例:IPsec VPN 用のシングル MX シリーズ(ECMP ベースの一貫性のあるハッシュ)とスケールアウトされた SRX シリーズ ファイアウォール(スタンドアロン)
概要 この構成では、IPsec VPNサービス用に、スケールアウトされたSRXシリーズファイアウォールを備えた単一のMXシリーズをスタンドアロンでセットアップする方法を学習します。
概要
表 1 に、この例で使用されている展開コンポーネントを示します。
| CSDSコンポーネント | の詳細 |
|---|---|
| 転送レイヤー | MX304とJunos OSリリース23.4R1以降 |
| サービスレイヤー | vSRX 3.0 と Junos OS リリース 23.4R1 以降 |
| 冗長性 | ロードバランサー向けのECMPベースの一貫性のあるハッシュを備えた単一のMXシリーズ。 SRXシリーズファイアウォール(スタンドアロン) |
| 機能 | IPsec VPN |
| 追加コンポーネント | IPsecイニシエーターデバイス - SPC3カードを搭載したMXルーター。任意のIPsecイニシエータ デバイスを使用できます。 |
トラフィックフローとVPNの詳細については、 表2 と 表3 を参照してください。
| 機能トラフィック | フローコンポーネントの | IPアドレス |
|---|---|---|
| SRX1、SRX2、SRX3 上の IPsec VPN | IKE ゲートウェイ ソース(IPsec イニシエーター) | 200.0.0.0/8 |
| IKE ゲートウェイ宛先(IPsec レスポンダー) | 100.0.0.1/32 | |
| IPsec データ ソース | 6.0.0.0/8 | |
| IPsec データ送信先 | 75.0.0.0/8 |
| デバイス | IKEゲートウェイIPsec | データエンドポイント |
|---|---|---|
| SRX1 | 200.0.0.1 および 100.0.0.1 | 6.0.0.3と75.0.0.3の間のトンネル1 |
| SRX2 | 200.0.0.2 および 100.0.0.1 | 6.0.0.2と75.0.0.2の間のトンネル2 |
| SRX3 | 200.0.0.6 および 100.0.0.1 | 6.0.0.1と75.0.0.1の間のトンネル3 |
トラフィックフローについては 表4 を参照してください。
| フロー タイプ | トラフィック フロー コンポーネントの | IP アドレス |
|---|---|---|
| SRXへのIKEイニシエータ | ソースロードバランサー(MXのルートフィルター) | 100.0.0.1/32 |
| IPsec VPN フォワード フロー | ルーティングベース | |
| IPsec VPNリバースフロー | ルーティングベース | SRXごとの一意のARIルート |
トポロジーの図
図1:シングルMXシリーズ(ECMPベースのコンシステントハッシュ)とIPsec VPNサービス用のスケールアウトSRXシリーズファイアウォール
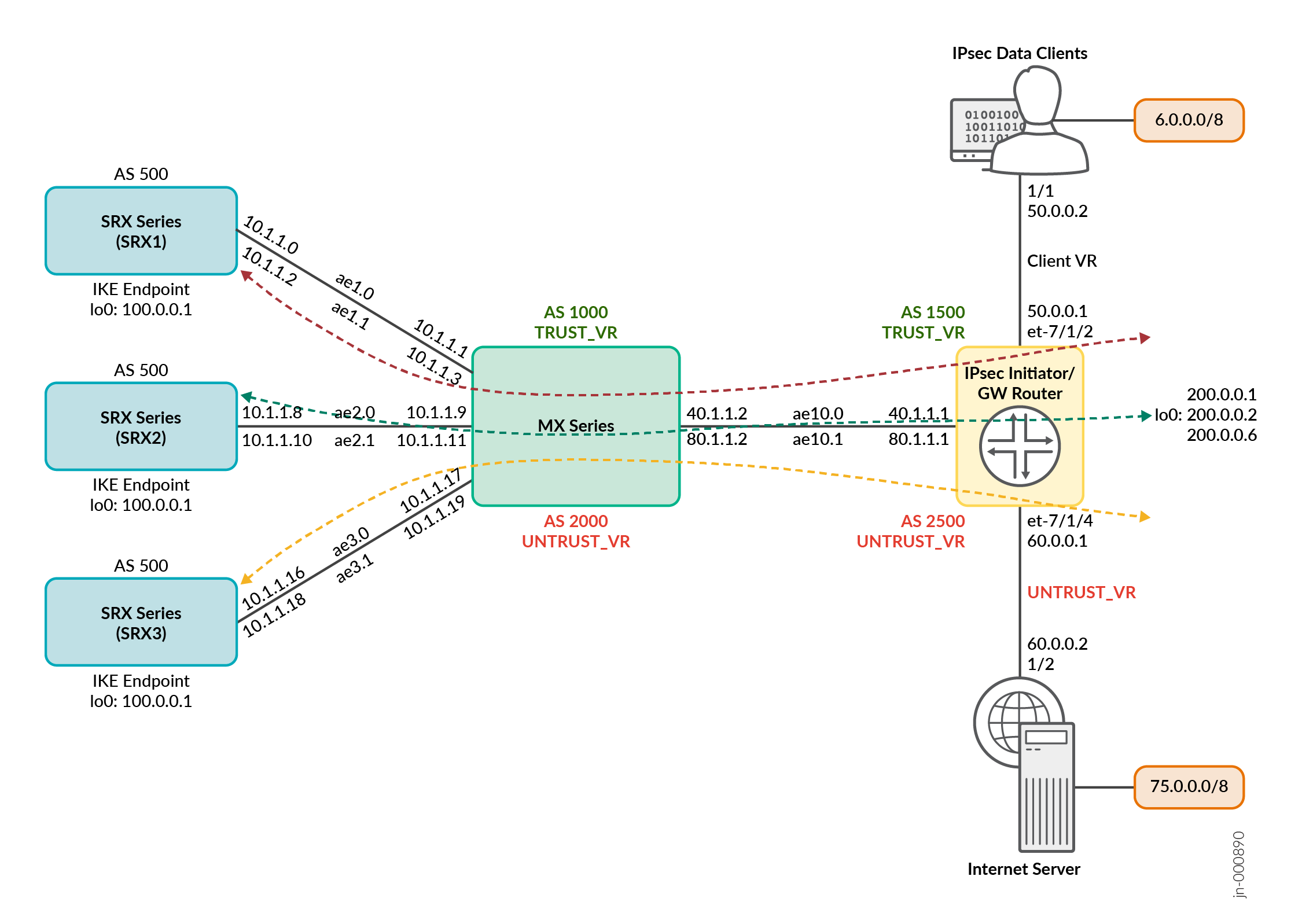

図 2: IPsec VPN サービス
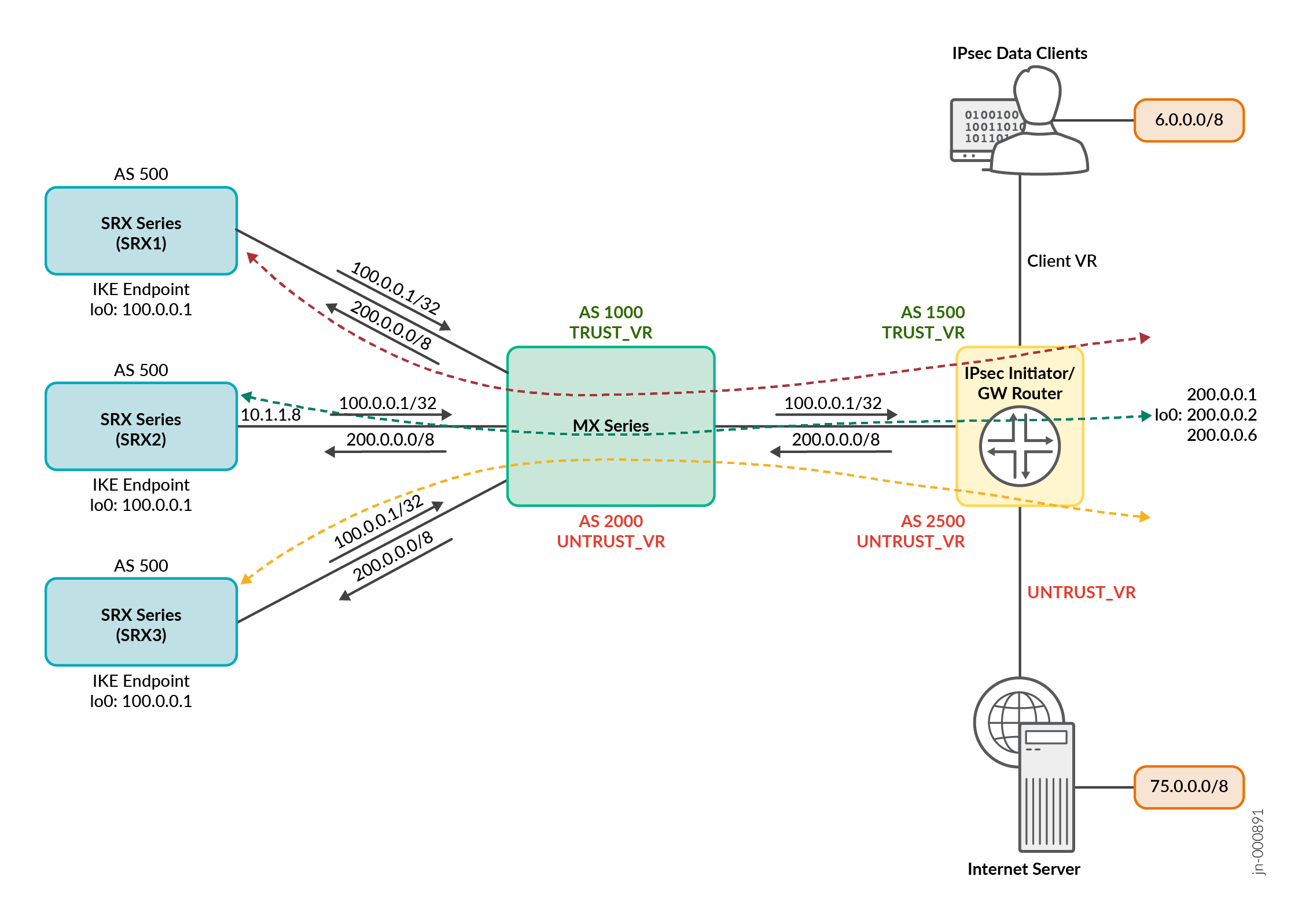 用の IKE ゲートウェイのルート広告
用の IKE ゲートウェイのルート広告
 用の IKE ゲートウェイのルート広告
用の IKE ゲートウェイのルート広告
図 3: IPsec VPN サービスの
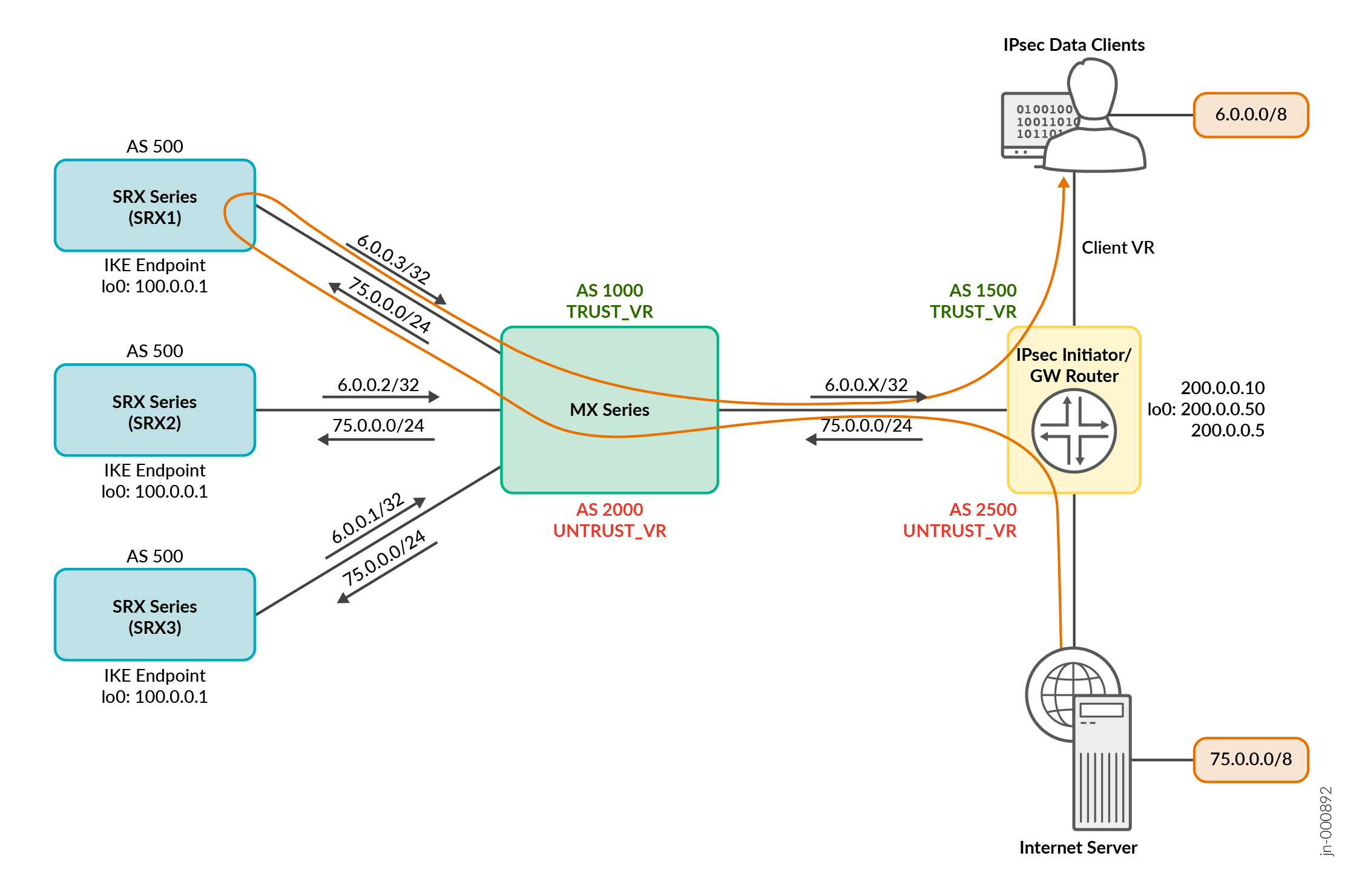 IPsec エンドポイントのルート広告
IPsec エンドポイントのルート広告
 IPsec エンドポイントのルート広告
IPsec エンドポイントのルート広告
構成
この例を素早く設定するには、以下のコマンドをコピーしてテキスト・ファイルに貼り付け、改行を削除し、ネットワーク・コンフィギュレーションに合わせて必要な詳細を変更し、[edit]階層レベルのCLIにコマンドをコピー&ペーストし、コンフィギュレーション・モードからコミットを入力してください。
これらの構成はラボ環境からキャプチャされたものであり、参照用にのみ提供されています。実際の構成は、環境の特定の要件によって異なる場合があります。
次の項目は、この例の構成コンポーネントの一覧を示しています。
- MXシリーズを設定する
- IPsecイニシエーターを設定する
- SRX1の設定
- SRX2の設定
- SRX3の設定
MXシリーズを設定する
[edit] set interfaces et-0/0/0 gigether-options 802.3ad ae1 set interfaces et-0/0/1 gigether-options 802.3ad ae2 set interfaces et-0/0/2 gigether-options 802.3ad ae3 set interfaces et-0/0/7 gigether-options 802.3ad ae1 set interfaces et-0/0/8 gigether-options 802.3ad ae2 set interfaces et-0/0/9 gigether-options 802.3ad ae3 set interfaces et-0/0/10 gigether-options 802.3ad ae10 set interfaces et-0/0/11 gigether-options 802.3ad ae10 set interfaces et-0/1/0 gigether-options 802.3ad ae10 set interfaces et-0/1/1 gigether-options 802.3ad ae10 set interfaces et-0/1/2 gigether-options 802.3ad ae10 set interfaces ae1 vlan-tagging set interfaces ae1 aggregated-ether-options minimum-links 1 set interfaces ae1 aggregated-ether-options lacp active set interfaces ae1 aggregated-ether-options lacp periodic fast set interfaces ae1 unit 0 vlan-id 1 set interfaces ae1 unit 0 family inet address 10.1.1.1/31 set interfaces ae1 unit 0 family inet6 address 10:1:1::1/127 set interfaces ae1 unit 1 vlan-id 2 set interfaces ae1 unit 1 family inet address 10.1.1.3/31 set interfaces ae1 unit 1 family inet6 address 10:1:1::3/127 set interfaces ae2 vlan-tagging set interfaces ae2 aggregated-ether-options minimum-links 1 set interfaces ae2 aggregated-ether-options lacp active set interfaces ae2 aggregated-ether-options lacp periodic fast set interfaces ae2 unit 0 vlan-id 9 set interfaces ae2 unit 0 family inet address 10.1.1.9/31 set interfaces ae2 unit 0 family inet6 address 10:2:2::1/127 set interfaces ae2 unit 1 vlan-id 10 set interfaces ae2 unit 1 family inet address 10.1.1.11/31 set interfaces ae2 unit 1 family inet6 address 10:2:2::3/127 set interfaces ae3 vlan-tagging set interfaces ae3 aggregated-ether-options minimum-links 1 set interfaces ae3 aggregated-ether-options lacp active set interfaces ae3 aggregated-ether-options lacp periodic fast set interfaces ae3 unit 0 vlan-id 9 set interfaces ae3 unit 0 family inet address 10.1.1.17/31 set interfaces ae3 unit 0 family inet6 address 10:3:3::1/127 set interfaces ae3 unit 1 vlan-id 10 set interfaces ae3 unit 1 family inet address 10.1.1.19/31 set interfaces ae3 unit 1 family inet6 address 10:3:3::3/127 set interfaces ae10 flexible-vlan-tagging set interfaces ae10 encapsulation flexible-ethernet-services set interfaces ae10 aggregated-ether-options minimum-links 1 set interfaces ae10 aggregated-ether-options lacp active set interfaces ae10 aggregated-ether-options lacp periodic fast set interfaces ae10 unit 40 vlan-id 40 set interfaces ae10 unit 40 family inet address 40.1.1.2/30 set interfaces ae10 unit 40 family inet6 address 40:1:1::2/124 set interfaces ae10 unit 80 vlan-id 80 set interfaces ae10 unit 80 family inet address 80.1.1.2/30 set interfaces ae10 unit 80 family inet6 address 80:1:1::2/124 set routing-instances TRUST_VR instance-type virtual-router set routing-instances TRUST_VR routing-options autonomous-system 1000 set routing-instances TRUST_VR routing-options autonomous-system independent-domain no-attrset set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router type external set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router export srx_ike_endpoint_export set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router peer-as 1500 set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router local-as 1000 set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router bfd-liveness-detection minimum-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router bfd-liveness-detection minimum-receive-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router bfd-liveness-detection multiplier 3 set routing-instances TRUST_VR protocols bgp group MX-to-TRUST_GW_Router neighbor 40.1.1.1 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 type external set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 import pfe_consistent_hash set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 export trust-to-untrust-export set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 peer-as 500 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 local-as 1000 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 multipath set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 bfd-liveness-detection minimum-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 bfd-liveness-detection minimum-receive-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 bfd-liveness-detection multiplier 3 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx1 neighbor 10.1.1.0 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 type external set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 import pfe_consistent_hash set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 export trust-to-untrust-export set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 peer-as 500 