, write)
-
IPv6 Pools (read, write)
-
VNI Pools (read, write)
AAA
Includes permissions for the following:
-
Audit Config (read, write)
-
Audit Events (read only)
-
Roles (read, write)
-
Security Config (read, write)
-
Users (read, write)
Analytics
Includes permissions for the following:
-
Flow Data Collectors (read only)
-
Juniper Apstra Query Based Analytics (read only)
-
Telemetry Service Registry (read only)
External Systems
Includes permissions for the following:
-
AAA Providers (read, write)
-
Virtual Infra Manager (read, write)
Platform
Includes permissions for the following:
-
Exempt Juniper Apstra Cluster Management read-only mode (write only)
-
Juniper Apstra Cluster Management (read, write)
-
Juniper Apstra Licenses (read, write)
-
Juniper Apstra Metric Logs (read only)
-
Streaming (read, write)
-
Sysdb Data (read, write)
Other
Includes permissions for the following:
-
Connector Types (read only)
-
Graph Queries (read, write)
-
Port Setting Schema (read only)
-
Telemetry RPC Schema Registry (read only)
-
Tenants (read only)
Granular Permissions
You can apply granular permissions to all blueprints or to selected blueprints.
Common Permissions
Includes permissions for the following:
-
Read blueprint
-
Make any change to staging blueprint
-
Allow overriding other users staged changes
-
Commit changes
-
Show information about user who locked blueprint
Datacenter-specific Permissions
Includes permissions for the following:
-
Manage tenants
-
Manage racks and links
-
Manage resource groups
-
Manage routing zones
-
Manage generic systems
-
Manage virtual networks (includes managing VN endpoints)
-
Manage virtual network endpoints
Freeform-specific Permissions
Includes permissions for the following:
-
Manage property sets
-
Manage resources
Tenant Permissions
You can apply tenants permissions to tenants.
Tenant-specific Permissions
Includes permissions for the following:
-
Manage resource groups
-
Manage routing zones
-
Manage virtual networks
-
Manage virtual network endpoints
Blueprint Locking Feature
The blueprint locking feature prevents restricted users (based on their roles) from making changes that effectively are not permitted. In particular, a restricted user should not be able to commit changes made by another user.
If a blueprint has no changes to commit, it is unlocked.
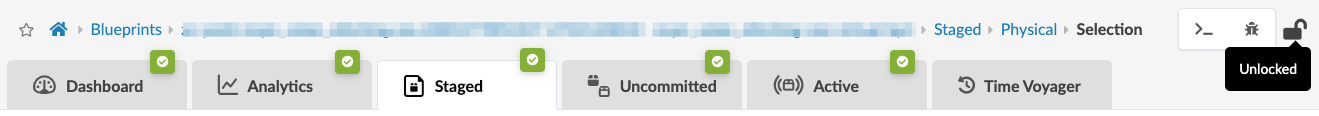
If you have permission (based on the your assigned roles) to create/update/delete virtual networks, for example, and another user has made uncommitted changes to the blueprint, the blueprint is locked. You can't create/update/delete virtual networks until the changes are committed or reverted by the locking user who made the uncommitted changes, unless you are the one who made the changes.
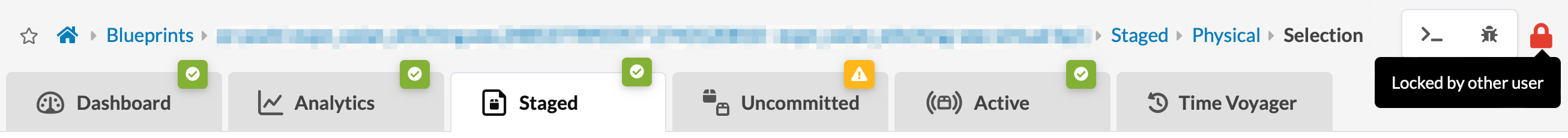
If you have permission (based on your assigned roles) to see the name of the user who created the pending changes, the name is displayed.
