示例:为瞻博网络安全连接配置 LDAP 身份验证(CLI 过程)
概述
LDAP有助于对用户进行身份验证。当您使用 LDAP 作为身份验证选项时,您可以定义一个或多个 LDAP 组,并根据组成员身份使用特定的本地 IP 池进行地址分配。如果未为每个组指定本地 IP 池,Junos OS 将从访问配置文件中配置的本地 IP 池中分配一个 IP 地址。
要配置用户组,请在 [edit access ldap-options] 层级包含allowed-groups 语句。这些组名与 LDAP 目录中的名称匹配。
请考虑以下 LDAP 组,例如 group1、group2 和 group3。可以将 group1 分配给地址池 Juniper_Secure_Connect_Addr-Pool。您可以将 group2 分配给地址池 poolB。您可以将 group3 分配给地址池 poolC。
-
User1 属于 group1。User1 的组与其中一个配置的组匹配,则对 User1 进行身份验证。根据组成员身份,系统从以下地址池 Juniper_Secure_Connect_Addr-Pool 中将 IP 地址分配给用户 1。
-
用户 2 属于组 2。User2 的组与其中一个配置的组匹配,User2 已通过身份验证。根据组成员身份,系统从以下地址池池 B 中将 IP 地址分配给用户 2。
-
用户 3 属于组 3。User3 的组与其中一个配置的组匹配,User3 已通过身份验证。根据组成员身份,系统从以下地址池 poolC 中将 IP 地址分配给 User3。
-
User4 的组与任一配置的组都不匹配。
表 1 描述了在全局访问级别和访问配置文件中配置时 ldap-options 的 LDAP 服务器响应。配置文件配置的优先级高于全局配置。
| 用户名 | 配置 匹配组 | LDAP 服务器 返回组 | 地址池 | 作 |
|---|---|---|---|---|
| 用户 1 | 组 1 | 组 1、组 2、组 3 | Juniper_Secure_Connect_Addr池 | 接受(匹配配置的组) |
| 用户 2 | 组 2 | 组 1、组 2、组 3 | 池B | 接受(匹配配置的组) |
| 用户 3 | 第 3 组 | 组 1、组 2、组 3 | poolC | 接受(匹配配置的组) |
| 用户 4 | 第 4 组 | groupX、groupY、groupZ | poolD | 拒绝(不匹配已配置的匹配组) |
此示例使用 LDAP 作为用户属于单个组的身份验证选项。
要求
此示例使用以下硬件和软件组件:
-
任何 SRX 系列防火墙
-
Junos OS 23.1R1 版
开始之前:
-
LDAP 选项,请参阅 LADP-OPTIONS
-
使用 TLS/SSL 启用 LDAP 身份验证以实现安全连接,请参阅 使用 TLS/SSL 启用 LDAP 身份验证以实现安全连接。
有关先决条件的信息,请参阅 瞻博网络安全连接的系统要求。
您必须确保 SRX 系列防火墙使用签名证书或自签名证书,而不是默认的系统生成的证书。开始配置瞻博网络安全连接之前,必须通过执行以下命令将证书绑定到 SRX 系列防火墙:
user@host# set system services web-management https pki-local-certificate <cert_name>
例如:
user@host# set system services web-management https pki-local-certificate SRX_Certificate
其中SRX_Certificate是从证书颁发机构获得的证书或自签名证书。
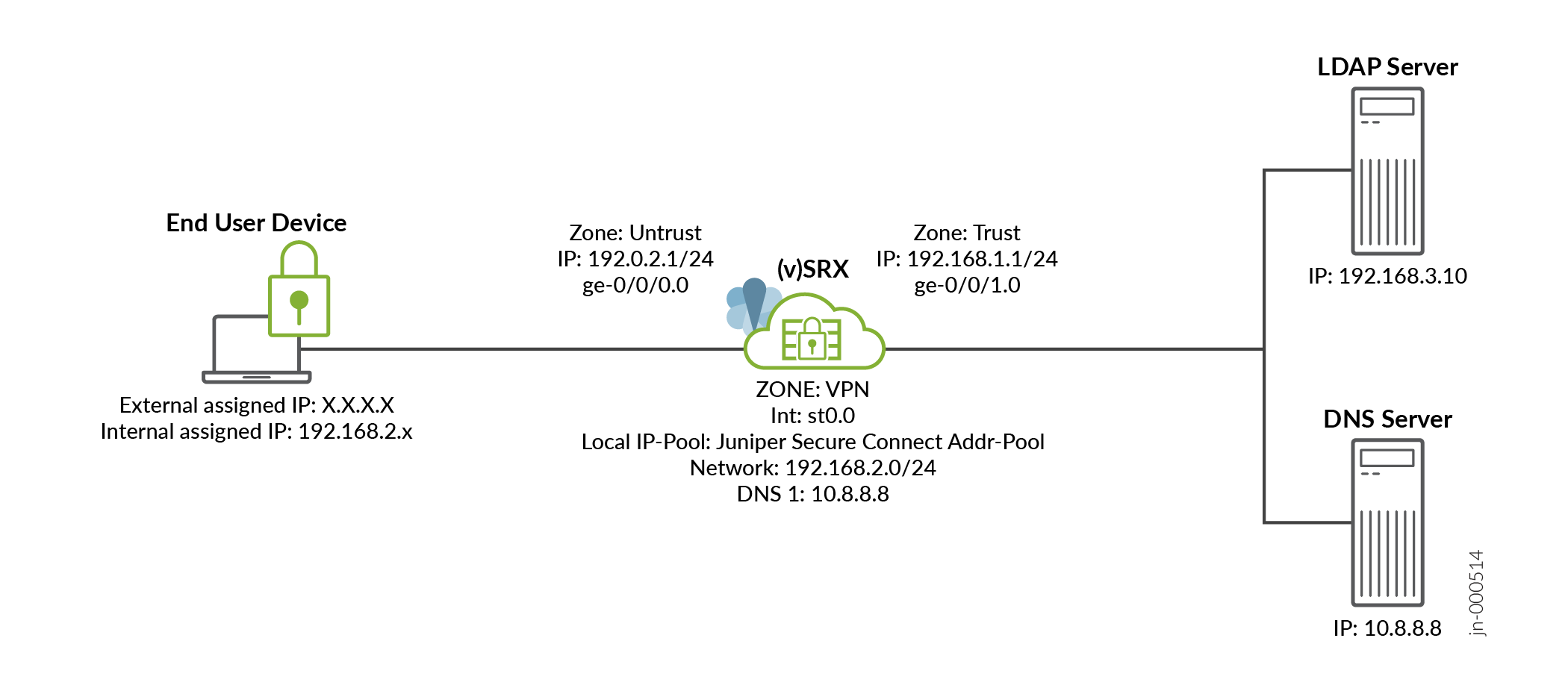
拓扑学
下图显示了此示例中的拓扑。
图 1:为瞻博网络安全连接配置 LDAP 身份验证
配置
在此示例中,我们使用 LDAP 作为用户属于单个组的身份验证选项。
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到 [编辑] 层次结构级别的 CLI 中。
set security ike proposal JUNIPER_SECURE_CONNECT authentication-method pre-shared-keys set security ike proposal JUNIPER_SECURE_CONNECT dh-group group19 set security ike proposal JUNIPER_SECURE_CONNECT authentication-algorithm sha-384 set security ike proposal JUNIPER_SECURE_CONNECT encryption-algorithm aes-256-cbc set security ike proposal JUNIPER_SECURE_CONNECT lifetime-seconds 28800 set security ike policy JUNIPER_SECURE_CONNECT mode aggressive set security ike policy JUNIPER_SECURE_CONNECT proposals JUNIPER_SECURE_CONNECT set security ike policy JUNIPER_SECURE_CONNECT pre-shared-key ascii-text "$9$vWL8xd24Zk.5bs.5QFAtM8X7bsgoJDHq4o" set security ike gateway JUNIPER_SECURE_CONNECT dynamic hostname ra.example.com set security ike gateway JUNIPER_SECURE_CONNECT dynamic ike-user-type shared-ike-id set security ike gateway JUNIPER_SECURE_CONNECT ike-policy JUNIPER_SECURE_CONNECT set security ike gateway JUNIPER_SECURE_CONNECT dead-peer-detection optimized set security ike gateway JUNIPER_SECURE_CONNECT dead-peer-detection interval 10 set security ike gateway JUNIPER_SECURE_CONNECT dead-peer-detection