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 local-as 1000 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 multipath set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 bfd-liveness-detection minimum-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 bfd-liveness-detection minimum-receive-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 bfd-liveness-detection multiplier 3 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx2 neighbor 10.1.1.8 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 type external set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 import pfe_consistent_hash set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 export trust-to-untrust-export set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 peer-as 500 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 local-as 1000 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 multipath set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 bfd-liveness-detection minimum-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 bfd-liveness-detection minimum-receive-interval 300 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 bfd-liveness-detection multiplier 3 set routing-instances TRUST_VR protocols bgp group MX-to-vsrx3 neighbor 10.1.1.16 set routing-instances TRUST_VR interface ae1.0 set routing-instances TRUST_VR interface ae2.0 set routing-instances TRUST_VR interface ae3.0 set routing-instances TRUST_VR interface ae10.40 set policy-options policy-statement srx_ike_endpoint_export term 1 from protocol bgp set policy-options policy-statement srx_ike_endpoint_export term 1 from route-filter 100.0.0.1/32 exact set policy-options policy-statement srx_ike_endpoint_export term 1 then next-hop self set policy-options policy-statement srx_ike_endpoint_export term 1 then accept set policy-options policy-statement srx_ike_endpoint_export term 2 then reject set policy-options policy-statement trust-to-untrust-export term 1 from protocol bgp set policy-options policy-statement trust-to-untrust-export term 1 from protocol static set policy-options policy-statement trust-to-untrust-export term 1 then next-hop self set policy-options policy-statement trust-to-untrust-export term 1 then accept set policy-options policy-statement trust-to-untrust-export term 2 then reject set routing-instances UNTRUST_VR instance-type virtual-router set routing-instances UNTRUST_VR routing-options autonomous-system 2000 set routing-instances UNTRUST_VR routing-options autonomous-system independent-domain no-attrset set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router type external set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router export srx_ari_route_export set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router peer-as 2500 set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router local-as 2000 set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router bfd-liveness-detection minimum-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router bfd-liveness-detection minimum-receive-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router bfd-liveness-detection multiplier 3 set routing-instances UNTRUST_VR protocols bgp group MX-to-UNTRUST_GW_Router neighbor 80.1.1.1 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 type external set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 export untrust-to-trust-export set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 peer-as 500 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 local-as 2000 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 multipath set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 bfd-liveness-detection minimum-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 bfd-liveness-detection minimum-receive-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 bfd-liveness-detection multiplier 3 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx1 neighbor 10.1.1.2 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 type external set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 export untrust-to-trust-export set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 peer-as 500 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 local-as 2000 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 multipath set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 bfd-liveness-detection minimum-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 bfd-liveness-detection minimum-receive-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 bfd-liveness-detection multiplier 3 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx2 neighbor 10.1.1.10 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 type external set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 export untrust-to-trust-export set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 peer-as 500 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 local-as 2000 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 multipath set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 bfd-liveness-detection minimum-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 bfd-liveness-detection minimum-receive-interval 300 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 bfd-liveness-detection multiplier 3 set routing-instances UNTRUST_VR protocols bgp group MX-to-vsrx3 neighbor 10.1.1.18 set routing-instances UNTRUST_VR interface ae1.1 set routing-instances UNTRUST_VR interface ae2.1 set routing-instances UNTRUST_VR interface ae3.1 set routing-instances UNTRUST_VR interface ae10.80 set policy-options policy-statement srx_ari_route_export term 1 from protocol bgp set policy-options policy-statement srx_ari_route_export term 1 from route-filter 6.0.0.0/8 orlonger set policy-options policy-statement srx_ari_route_export term 1 then next-hop self set policy-options policy-statement srx_ari_route_export term 1 then accept set policy-options policy-statement srx_ari_route_export term 2 then reject set policy-options policy-statement untrust-to-trust-export term 1 from protocol bgp set policy-options policy-statement untrust-to-trust-export term 1 from protocol static set policy-options policy-statement untrust-to-trust-export term 1 then next-hop self set policy-options policy-statement untrust-to-trust-export term 1 then accept set policy-options policy-statement untrust-to-trust-export term 2 then reject set policy-options policy-statement pfe_consistent_hash from route-filter 100.0.0.1/32 exact set policy-options policy-statement pfe_consistent_hash then load-balance consistent-hash set policy-options policy-statement pfe_consistent_hash then accept set policy-options policy-statement pfe_lb_hash term source_hash from route-filter 100.0.0.1/32 exact set policy-options policy-statement pfe_lb_hash term source_hash then load-balance source-ip-only set policy-options policy-statement pfe_lb_hash term source_hash then accept set policy-options policy-statement pfe_lb_hash term ALL-ELSE then load-balance per-packet set policy-options policy-statement pfe_lb_hash term ALL-ELSE then accept set routing-options forwarding-table export pfe_lb_hash
