Supervisar el estado del servicio de los firewalls de la serie SRX
Siga estos pasos para comprobar el estado del filtrado web, la detección de intrusiones y la seguridad de las aplicaciones.
Puede supervisar el estado del servicio de las siguientes funciones en su firewall de la serie SRX de Juniper Networks® en el portal de la nube de Juniper Mist™:
-
Filtrado web mejorado (EWF)
-
IDP
-
Seguridad de aplicaciones
Necesita una licencia válida para que su firewall de la serie SRX pueda usar la función. Para obtener más información sobre los requisitos de licencia y la instalación, consulte la Guía del usuario de licencias de Juniper.
En el firewall de la serie SRX, utilice el show system license comando para mostrar el nombre de la licencia con la fecha de caducidad.
user@host> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 2022-04-28 00:00:00 UTC
idp-sig 0 1 0 2022-04-28 00:00:00 UTC
dynamic-vpn 0 2 0 permanent
av_key_sophos_engine 0 1 0 2022-04-28 00:00:00 UTC
logical-system 1 3 0 permanent
wf_key_websense_ewf 0 1 0 2022-04-28 00:00:00 UTC
remote-access-ipsec-vpn-client 0 2 0 permanent
Licenses installed:
License identifier: DemoLabJUNOS386107562
License version: 4
Valid for device: CV4720AF0436
Customer ID: Juniper Internal
Features:
av_key_sophos_engine - Anti Virus with Sophos Engine
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
anti_spam_key_sbl - Anti-Spam
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
idp-sig - IDP Signature
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
wf_key_websense_ewf - Web Filtering EWF
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
Comprobar el estado de EWF
Para comprobar el estado de configuración del Filtrado web mejorado (EWF):
- Confirme si EWF está habilitado en su firewall de la serie SRX en modo operativo de CLI:
user@host> show security utm web-filtering status UTM web-filtering status: Server status: no-config root@00c52c4c3204>
El estado del servidor: no-config indica que el EWF no está configurado.
- Configure EWF en su firewall de la serie SRX mediante la CLI en el nivel jerárquico [editar]. Utilice el modo de configuración y confirme la configuración.
Nota:
Hemos capturado la siguiente configuración de un entorno de laboratorio y la hemos proporcionado solo con fines de referencia. Su propia configuración puede variar en función de los requisitos específicos de su entorno.
[edit] set system syslog file utm-log any any set system syslog file utm-log match RT_UTM set security utm custom-objects url-pattern blacklist value https://*.poki.com set security utm custom-objects custom-url-category restricted value blacklist set security utm default-configuration anti-virus type sophos-engine set security utm default-configuration anti-virus scan-options uri-check set security utm default-configuration anti-virus scan-options timeout 30 set security utm default-configuration anti-virus sophos-engine sxl-timeout 5 set security utm default-configuration web-filtering url-blacklist restricted set security utm default-configuration web-filtering type juniper-enhanced set security utm default-configuration web-filtering juniper-enhanced server host rp.cloud.threatseeker.com set security utm default-configuration web-filtering juniper-enhanced server port 80 set security utm default-configuration web-filtering juniper-enhanced default permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Games action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Gambling action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Abused_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Material action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Command_and_Control action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Payloads action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bot_Networks action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Compromised_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Emerging_Exploits action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Files_Containing_Passwords action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Hacking action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Illegal_or_Questionable action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Keyloggers action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_iFrame action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Web_Sites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Militancy_and_Extremist action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Mobile_Malware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Network_Errors action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Newly_Registered_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pay_to_Surf action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Phishing_and_Other_Frauds action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Damaging_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Exploited_Documents action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Unwanted_Software action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Racism_and_Hate action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Spyware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Unauthorized_Mobile_Marketplaces action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Alcohol_and_Tobacco action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Application_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bandwidth action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Computer_Security action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Custom_Encrypted_Payloads action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Elevated_Exposure action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment_Video action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_File_Download_Servers action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Freeware_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Instant_Messaging action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Auctions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Radio_and_TV action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Intolerance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Lingerie_and_Swimsuit action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Marijuana action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Media_File_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Message_Boards_and_Forums action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions_and_Occult_and_Folklore action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Nudity action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Parked_Domain action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Peer_to_Peer_File_Sharing action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Personals_and_Dating action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Prescribed_Medications action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Private_IP_Addresses action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Choice action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Life action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Proxy_Avoidance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex_Education action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Social_Networking_and_Personal_Sites action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Surveillance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Tasteless action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Violence action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Web_and_Email_Spam action log-and-permit set security utm utm-policy custom-utm-policy anti-virus http-profile junos-av-defaults set security utm utm-policy custom-utm-policy web-filtering http-profile wf-home
-
Compruebe el estado en el modo operativo de la CLI.
user@host> show security utm web-filtering status UTM web-filtering status: Server status: Juniper Enhanced using Websense server UP
Ahora, el estado cambia a Estado del servidor: Juniper Enhanced using Websense server UP. Este estado indica que el servicio EWF está habilitado en su dispositivo.