threshold 5 set security ike gateway JUNIPER_SECURE_CONNECT version v1-only set security ike gateway JUNIPER_SECURE_CONNECT aaa access-profile JUNIPER_SECURE_CONNECT set security ike gateway JUNIPER_SECURE_CONNECT tcp-encap-profile SSL-VPN set security ike gateway JUNIPER_SECURE_CONNECT external-interface ge-0/0/0 set security ipsec proposal JUNIPER_SECURE_CONNECT authentication-algorithm hmac-sha-256-128 set security ipsec proposal JUNIPER_SECURE_CONNECT encryption-algorithm aes-256-cbc set security ipsec proposal JUNIPER_SECURE_CONNECT lifetime-seconds 3600 set security ipsec policy JUNIPER_SECURE_CONNECT perfect-forward-secrecy keys group19 set security ipsec policy JUNIPER_SECURE_CONNECT proposals JUNIPER_SECURE_CONNECT set security ipsec vpn JUNIPER_SECURE_CONNECT bind-interface st0.0 set security ipsec vpn JUNIPER_SECURE_CONNECT ike gateway JUNIPER_SECURE_CONNECT set security ipsec vpn JUNIPER_SECURE_CONNECT ike ipsec-policy JUNIPER_SECURE_CONNECT set security ipsec vpn JUNIPER_SECURE_CONNECT traffic-selector ts1 local-ip 0.0.0.0/0 set security ipsec vpn JUNIPER_SECURE_CONNECT traffic-selector ts1 remote-ip 0.0.0.0/0 set security remote-access profile ra.example.com ipsec-vpn JUNIPER_SECURE_CONNECT set security remote-access profile ra.example.com access-profile JUNIPER_SECURE_CONNECT set security remote-access profile ra.example.com client-config JUNIPER_SECURE_CONNECT set security remote-access client-config JUNIPER_SECURE_CONNECT connection-mode manual set security remote-access client-config JUNIPER_SECURE_CONNECT dead-peer-detection interval 10 set security remote-access client-config JUNIPER_SECURE_CONNECT dead-peer-detection threshold 5 set access address-assignment pool Juniper_Secure_Connect_Addr-Pool family inet network 192.168.2.0/24 set access address-assignment pool Juniper_Secure_Connect_Addr-Pool family inet xauth-attributes primary-dns 10.8.8.8/32 set access address-assignment pool Juniper_Secure_Connect_Addr-Pool family inet xauth-attributes primary-wins 192.168.3.10/32 set access profile JUNIPER_SECURE_CONNECT authentication-order ldap set access profile JUNIPER_SECURE_CONNECT ldap-options base-distinguished-name CN=Users,DC=juniper,DC=net set access profile JUNIPER_SECURE_CONNECT ldap-options search search-filter CN= set access profile JUNIPER_SECURE_CONNECT ldap-options search admin-search distinguished-name CN=Administrator,CN=Users,DC=juniper,DC=net set access profile JUNIPER_SECURE_CONNECT ldap-options search admin-search password "$9$Bmf1hreK8x7Vrl24ZGiHkqmPQ36/t0OR" set access profile JUNIPER_SECURE_CONNECT ldap-options allowed-groups group1 address-assignment pool Juniper_Secure_Connect_Addr-Pool set access profile JUNIPER_SECURE_CONNECT ldap-server 192.168.3.10 set access firewall-authentication web-authentication default-profile JUNIPER_SECURE_CONNECT set services ssl termination profile Juniper_SCC-SSL-Term-Profile