IPsecイニシエータの設定
[edit] set services service-set IPSEC_TUN_1 next-hop-service inside-service-interface vms-3/0/0.1 set services service-set IPSEC_TUN_1 next-hop-service outside-service-interface vms-3/0/0.2001 set services service-set IPSEC_TUN_1 ipsec-vpn TUN_1 set services service-set IPSEC_TUN_2 next-hop-service inside-service-interface vms-3/0/0.2 set services service-set IPSEC_TUN_2 next-hop-service outside-service-interface vms-3/0/0.2002 set services service-set IPSEC_TUN_2 ipsec-vpn TUN_2 set services service-set IPSEC_TUN_3 next-hop-service inside-service-interface vms-3/0/0.3 set services service-set IPSEC_TUN_3 next-hop-service outside-service-interface vms-3/0/0.2003 set services service-set IPSEC_TUN_3 ipsec-vpn TUN_3 set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group2 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POLICY proposals IKE_PROP set security ike policy IKE_POLICY pre-shared-key ascii-text "$ABC123" set security ike gateway IKE_GW_1 ike-policy IKE_POLICY set security ike gateway IKE_GW_1 address 100.0.0.1 set security ike gateway IKE_GW_1 dead-peer-detection probe-idle-tunnel set security ike gateway IKE_GW_1 dead-peer-detection interval 10 set security ike gateway IKE_GW_1 dead-peer-detection threshold 3 set security ike gateway IKE_GW_1 local-identity hostname peer1.juniper.net set security ike gateway IKE_GW_1 remote-identity hostname vsrx.juniper.net set security ike gateway IKE_GW_1 external-interface lo0.0 set security ike gateway IKE_GW_1 local-address 200.0.0.1 set security ike gateway IKE_GW_1 version v2-only set security ike gateway IKE_GW_2 ike-policy IKE_POLICY set security ike gateway IKE_GW_2 address 100.0.0.1 set security ike gateway IKE_GW_2 dead-peer-detection probe-idle-tunnel set security ike gateway IKE_GW_2 dead-peer-detection interval 10 set security ike gateway IKE_GW_2 dead-peer-detection threshold 3 set security ike gateway IKE_GW_2 local-identity hostname peer2.juniper.net set security ike gateway IKE_GW_2 remote-identity hostname vsrx.juniper.net set security ike gateway IKE_GW_2 external-interface lo0.0 set security ike gateway IKE_GW_2 local-address 200.0.0.2 set security ike gateway IKE_GW_2 version v2-only set security ike gateway IKE_GW_3 ike-policy IKE_POLICY set security ike gateway IKE_GW_3 address 100.0.0.1 set security ike gateway IKE_GW_3 dead-peer-detection probe-idle-tunnel set security ike gateway IKE_GW_3 dead-peer-detection interval 10 set security ike gateway IKE_GW_3 dead-peer-detection threshold 3 set security ike gateway IKE_GW_3 local-identity hostname peer3.juniper.net set security ike gateway IKE_GW_3 remote-identity hostname vsrx.juniper.net set security ike gateway IKE_GW_3 external-interface lo0.0 set security ike gateway IKE_GW_3 local-address 200.0.0.6 set security ike gateway IKE_GW_3 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3600 set security ipsec policy IPSEC_POLICY proposals IPSEC_PROP set security ipsec vpn TUN_1 bind-interface st0.1 set security ipsec vpn TUN_1 ike gateway IKE_GW_1 set security ipsec vpn TUN_1 ike ipsec-policy IPSEC_POLICY set security ipsec vpn TUN_1 traffic-selector ts1 local-ip 6.0.0.1/32 set security ipsec vpn TUN_1 traffic-selector ts1 remote-ip 75.0.0.1/32 set security ipsec vpn TUN_1 establish-tunnels immediately set security ipsec vpn TUN_2 bind-interface st0.2 set security ipsec vpn TUN_2 ike gateway IKE_GW_2 set security ipsec vpn TUN_2 ike ipsec-policy IPSEC_POLICY set security ipsec vpn TUN_2 traffic-selector ts1 local-ip 6.0.0.2/32 set security ipsec vpn TUN_2 traffic-selector ts1 remote-ip 75.0.0.2/32 set security ipsec vpn TUN_2 establish-tunnels immediately set security ipsec vpn TUN_3 bind-interface st0.3 set security ipsec vpn TUN_3 ike gateway IKE_GW_3 set security ipsec vpn TUN_3 ike ipsec-policy IPSEC_POLICY set security ipsec vpn TUN_3 traffic-selector ts1 local-ip 6.0.0.3/32 set security ipsec vpn TUN_3 traffic-selector ts1 remote-ip 75.0.0.3/32 set security ipsec vpn TUN_3 establish-tunnels immediately set security ipsec anti-replay-window-size 512 set security flow power-mode-ipsec set interfaces vms-3/0/0 unit 1 family inet set interfaces vms-3/0/0 unit 1 service-domain inside set interfaces vms-3/0/0 unit 2 family inet set interfaces vms-3/0/0 unit 2 service-domain inside set interfaces vms-3/0/0 unit 3 family inet set interfaces vms-3/0/0 unit 3 service-domain inside set interfaces vms-3/0/0 unit 2001 family inet set interfaces vms-3/0/0 unit 2001 service-domain outside set interfaces vms-3/0/0 unit 2002 family inet set interfaces vms-3/0/0 unit 2002 service-domain outside set interfaces vms-3/0/0 unit 2003 family inet set interfaces vms-3/0/0 unit 2003 service-domain outside set interfaces lo0 unit 0 family inet address 200.0.0.1/32 set interfaces lo0 unit 0 family inet address 200.0.0.2/32 set interfaces lo0 unit 0 family inet address 200.0.0.6/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 2 family inet set interfaces st0 unit 3 family inet set interfaces et-7/0/0 gigether-options 802.3ad ae10 set interfaces et-7/1/3 gigether-options 802.3ad ae10 set interfaces et-7/0/3 gigether-options 802.3ad ae10 set interfaces et-7/0/4 gigether-options 802.3ad ae10 set interfaces et-7/0/1 gigether-options 802.3ad ae11 set interfaces et-7/0/2 gigether-options 802.3ad ae11 set interfaces et-7/1/0 gigether-options 802.3ad ae11 set interfaces et-7/1/1 gigether-options 802.3ad ae11 set interfaces et-7/1/2 mtu 9192 set interfaces et-7/1/2 unit 0 family inet address 50.0.0.1/30 set interfaces et-7/1/4 mtu 9192 set interfaces et-7/1/4 unit 0 family inet address 60.0.0.1/30 set interfaces ae10 flexible-vlan-tagging set interfaces ae10 encapsulation flexible-ethernet-services set interfaces ae10 aggregated-ether-options minimum-links 1 set interfaces ae10 aggregated-ether-options lacp active set interfaces ae10 aggregated-ether-options lacp periodic fast set interfaces ae10 unit 40 vlan-id 40 set interfaces ae10 unit 40 family inet address 40.1.1.1/30 set interfaces ae10 unit 40 family inet6 address 40:1:1::1/124 set interfaces ae10 unit 80 vlan-id 80 set interfaces ae10 unit 80 family inet address 80.1.1.1/30 set interfaces ae10 unit 80 family inet6 address 80:1:1::1/124 set interfaces ae11 flexible-vlan-tagging set interfaces ae11 encapsulation flexible-ethernet-services set interfaces ae11 aggregated-ether-options minimum-links 1 set interfaces ae11 aggregated-ether-options lacp active set interfaces