ON THIS PAGE
Using QFX5100, QFX5110, QFX5120, QFX5200, QFX5210, EX4300-48MP, and EX4600 Switches with VXLANs
Changing the UDP Port on QFX5100, QFX5110, QFX5200, QFX5210, and EX4600 Switches
Controlling Transit Multicast Traffic on QFX5100, QFX5110, QFX5200, QFX5210, and EX4600 Switches
Using an MX Series Router, EX9200 Switch, or QFX10000 Switch as a VTEP
Enabling QFX5120 Switches to Tunnel Traffic on Core-Facing Layer 3 Tagged and IRB Interfaces
Understanding VXLANs
Virtual Extensible LAN protocol (VXLAN) technology allows networks to support more VLANs. According to the IEEE 802.1Q standard, traditional VLAN identifiers are 12 bits long—this naming limits networks to 4094 VLANs. The VXLAN protocol overcomes this limitation by using a longer logical network identifier that allows more VLANs and, therefore, more logical network isolation for large networks such as clouds that typically include many virtual machines.
VXLAN Benefits
VXLAN technology allows you to segment your networks (as VLANs do), but it provides benefits that VLANs cannot. Here are the most important benefits of using VXLANs:
You can theoretically create as many as 16 million VXLANs in an administrative domain (as opposed to 4094 VLANs on a Juniper Networks device).
MX Series routers and EX9200 switches support as many as 32,000 VXLANs, 32,000 multicast groups, and 8000 virtual tunnel endpoints (VTEPs). This means that VXLANs based on MX Series routers provide network segmentation at the scale required by cloud builders to support very large numbers of tenants.
QFX10000 Series switches support 4000 VXLANs and 2000 remote VTEPs.
QFX5100, QFX5110, QFX5200, QFX5210, and EX4600 switches support 4000 VXLANs, 4000 multicast groups, and 2000 remote VTEPs.
EX4300-48MP switches support 4000 VXLANs.
You can enable migration of virtual machines between servers that exist in separate Layer 2 domains by tunneling the traffic over Layer 3 networks. This functionality allows you to dynamically allocate resources within or between data centers without being constrained by Layer 2 boundaries or being forced to create large or geographically stretched Layer 2 domains.
Using VXLANs to create smaller Layer 2 domains that are connected over a Layer 3 network means that you do not need to use Spanning Tree Protocol (STP) to converge the topology but can use more robust routing protocols in the Layer 3 network instead. In the absence of STP, none of your links are blocked, which means you can get full value from all the ports that you purchase. Using routing protocols to connect your Layer 2 domains also allows you to load-balance the traffic to ensure that you get the best use of your available bandwidth. Given the amount of east-west traffic that often flows within or between data centers, maximizing your network performance for that traffic is very important.
The video Why Use an Overlay Network in a Data Center? presents a brief overview of the advantages of using VXLANs.
How Does VXLAN Work?
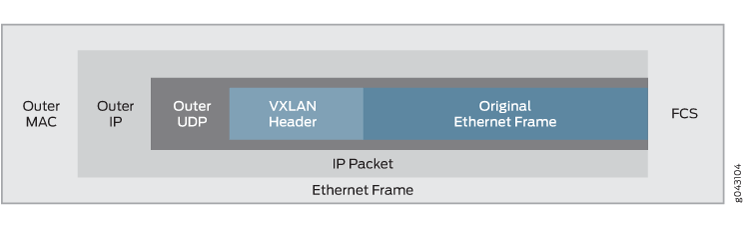
VXLAN is often described as an overlay technology because it allows you to stretch Layer 2 connections over an intervening Layer 3 network by encapsulating (tunneling) Ethernet frames in a VXLAN packet that includes IP addresses. Devices that support VXLANs are called virtual tunnel endpoints (VTEPs)—they can be end hosts or network switches or routers. VTEPs encapsulate VXLAN traffic and de-encapsulate that traffic when it leaves the VXLAN tunnel. To encapsulate an Ethernet frame, VTEPs add a number of fields, including the following fields:
Outer media access control (MAC) destination address (MAC address of the tunnel endpoint VTEP)
Outer MAC source address (MAC address of the tunnel source VTEP)
Outer IP destination address (IP address of the tunnel endpoint VTEP)
Outer IP source address (IP address of the tunnel source VTEP)
Outer UDP header
A VXLAN header that includes a 24-bit field—called the VXLAN network identifier (VNI)—that is used to uniquely identify the VXLAN. The VNI is similar to a VLAN ID, but having 24 bits allows you to create many more VXLANs than VLANs.
Because VXLAN adds 50 to 54 bytes of additional header information to the original Ethernet frame, you might want to increase the MTU of the underlying network. In this case, configure the MTU of the physical interfaces that participate in the VXLAN network, not the MTU of the logical VTEP source interface, which is ignored.