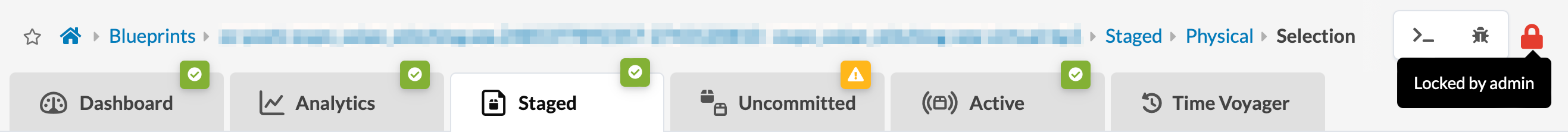
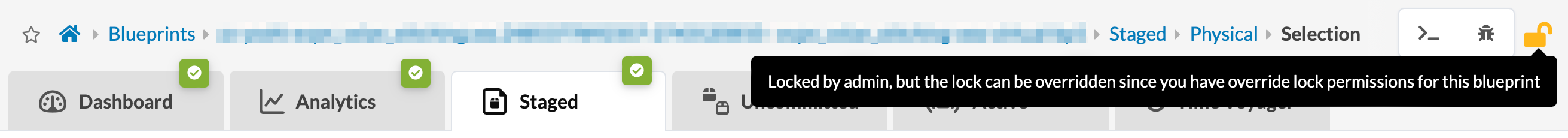
A user with "Allow overriding other users staged changes" permission can make any changes to, apply changes for, and revert changes for any blueprint.
Role-Based Access Control (RBAC)
You can map roles to external groups used by authentication providers such as LDAP, Active Directory, TACACS+, and RADIUS.
With Enhanced Role Based Access Control, you can create blueprint-specific roles with specific privileges allowing limited control to associated users. This allows you to create more hierarchical roles and protect against accidental changes to the network.
For example, a user assigned the role Manage generic systems can add generic systems, copy existing generics, add links to generic systems, add links to leaf devices, and update node tags. A user assigned the role Manage racks and links can perform all those operations plus they can change rack speeds and delete links. A user with the Manage racks and links role essentially has permissions for all FE/FFE operations. If you want to restrict a user to physical server operations only, assign them the Manage generic systems role, and not the Manage racks and links role.