ae11 aggregated-ether-options lacp periodic fast set interfaces ae11 unit 41 vlan-id 41 set interfaces ae11 unit 41 family inet address 41.1.1.1/30 set interfaces ae11 unit 41 family inet6 address 41:1:1::1/124 set interfaces ae11 unit 81 vlan-id 81 set interfaces ae11 unit 81 family inet address 81.1.1.1/30 set interfaces ae11 unit 81 family inet6 address 81:1:1::1/124 set routing-instances TRUST_VR instance-type virtual-router set routing-instances TRUST_VR routing-options autonomous-system 1500 set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust type external set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust export client_to_server_export set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust peer-as 1000 set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust local-as 1500 set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust bfd-liveness-detection minimum-interval 300 set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust bfd-liveness-detection minimum-receive-interval 300 set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust bfd-liveness-detection multiplier 3 set routing-instances TRUST_VR protocols bgp group trust_GW-to-MX1_trust neighbor 40.1.1.2 set routing-instances TRUST_VR protocols bgp multipath set routing-instances TRUST_VR interface vms-3/0/0.2001 set routing-instances TRUST_VR interface vms-3/0/0.2002 set routing-instances TRUST_VR interface vms-3/0/0.2003 set routing-instances TRUST_VR interface ae10.40 set routing-instances TRUST_VR interface lo0.0 set policy-options policy-statement client_to_server_export term 1 from protocol direct set policy-options policy-statement client_to_server_export term 1 from route-filter 200.0.0.0/8 orlonger set policy-options policy-statement client_to_server_export term 1 then accept set policy-options policy-statement client_to_server_export term 2 then reject set policy-options policy-statement client_to_server_export_mx2 term 1 from protocol static set policy-options policy-statement client_to_server_export_mx2 term 1 from route-filter 141.0.0.0/8 orlonger set policy-options policy-statement client_to_server_export_mx2 term 1 from route-filter 140.0.0.0/8 orlonger set policy-options policy-statement client_to_server_export_mx2 term 1 then accept set policy-options policy-statement client_to_server_export_mx2 term 2 then reject set routing-instances UNTRUST_VR instance-type virtual-router set routing-instances UNTRUST_VR routing-options autonomous-system 2500 set routing-instances UNTRUST_VR routing-options static route 75.0.0.0/8 next-hop 60.0.0.2 set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust type external set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust export server_to_client_export set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust peer-as 2000 set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust local-as 2500 set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust bfd-liveness-detection minimum-interval 300 set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust bfd-liveness-detection minimum-receive-interval 300 set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust bfd-liveness-detection multiplier 3 set routing-instances UNTRUST_VR protocols bgp group Untrust_GW-to-MX1_Untrust neighbor 80.1.1.2 set routing-instances UNTRUST_VR protocols bgp multipath set routing-instances UNTRUST_VR interface et-7/1/4.0 set routing-instances UNTRUST_VR interface ae10.80 set policy-options policy-statement server_to_client_export term t1 from protocol static set policy-options policy-statement server_to_client_export term t1 from route-filter 75.0.0.0/8 exact set policy-options policy-statement server_to_client_export term t1 then accept set policy-options policy-statement server_to_client_export term t2 then reject set policy-options policy-statement server_to_client_export_mx2 term t1 from protocol static set policy-options policy-statement server_to_client_export_mx2 term t1 from route-filter 0.0.0.0/0 exact set policy-options policy-statement server_to_client_export_mx2 term t1 then accept set policy-options policy-statement server_to_client_export_mx2 term t2 then reject set routing-instances client instance-type virtual-router set routing-instances client routing-options static route 6.0.0.0/8 next-hop 50.0.0.2 set routing-instances client interface vms-3/0/0.1 set routing-instances client interface vms-3/0/0.2 set routing-instances client interface vms-3/0/0.3 set routing-instances client interface et-7/1/2.0 set routing-instances client interface st0.1 set routing-instances client interface st0.2 set routing-instances client interface st0.3 set policy-options policy-statement ECMP_POLICY-LB then load-balance per-packet set routing-options forwarding-table export ECMP_POLICY-LB
SRX1の設定
[edit] set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group2 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POLICY proposals IKE_PROP set security ike policy IKE_POLICY pre-shared-key ascii-text "$ABC123" set security ike gateway avpn_ike_gw ike-policy IKE_POLICY set security ike gateway avpn_ike_gw dynamic hostname .juniper.net set security ike gateway avpn_ike_gw dynamic ike-user-type group-ike-id set security ike gateway avpn_ike_gw dead-peer-detection probe-idle-tunnel set security ike gateway avpn_ike_gw dead-peer-detection interval 10 set security ike gateway avpn_ike_gw dead-peer-detection threshold 3 set security ike gateway avpn_ike_gw local-identity hostname vsrx.juniper.net set security ike gateway avpn_ike_gw external-interface lo0.0 set security ike gateway avpn_ike_gw local-address 100.0.0.1 set security ike gateway avpn_ike_gw version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3600 set security ipsec policy IPSEC_POLICY proposals IPSEC_PROP set security ipsec vpn avpn_ipsec_vpn bind-interface st0.1 set security ipsec vpn avpn_ipsec_vpn ike gateway avpn_ike_gw set security ipsec vpn avpn_ipsec_vpn ike ipsec-policy IPSEC_POLICY set security ipsec vpn avpn_ipsec_vpn traffic-selector ts local-ip 0.0.0.0/0 set security ipsec vpn avpn_ipsec_vpn traffic-selector ts remote-ip 0.0.0.0/0 set security ipsec anti-replay-window-size 512 set interfaces lo0 unit 0 family inet address 100.0.