示例:使用单个 AFTR 和多个服务 PIC 配置冗余和负载平衡
此示例说明如何使用单个 DS-Lite 地址族转换路由器 (AFTR) 配置冗余和负载平衡。
要求
此示例使用以下硬件和软件组件:
瞻博网络 MX 系列 3D 通用边缘路由器,配备多服务密集端口集中器 (DPC)
在 AFTR 上运行的瞻博网络® Junos 操作系统 (Junos® OS) 10.4 或更高版本
此配置示例已使用列出的软件版本进行了测试,并假定适用于所有更高版本。
概述
您可以使用同一 AFTR 上的多个服务 PIC 和单个任播地址(其中两个服务 PIC 主动对流量进行负载均衡)来提供冗余和负载平衡。 在图 1 中,三个基本桥接宽带元件(B4 或软线启动器)使用不同的隧道连接到 AFTR 的软线 (ID 1001::1)。AFTR 有两种用于负载平衡和冗余的服务。当 HTTP 客户端连接到服务器时,将在服务 PIC 之间对流量进行负载平衡。此外,当其中一个服务 PIC 关闭时,来自所有三个 B4 的流量将通过另一个服务 PIC 进行通道化。
拓扑
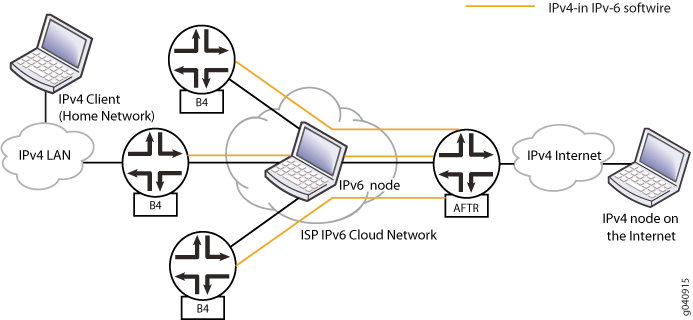
家庭网络中的 IPv4 客户端或主机配置了到 ISP 的 IPv4 接口和到互联网上 IPv4 服务器的静态路由。
多个 B4 或软线启动器配置了一个 IPv4 接口、一个 IPv6 接口和一个到任播地址的 IPv4-in-IPv6 隧道。
IPv6 云中的纯 IPv6 节点配置了到 IPv6 接口的接口。
AFTR 与互联网之间的 NAT 池地址范围为 33.33.33.1 至 33.33.33.32(对应 NAT 规则
dslite-nat-rule1),44.44.44.1 至 44.44.44.32(对应 NAT 规则dslite-nat-rule2)。NAT 规则对应于服务 PIC,NAT 规则
dslite-nat-rule1dslite-nat-rule2对应于服务 PICsp-0/1/0sp-1/3/0。AFTR 配置了任播地址 2001::1/16,用于朝向三个 B4 的接口。为从 AFTR 到互联网的接口配置了地址 200.200.200.1/24。两个服务 PIC 是
sp-0/1/0和sp-1/3/0。互联网上的 IPv4 节点配置了用于反向流量的 IPv4 接口和路由。
配置
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改与您的网络配置匹配所需的任何详细信息,然后将命令复制并粘贴到层次结构级别的 CLI [edit] 中。
AFTR
set chassis fpc 1 pic 1 adaptive-services service-package layer-3 set services nat pool dslite-pool1 address-range low 33.33.33.1 high 33.33.33.32 set services nat pool dslite-pool1 port automatic set services nat pool dslite-pool2 address-range low 44.44.44.1 high 44.44.44.32 set services nat pool dslite-pool2 port automatic set services nat rule dslite-nat-rule1 match-direction input set services nat rule dslite-nat-rule1 term t1 from source-address 20.20.0.0/16 set services nat rule dslite-nat-rule1 term t1 then translated source-pool dslite-pool1 set services nat rule dslite-nat-rule1 term t1 then translated translation-type napt-44 set services nat rule dslite-nat-rule2 match-direction input set services nat rule dslite-nat-rule2 term t1 from source-address 20.20.0.0/16 set services nat rule dslite-nat-rule2 term t1 then translated source-pool dslite-pool2 set services nat rule dslite-nat-rule2 term t1 then translated translation-type napt-44 set services softwire softwire-concentrator ds-lite ds1 softwire-address 1001::1 set services softwire softwire-concentrator ds-lite ds1 mtu-v6 9192 set services softwire rule dslite-rule match-direction input set services softwire rule dslite-rule term t1 then ds-lite ds1 set services service-set dslite-svc-set1 syslog host local services any set services service-set dslite-svc-set1 softwire-rules dslite-rule set services service-set dslite-svc-set1 stateful-firewall-rules sfw-r1 set services service-set dslite-svc-set1 nat-rules dslite-nat-rule1 set services service-set dslite-svc-set1 next-hop-service inside-service-interface sp-0/1/0.1 set services service-set dslite-svc-set1 