- Puede comprobar el estado en el portal de la nube de Juniper Mist, como se muestra en la figura 1.
Comprobar el estado de los desplazados internos
Antes de configurar la detección y prevención de intrusiones (IDP), debe descargar e instalar el paquete de seguridad de IDP siguiendo estos pasos:
-
Descargue el paquete IDP siguiendo las instrucciones del comando de descarga del paquete de seguridad IDP de seguridad de solicitud de seguridad.
-
Instale el paquete siguiendo las instrucciones del comando request security idp security-package install .
En este ejemplo se utilizan las plantillas de IDP que se descargan e instalan de la siguiente manera: .
- Descargue la plantilla de IDP siguiendo las instrucciones del comando solicitar seguridad del paquete de seguridad del IDP descargar plantillas de políticas .
- Instale las plantillas siguiendo las instrucciones del comando request security idp security-package install policy-templates .
- Active el script de confirmación de plantilla:
[edit] user@host-1# set system scripts commit file templates.xsl
Las plantillas descargadas se guardan en la base de datos de configuración de Junos OS y están disponibles en la CLI en el nivel jerárquico
[edit security idp idp-policy]. Active la directiva predefinida como la política activa. En este ejemplo, se usa
Recommendedla directiva como directiva activa.[edit] user@host-1# set security idp default-policy Recommended user@host-1# set security idp active-policy Recommended
- Habilite la directiva de IDP en su configuración. El siguiente fragmento de código muestra un ejemplo de configuración.
set security idp idp-policy idpengine rulebase-ips rule 1 match from-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match source-address any set security idp idp-policy idpengine rulebase-ips rule 1 match to-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match destination-address any set security idp idp-policy idpengine rulebase-ips rule 1 match application junos-echo set security idp idp-policy idpengine rulebase-ips rule 1 match attacks predefined-attack-groups Critical
- Utilice los siguientes comandos en modo operativo para comprobar el estado de la directiva del IDP:
- Política de desplazados internos recomendada:
show security idp policies - Nombre de la directiva:
show security idp policies - Estado del desplazado interno:
show security idp status
- Compruebe el estado del IDP en el portal de Juniper Mist Cloud como se muestra en la figura 1 .
- Política de desplazados internos recomendada:
Configurar la seguridad de la aplicación
En el firewall de la serie SRX, la seguridad de aplicaciones está habilitada de forma predeterminada si tiene una licencia válida. El equipo de OC se asegura de que todos los dispositivos tengan la versión de firma de aplicación más actualizada. Si desea cambiar la versión o instalar una versión personalizada, consulte Firmas de aplicación predefinidas para la identificación de aplicaciones.
Ver el estado del servicio de seguridad en Juniper Mist Cloud Portal
En el portal de la nube de Juniper Mist, puede ver el estado de los servicios de seguridad en el panel SERVICIOS DE SEGURIDAD . En el cuadro 1 se detallan la situación.
| Significado de estado de visualización de | servicios de seguridad | |
|---|---|---|
| EWF | Habilitado | La conexión al servidor de Websense está activa. |
| Deshabilitado | EWF no está configurado en su dispositivo. | |
| Abajo | La conexión al servidor de Websense está inactiva. | |
| IDP | Habilitado | Se configura el IDP y se aplica la directiva del IDP. |
| Deshabilitado | El IDP no está configurado. En este caso, el nombre de la directiva de IDP se muestra en blanco. | |
| Seguridad de aplicaciones | Habilitado | La seguridad de la aplicación está habilitada. Se muestra la versión de firma de la aplicación. |
| Deshabilitado | La seguridad de la aplicación no está habilitada. La versión de firma de la aplicación se muestra como cero. |
La figura 1 muestra el estado de los servicios de seguridad en el portal de nube de Juniper Mist.