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 2 family inet set interfaces st0 unit 3 family inet set security zones security-zone vr-1_trust_zone host-inbound-traffic system-services all set security zones security-zone vr-1_trust_zone host-inbound-traffic protocols all set security zones security-zone vr-1_trust_zone interfaces ae1.0 set security zones security-zone vr-1_trust_zone interfaces lo0.0 set security zones security-zone vr-1_trust_zone interfaces st0.1 set security zones security-zone vr-1_trust_zone interfaces st0.2 set security zones security-zone vr-1_trust_zone interfaces st0.3 set security zones security-zone vr-1_untrust_zone host-inbound-traffic system-services all set security zones security-zone vr-1_untrust_zone host-inbound-traffic protocols all set security zones security-zone vr-1_untrust_zone interfaces ae1.1 set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match source-address ipsec_data_source_prefix_6.0.0.0/8 set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match destination-address any set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match application any set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY then permit set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match source-address ike_source_prefix_200.0.0.0/8 set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match destination-address any set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match application any set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY then permit set security policies default-policy permit-all set security address-book global address ipsec_data_source_prefix_6.0.0.0/8 6.0.0.0/8 set security address-book global address ike_source_prefix_200.0.0.0/8 200.0.0.0/8 set interfaces et-1/0/0 gigether-options 802.3ad ae1 set interfaces et-1/0/1 gigether-options 802.3ad ae1 set interfaces ae1 vlan-tagging set interfaces ae1 aggregated-ether-options minimum-links 1 set interfaces ae1 aggregated-ether-options lacp active set interfaces ae1 aggregated-ether-options lacp periodic fast set interfaces ae1 unit 0 vlan-id 1 set interfaces ae1 unit 0 family inet address 10.1.1.0/31 set interfaces ae1 unit 0 family inet6 address 10:1:1::0/127 set interfaces ae1 unit 1 vlan-id 2 set interfaces ae1 unit 1 family inet address 10.1.1.2/31 set interfaces ae1 unit 1 family inet6 address 10:1:1::2/127 set protocols bgp group Vsrx-to-MX_TRUST type external set protocols bgp group Vsrx-to-MX_TRUST export ike_endpoint_export_policy set protocols bgp group Vsrx-to-MX_TRUST local-as 500 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection minimum-interval 300 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection minimum-receive-interval 300 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection multiplier 3 set protocols bgp group Vsrx-to-MX_TRUST neighbor 10.1.1.1 peer-as 1000 set protocols bgp group Vsrx-to-MX_UNTRUST type external set protocols bgp group Vsrx-to-MX_UNTRUST export ari_export_untrust set protocols bgp group Vsrx-to-MX_UNTRUST local-as 500 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection minimum-interval 300 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection minimum-receive-interval 300 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection multiplier 3 set protocols bgp group Vsrx-to-MX_UNTRUST neighbor 10.1.1.3 peer-as 2000 set policy-options policy-statement ari_export_untrust term 1 from protocol ari-ts set policy-options policy-statement ari_export_untrust term 1 then accept set policy-options policy-statement ari_export_untrust term defualt then reject set policy-options policy-statement ike_endpoint_export_policy term 1 from protocol direct set policy-options policy-statement ike_endpoint_export_policy term 1 from route-filter 100.0.0.1/32 exact set policy-options policy-statement ike_endpoint_export_policy term 1 then next-hop self set policy-options policy-statement ike_endpoint_export_policy term 1 then accept set policy-options policy-statement ike_endpoint_export_policy term 2 then reject set policy-options policy-statement ecmp_policy_lab then load-balance per-packet set routing-options forwarding-table export ecmp_policy_lab
SRX2の設定
[edit] set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group2 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POLICY proposals IKE_PROP set security ike policy IKE_POLICY pre-shared-key ascii-text "$ABC123" set security ike gateway avpn_ike_gw ike-policy IKE_POLICY set security ike gateway avpn_ike_gw dynamic hostname .juniper.net set security ike gateway avpn_ike_gw dynamic ike-user-type group-ike-id set security ike gateway avpn_ike_gw dead-peer-detection probe-idle-tunnel set security ike gateway avpn_ike_gw dead-peer-detection interval 10 set security ike gateway avpn_ike_gw dead-peer-detection threshold 3 set security ike gateway avpn_ike_gw local-identity hostname vsrx.juniper.net set security ike gateway avpn_ike_gw external-interface lo0.0 set security ike gateway avpn_ike_gw local-address 100.0.0.1 set security ike gateway avpn_ike_gw version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3600 set security ipsec policy IPSEC_POLICY proposals IPSEC_PROP set security ipsec vpn avpn_ipsec_vpn bind-interface st0.1 set security ipsec vpn avpn_ipsec_vpn ike gateway avpn_ike_gw set security ipsec vpn avpn_ipsec_vpn ike ipsec-policy IPSEC_POLICY set security ipsec vpn avpn_ipsec_vpn traffic-selector ts local-ip 0.0.0.0/0 set security ipsec vpn avpn_ipsec_vpn traffic-selector ts remote-ip 0.0.0.0/0 set security ipsec anti-replay-window-size 512 set interfaces lo0 unit 0 family inet address 100.0.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 2 family inet set interfaces st0 unit 3 family inet set security zones security-zone vr-1_trust_zone host-inbound-traffic system-services all set security zones security-zone vr-1_trust_zone host-inbound-traffic protocols all set security zones security-zone vr-1_trust_zone interfaces ae1.0 set security zones security-zone vr-1_trust_zone interfaces lo0.0 set security zones security-zone vr-1_trust_zone interfaces st0.1 set security zones security-zone vr-1_trust_zone interfaces st0.2 set security zones security-zone vr-1_trust_zone interfaces st0.3 set security zones security-zone vr-1_untrust_zone host-inbound-traffic system-services all set security zones security-zone vr-1_untrust_zone host-inbound-traffic protocols all set security zones security-zone vr-1_untrust_zone interfaces ae1.1 set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match source-address ipsec_data_source_prefix_6.0.0.0/8 set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match destination-address any set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match application any set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY then permit set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match source-address ike_source_prefix_200.0.0.0/8 set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match destination-address any set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match application any set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY then permit set security policies default-policy permit-all set security address-book global address ipsec_data_source_prefix_6.0.0.0/8 6.0.0.0/8 set security address-book global