使用外部门户进行访客访问
如果您希望来宾转到 Web 开发人员在您自己的网站上设计的登录门户,请启用外部门户。
外部门户是您的 WLAN 用户在选择您的 SSID 后看到的网页。例如,您可以将来宾发送到公司的主页或 Web 开发人员专门为组织设置的登录门户。
为了提高安全性,您可以指定授权用户、允许的子网和允许的主机名。您还可以输入要阻止的主机名列表。
- 导航至 WLAN。
注意:
-
如果 WLAN 在 WLAN 模板中,请选择“ 无线>组织 |WLAN 模板,单击该模板,然后单击该 WLAN。
-
对于站点级 WLAN,请选择 站点>无线 |WLAN,然后单击该 WLAN。
-
- 在“编辑 WLAN”窗口中的“访客门户”下,单击“转发到外部门户”。
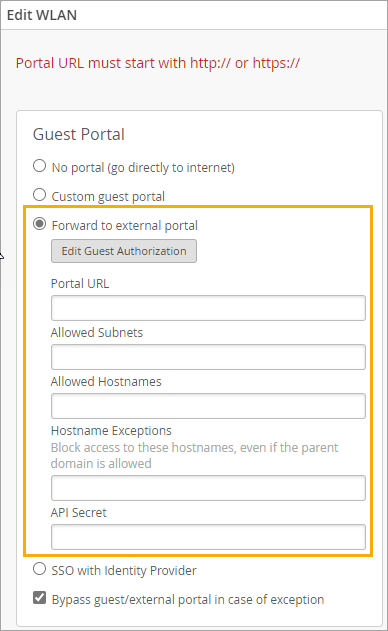
- (可选)如果要将访问权限限制为特定用户,请单击“编辑访客授权”按钮。然后完成以下步骤:
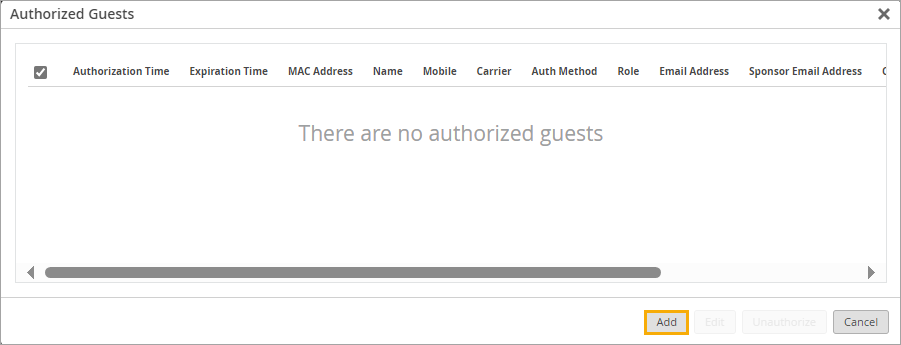
- 在“授权来宾”窗口中,单击“添加”。
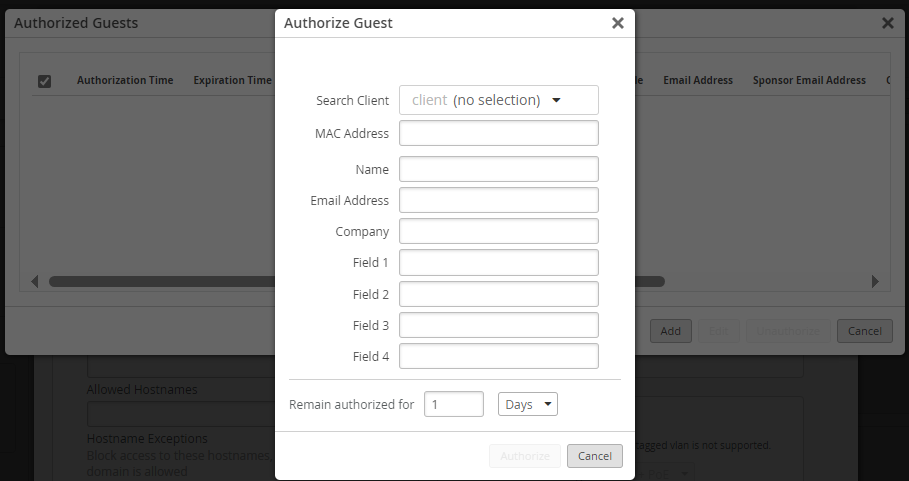
- 在“授权访客”窗口中,输入访客的 MAC 地址(必需)、可选用户信息以及用户保持授权的期限。
 注意:
注意:您可以使用 “搜索客户端” 选项搜索已连接到 WLAN 的客户端。
- 单击“授权来宾”窗口底部的“授权”。
- 重复这些步骤以将更多来宾添加到列表中。
- 在“授权来宾”窗口中,单击“添加”。
- 输入门户 URL,以 http:// 或 https:// 开头。
注意:
使用其他字段对访问权限进行微调。例如,仅允许某些子网或主机名。
- 选中或清除“在出现异常时绕过客户机/外部门户”复选框。
选择此功能后,每个接入点都会尝试访问门户或 IdP,但如果无法访问,则 AP 将自动授权访客连接到 WLAN。
- 单击编辑 WLAN 窗口底部的保存。
使用 PHP 和自述文件创建外部门户
- 参考以下示例 PHP 文件和自述文件信息创建外部门户。
<?php /* These parameters are sent by Mist on the 302 redirect to this portal page: wlan_id - WLAN object's UUID ap_mac - MAC address of the AP client_mac - MAC address of the client device url - Originally requested url by the client, ie: http://www.mist.com ap_name - Name of the AP site_name - Name of the Site If you want to send the guest to a content page after authorization, configure the $url instead of using the valued that is passed as a parameter. */ $wlan_id = $_GET['wlan_id']; $ap_mac = $_GET['ap_mac']; $client_mac = $_GET['client_mac']; $url = $_GET['url']; $ap_name = $_GET['ap_name']; $site_name = $_GET['site_name']; ?> <html> <body> <form action="authme.php" method="post"> <input type="hidden" name="wlan_id" value="<?php echo($wlan_id) ?>" /> <input type="hidden" name="ap_mac" value="<?php echo($ap_mac) ?>" /> <input type="hidden" name="client_mac" value="<?php echo($client_mac) ?>" /> <input type="hidden" name="url" value="<?php echo($url) ?>" /> <input type="hidden" name="ap_name" value="<?php echo($ap_name) ?>" /> <input type="hidden" name="site_name" value="<?php echo($site_name) ?>" /> <table> <tr> <td><b>Your Full Name</b></td> <td><input type="text" name="name" /></td> </tr> <tr> <td><b>Your Email Address</b></td> <td><input type="text" name="email" /></td> </tr> <tr> <td><input type="submit" value="Login" /></td> </tr> </table> </form> </body> </html>