next-hop-service outside-service-interface sp-0/1/0.2 set services service-set dslite-svc-set2 syslog host local services any set services service-set dslite-svc-set2 softwire-rules dslite-rule set services service-set dslite-svc-set2 stateful-firewall-rules sfw-r1 set services service-set dslite-svc-set2 nat-rules dslite-nat-rule2 set services service-set dslite-svc-set2 next-hop-service inside-service-interface sp-1/3/0.1 set services service-set dslite-svc-set2 next-hop-service outside-service-interface sp-1/3/0.2 set services stateful-firewall rule sfw-r1 match-direction input set services stateful-firewall rule sfw-r1 term t1 from applications junos-http set services stateful-firewall rule sfw-r1 term t1 from applications junos-ftp set services stateful-firewall rule sfw-r1 term t1 from applications junos-rtsp set services stateful-firewall rule sfw-r1 term t1 from applications junos-icmp-all set services stateful-firewall rule sfw-r1 term t1 then accept set services stateful-firewall rule sfw-r1 term t1 then syslog set interfaces ge-0/0/2 unit 0 family inet set interfaces ge-0/0/2 unit 0 family inet6 address 2001::1/16 set interfaces ge-0/0/3 unit 0 family inet address 200.200.200.1/24 set interfaces sp-0/1/0 services-options syslog host local services any set interfaces sp-0/1/0 unit 0 family inet set interfaces sp-0/1/0 unit 0 family inet6 set interfaces sp-0/1/0 unit 1 family inet6 set interfaces sp-0/1/0 unit 1 service-domain inside set interfaces sp-0/1/0 unit 2 family inet6 set interfaces sp-0/1/0 unit 2 service-domain outside set interfaces sp-1/3/0 services-options syslog host local services any set interfaces sp-1/3/0 unit 0 family inet set interfaces sp-1/3/0 unit 0 family inet6 set interfaces sp-1/3/0 unit 1 family inet6 set interfaces sp-1/3/0 unit 1 service-domain inside set interfaces sp-1/3/0 unit 2 family inet6 set interfaces sp-1/3/0 unit 2 service-domain outside set routing-options forwarding-table export load-balancing-policy set policy-options policy-statement load-balancing-policy then load-balance per-packet set routing-options rib inet6.0 static route 1001::1/128 next-hop sp-1/3/0.1 set routing-options rib inet6.0 static route 1001::1/128 next-hop sp-0/1/0.1 set forwarding-options hash-key family inet6 layer-3 destination-address set forwarding-options hash-key family inet6 layer-3 source-address
配置 AFTR
分步过程
以下示例要求您在配置层次结构中导航各个级别。有关导航 CLI 的信息,请参阅 Junos OS CLI 用户指南。
配置第 3 层服务包。 此示例假定 PIC 位于 FPC 1 插槽 1 中。
[edit chassis] user@AFTR1# set fpc 1 pic 1 adaptive-services service-package layer-3
服务包及其关联
sp-接口用于在流量传递到其目标之前对其进行操作。有关配置服务包的详细信息,请参阅 Junos OS 服务接口配置指南。为两个服务 PIC 配置两个不同的 NAT 池和 NAPT。
