Step 2: Up and Running
Now that the SRX300 is powered on, let’s do some initial configuration to get it up and running on the network.
Be sure to check out our Guided Setup: SRX300 Line Firewalls. Our Guided Setup picks up where this Day One+ leaves off, providing step-by-step instructions on how to easily secure and validate your branch location.
SRX300 Provisioning Options
It’s simple to provision and manage the SRX300 and other devices on your network. Choose the configuration tool that’s right for you:
Junos CLI commands. In this guide we show you how to configure the SRX300 with CLI commands that leverage the plug and play factory defaults.
J-Web, Juniper Networks GUI that is preinstalled on the SRX300. For information on performing initial configuration using the J-Web setup wizard see Configure SRX Devices Using the J-Web Setup Wizard in the J-Web User Guide for SRX Series Devices.
Juniper Sky™ Enterprise, Juniper Networks-hosted public cloud-based Software as a Service (SaaS) solution. You’ll need to have a Juniper Sky Enterprise subscription service before you can use it to configure the SRX300. For more information, check out the Juniper Sky Enterprise Getting Started Guide.
Contrail Service Orchestration (CSO). If you are using Junos OS Release 19.2 or earlier, you can use Juniper Networks Network Service Controller to configure the SRX300 with ZTP. Network Service Controller is a component of CSO. See Configure the Device Using ZTP with Juniper Networks Network Service Controller.
To use CSO, you’ll need an authentication code. See the Contrail Service Orchestration (CSO ) Deployment Guide.
Initial Configuration Using the CLI
You can use the console port on the SRX to do the initial configuration. This section assumes you start from a factory default configuration. See SRX300 Firewall Hardware Guide for details on the SRX300 factory default configuration.
After you configure the SRX300, you can log in on a local LAN port, or remotely over the WAN interface, to manage and configure the SRX using the CLI or J-Web.
We recommend that you use the ge-0/0/0 interface for WAN connectivity on the SRX300. By default, this interface is set to receive its Internet access configuration from the service provider.
This examples assumes you are using DHCP to configure the WAN interface. If the WAN provider does not support DHCP, you’ll need to manually configure the WAN interface and related static routing. See Junos Initial Configuration.
Have this information handy before you begin the initial configuration:
Root password
Hostname
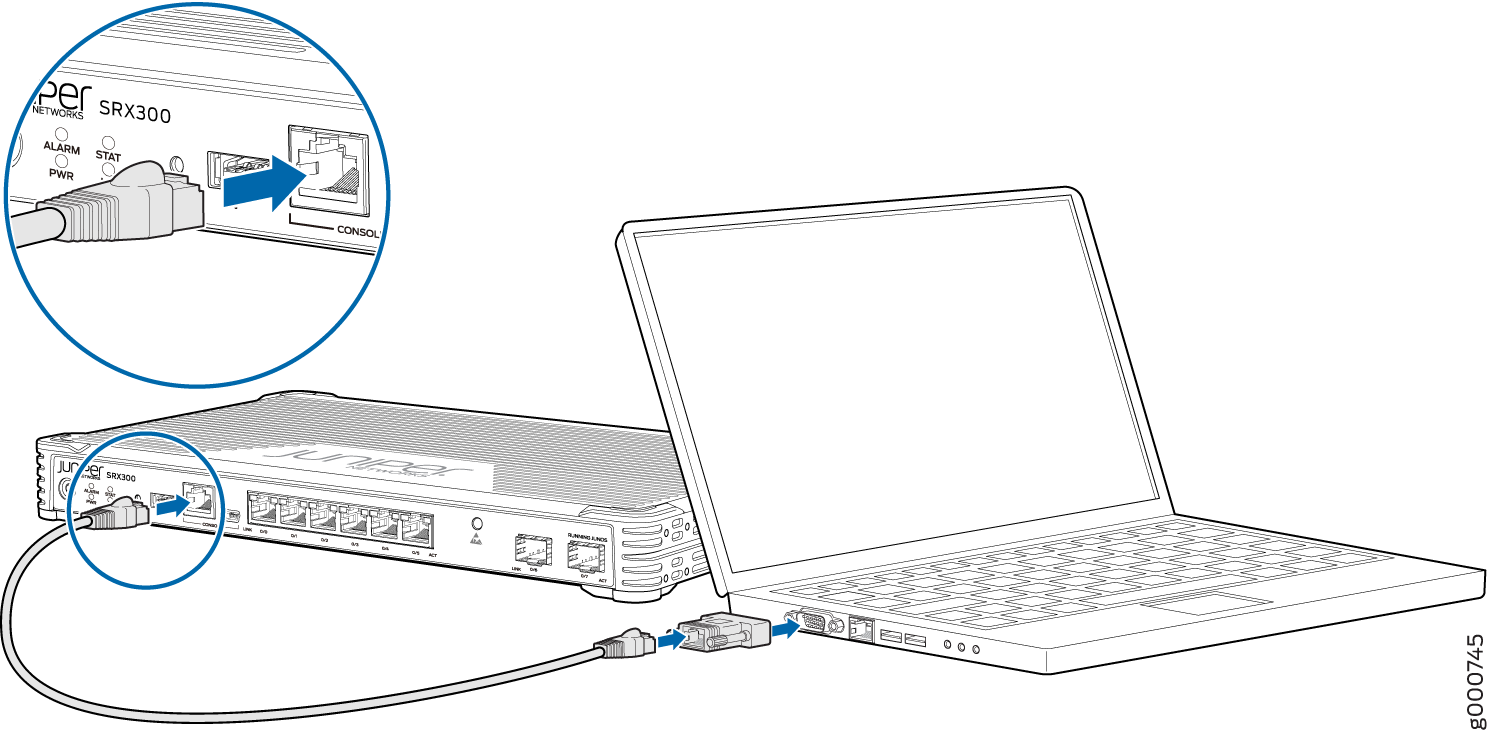
Connect to the Serial Console Port
You can also connect to the SRX300 using a mini-USB console port. See the SRX300 Hardware Guide.