Use Cases
These use cases are meant to give you an idea of how to work with roles and users. Specific steps for creating roles and users are described in later sections.
- Read, Write and Commit Specific Blueprints
- Manage VN Endpoints on Specific Blueprints
- Read and Write Resources on all Blueprints
- Create Virtual Networks only (not Including Allocating Resources)
- Create Virtual Networks and Allocate Resources
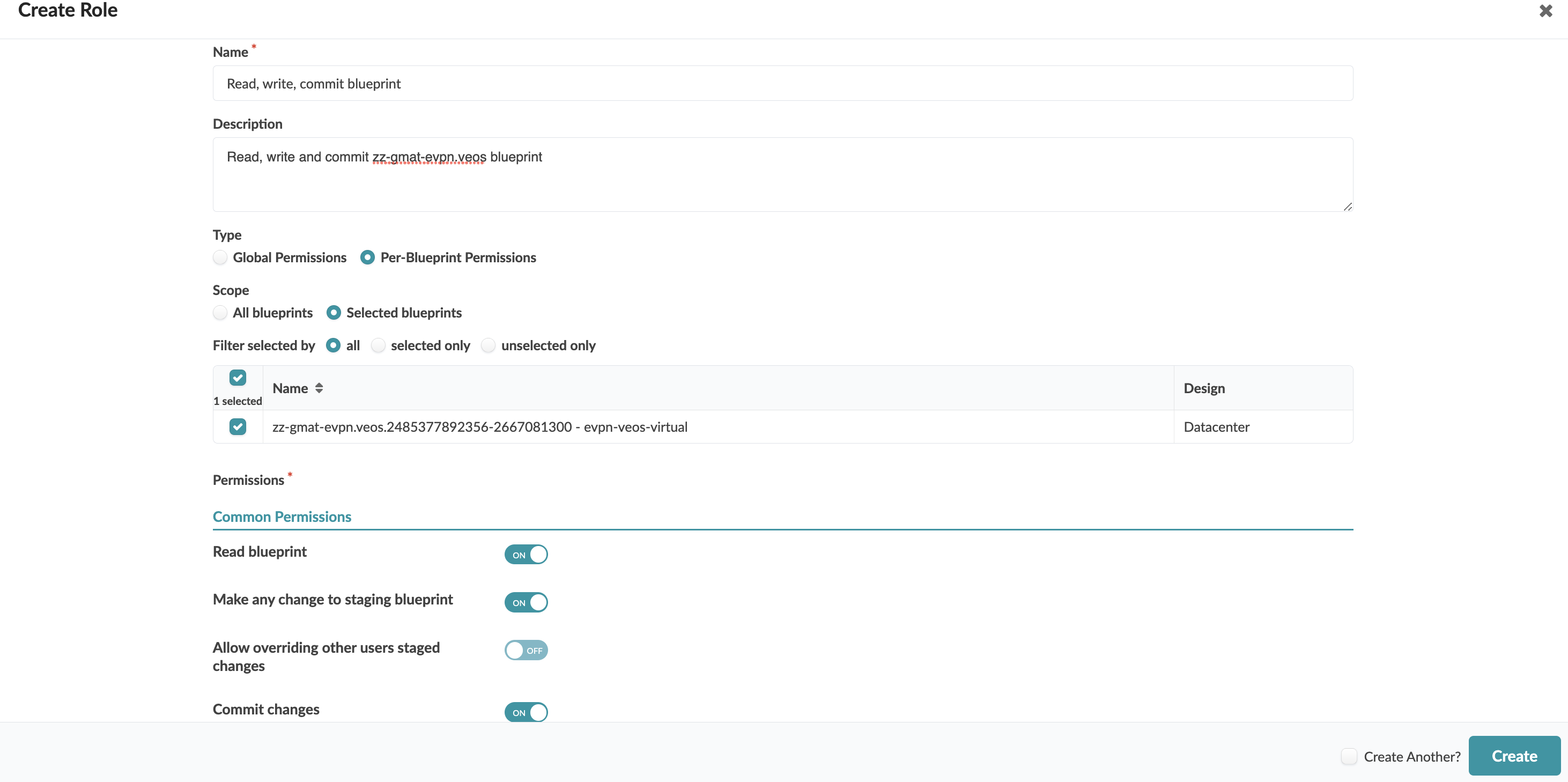
Read, Write and Commit Specific Blueprints
To allow a user to read, write and commit specific blueprints, create a per-blueprint permissions role for the specified blueprint(s). Toggle on Read blueprint, Make any change to staging blueprint, and Commit changes. These permissions include Manage virtual networks and Manage virtual network endpoints even though those permissions may or may not be toggled on. Assign the role to the user.