Figure 1 shows the VXLAN packet format.
VXLAN Implementation Methods
Junos OS supports implementing VXLANs in the following environments:
Manual VXLAN—In this environment, a Juniper Networks device acts as a transit device for downstream devices acting as VTEPs, or a gateway that provides connectivity for downstream servers that host virtual machines (VMs), which communicate over a Layer 3 network. In this environment, software-defined networking (SDN) controllers are not deployed.
Note:QFX10000 switches do not support manual VXLANs.
OVSDB-VXLAN—In this environment, SDN controllers use the Open vSwitch Database (OVSDB) management protocol to provide a means through which controllers (such as a VMware NSX or Juniper Networks Contrail controller) and Juniper Networks devices that support OVSDB can communicate.
EVPN-VXLAN—In this environment, Ethernet VPN (EVPN) is a control plane technology that enables hosts (physical servers and VMs) to be placed anywhere in a network and remain connected to the same logical Layer 2 overlay network, and VXLAN creates the data plane for the Layer 2 overlay network.
Using QFX5100, QFX5110, QFX5120, QFX5200, QFX5210, EX4300-48MP, and EX4600 Switches with VXLANs
You can configure the switches to perform all of the following roles:
(All switches except EX4300-48MP) In an environment without an SDN controller, act as a transit Layer 3 switch for downstream hosts acting as VTEPs. In this configuration, you do not need to configure any VXLAN functionality on the switch. You do need to configure IGMP and PIM so that the switch can form the multicast trees for the VXLAN multicast groups. (See Manual VXLANs Require PIM for more information.)
(All switches except EX4300-48MP) In an environment with or without an SDN controller, act as a Layer 2 gateway between virtualized and nonvirtualized networks in the same data center or between data centers. For example, you can use the switch to connect a network that uses VXLANs to one that uses VLANs.
(EX4300-48MP switches) Act as a Layer 2 gateway between virtualized and nonvirtualized networks in a campus network. For example, you can use the switch to connect a network that uses VXLANs to one that uses VLANs.
(All switches except EX4300-48MP) Act as a Layer 2 gateway between virtualized networks in the same or different data centers and allow virtual machines to move (VMotion) between those networks and data centers. For example, if you want to allow VMotion between devices in two different networks, you can create the same VLAN in both networks and put both devices on that VLAN. The switches connected to these devices, acting as VTEPs, can map that VLAN to the same VXLAN, and the VXLAN traffic can then be routed between the two networks.
(QFX5110 and QFX5120 switches with EVPN-VXLAN) Act as a Layer 3 gateway to route traffic between different VXLANs in the same data center.
(QFX5110 and QFX5120 switches with EVPN-VXLAN) Act as a Layer 3 gateway to route traffic between different VXLANs in different data centers over a WAN or the Internet using standard routing protocols or virtual private LAN service (VPLS) tunnels.
If you want a QFX5110 or QFX5120 switch to be a Layer 3 VXLAN gateway in an EVPN-VXLAN environment, you must configure integrated routing and bridging (IRB) interfaces to connect the VXLANs, just as you do if you want to route traffic between VLANs.
Because the additional headers add 50 to 54 bytes, you might need to increase the MTU on a VTEP to accommodate larger packets. For example, if the switch is using the default MTU value of 1514 bytes and you want to forward 1500-byte packets over the VXLAN, you need to increase the MTU to allow for the increased packet size caused by the additional headers.
Changing the UDP Port on QFX5100, QFX5110, QFX5200, QFX5210, and EX4600 Switches
Starting with Junos OS Release 14.1X53-D25 on QFX5100 switches, Junos OS Release 15.1X53-D210 on QFX5110 and QFX5200 switches, Junos OS Release 18.1R1 on QFX5210 switches, and Junos OS Release 18.2R1 on EX4600 switches, you can configure the UDP port used as the destination port for VXLAN traffic. To configure the VXLAN destination port to be something other than the default UDP port of 4789, enter the following statement:
set protocols l2-learning destination-udp-port port-number
The port you configure will be used for all VXLANs configured on the switch.
If you make this change on one switch in a VXLAN, you must make the same change on all the devices that terminate the VXLANs configured on your switch. If you do not do so, traffic will be disrupted for all the VXLANs configured on your switch. When you change the UDP port, the previously learned remote VTEPs and remote MACs are lost and VXLAN traffic is disrupted until the switch relearns the remote VTEPs and remote MACs.
Host Entry Overflow Prevention
By default, when the host table reaches its capacity, additional host entries overflow into the Longest Prefix Match (LPM) table. This can cause a degradation of routing performance that results from smaller host entries consuming valuable space in the LPM table.