Perform Initial Configuration
Congratulations! Your SRX is Up and Running
Your SRX300 is now online and providing secure Internet access to devices attached to the LAN ports. You can manage the device locally and remotely, using the Junos CLI, J-Web, or a cloud based provisioning service. Here's what your network looks like:
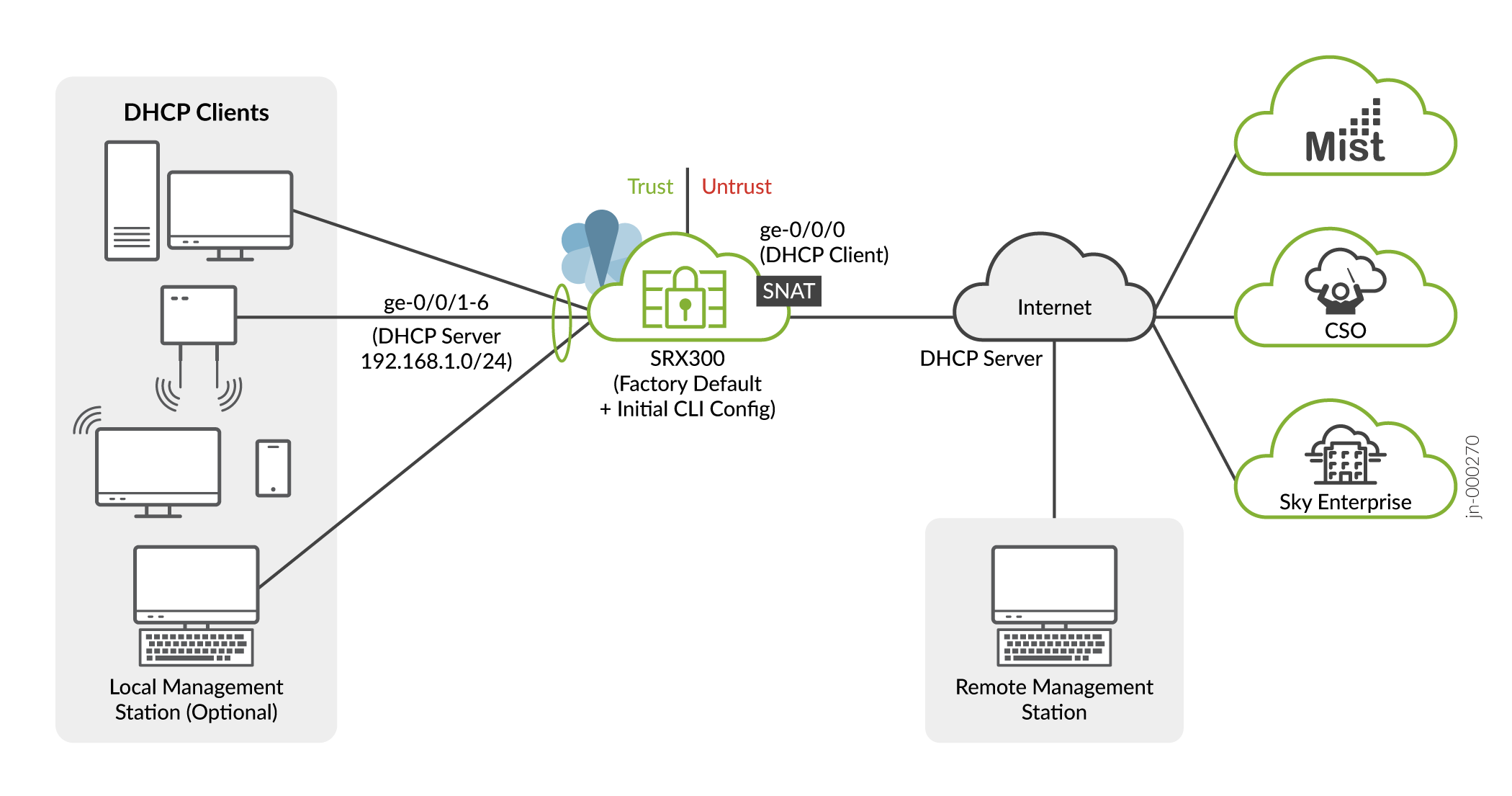
A few things to keep in mind about your new SRX300 branch network:
You access the SRX CLI or J-Web user interface locally using the 192.168.1.1 address. To access the SRX remotely, specify the IP address assigned by the WAN provider. Simply issue a
show interfaces ge-0/0/0 terseCLI command to confirm the address in use by the WAN interface.Devices attached to the LAN ports are configured to use DHCP. They receive their network configuration from the SRX. These devices obtain an IP address from the 192.168.1.0/24 address pool and use the SRX as their default gateway.
All LAN ports are in the same subnet with Layer 2 connectivity. All traffic is permitted between trust zone interfaces.
All traffic originating in the trust zone is permitted in the untrust zone. Matching response traffic is allowed back from the untrust to the trust zone. Traffic that originates from the untrust zone is blocked from the trust zone.
The SRX performs source NAT (S-NAT) using the WAN interface’s IP for traffic sent to the WAN that originated from the trust zone.
Traffic associated with specific system services (HTTPS, DHCP, TFTP, and SSH) is permitted from the untrust zone to the local host. All local host services and protocols are allowed for traffic that originates from the trust zone.
If you’d like to quickly configure and validate a secure branch office, be sure to check out our Guided Setup: SRX300 Line Firewalls.