server-certificate JUNIPER_SECURE_CONNECT(RSA) set security tcp-encap profile SSL-VPN ssl-profile Juniper_SCC-SSL-Term-Profile set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 match source-address any set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 match destination-address any set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 match application any set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 then permit set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 then log session-close set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 match source-address any set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 match destination-address any set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 match application any set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 then permit set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 then log session-close set interfaces ge-0/0/0 description untrust set interfaces ge-0/0/0 unit 0 family inet address 192.0.2.1/24 set interfaces ge-0/0/1 description trust set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24 set interfaces st0 unit 0 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services https set security zones security-zone untrust host-inbound-traffic system-services tcp-encap set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone vpn interface st0.0
分步过程
下面的示例要求您在各个配置层级中进行导航。
- 配置一个或多个互联网密钥交换 (IKE) 提议;然后将这些提议与 IKE 策略相关联。配置 IKE 网关选项。
user@host# set security ike proposal JUNIPER_SECURE_CONNECT authentication-method pre-shared-keys user@host# set security ike proposal JUNIPER_SECURE_CONNECT dh-group group19 user@host# set security ike proposal JUNIPER_SECURE_CONNECT authentication-algorithm sha-384 user@host# set security ike proposal JUNIPER_SECURE_CONNECT encryption-algorithm aes-256-cbc user@host# set security ike proposal JUNIPER_SECURE_CONNECT lifetime-seconds 28800 user@host# set security ike policy JUNIPER_SECURE_CONNECT mode aggressive user@host# set security ike policy JUNIPER_SECURE_CONNECT proposals JUNIPER_SECURE_CONNECT user@host# set security ike policy JUNIPER_SECURE_CONNECT pre-shared-key ascii-text "$9$vWL8xd24Zk.5bs.5QFAtM8X7bsgoJDHq4o" user@host# set security ike gateway JUNIPER_SECURE_CONNECT dynamic hostname ra.example.com user@host# set security ike gateway JUNIPER_SECURE_CONNECT dynamic ike-user-type shared-ike-id user@host# set security ike gateway JUNIPER_SECURE_CONNECT ike-policy JUNIPER_SECURE_CONNECT user@host# set security ike gateway JUNIPER_SECURE_CONNECT dead-peer-detection optimized user@host# set security ike gateway JUNIPER_SECURE_CONNECT dead-peer-detection interval 10 user@host# set security ike gateway JUNIPER_SECURE_CONNECT dead-peer-detection threshold 5 user@host# set security ike gateway JUNIPER_SECURE_CONNECT version v1-only user@host# set security ike gateway JUNIPER_SECURE_CONNECT aaa access-profile JUNIPER_SECURE_CONNECT user@host# set security ike gateway JUNIPER_SECURE_CONNECT tcp-encap-profile SSL-VPN user@host# set security ike gateway JUNIPER_SECURE_CONNECT external-interface ge-0/0/0