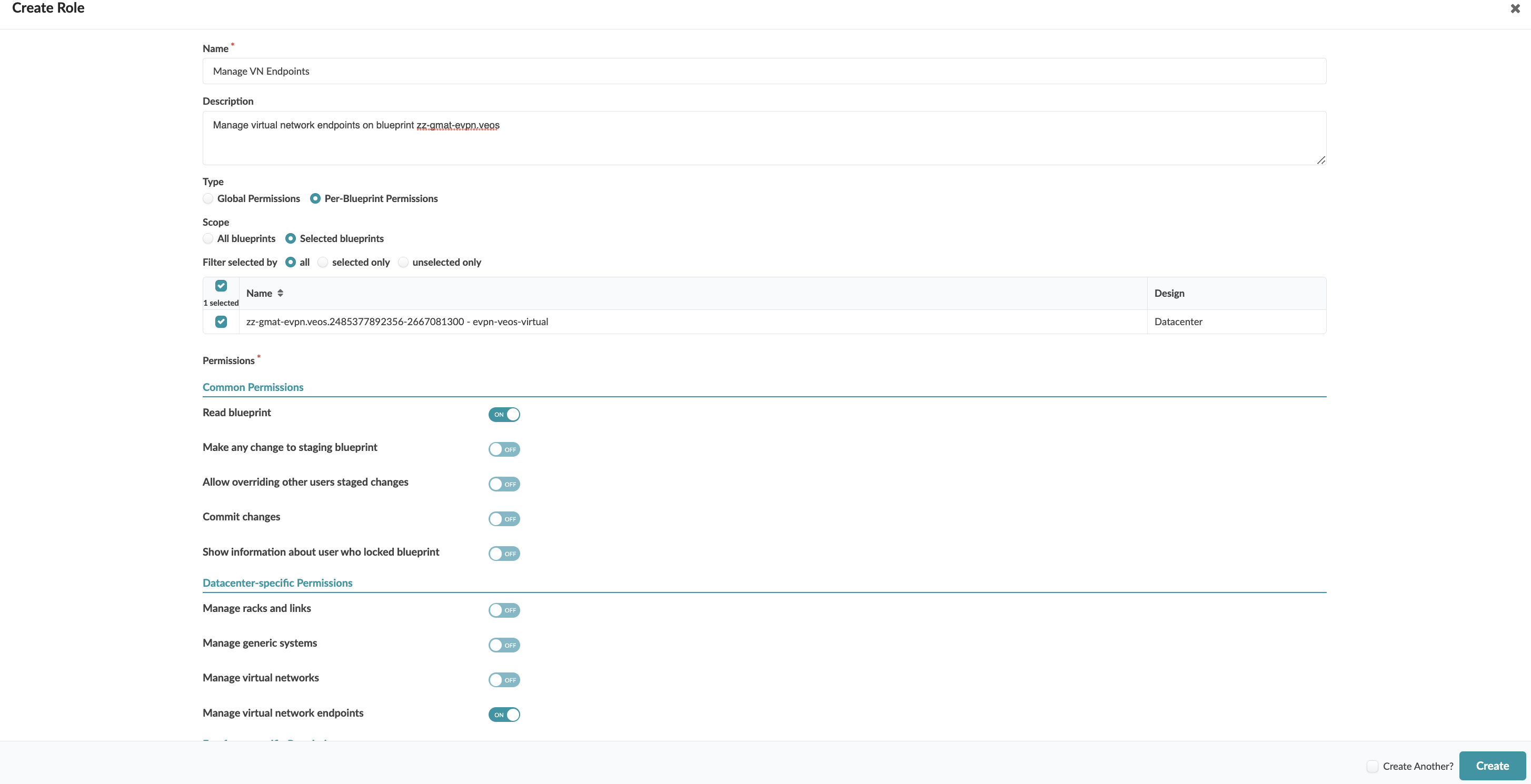
Manage VN Endpoints on Specific Blueprints
To allow a user to only manage virtual network endpoints on specific blueprints, select Per-Blueprint Permissions, select one or more blueprint IDs (or All for all blueprints), then toggle on Manage virtual network endpoints. Assign the role to the user.