<?php $secret = ''; // WLAN API Key, obtained from the Mist Web GUI after creating the WLAN $wlan_id = $_POST['wlan_id']; $ap_mac = $_POST['ap_mac']; $client_mac = $_POST['client_mac']; $url = $_POST['url']; $ap_name = $_POST['ap_name']; $site_name = $_POST['site_name']; $authorize_min = 525600; // Duration (in minutes) the guest MAC address is authorized before they are redirected back to the portal page) $context = sprintf('%s/%s/%s/%d/%d/%d/%d', $wlan_id, $ap_mac, $client_mac, $authorize_min, ); $token = urlencode(base64_encode($context)); // The below portal fields are passed back to Mist and shown in the Guest Portal Information $name = $_POST['name']; $email = $_POST['email']; $field1 = 'Whatever you want Custom field 1 to be'; $field2 = 'Whatever you want Custom field 2 to be'; $field3 = 'Whatever you want Custom field 3 to be'; $field4 = 'Whatever you want Custom field 4 to be'; $forward = urlencode($url); // URL the user is forwarded to after authorization $extra = '&forward=' . $forward; $extra .= '&name=' . urlencode("$name"); $extra .= '&field1=' . urlencode("$field1"); $extra .= '&field2=' . urlencode("$field2"); $extra .= '&field3=' . urlencode("$field3"); $extra .= '&field4=' . urlencode("$field4"); $extra .= '&email=' . urlencode("$email"); $expires = time() + 120; // The time until which the authorization URL is valid $payload = sprintf('expires=%d&token=%s%s', $expires, $token, $extra); $signature = urlencode(base64_encode(hash_hmac('sha1', $payload, $secret, true))); $final_url = sprintf('http://portal.mist.com/authorize?signature=%s&%s', $signature, $payload); /* Debug code used for testing purposes only If set to true, display the variable details without authorizing the guest in the Mist cloud */ $debugging = false; if ($debugging) { header('Content-Type: text/plain'); echo sprintf('token : urlencode(base64(%s))', $context) . PHP_EOL; echo sprintf(' %s', $token) . PHP_EOL; echo sprintf('foward : %s', $url) . PHP_EOL; echo sprintf(' %s', $foward) . PHP_EOL; echo sprintf('payload-to-sign: %s', $payload) . PHP_EOL; echo sprintf('signature : %s', $signature) . PHP_EOL; echo sprintf('URL : %s', $final_url) . PHP_EOL; echo sprintf('client_mac : %s', $client_mac) . PHP_EOL; echo sprintf('ap_mac : %s', $ap_mac) . PHP_EOL; echo sprintf('ap_name : %s', $ap_name) . PHP_EOL; echo sprintf('wlan_id : %s', $wlan_id) . PHP_EOL; echo sprintf('site_name : %s', $site_name) . PHP_EOL; echo sprintf('name : %s', $name) . PHP_EOL; echo sprintf('email : %s', $email) . PHP_EOL; echo sprintf('field1 : %s', $field1) . PHP_EOL; echo sprintf('field2 : %s', $field2) . PHP_EOL; echo sprintf('field3 : %s', $field3) . PHP_EOL; echo sprintf('field4 : %s', $field4) . PHP_EOL; } else { // Guest is redirected to the Mist portal for authorization. If successful, the Mist portal will then redirect the guest to the $url header('Location: ' . $final_url); } ?