- 配置一个或多个 IPsec 提议;然后将这些提议与 IPsec 策略相关联。配置 IPsec VPN 参数和流量选择器。
user@host# set security ipsec proposal JUNIPER_SECURE_CONNECT authentication-algorithm hmac-sha-256-128 user@host# set security ipsec proposal JUNIPER_SECURE_CONNECT encryption-algorithm aes-256-cbc user@host# set security ipsec proposal JUNIPER_SECURE_CONNECT lifetime-seconds 3600 user@host# set security ipsec policy JUNIPER_SECURE_CONNECT perfect-forward-secrecy keys group19 user@host# set security ipsec policy JUNIPER_SECURE_CONNECT proposals JUNIPER_SECURE_CONNECT user@host# set security ipsec vpn JUNIPER_SECURE_CONNECT bind-interface st0.0 user@host# set security ipsec vpn JUNIPER_SECURE_CONNECT ike gateway JUNIPER_SECURE_CONNECT user@host# set security ipsec vpn JUNIPER_SECURE_CONNECT ike ipsec-policy JUNIPER_SECURE_CONNECT user@host# set security ipsec vpn JUNIPER_SECURE_CONNECT traffic-selector ts1 local-ip 0.0.0.0/0 user@host# set security ipsec vpn JUNIPER_SECURE_CONNECT traffic-selector ts1 remote-ip 0.0.0.0/0
- 配置远程访问配置文件和客户端配置。
user@host# set security remote-access profile ra.example.com ipsec-vpn JUNIPER_SECURE_CONNECT user@host# set security remote-access profile ra.example.com access-profile JUNIPER_SECURE_CONNECT user@host# set security remote-access profile ra.example.com client-config JUNIPER_SECURE_CONNECT user@host# set security remote-access client-config JUNIPER_SECURE_CONNECT connection-mode manual user@host# set security remote-access client-config JUNIPER_SECURE_CONNECT dead-peer-detection interval 10 user@host# set security remote-access client-config JUNIPER_SECURE_CONNECT dead-peer-detection threshold 5
- 指定外部认证顺序的 LDAP 服务器。
user@host# set access address-assignment pool Juniper_Secure_Connect_Addr-Pool family inet network 192.168.2.0/24 user@host# set access address-assignment pool Juniper_Secure_Connect_Addr-Pool family inet xauth-attributes primary-dns 10.8.8.8/32 user@host# set access address-assignment pool Juniper_Secure_Connect_Addr-Pool family inet xauth-attributes primary-wins 192.168.3.10/32 user@host# set access profile JUNIPER_SECURE_CONNECT authentication-order ldap user@host# set access profile JUNIPER_SECURE_CONNECT ldap-options base-distinguished-name CN=Users,DC=juniper,DC=net user@host# set access profile JUNIPER_SECURE_CONNECT ldap-options search search-filter CN= user@host# set access profile JUNIPER_SECURE_CONNECT ldap-options search admin-search distinguished-name CN=Administrator,CN=Users,DC=juniper,DC=net user@host# set access profile JUNIPER_SECURE_CONNECT ldap-options search admin-search password "$9$Bmf1hreK8x7Vrl24ZGiHkqmPQ36/t0OR" user@host# set access profile JUNIPER_SECURE_CONNECT ldap-options allowed-groups group1 address-assignment pool Juniper_Secure_Connect_Addr-Pool user@host# set access profile JUNIPER_SECURE_CONNECT ldap-server 192.168.3.10 user@host# set access firewall-authentication web-authentication default-profile JUNIPER_SECURE_CONNECT