[edit services nat] user@AFTR1# set pool dslite-pool1 address-range low 33.33.33.1 high 33.33.33.32 user@AFTR1# set pool dslite-pool1 port automatic user@AFTR1# set pool dslite-pool2 address-range low 44.44.44.1 high 44.44.44.32 user@AFTR1# set pool dslite-pool2 port automatic user@AFTR1# set rule dslite-nat-rule1 match-direction input user@AFTR1# set rule dslite-nat-rule1 term t1 from source-address 20.20.0.0/16 user@AFTR1# set rule dslite-nat-rule1 term t1 then translated source-pool dslite-pool1 user@AFTR1# set rule dslite-nat-rule1 term t1 then translated translation-type napt-44 user@AFTR1# set rule dslite-nat-rule2 match-direction input user@AFTR1# set rule dslite-nat-rule2 term t1 from source-address 20.20.0.0/16 user@AFTR1# set rule dslite-nat-rule2 term t1 then translated source-pool dslite-pool2 user@AFTR1# set rule dslite-nat-rule2 term t1 then translated translation-type napt-44
配置软线集中器并创建软线规则。
[edit services softwire] user@AFTR1# set softwire-concentrator ds-lite ds1 softwire-address 1001::1 user@AFTR1# set softwire-concentrator ds-lite ds1 mtu-v6 9192 user@AFTR1# set rule dslite-rule match-direction input user@AFTR1# set rule dslite-rule term t1 then ds-lite ds1
分别为服务 PIC 和 配置下一跃点样式的服务集
dslite-svc-set1dslite-svc-set2和sp-1/3/0。sp-0/1/0[edit services] user@AFTR1# set service-set dslite-svc-set1 syslog host local services any user@AFTR1# set service-set dslite-svc-set1 softwire-rules dslite-rule user@AFTR1# set service-set dslite-svc-set1 stateful-firewall-rules sfw-r1 user@AFTR1# set service-set dslite-svc-set1 nat-rules dslite-nat-rule1 user@AFTR1# set service-set dslite-svc-set1 next-hop-service inside-service-interface sp-0/1/0.1 user@AFTR1# set service-set dslite-svc-set1 next-hop-service outside-service-interface sp-0/1/0.2 user@AFTR1# set service-set dslite-svc-set2 syslog host local services any user@AFTR1# set service-set dslite-svc-set2 softwire-rules dslite-rule user@AFTR1# set service-set dslite-svc-set2 stateful-firewall-rules sfw-r1 user@AFTR1# set service-set dslite-svc-set2 nat-rules dslite-nat-rule2 user@AFTR1# set service-set dslite-svc-set2 next-hop-service inside-service-interface sp-1/3/0.1 user@AFTR1# set service-set dslite-svc-set2 next-hop-service outside-service-interface sp-1/3/0.2
配置状态防火墙和软线规则。
[edit services] user@AFTR1# set stateful-firewall rule sfw-r1 match-direction input user@AFTR1# set stateful-firewall rule sfw-r1 term t1 from applications junos-http user@AFTR1# set stateful-firewall rule sfw-r1 term t1 from applications junos-ftp user@AFTR1# set stateful-firewall rule sfw-r1 term t1 from applications junos-rtsp user@AFTR1# set stateful-firewall rule sfw-r1 term t1 from applications junos-icmp-all user@AFTR1# set stateful-firewall rule sfw-r1 term t1 then accept user@AFTR1# set stateful-firewall rule sfw-r1 term t1 then syslog
配置服务接口。