>自述信息This sample code shows how to use the PHP POST method to pass the below parameter values from the landing page (index.php) to the authorization page (authme.php). The authorization page will also request the user to provide some information. Authorization HOW-TOs ===================== Syntax: signature=<signature>&expires=<epoch-seconds>&token=<token>&forward=<forward> Note: Wired captive portal does not support this mechanism, please use the JWT based one. <forward>: url to forward the user to after authorization <token>: base64("wlan-id/ap-mac/client-mac/authorize_min/0/0/0") <signature>: base64(hmac_sha1(<secret>, "expires=...")) Example token : urlencode(base64("be22bba7-8e22-e1cf-5185-b880816fe2cf/5c5b35001234/d58f6bb4c9d8/480/0/0/0")) = YmUyMmJiYTctOGUyMi1lMWNmLTUxODUtYjg4MDgxNmZlMmNmLzVjNWIzNTAwMTIzNC9kNThmNmJiNGM5ZDgvNDgwLzAvMC8w expires : 1768587994 forward : urlencode("http://www.mist.com") http%3A%2F%2Fwww.mist.com%2F payload-to-sign: expires=1768587994&token=YmUyMmJiYTctOGUyMi1lMWNmLTUxODUtYjg4MDgxNmZlMmNmLzVjNWIzNTAwMTIzNC9kNThmNmJiNGM5ZDgvNDgwLzAvMC8w&forward=http%3A%2F%2Fwww.mist.com%2F secret : test-secret (only used by /authorize-test for testing purpose) signature : J7VJlf2Zlcs%2BOxhVxCf8hL0XYC0%3D final URL : http://portal.mist.com/authorize-test?signature=J7VJlf2Zlcs%2BOxhVxCf8hL0XYC0%3D&expires=1768587994&token=YmUyMmJiYTctOGUyMi1lMWNmLTUxODUtYjg4MDgxNmZlMmNmLzVjNWIzNTAwMTIzNC9kNThmNmJiNGM5ZDgvNDgwLzAvMC8w&forward=http%3A%2F%2Fwww.mist.com%2F Alternatively, you can use JWT tokens: Syntax: jwt=<jwt token> Payload: { "ap_mac": "5c5b35001234", "wlan_id": "be22bba7-8e22-e1cf-5185-b880816fe2cf", "client_mac": "d58f6bb4c9d8", "minutes": 480, "expires": 1768587994, "forward": "http://www.mist.com", "authorize_only": false } Notes: authorize_only: if true and authorization is successful, 200 OK will be returned instead of 302 Redirect the user to the `forward` URL Example ``` import jwt secret = "test-secret" payload = { "ap_mac": "5c5b35001234", "wlan_id": "be22bba7-8e22-e1cf-5185-b880816fe2cf", # only for _wireless_ captive portal "site_id": "ce22bba7-8e22-e1cf-5185-b880816fe2ce", # only for _wired_ captive portal" "port_name": "eth0", # only for _wired_ captive portal" "client_mac": "d58f6bb4c9d8", "minutes": 480, "expires": 1768587994, "forward": "http://www.mist.com", "authorize_only": False } encoded_jwt = jwt.encode(payload, secret, algorithm='HS256') ``` encoded_jwt: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdXRob3JpemVfb25seSI6ZmFsc2UsImV4cGlyZXMiOjE3Njg1ODc5OTQsImFwX21hYyI6IjVjNWIzNTAwMTIzNCIsImZvcndhcmQiOiJodHRwOi8vd3d3Lm1pc3QuY29tIiwiY2xpZW50X21hYyI6ImQ1OGY2YmI0YzlkOCIsIm1pbnV0ZXMiOjQ4MCwid2xhbl9pZCI6ImJlMjJiYmE3LThlMjItZTFjZi01MTg1LWI4ODA4MTZmZTJjZiJ9.msBloHe05XzbzaMEqjsi8XSNWa_3uc--4wucKz3dQGk final URL : http://portal.mist.com/authorize-test?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdXRob3JpemVfb25seSI6ZmFsc2UsImV4cGlyZXMiOjE3Njg1ODc5OTQsImFwX21hYyI6IjVjNWIzNTAwMTIzNCIsImZvcndhcmQiOiJodHRwOi8vd3d3Lm1pc3QuY29tIiwiY2xpZW50X21hYyI6ImQ1OGY2YmI0YzlkOCIsIm1pbnV0ZXMiOjQ4MCwid2xhbl9pZCI6ImJlMjJiYmE3LThlMjItZTFjZi01MTg1LWI4ODA4MTZmZTJjZiJ9.msBloHe05XzbzaMEqjsi8XSNWa_3uc--4wucKz3dQGk注意:portal.mist.com根据创建Mist组织的云实例替换为相应的访客 Wi-Fi 门户 URL。要查找您所在地区的访客 Wi-Fi 门户 URL,请参阅《Juniper Mist管理指南》中的Mist 云 IP 地址和端口信息。 - 要获取auth.php中所需的
$secret值,请重新打开“编辑 WLAN”窗口,然后复制 API 机密。 - 配置授权页 (authme.php) 以使用所需的查询字符串参数调用Juniper Mist后端:
?signature=signature&expires=expires&token=token&optional-
expires – 授权 URL 有效期至的纪元时间戳。
-
例如:1768587994(这意味着授权 URL 将于 UTC 时间 2026 年 1 月 16 日下午 6:26:34 过期。
-
-
token – 格式为:wlan_id/ap_mac/client_mac/authorize_min/0/0/0 的 base64 字符串
-
例如:be22bba7-8e22-e1cf-5185-b880816fe2cf/5c5b35001234/d58f6bb4c9d8/480/0/0/0
-
-
signature – 一个 base64 哈希值字符串,使用 sha1 作为哈希算法,将访客 WLAN 的 API Secret 作为密钥。这将采用以下格式:expires=expires&token=token&optional
-
例如:J7VJlf2Zlcs%2BOxhVxCf8hL0XYC0%3D
-
-
optional – 可选的来宾详细信息和授权后用户转发到的 URL,格式如下:forward=url&name=name&email=email&company&field1=field1=field1&field2=field2&field3=field3&field4=field4
注意:确保所有参数值都作为 base64 传递。
-
例如:forward=http%3A%2F%2Fwww.mist.com%2F
-
-
- 将授权页面配置为调用Juniper Mist进行访客授权。最终授权 URL 如下所示:
http://portal.mist.com/authorize?signature=J7VJlf2Zlcs%2BOxhVxCf8hL0XYC0%3D&expires=1768587994&token=YmUyMmJiYTctOGUyMi1lMWNmLTUxODUtYjg4MDgxNmZlMmNmLzVjNWIzNTAwMTIzNC9kNThmNmJiNGM5ZDgvNDgwLzAvMC8w&forward=http%3A%2F%2Fwww.mist.com%2F - 通过连接设备并尝试进行身份验证来测试外部强制门户。
应将设备重定向到 Juniper Mist 门户进行授权。如果身份验证成功,用户将被重定向到外部强制强制门户代码中定义的 URL。
注意:用于
/authorize实时门户。出于测试目的,可以使用/authorize-test,这需要自述文件信息中提供的虚拟示例值。