address ike_source_prefix_200.0.0.0/8 200.0.0.0/8 set interfaces et-1/0/0 gigether-options 802.3ad ae1 set interfaces et-1/0/1 gigether-options 802.3ad ae1 set interfaces ae1 vlan-tagging set interfaces ae1 aggregated-ether-options minimum-links 1 set interfaces ae1 aggregated-ether-options lacp active set interfaces ae1 aggregated-ether-options lacp periodic fast set interfaces ae1 unit 0 vlan-id 9 set interfaces ae1 unit 0 family inet address 10.1.1.8/31 set interfaces ae1 unit 0 family inet6 address 10:2:2::0/127 set interfaces ae1 unit 1 vlan-id 10 set interfaces ae1 unit 1 family inet address 10.1.1.10/31 set interfaces ae1 unit 1 family inet6 address 10:2:2::2/127 set protocols bgp group Vsrx-to-MX_TRUST type external set protocols bgp group Vsrx-to-MX_TRUST export ike_endpoint_export_policy set protocols bgp group Vsrx-to-MX_TRUST local-as 500 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection minimum-interval 300 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection minimum-receive-interval 300 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection multiplier 3 set protocols bgp group Vsrx-to-MX_TRUST neighbor 10.1.1.9 peer-as 1000 set protocols bgp group Vsrx-to-MX_UNTRUST type external set protocols bgp group Vsrx-to-MX_UNTRUST export ari_export_untrust set protocols bgp group Vsrx-to-MX_UNTRUST local-as 500 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection minimum-interval 300 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection minimum-receive-interval 300 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection multiplier 3 set protocols bgp group Vsrx-to-MX_UNTRUST neighbor 10.1.1.11 peer-as 2000 set policy-options policy-statement ari_export_untrust term 1 from protocol ari-ts set policy-options policy-statement ari_export_untrust term 1 then accept set policy-options policy-statement ari_export_untrust term defualt then reject set policy-options policy-statement ike_endpoint_export_policy term 1 from protocol direct set policy-options policy-statement ike_endpoint_export_policy term 1 from route-filter 100.0.0.1/32 exact set policy-options policy-statement ike_endpoint_export_policy term 1 then next-hop self set policy-options policy-statement ike_endpoint_export_policy term 1 then accept set policy-options policy-statement ike_endpoint_export_policy term 2 then reject set policy-options policy-statement ecmp_policy_lab then load-balance per-packet set routing-options forwarding-table export ecmp_policy_lab
SRX3の設定
[edit] set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group2 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POLICY proposals IKE_PROP set security ike policy IKE_POLICY pre-shared-key ascii-text "$ABC123" set security ike gateway avpn_ike_gw ike-policy IKE_POLICY set security ike gateway avpn_ike_gw dynamic hostname .juniper.net set security ike gateway avpn_ike_gw dynamic ike-user-type group-ike-id set security ike gateway avpn_ike_gw dead-peer-detection probe-idle-tunnel set security ike gateway avpn_ike_gw dead-peer-detection interval 10 set security ike gateway avpn_ike_gw dead-peer-detection threshold 3 set security ike gateway avpn_ike_gw local-identity hostname vsrx.juniper.net set security ike gateway avpn_ike_gw external-interface lo0.0 set security ike gateway avpn_ike_gw local-address 100.0.0.1 set security ike gateway avpn_ike_gw version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3600 set security ipsec policy IPSEC_POLICY proposals IPSEC_PROP set security ipsec vpn avpn_ipsec_vpn bind-interface st0.1 set security ipsec vpn avpn_ipsec_vpn ike gateway avpn_ike_gw set security ipsec vpn avpn_ipsec_vpn ike ipsec-policy IPSEC_POLICY set security ipsec vpn avpn_ipsec_vpn traffic-selector ts local-ip 0.0.0.0/0 set security ipsec vpn avpn_ipsec_vpn traffic-selector ts remote-ip 0.0.0.0/0 set security ipsec anti-replay-window-size 512 set interfaces lo0 unit 0 family inet address 100.0.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 2 family inet set interfaces st0 unit 3 family inet set security zones security-zone vr-1_trust_zone host-inbound-traffic system-services all set security zones security-zone vr-1_trust_zone host-inbound-traffic protocols all set security zones security-zone vr-1_trust_zone interfaces ae1.0 set security zones security-zone vr-1_trust_zone interfaces lo0.0 set security zones security-zone vr-1_trust_zone interfaces st0.1 set security zones security-zone vr-1_trust_zone interfaces st0.2 set security zones security-zone vr-1_trust_zone interfaces st0.3 set security zones security-zone vr-1_untrust_zone host-inbound-traffic system-services all set security zones security-zone vr-1_untrust_zone host-inbound-traffic protocols all set security zones security-zone vr-1_untrust_zone interfaces ae1.1 set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match source-address ipsec_data_source_prefix_6.0.0.0/8 set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match destination-address any set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY match application any set security policies from-zone vr-1_trust_zone to-zone vr-1_untrust_zone policy IPSEC_DATA_POLICY then permit set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match source-address ike_source_prefix_200.0.0.0/8 set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match destination-address any set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY match application any set security policies from-zone vr-1_trust_zone to-zone vr-1_trust_zone policy IKE_ALLOW_POLICY then permit set security policies default-policy permit-all set security address-book global address ipsec_data_source_prefix_6.0.0.0/8 6.0.0.0/8 set security address-book global address ike_source_prefix_200.0.0.0/8 200.0.0.0/8 set interfaces et-1/0/0 gigether-options 802.3ad ae1 set interfaces et-1/0/1 gigether-options 802.3ad ae1 set interfaces ae1 vlan-tagging set interfaces ae1 aggregated-ether-options minimum-links 1 set interfaces ae1 aggregated-ether-options lacp active set interfaces ae1 aggregated-ether-options lacp periodic fast set interfaces ae1 unit 0 vlan-id 9 set interfaces ae1 unit 0 family inet address 10.1.1.16/31 set interfaces ae1 unit 1 vlan-id 10 set interfaces ae1 unit 1 family inet address 10.1.1.18/31 set protocols bgp group Vsrx-to-MX_TRUST type external set protocols bgp group Vsrx-to-MX_TRUST export ike_endpoint_export_policy set protocols bgp group Vsrx-to-MX_TRUST local-as 500 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection minimum-interval 300 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection minimum-receive-interval 300 set protocols bgp group Vsrx-to-MX_TRUST bfd-liveness-detection multiplier 3 set protocols bgp group Vsrx-to-MX_TRUST neighbor 10.1.1.17 peer-as 1000 set