-
创建 SSL 终止配置文件。SSL 终止是 SRX 系列防火墙充当 SSL 代理服务器并终止客户端 SSL 会话的过程。输入 SSL 终止配置文件的名称,然后选择用于 SRX 系列防火墙上 SSL 终止的服务器证书。服务器证书是本地证书标识符。服务器证书用于验证服务器的身份。
user@host# set services ssl termination profile Juniper_SCC-SSL-Term-Profile server-certificate JUNIPER_SECURE_CONNECT(RSA)
创建 SSL VPN 配置文件。 请参阅 tcp-encap。
user@host# set security tcp-encap profile SSL-VPN ssl-profile Juniper_SCC-SSL-Term-Profile
-
创建防火墙策略。
创建安全策略以允许从信任区域到 VPN 区域的流量。
user@host# set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 match source-address any user@host# set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 match destination-address anyuser@host# set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 match application any user@host# set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 then permit user@host# set security policies from-zone trust to-zone VPN policy JUNIPER_SECURE_CONNECT-1 then log session-close
创建安全策略以允许从 VPN 区域到信任区域的流量。
user@host# set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 match source-address any user@host# set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 match destination-address any user@host# set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 match application any user@host# set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 then permit user@host# set security policies from-zone VPN to-zone trust policy JUNIPER_SECURE_CONNECT-2 then log session-close
-
配置以太网接口信息。
user@host# set interfaces ge-0/0/0 description untrust user@host# set interfaces ge-0/0/0 unit 0 family inet address 192.0.2.1/24 user@host# set interfaces ge-0/0/1 description trust user@host# set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24
配置 st0 接口,并将系列设置为 inet。
user@host# set interfaces st0 unit 0 family inet
-
配置安全区域。
user@host# set security zones security-zone untrust host-inbound-traffic system-services ike user@host# set security zones security-zone untrust host-inbound-traffic system-services https user@host# set security zones security-zone untrust host-inbound-traffic system-services tcp-encap user@host# set security zones security-zone untrust interfaces ge-0/0/0.0 user@host# set security zones security-zone trust interfaces ge-0/0/1.0 user@host# set security zones security-zone vpn interface st0.0
结果
检查配置结果:
[edit security ike]
proposal JUNIPER_SECURE_CONNECT {
authentication-method pre-shared-keys;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 28800;
}
policy JUNIPER_SECURE_CONNECT {
mode aggressive;
proposals JUNIPER_SECURE_CONNECT;
pre-shared-key ascii-text “$9$vWL8xd24Zk.5bs.5QFAtM8X7bsgoJDHq4o"; ## SECRET-DATA
}
gateway JUNIPER_SECURE_CONNECT {
dynamic {
hostname ra.example.com;
ike-user-type shared-ike-id;
}
ike-policy JUNIPER_SECURE_CONNECT;