[edit interfaces] user@AFTR1# set sp-0/1/0 services-options syslog host local services any user@AFTR1# set sp-0/1/0 unit 0 family inet user@AFTR1# set sp-0/1/0 unit 0 family inet6 user@AFTR1# set sp-0/1/0 unit 1 family inet6 user@AFTR1# set sp-0/1/0 unit 1 service-domain inside user@AFTR1# set sp-0/1/0 unit 2 family inet6 user@AFTR1# set sp-0/1/0 unit 2 service-domain outside user@AFTR1# set sp-1/3/0 services-options syslog host local services any user@AFTR1# set sp-1/3/0 unit 0 family inet user@AFTR1# set sp-1/3/0 unit 0 family inet6 user@AFTR1# set sp-1/3/0 unit 1 family inet6 user@AFTR1# set sp-1/3/0 unit 1 service-domain inside user@AFTR1# set sp-1/3/0 unit 2 family inet6 user@AFTR1# set sp-1/3/0 unit 2 service-domain outside
配置运行 B4 的家用路由器与 AFTR 之间的接口。
[edit interfaces] user@AFTR1# set ge-0/0/2 unit 0 family inet user@AFTR1# set ge-0/0/2 unit 0 family inet6 address 2001::1/16
配置 AFTR 和互联网之间的接口。
[edit interfaces] user@AFTR1# set ge-0/0/3 unit 0 family inet address 200.200.200.1/24
配置数据包转发引擎的负载平衡选项,以确定如何在两个服务 PIC 之间对流量进行负载平衡。
[edit] user@AFTR1# set policy-options policy-statement load-balancing-policy then load-balance per-packet user@AFTR1# set routing-options forwarding-table export load-balancing-policy
配置路由选项,以安装到两个服务 PIC 的任播地址的高优先级路由。
配置静态路由目标地址。
配置到目标地址的下一跃点。在下一跃点列表中包括服务 PIC(
sp-1/3/0.1sp-0/1/0.1)。
[edit routing-options]user@AFTR1# set rib inet6.0 static route 1001::1/128 next-hop sp-1/3/0.1 user@AFTR1# set rib inet6.0 static route 1001::1/128 next-hop sp-0/1/0.1配置数据包转发引擎的负载平衡选项。
[edit forwarding-options] user@AFTR1# set hash-key family inet6 layer-3 destination-address user@AFTR1# set hash-key family inet6 layer-3 source-address
结果
在配置模式下,通过输入 show chassis、 、 、 show routing-optionsshow policy-optionsshow servicesshow interfaces和show forwarding-options命令来确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置。
user@AFTR1# show chassis
fpc 1 {
pic 1 {
adaptive-services {
service-package layer-3;
}
}
}
user@AFTR1# show services
service-set dslite-svc-set1 {
syslog {
host local {
services any;
}
}
softwire-rules dslite-rule;
stateful-firewall-rules sfw-r1;
nat-rules dslite-nat-rule1;
next-hop-service {
inside-service-interface sp-0/1/0.1;
outside-service-interface sp-0/1/0.2;
}
}
service-set dslite-svc-set2 {
syslog {
host local {
services any;
}
}
softwire-rules dslite-rule;
stateful-firewall-rules sfw-r1;
nat-rules dslite-nat-rule2;
next-hop-service {
inside-service-interface sp-1/3/0.1;
outside-service-interface sp-1/3/0.2;
}
}
stateful-firewall {
rule sfw-r1 {
match-direction input;
term t1 {
from {
applications [ junos-http junos-ftp junos-rtsp junos-icmp-all ];
}
then {
accept;
syslog;
}
}
}
}
softwire {
softwire-concentrator {
ds-lite ds1 {
softwire-address 1001::1;
mtu-v6 9192;
}
}
rule dslite-rule {
match-direction input;
term t1 {
then {
ds-lite ds1;
}
}
}
}
nat {
pool dslite-pool1 {