Starting with Junos OS Release 25.2R1, you can prevent host entries from spilling
over into the LPM table by configuring the set forwarding-options
no-host-as-lpm statement. When you enable this option, host entries are
blocked from entering the LPM table, and an error message is logged to notify you of
the full host table condition. This restriction maintains the LPM table's integrity
for larger subnet routes, which are typically more critical for efficient network
operation. This configuration requires a PFE restart to clear any existing host
entries from the LPM table, ensuring that the table is dedicated solely to subnet
routes moving forward. The restart is crucial for maintaining a clean state, as it
prevents any residual host entries from affecting table space utilization.
Configuring the set forwarding-options no-host-as-lpm statement restarts
the PFE in standalone devices. Virtual Chassis (VC) devices require a manual
restart. Restarting the PFE removes any previously learned host entries from the
LPM table.
Host entry overflow prevention is particularly beneficial for environments with high host entry demands. The feature supports both IPv4 and IPv6 routes and applies to VXLAN and non-VXLAN environments, making it versatile for various deployment scenarios. Segregating host and subnet routes avoids the degradation of routing performance that results from host entries spilling over to the LPM table. Additionally, the system generates a system log message each time you toggle the CLI option, providing an audit trail for change management and troubleshooting. By leveraging this feature, you can enhance routing table management, improve routing efficiency, and ensure systematic control over routing table entries.
Please refer to Feature Explorer for a complete list of the products that support the host entry overflow prevention feature.
CLI Commands
To configure the host entry overflow prevention feature, use the following CLI command:
set forwarding-options no-host-as-lpm
This command enables the feature that blocks host entries from being added to the LPM table when the host table is full, preserving LPM space for larger subnet routes.
To verify the status of the host entry overflow prevention feature, use the command:
show forwarding-options no-host-as-lpm
This command displays the current configuration status, indicating whether the feature is enabled or disabled.
To display the a summary of the routes in the Packet Forwarding Engine Host and LPM forwarding tables, use the command:
show pfe route summary
hw
By using these commands, you can effectively manage and monitor the routing table entries, ensuring optimal performance and scalability in your network environment.
Controlling Transit Multicast Traffic on QFX5100, QFX5110, QFX5200, QFX5210, and EX4600 Switches
When the switch acting as a VTEP receives a broadcast, unknown unicast, or multicast packet, it performs the following actions on the packet:
It de-encapsulates the packet and delivers it to the locally attached hosts.
It then adds the VXLAN encapsulation again and sends the packet to the other VTEPs in the VXLAN.
These actions are performed by the loopback interface used as the VXLAN tunnel address and can, therefore, negatively impact the bandwidth available to the VTEP. Starting with Junos OS Release 14.1X53-D30 for QFX5100 switches, Junos OS Release 15.1X53-D210 for QFX5110 and QFX5200 switches, Junos OS Release 18.1R1 for QFX5210 switches, and Junos OS Release 18.2R1 for EX4600 switches, if you know that there are no multicast receivers attached to other VTEPs in the VXLAN that want traffic for a specific multicast group, you can reduce the processing load on the loopback interface by entering the following statement:
set protocols l2-learning disable-vxlan-multicast-transit vxlan-multicast-group multicast-group
In this case, no traffic will be forwarded for the specified group but all other multicast traffic will be forwarded. If you do not want to forward any multicast traffic to other VTEPs in the VXLAN, enter the following statement:
set protocols l2-learning disable-vxlan-multicast-transit vxlan-multicast-group all
Using an MX Series Router, EX9200 Switch, or QFX10000 Switch as a VTEP
You can configure an MX Series router, EX9200 switch, or QFX10000 switch to act as a VTEP and perform all of the following roles:
Act as a Layer 2 gateway between virtualized and nonvirtualized networks in the same data center or between data centers. For example, you can use an MX Series router to connect a network that uses VXLANs to one that uses VLANs.
Act as a Layer 2 gateway between virtualized networks in the same or different data centers and allow virtual machines to move (VMotion) between those networks and data centers.
Act as a Layer 3 gateway to route traffic between different VXLANs in the same data center.
Act as a Layer 3 gateway to route traffic between different VXLANs in different data centers over a WAN or the Internet using standard routing protocols or virtual private LAN service (VPLS) tunnels.
If you want one of the devices described in this section to be a VXLAN Layer 3 gateway, you must configure integrated routing and bridging (IRB) interfaces to connect the VXLANs, just as you do if you want to route traffic between VLANs.