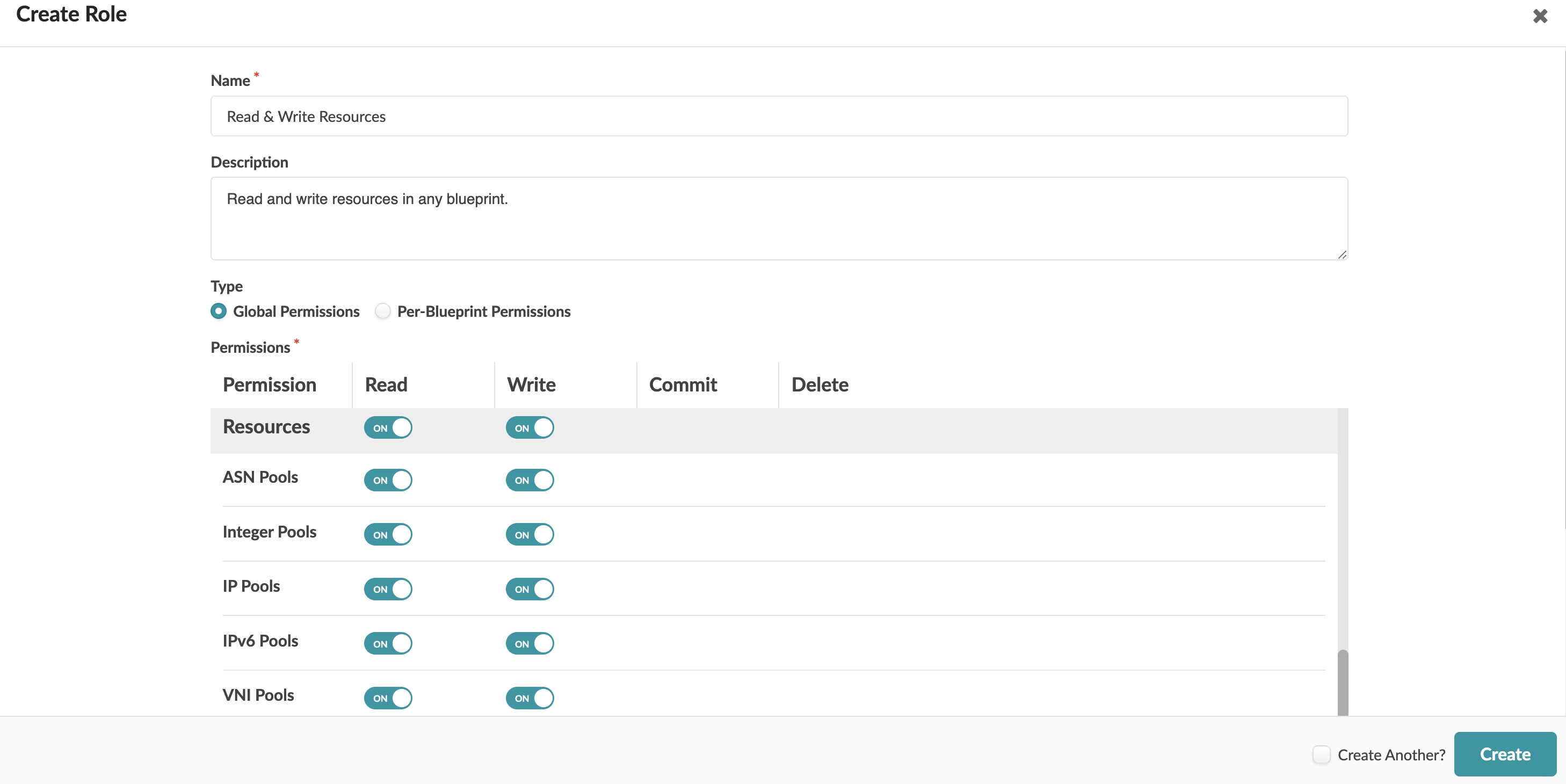
Read and Write Resources on all Blueprints
To allow a user to read and write resources on any blueprint, create a global permissions role. Toggle on Resources for Read and Write to toggle on all resources at once. Assign the role to the user.