address-range low 33.33.33.1 high 33.33.33.32;
port {
automatic;
}
}
pool dslite-pool2 {
address-range low 44.44.44.1 high 44.44.44.32;
port {
automatic;
}
}
rule dslite-nat-rule1 {
match-direction input;
term t1 {
from {
source-address {
20.20.0.0/16;
}
}
then {
translated {
source-pool dslite-pool1;
translation-type {
napt-44;
}
}
}
}
}
rule dslite-nat-rule2 {
match-direction input;
term t1 {
from {
source-address {
20.20.0.0/16;
}
}
then {
translated {
source-pool dslite-pool2;
translation-type {
napt-44;
}
}
}
}
}
}
user@AFTR1# show interfaces
ge-0/0/2 {
unit 0 {
family inet;
family inet6 {
address 2001::1/16;
}
}
}
ge-0/0/3 {
unit 0 {
family inet {
address 200.200.200.1/24;
}
}
}
sp-0/1/0 {
services-options {
syslog {
host local {
services any;
}
}
}
unit 0 {
family inet;
family inet6;
}
unit 1 {
family inet6;
service-domain inside;
}
unit 2 {
family inet6;
service-domain outside;
}
}
sp-1/3/0 {
services-options {
syslog {
host local {
services any;
}
}
}
unit 0 {
family inet;
family inet6;
}
unit 1 {
family inet6;
service-domain inside;
}
unit 2 {
family inet6;
service-domain outside;
}
}
user@AFTR1# show routing-options
rib inet6.0 {
static {
route 1001::1/128 next-hop [ sp-1/3/0.1 sp-0/1/0.1 ];
}
}
forwarding-table {
export load-balancing-policy;
}
user@AFTR1# show policy-options
policy-statement load-balancing-policy {
then {
load-balance per-packet;
}
}
user@AFTR1# show forwarding-options
hash-key {
family inet6 {
layer-3 {
destination-address;
source-address;
}
}
}
如果完成设备配置,请从配置模式输入 commit 。
验证
确认配置工作正常。
验证两个服务 PIC 之间的负载平衡
目的
验证流量是否在两个服务 PIC 之间进行了负载平衡。
行动
使用
show services stateful-firewall flows命令验证本地网络上的 IPv4 主机与互联网上的 IPv4 节点之间的流量。user@AFTR> show services stateful-firewall flows Interface: sp-0/1/0, Service set: dslite-svc-set1 Flow State Dir Frm count ICMP 10.0.10.1 -> 45.45.45.2 Watch I 3 NAT source 10.0.10.1 -> 129.0.0.1 Softwire 5002::12 -> 1001::1 DS-LITE 5002::12 -> 1001::1 Forward I 6 ICMP 45.45.45.2 -> 129.0.0.1 Watch O 3 NAT dest 129.0.0.1 -> 10.0.10.1 Softwire 5002::12 -> 1001::1输出显示 ICMP 统计信息,指示本地网络上的 IPv4 主机与互联网上的 IPv4 节点之间的流量。
show services softwire发出 、 、show services stateful-firewall conversationsshow services stateful-firewall flows count和show services stateful-firewall statistics命令以检查流量。user@AFTR> show services softwire Interface: sp-0/1/0, Service set: dslite-svc-set2 Softwire Direction Flow count 2001::3 -> 1001::1 I 3 Interface: sp-1/3/0, Service set: dslite-svc-set1 Softwire Direction Flow count 2001::2 -> 1001::1 I 3
输出显示与服务接口关联的服务集和与服务接口