dead-peer-detection {
optimized;
interval 10;
threshold 5;
}
version v1-only;
aaa {
access-profile JUNIPER_SECURE_CONNECT;
}
tcp-encap-profile SSL-VPN;
external-interface ge-0/0/0;
}
[edit security ipsec]
proposal JUNIPER_SECURE_CONNECT {
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy JUNIPER_SECURE_CONNECT {
perfect-forward-secrecy {
keys group19;
}
proposals JUNIPER_SECURE_CONNECT;
}
vpn JUNIPER_SECURE_CONNECT {
bind-interface st0.0;
ike {
gateway JUNIPER_SECURE_CONNECT;
ipsec-policy JUNIPER_SECURE_CONNECT;
}
traffic-selector ts1 {
local-ip 0.0.0.0/0;
remote-ip 0.0.0.0/0;
}
}
[edit security remote-access]
profile ra.example.com {
ipsec-vpn JUNIPER_SECURE_CONNECT;
access-profile JUNIPER_SECURE_CONNECT;
client-config JUNIPER_SECURE_CONNECT;
}
client-config JUNIPER_SECURE_CONNECT {
connection-mode manual;
dead-peer-detection {
interval 10;
threshold 5;
}
}
[edit access]
address-assignment {
pool Juniper_Secure_Connect_Addr-Pool {
family inet {
network 192.168.2.0/24;
xauth-attributes {
primary-dns 10.8.8.8/32;
primary-wins 192.168.3.10/32;
}
}
}
}
profile JUNIPER_SECURE_CONNECT {
authentication-order ldap;
ldap-options {
base-distinguished-name DC=juniper,DC=net;
search {
search-filter CN=
admin-search {
distinguished-name CN=Administrator,CN=Users,DC=juniper,DC=net;
password "$9$Bmf1hreK8x7Vrl24ZGiHkqmPQ36/t0OR"; ## SECRET-DATA
}
}
allowed-groups {
group1 {
address-assignment {
pool Juniper_Secure_Connect_Addr-Pool;
}
}
}
}
ldap-server 192.168.3.10;
}
firewall-authentication {
web-authentication {
default-profile JUNIPER_SECURE_CONNECT;
}
}
[edit services]
ssl {
termination {
profile Juniper_SCC-SSL-Term-Profile {
server-certificate JUNIPER_SECURE_CONNECT(RSA);
}
}
}
确保您已具有要附加到 SSL 终止配置文件的服务器证书。
[edit security]
tcp-encap {
profile SSL-VPN {
ssl-profile Juniper_SCC-SSL-Term-Profile;
}
}
policies {
from-zone trust to-zone VPN {
policy JUNIPER_SECURE_CONNECT-1 {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
log {
session-close;
}
}
}
}
from-zone VPN to-zone trust {
policy JUNIPER_SECURE_CONNECT-2 {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
log {
session-close;
}
}
}
}
}
[edit interfaces]
ge-0/0/0 {
description untrust;
unit 0 {
family inet {
address 192.0.2.1/24;
}
}
}
ge-0/0/1 {
description trust;
unit 0 {
family inet {
address 192.168.1.1/24;
}
}
}
st0 {
unit 0 {
family inet;
}
}
[edit security zones]
security-zone untrust {
host-inbound-traffic {
system-services (ike | https | tcp-encap);
}
interfaces {
ge-0/0/0.0;
}
}
security-zone trust {
interfaces {
ge-0/0/1.0;
}
}
security-zone vpn {
interfaces {
st0.0;
}
}
验证
要确认配置工作正常,请输入以下 show 命令。
验证 IPsec、IKE 和组信息
目的
当您使用访问配置文件并在该配置文件中进行配置 ldap-options 时JUNIPER_SECURE_CONNECT根据 LDAP 服务器响应显示可能的结果列表。
行动
在作模式下,输入以下命令:
user@host> show network-access address-assignment pool Juniper_Secure_Connect_Addr-Pool IP address/prefix Hardware address Host/User Type 192.168.2.3 FF:FF:C0:A8:02:03 user1 xauth