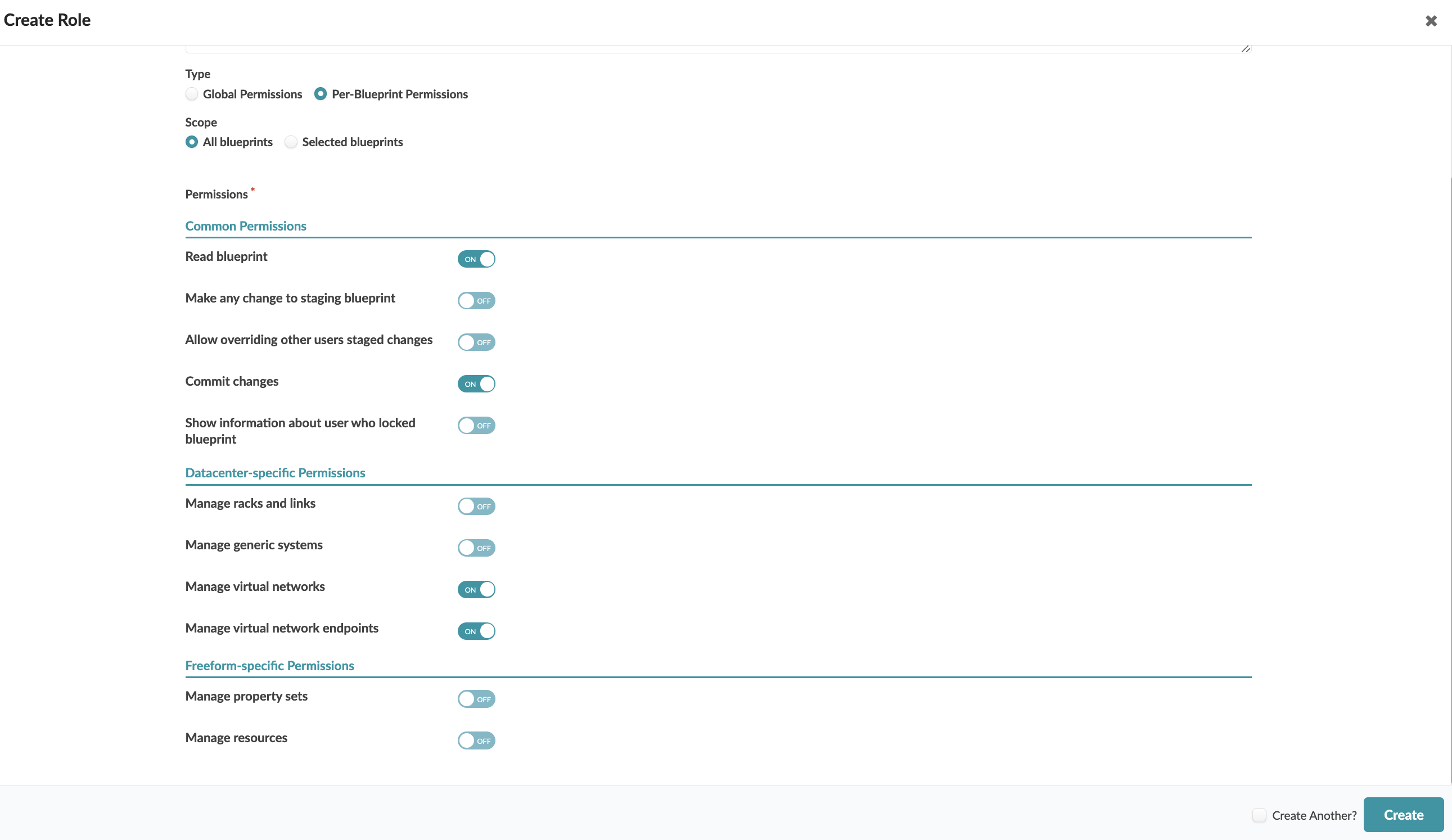
Create Virtual Networks only (not Including Allocating Resources)
To limit a user's role to only create virtual networks and look at blueprint details, create a role for Per-Blueprint Permissions, and either select specific blueprints or all blueprints. Then toggle on Read Blueprint, Commit changes, Manage virtual networks, and Manage virtual network endpoints. By not selecting Make any change to staging blueprint you are limiting the changes that can be made to virtual networks only. Assign the role to the user.
Create Virtual Networks and Allocate Resources
To be able to create virtual networks and allocate resources to them, you can assign several roles as follows:
-
Read and Write Resources on all Blueprints (described in previous section)
-
Create Virtual Networks Only (not Including Allocating Resources) (described in previous section) with the addition of toggling on Make any change to staging blueprint. This also permits a user with this role to make other changes besides virtual network changes.