sp-0/1/0sp-1/3/0关联的服务集dslite-svc-set1dslite-svc-set2的统计信息。user@AFTR> show services stateful-firewall conversations Interface: sp-0/1/0, Service set: dslite-svc-set2 Conversation: ALG protocol: tcp Number of initiators: 1, Number of responders: 1 Flow State Dir Frm count TCP 20.20.1.2:1025 -> 200.200.200.2:80 Forward I 189280 NAT source 20.20.1.2:1025 -> 44.44.44.1:1024 Softwire 2001::3 -> 1001::1 TCP 200.200.200.2:80 -> 44.44.44.1:1024 Forward O 363675 NAT dest 44.44.44.1:1024 -> 20.20.1.2:1025 Softwire 2001::3 -> 1001::1 Interface: sp-1/3/0, Service set: dslite-svc-set1 Conversation: ALG protocol: tcp Number of initiators: 1, Number of responders: 1 Flow State Dir Frm count TCP 20.20.1.2:1025 -> 200.200.200.2:80 Forward I 195847 NAT source 20.20.1.2:1025 -> 33.33.33.1:1025 Softwire 2001::2 -> 1001::1 TCP 200.200.200.2:80 -> 33.33.33.1:1025 Forward O 391972 NAT dest 33.33.33.1:1025 -> 20.20.1.2:1025 Softwire 2001::2 -> 1001::1 Conversation: ALG protocol: tcp Number of initiators: 1, Number of responders: 1 Flow State Dir Frm count TCP 20.20.1.2:1025 -> 200.200.200.2:80 Forward I 219333 NAT source 20.20.1.2:1025 -> 33.33.33.1:1024 Softwire 2001::4 -> 1001::1 TCP 200.200.200.2:80 -> 33.33.33.1:1024 Forward O 438848 NAT dest 33.33.33.1:1024 -> 20.20.1.2:1025 Softwire 2001::4 -> 1001::1输出显示两个服务接口的流量,以及
sp-1/3/0,sp-0/1/0指示两个服务 PIC 都处于活动状态。user@AFTR> show services stateful-firewall flows count Interface Service set Flow count sp-0/1/0 dslite-svc-set2 3 sp-1/3/0 dslite-svc-set1 6
输出显示两个服务接口的流计数,以及
sp-1/3/0,sp-0/1/0指示两个服务 PIC 都处于活动状态。user@AFTR> show services stateful-firewall statistics Interface Service set Accept Discard Reject Errors sp-0/1/0 dslite-svc-set2 118991296 0 0 0 sp-1/3/0 dslite-svc-set1 237615050 0 0 0
意义
输出显示服务 PIC sp-0/1/0 和 sp-1/3/0的流量。这表示流量在两个服务 PIC 之间进行了负载平衡。
验证两个服务 PIC 之间的冗余
目的
验证两个服务 PIC 之间的冗余。
行动
通过发出
request chassis pic fpc-slot slot-number pic-slot pic-number offline命令使服务 PICsp-0/1/0脱机。user@host> request chassis pic fpc-slot 0 pic-slot 1 offline fpc 0 pic 1 offline initiated, use “show chassis fpc pic-status” to verify
再次发出命令以
show services stateful-firewall conversations检查通过冗余服务 PICsp-1/3/0的流量。检查输出中的接口名称和服务集名称。
user@host> show services stateful-firewall conversations Interface: sp-1/3/0, Service set: dslite-svc-set1 Conversation: ALG protocol: tcp Number of initiators: 1, Number of responders: 1 Flow State Dir Frm count TCP 20.20.1.2:1025 -> 200.200.200.2:80 Forward I 195847 NAT source 20.20.1.2:1025 -> 33.33.33.1:1025 Softwire 2001::2 -> 1001::1 TCP 200.200.200.2:80 -> 33.33.33.1:1025 Forward O 391972 NAT dest 33.33.33.1:1025 -> 20.20.1.2:1025 Softwire 2001::2 -> 1001::1 Conversation: ALG protocol: tcp Number of initiators: 1, Number of responders: 1 Flow State Dir Frm count TCP 20.20.1.2:1025 -> 200.200.200.2:80 Forward I 219333 NAT source 20.20.1.2:1025 -> 33.33.33.1:1024 Softwire 2001::4 -> 1001::1 TCP 200.200.200.2:80 -> 33.33.33.1:1024 Forward O 438848 NAT dest 33.33.33.1:1024 -> 20.20.1.2:1025 Softwire 2001::4 -> 1001::1
意义
输出指示,停用后sp-0/1/0,所有流量现在都通过服务 PIC sp-1/3/0 进行路由。这表示两个服务 PIC 之间的冗余正在运行。