user@host> show security ike security-associations detail
IKE peer 192.0.2.100, Index 6771534, Gateway Name: JUNIPER_SECURE_CONNECT
Role: Responder, State: UP
Initiator cookie: f174398039244783, Responder cookie: ffb63035b9f3f098
Exchange type: Aggressive, Authentication method: Pre-shared-keys
Local: 192.0.2.1:500, Remote: 192.0.2.100:10952
Lifetime: Expires in 28746 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Disabled, Size: 0
Remote Access Client Info: Juniper Secure Connect
Peer ike-id: ra.example.com
AAA assigned IP: 192.168.2.3
Algorithms:
Authentication : hmac-sha384-192
Encryption : aes256-cbc
Pseudo random function: hmac-sha384
Diffie-Hellman group : DH-group-19
Traffic statistics:
Input bytes : 2058
Output bytes : 1680
Input packets: 12
Output packets: 10
Input fragmentated packets: 0
Output fragmentated packets: 0
IPSec security associations: 1 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 192.0.2.1:500, Remote: 192.0.2.100:10952
Local identity: 192.0.2.1
Remote identity: ra.example.com
Flags: IKE SA is created
user@host> show security ike active-peer detail Peer address: 192.0.2.100, Port: 10952, Peer IKE-ID : ra.example.com AAA username: user1 Assigned network attributes: IP Address : 192.168.2.3 , netmask : 255.255.255.0 DNS Address : 10.8.8.8 , DNS2 Address : 0.0.0.0 WINS Address : 192.168.3.10 , WINS2 Address : 0.0.0.0 Previous Peer address : 0.0.0.0, Port : 0 Active IKE SA indexes : 6771534 IKE SA negotiated : 1 IPSec tunnels active : 1, IPSec Tunnel IDs : 67108869 DPD Config Mode : optimized DPD Config Interval: 10 DPD Config Treshold: 5 DPD Config P1SA IDX: 6771534 DPD Flags : REMOTE_ACCESS DPD Stats Req sent: 0, DPD Stats Resp rcvd: 0 DPD Statistics : DPD TTL :5 DPD seq-no :515423892 DPD Statistics : DPD triggerd p1SA :0 DPD Reserved :0
user@host> show security ipsec security-associations detail
ID: 67108869 Virtual-system: root, VPN Name: JUNIPER_SECURE_CONNECT
Local Gateway: 192.0.2.1, Remote Gateway: 192.0.2.100
Traffic Selector Name: ts1
Local Identity: ipv4(0.0.0.0-255.255.255.255)
Remote Identity: ipv4(192.168.2.3)
Version: IKEv1
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.0
Port: 500, Nego#: 4, Fail#: 0, Def-Del#: 0 Flag: 0x24608f29
Multi-sa, Configured SAs# 1, Negotiated SAs#: 1
Tunnel events:
Tue Mar 28 2023 11:34:36: IPSec SA negotiation successfully completed (1 times)
Tue Mar 28 2023 11:34:36: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Mar 28 2023 11:34:35: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: f74fcaad, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3435 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2838 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 8605b13f, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3435 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2838 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
意义
命令输出提供匹配组的详细信息。
