Introduction
Apstra manages network security and workload isolation through a Group Based Policy (GBP) framework. This GBP framework isn't necessarily new, and variants of the concept of using endpoint/group-based policy specifications can be found in OpenStack, for example. This feature allows you to create policies that are decoupled from enforcement mechanisms and allows specification of the intent in an implementation-independent way. Apstra's current reference design translates these policies into Access Lists (ACLs) for each supported vendor Network Operating System (NOS). These ACLs are installed on the associated L3 interfaces, controlling traffic flows between virtual networks and external systems.
Security policies allow or block traffic between endpoints based on their IP addresses, port numbers, and protocols. You create separate policies for each direction (ingress, egress) between endpoints, entire networks, or more specific host IP endpoints. The order of the rules matters! The security policies define permitted or denied communications in your data center fabric. An easy way to think about this is with a human analogy:
- Party A - A group of people
- Party B - Another group of people
- Conversation - What can they talk about? Should we block all mention of sports?
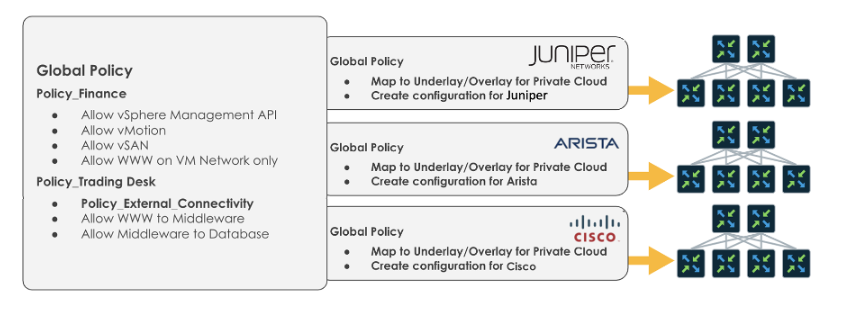
The following image visualizes Juniper Apstra's goal of decoupling policies from various policy mechanisms, enabling you to enforce policy intent without the need for tedious management.
Policy Assurance is designed to keep you, the architect or administrator, “above the fray.” You do not want to get into the weeds of managing ACL intricacies or the differences between vendor syntax.
Apstra provides a simple user interface, or API, that allows you to define policies to control traffic flow between virtual networks and IP endpoints. Policy Assurance radically simplifies the management of ACL and reduces ACL table size. Apstra automatically composes ACLs and applies them to routed interfaces, such as Switch Virtual Interfaces (SVI) or Integrated Routing and Bridging (IRB) interfaces for internal or external connectivity. ACLs are auto-rendered in the correct device syntax and applied to the relevant enforcement points. Adding a new VXLAN Endpoint, such as a rack or leaf, to a virtual network automatically places the ACL on the virtual network interface. Furthermore, Apstra can detect conflicts when multiple policies applied within a Blueprint overlap and automatically resolve the conflicts based on user settings such as More specific first or More generic first. You can search existing policies based on source/destination object and by type of traffic (protocol and port number) to determine if a particular traffic flow is affected by any active policies.
Further maintaining a responsive and effective security posture, Apstra ensures the network does not enter an open (free-flowing traffic) state while the rules are being provisioned. To minimize the potential impact on existing traffic flows of policy deployment, Apstra will automatically perform an incremental ACL deployment process for deploying policy changes on each enforcement point.
Security Policy Benefits
- Simplicity
- Vendor-agnostic GUI implementation for creating ACLs
- Introspection/visibility
- Given an endpoint/group, what are all the policies that apply to it (security, reachability, QoS)
-
Given a policy, which endpoints/groups it applies to
-
Conflict Detection (at the policy level)
-
Security conflicts, admission control constraints/priorities/pre-emption
-
-
Conflict resolution
-
Defaults (“more specific wins,” “override”)
-
Apstra automates merging multiple policies and assists with conflicts in remediation (both automated and user resolved). Policies are combined before device config rendering takes place, which ensures that Apstra can support rendering the final policy for multiple vendors. Apstra also ensures that the resulting vendor configuration syntax accurately reflects your intent.
Routing Policies are supported via Virtual Networks (VXLAN/VLAN) and Routing Zone (RZ), which are rendered as Virtual Routing and Forwarding (VRF) instances on physical devices. A Role-Based Access Control (RBAC) model also controls user privileges per Blueprint, Routing Zone, or Virtual Network basis.
Apstra enables customers to create granular security policies and enforcement across the entire Data Center between these constructs.