protocols bgp group Vsrx-to-MX_UNTRUST type external set protocols bgp group Vsrx-to-MX_UNTRUST export ari_export_untrust set protocols bgp group Vsrx-to-MX_UNTRUST local-as 500 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection minimum-interval 300 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection minimum-receive-interval 300 set protocols bgp group Vsrx-to-MX_UNTRUST bfd-liveness-detection multiplier 3 set protocols bgp group Vsrx-to-MX_UNTRUST neighbor 10.1.1.19 peer-as 2000 set policy-options policy-statement ari_export_untrust term 1 from protocol ari-ts set policy-options policy-statement ari_export_untrust term 1 then accept set policy-options policy-statement ari_export_untrust term defualt then reject set policy-options policy-statement ike_endpoint_export_policy term 1 from protocol direct set policy-options policy-statement ike_endpoint_export_policy term 1 from route-filter 100.0.0.1/32 exact set policy-options policy-statement ike_endpoint_export_policy term 1 then next-hop self set policy-options policy-statement ike_endpoint_export_policy term 1 then accept set policy-options policy-statement ike_endpoint_export_policy term 2 then reject set policy-options policy-statement ecmp_policy_lab then load-balance per-packet set routing-options forwarding-table export ecmp_policy_lab
検証
以下の項目は、この例の機能を検証するために使用される show コマンドのリストを示しています。
- MXシリーズ設定の確認
- SRX1の設定を確認する
- SRX2 の設定を確認する
- SRX3 の設定を確認する
MXシリーズ設定の確認
user@MX304# run show route 100.0.0.1/32 active-path
TRUST_VR.inet.0: 12 destinations, 14 routes (12 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
100.0.0.1/32 *[BGP/170] 03:14:10, localpref 100
AS path: 500 I, validation-state: unverified
to 10.1.1.0 via ae1.0
> to 10.1.1.8 via ae2.0
to 10.1.1.16 via ae3.0
user@MX304# run show route 100.0.0.1/32 active-path extensive
TRUST_VR.inet.0: 12 destinations, 14 routes (12 active, 0 holddown, 0 hidden)
100.0.0.1/32 (3 entries, 1 announced)
TSI:
KRT in-kernel 100.0.0.1/32 -> {list:10.1.1.0, 10.1.1.8, 10.1.1.16 Flags source ip load-balance}
Page 0 idx 1, (group MX-to-TRUST_GW_Router type External) Type 1 val 0x12b04ce0 (adv_entry)
Advertised metrics:
Flags: Nexthop Change
Nexthop: Self
AS path: [1000] 500 I
Communities:
Advertise: 00000001
Path 100.0.0.1
from 10.1.1.8
Vector len 4. Val: 1
*BGP Preference: 170/-101
Next hop type: Router, Next hop index: 0
Address: 0xf918b24
Next-hop reference count: 2, Next-hop session id: 0
Kernel Table Id: 0
Source: 10.1.1.8
Next hop: 10.1.1.0 via ae1.0
Session Id: 0
Next hop: 10.1.1.8 via ae2.0, selected
Session Id: 0
Next hop: 10.1.1.16 via ae3.0
Session Id: 0
State: <Active Ext LoadBalConsistentHash>
Local AS: 1000 Peer AS: 500
Age: 3:14:15
Validation State: unverified
Task: BGP_500_1000.10.1.1.8
Announcement bits (3): 0-KRT 1-BGP_Multi_Path 2-BGP_RT_Background
AS path: 500 I
Accepted Multipath
Localpref: 100
Router ID: 10.255.33.26
Thread: junos-main
user@MX304# run show route 75/8
UNTRUST_VR.inet.0: 12 destinations, 12 routes (12 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
75.0.0.0/8 *[BGP/170] 06:27:07, localpref 100
AS path: 2500 I, validation-state: unverified
> to 80.1.1.1 via ae10.80
user@MX304# run show route 6/8
UNTRUST_VR.inet.0: 12 destinations, 12 routes (12 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
6.0.0.1/32 *[BGP/170] 03:13:30, MED 5, localpref 100
AS path: 500 I, validation-state: unverified
> to 10.1.1.18 via ae3.1
6.0.0.2/32 *[BGP/170] 03:13:31, MED 5, localpref 100
AS path: 500 I, validation-state: unverified
> to 10.1.1.10 via ae2.1
6.0.0.3/32 *[BGP/170] 02:12:57, MED 5, localpref 100
AS path: 500 I, validation-state: unverified
> to 10.1.1.2 via ae1.1
user@MX304# run show route 200/8
TRUST_VR.inet.0: 12 destinations, 14 routes (12 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
200.0.0.1/32 *[BGP/170] 06:26:30, localpref 100
AS path: 1500 I, validation-state: unverified
> to 40.1.1.1 via ae10.40
200.0.0.2/32 *[BGP/170] 06:26:30, localpref 100
AS path: 1500 I, validation-state: unverified
> to 40.1.1.1 via ae10.40
200.0.0.6/32 *[BGP/170] 02:14:13, localpref 100
AS path: 1500 I, validation-state: unverified
> to 40.1.1.1 via ae10.40
user@MX304# run show bgp summary
Warning: License key missing; requires 'bgp' license
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 8 Peers: 8 Down peers: 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.1.1.0 500 501 493 0 6 3:44:50 Establ
TRUST_VR.inet.0: 1/1/1/0
10.1.1.2 500 466 449 0 6 3:25:47 Establ
UNTRUST_VR.inet.0: 1/1/1/0
10.1.1.8 500 503 495 0 5 3:45:35 Establ
TRUST_VR.inet.0: 1/1/1/0
10.1.1.10 500 529 504 0 3 3:50:55 Establ
UNTRUST_VR.inet.0: 1/1/1/0
10.1.1.16 500 780 768 0 3 5:50:32 Establ
TRUST_VR.inet.0: 1/1/1/0
10.1.1.18 500 792 763 0 2 5:50:37 Establ
UNTRUST_VR.inet.0: 1/1/1/0
40.1.1.1 1500 13601 13345 0 1 4d 7:42:56 Establ
TRUST_VR.inet.0: 3/3/3/0
80.1.1.1 2500 13588 13405 0 1 4d 7:42:56 Establ
UNTRUST_VR.inet.0: 1/1/1/0
user@MX304# run show bfd session
Detect Transmit
Address State Interface Time Interval Multiplier
10.1.1.0 Up ae1.0 0.900 0.300 3
10.1.1.2 Up ae1.1 0.900 0.300 3
10.1.1.8 Up ae2.0 0.900 0.300 3
10.1.1.10 Up ae2.1 0.900 0.300 3
10.1.1.16 Up ae3.0 0.900 0.300 3
10.1.1.18 Up ae3.1 0.900 0.300 3
40.1.1.1 Up ae10.40 0.900 0.300 3
80.1.1.1 Up ae10.80 0.900 0.300 3
8 sessions, 8 clients
Cumulative transmit rate 26.7 pps, cumulative receive rate 26.7 pps
IPsecイニシエータの設定の確認
user@IPsec# run show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
380363 UP a8b642f8a828eb57 de97df1ba140e292 IKEv2 100.0.0.1
380364 UP 55b7e5a43d7462ba 201a1b9523442c50 IKEv2 100.0.0.1
380365 UP 3484ff0e307d1ddc 869cabffae9d261e IKEv2 100.0.0.1
user@IPsec# run show security ipsec security-associations
Total active tunnels: 3 Total IPsec sas: 3
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<542828 ESP:aes-gcm-256/aes256-gcm 0xd23dbafa 3009/ unlim - root 500 100.0.0.1
>542828 ESP:aes-gcm-256/aes256-gcm 0xb74e6311 3009/ unlim - root 500 100.0.0.1
<542827 ESP:aes-gcm-256/aes256-gcm 0xb2943202 3053/ unlim - root 500 100.0.0.1
>542827 ESP:aes-gcm-256/aes256-gcm 0xd87a527b 3053/ unlim - root 500 100.0.0.1
<542832 ESP:aes-gcm-256/aes256-gcm 0x960b3fe9 834/ unlim - root 500 100.0.0.1
>542832 ESP:aes-gcm-256/aes256-gcm 0x1143a22f 834/ unlim - root 500 100.0.0.1
SRX1の設定を確認する
user@SRX1> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
20 UP a8b642f8a828eb57 de97df1ba140e292 IKEv2 200.0.0.6
user@SRX1> show security ipsec security-associations
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<500017 ESP:aes-gcm-256/aes256-gcm 0x1143a22f 1314/ unlim - root 500 200.0.0.6
>500017 ESP:aes-gcm-256/aes256-gcm 0x960b3fe9 1314/ unlim - root 500 200.0.0.6
user@SRX1> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
4 4 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.1.1.1 1000 500 505 0 4 3:47:18 Establ