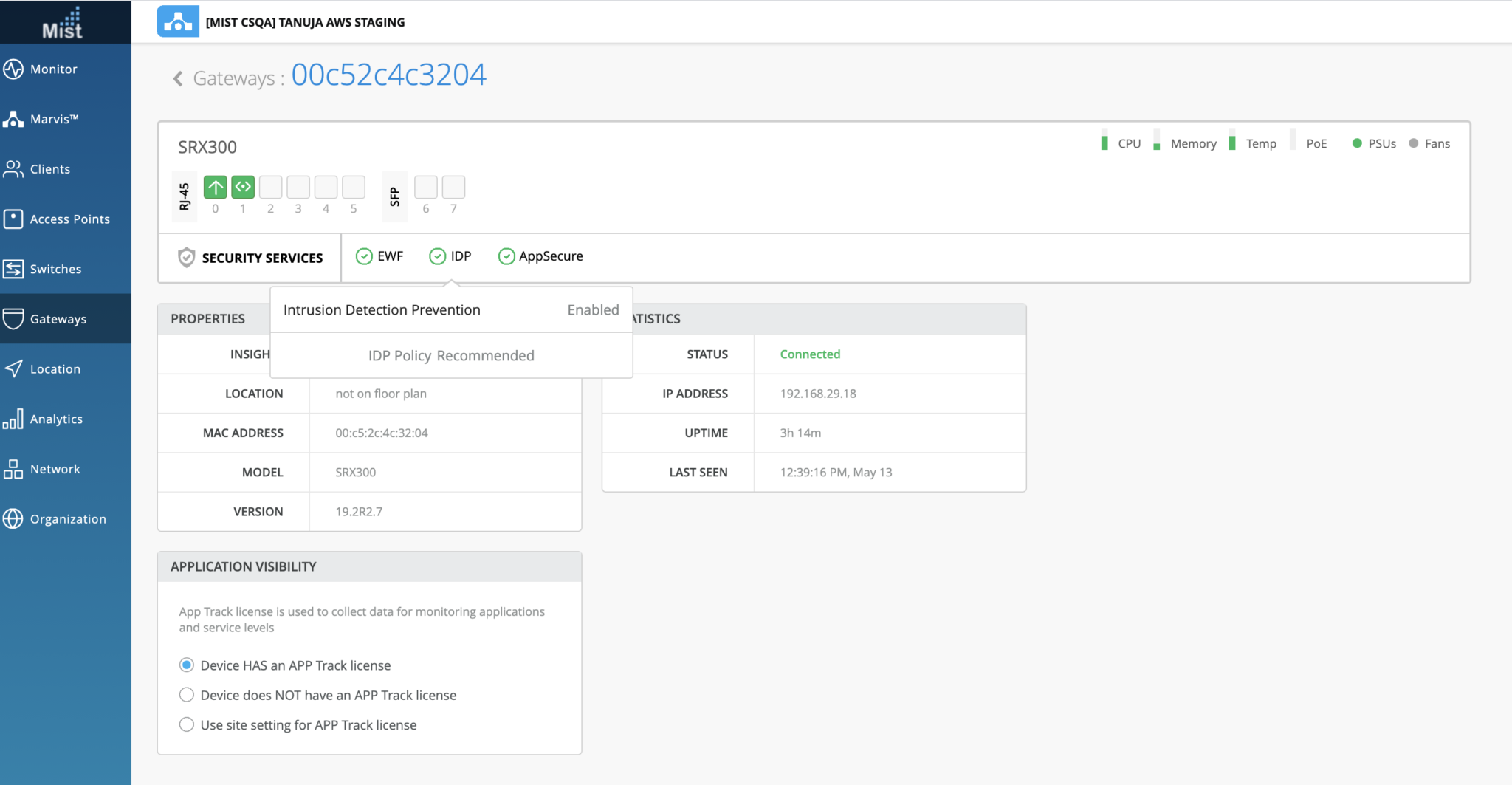 servicios de seguridad
servicios de seguridad
Puede obtener detalles como la presencia o ausencia de una licencia válida y el estado de los servicios de seguridad.
"service_status": {
"idp_status": "disabled", // either "enabled" or "disabled"
"idp_policy": "", // if the above is disabled this will be empty
"appid_status": "disabled", // either "enabled" or "disabled"
"ewf_status": "disabled", // either "enabled" (websense up), "disabled" (no config) or "down" (websense down)
"appid_version": 0 // this will be 0 if appid_status is disabled, as we then don't check the version number
},