Manual VXLANs Require PIM
In an environment with a controller (such as a VMware NSX or Juniper Networks Contrail controller), you can provision VXLANs on a Juniper Networks device. A controller also provides a control plane that VTEPs use to advertise their reachability and learn about the reachability of other VTEPs. You can also manually create VXLANs on Juniper Networks devices instead of using a controller. If you use this approach, you must also configure Protocol Independent Multicast (PIM) on the VTEPs so that they can create VXLAN tunnels between themselves.
You must also configure each VTEP in a given VXLAN to be a member of the same multicast group. (If possible, you should assign a different multicast group address to each VXLAN, although this is not required. Multiple VXLANs can share the same multicast group.) The VTEPs can then forward ARP requests they receive from their connected hosts to the multicast group. The other VTEPs in the group de-encapsulate the VXLAN information, and (assuming they are members of the same VXLAN) they forward the ARP request to their connected hosts. When the target host receives the ARP request, it responds with its MAC address, and its VTEP forwards this ARP reply back to the source VTEP. Through this process, the VTEPs learn the IP addresses of the other VTEPs in the VXLAN and the MAC addresses of the hosts connected to the other VTEPs.
The multicast groups and trees are also used to forward broadcast, unknown unicast, and multicast (BUM) traffic between VTEPs. This prevents BUM traffic from being unnecessarily flooded outside the VXLAN.
Multicast traffic that is forwarded through a VXLAN tunnel is sent only to the remote VTEPs in the VXLAN. That is, the encapsulating VTEP does not copy and send copies of the packets according to the multicast tree—it only forwards the received multicast packets to the remote VTEPs. The remote VTEPs de-encapsulate the encapsulated multicast packets and forward them to the appropriate Layer 2 interfaces.
Load Balancing VXLAN Traffic
The Layer 3 routes that form VXLAN tunnels use per-packet load balancing by default, which means that load balancing is implemented if there are ECMP paths to the remote VTEP. This is different from normal routing behavior in which per-packet load balancing is not used by default. (Normal routing uses per-prefix load balancing by default.)
The source port field in the UDP header is used to enable ECMP load balancing of the VXLAN traffic in the Layer 3 network. This field is set to a hash of the inner packet fields, which results in a variable that ECMP can use to distinguish between tunnels (flows).
None of the other fields that flow-based ECMP normally uses are suitable for use with VXLANs. All tunnels between the same two VTEPs have the same outer source and destination IP addresses, and the UDP destination port is set to port 4789 by definition. Therefore, none of these fields provide a sufficient way for ECMP to differentiate flows.
Enabling QFX5120 Switches to Tunnel Traffic on Core-Facing Layer 3 Tagged and IRB Interfaces
This section applies only to QFX5120 switches running Junos OS Releases 18.4R1, 18.4R2, 18.4R2-S1 through 18.4R2-S3, 19.1R1, 19.1R2, 19.2Rx, and 19.3Rx.
When a QFX5120 switch attempts to tunnel traffic on core-facing Layer 3 tagged interfaces or IRB interfaces, the switch drops the packets. To avoid this issue, you can configure a simple two-term filter-based firewall on the Layer 3 tagged or IRB interface.
QFX5120 switches support a maximum of 256 two-term filter-based firewalls.
For example:
set interfaces et-0/0/3 unit 0 family inet filter input vxlan100 set firewall family inet filter vxlan100 term 1 from destination-address 192.168.0.1/24 then accept set firewall family inet filter vxlan100 term 2 then routing-instance route1
Term 1 matches and accepts traffic that is destined for the QFX5210 switch, which is identified by the source VTEP IP address (192.168.0.1/24) assigned to the switch's loopback interface. For term 1, note that when specifying an action, you can alternatively count traffic instead of accepting it.
Term 2 matches and forwards all other data traffic to a routing instance (route 1), which is configured interface et-0/0/3.
In this example, note that interface et-0/0/3 is referenced
by routing instance route1. As a result, you must include the set firewall family inet filter vxlan100 term 2 then routing-instance
route1 command. Without this command, the firewall filter will
not work properly.
Using ping and traceroute with a VXLAN
On QFX5100 and QFX5110 switches, you can use the ping and traceroute commands to troubleshoot traffic flow
through a VXLAN tunnel by including the overlay parameter
and various options. You use these options to force the ping or traceroute packets to follow the same path as data
packets through the VXLAN tunnel. In other words, you make the underlay
packets (ping and traceroute) take the same
route as the overlay packets (data traffic). See ping overlay and traceroute overlay for more information.
Supported VXLAN Standards
RFCs and Internet drafts that define standards for VXLAN:
RFC 7348, Virtual eXtensible Local Area Network (VXLAN): A Framework for Overlaying Virtualized Layer 2 Networks over Layer 3 Networks
Internet draft draft-ietf-nvo3-vxlan-gpe, Generic Protocol Extension for VXLAN
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