inet.0: 3/3/3/0
10.1.1.3 2000 456 470 0 4 3:28:15 Establ
inet.0: 1/1/1/0
user@SRX1> show bfd session
Detect Transmit
Address State Interface Time Interval Multiplier
10.1.1.1 Up ae1.0 0.900 0.300 3
10.1.1.3 Up ae1.1 0.900 0.300 3
2 sessions, 2 clients
Cumulative transmit rate 6.7 pps, cumulative receive rate 6.7 pps
user@SRX1> show route 200.0.0.0/8
inet.0: 27 destinations, 27 routes (26 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
200.0.0.1/32 *[BGP/170] 03:47:45, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.1 via ae1.0
200.0.0.2/32 *[BGP/170] 03:47:45, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.1 via ae1.0
200.0.0.6/32 *[BGP/170] 02:16:35, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.1 via ae1.0
user@SRX1> show route 6.0.0.0/8
inet.0: 27 destinations, 27 routes (26 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
6.0.0.3/32 *[ARI-TS/5] 02:16:49, metric 5
> via st0.1
user@SRX1> show route 75.0.0.0/8
inet.0: 27 destinations, 27 routes (26 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
75.0.0.0/8 *[BGP/170] 03:29:51, localpref 100
AS path: 2000 2500 I, validation-state: unverified
> to 10.1.1.3 via ae1.1
user@SRX1> show security flow session protocol esp
Session ID: 2894133, Policy name: N/A, Timeout: N/A, Session State: Valid
In: 200.0.0.6/0 --> 100.0.0.1/0;esp, Conn Tag: 0x0, If: ae1.0, Pkts: 0, Bytes: 0,
Session ID: 2894160, Policy name: N/A, Timeout: N/A, Session State: Valid
In: 200.0.0.6/4419 --> 100.0.0.1/41519;esp, Conn Tag: 0x0, If: lo0.0, Pkts: 0, Bytes: 0,
Total sessions: 2
user@SRX1> show security flow session protocol udp source-prefix 75.0.0.0/8
Session ID: 2894145, Policy name: IPSEC_DATA_POLICY, Timeout: 60, Session State: Valid
In: 75.0.0.3/2001 --> 6.0.0.3/1002;udp, Conn Tag: 0x0, If: ae1.1, Pkts: 51609457, Bytes: 30036703974,
Out: 6.0.0.3/1002 --> 75.0.0.3/2001;udp, Conn Tag: 0x0, If: st0.1, Pkts: 7741418, Bytes: 4505505276,
SRX2 の設定を確認する
user@SRX2> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
26 UP 3484ff0e307d1ddc 869cabffae9d261e IKEv2 200.0.0.2
user@SRX2> show security ipsec security-associations
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<500018 ESP:aes-gcm-256/aes256-gcm 0xd87a527b 3257/ unlim - root 500 200.0.0.2
>500018 ESP:aes-gcm-256/aes256-gcm 0xb2943202 3257/ unlim - root 500 200.0.0.2
user@SRX2> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
4 4 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.1.1.9 1000 511 516 0 3 3:52:21 Establ
inet.0: 3/3/3/0
10.1.1.11 2000 520 542 0 1 3:57:40 Establ
inet.0: 1/1/1/0
user@SRX2> show bfd session
Detect Transmit
Address State Interface Time Interval Multiplier
10.1.1.9 Up ae1.0 0.900 0.300 3
10.1.1.11 Up ae1.1 0.900 0.300 3
2 sessions, 2 clients
Cumulative transmit rate 6.7 pps, cumulative receive rate 6.7 pps
user@SRX2> show route 200.0.0.0/8
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
200.0.0.1/32 *[BGP/170] 03:52:29, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.9 via ae1.0
200.0.0.2/32 *[BGP/170] 03:52:29, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.9 via ae1.0
200.0.0.6/32 *[BGP/170] 02:20:34, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.9 via ae1.0
user@SRX2> show route 6.0.0.0/8
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
6.0.0.2/32 *[ARI-TS/5] 03:21:10, metric 5
> via st0.1
user@SRX2> show route 75.0.0.0/8
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
75.0.0.0/8 *[BGP/170] 03:58:00, localpref 100
AS path: 2000 2500 I, validation-state: unverified
> to 10.1.1.11 via ae1.1
user@SRX2> show security flow session protocol esp
Session ID: 2897660, Policy name: N/A, Timeout: N/A, Session State: Valid
In: 200.0.0.2/0 --> 100.0.0.1/0;esp, Conn Tag: 0x0, If: ae1.0, Pkts: 0, Bytes: 0,
Session ID: 2897694, Policy name: N/A, Timeout: N/A, Session State: Valid
In: 200.0.0.2/55418 --> 100.0.0.1/21115;esp, Conn Tag: 0x0, If: lo0.0, Pkts: 0, Bytes: 0,
Total sessions: 2
user@SRX2> show security flow session protocol udp source-prefix 75.0.0.0/8
Session ID: 2897677, Policy name: IPSEC_DATA_POLICY, Timeout: 60, Session State: Valid
In: 75.0.0.2/2001 --> 6.0.0.2/1009;udp, Conn Tag: 0x0, If: ae1.1, Pkts: 52336685, Bytes: 30459950670,
Out: 6.0.0.2/1009 --> 75.0.0.2/2001;udp, Conn Tag: 0x0, If: st0.1, Pkts: 7850503, Bytes: 4568992746,
SRX3設定の確認
user@SRX3> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
19 UP 55b7e5a43d7462ba 201a1b9523442c50 IKEv2 200.0.0.1
user@SRX3> show security ipsec security-associations
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<500009 ESP:aes-gcm-256/aes256-gcm 0xb74e6311 3107/ unlim - root 500 200.0.0.1
>500009 ESP:aes-gcm-256/aes256-gcm 0xd23dbafa 3107/ unlim - root 500 200.0.0.1
user@SRX3> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
4 4 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.1.1.17 1000 787 797 0 1 5:58:59 Establ
inet.0: 3/3/3/0
10.1.1.19 2000 783 810 0 0 5:59:04 Establ
inet.0: 1/1/1/0
user@SRX3> show bfd session
Detect Transmit
Address State Interface Time Interval Multiplier
10.1.1.17 Up ae1.0 0.900 0.300 3
10.1.1.19 Up ae1.1 0.900 0.300 3
2 sessions, 2 clients
Cumulative transmit rate 6.7 pps, cumulative receive rate 6.7 pps
user@SRX3> show route 200.0.0.0/8
inet.0: 26 destinations, 26 routes (26 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
200.0.0.1/32 *[BGP/170] 05:59:07, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.17 via ae1.0
200.0.0.2/32 *[BGP/170] 05:59:07, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.17 via ae1.0
200.0.0.6/32 *[BGP/170] 02:22:15, localpref 100
AS path: 1000 1500 I, validation-state: unverified
> to 10.1.1.17 via ae1.0
user@SRX3> show route 6.0.0.0/8
inet.0: 26 destinations, 26 routes (26 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
6.0.0.1/32 *[ARI-TS/5] 03:22:51, metric 5
> via st0.1
user@SRX3> show route 75.0.0.0/8
inet.0: 26 destinations, 26 routes (26 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
75.0.0.0/8 *[BGP/170] 05:59:22, localpref 100
AS path: 2000 2500 I, validation-state: unverified
> to 10.1.1.19 via ae1.1
user@SRX3> show security flow session protocol esp
Session ID: 2889066, Policy name: N/A, Timeout: N/A, Session State: Valid
In: 200.0.0.1/0 --> 100.0.0.1/0;esp, Conn Tag: 0x0, If: ae1.0, Pkts: 0, Bytes: 0,
Session ID: 2889104, Policy name: N/A, Timeout: N/A, Session State: Valid
In: 200.0.0.1/46926 --> 100.0.0.1/25361;esp, Conn Tag: 0x0, If: lo0.0, Pkts: 0, Bytes: 0,
Total sessions: 2
user@SRX3> show security flow session protocol udp source-prefix 75.0.0.0/8
Session ID: 2889087, Policy name: IPSEC_DATA_POLICY, Timeout: 60, Session State: Valid
In: 75.0.0.1/2001 --> 6.0.0.1/1005;udp, Conn Tag: 0x0, If: ae1.1, Pkts: 53008715, Bytes: 30851072130,
Out: 6.0.0.1/1005 --> 75.0.0.1/2001;udp, Conn Tag: 0x0, If: st0.1, Pkts: 7951308, Bytes: 4627661256,
