附录:测试用例示例信息
虚拟测试实验室
JVDE 本附录中的示例在由 vJunos 交换机、vMX 路由器和 vSRX V3.0 防火墙组成的虚拟测试实验室中进行评估。我们没有创建一对虚拟服务块交换机,但确保两种类型的 WAN 路由器(路由器或防火墙)都可以作为冗余对使用。这与用于需要使用物理硬件的测试的实验室不同。我们以此为例,您可以使用 EVE-NG 等环境自行构建一些东西,以构建自己的实验室来测试配置示例。在本例中,交换矩阵配置为 IP Clos。
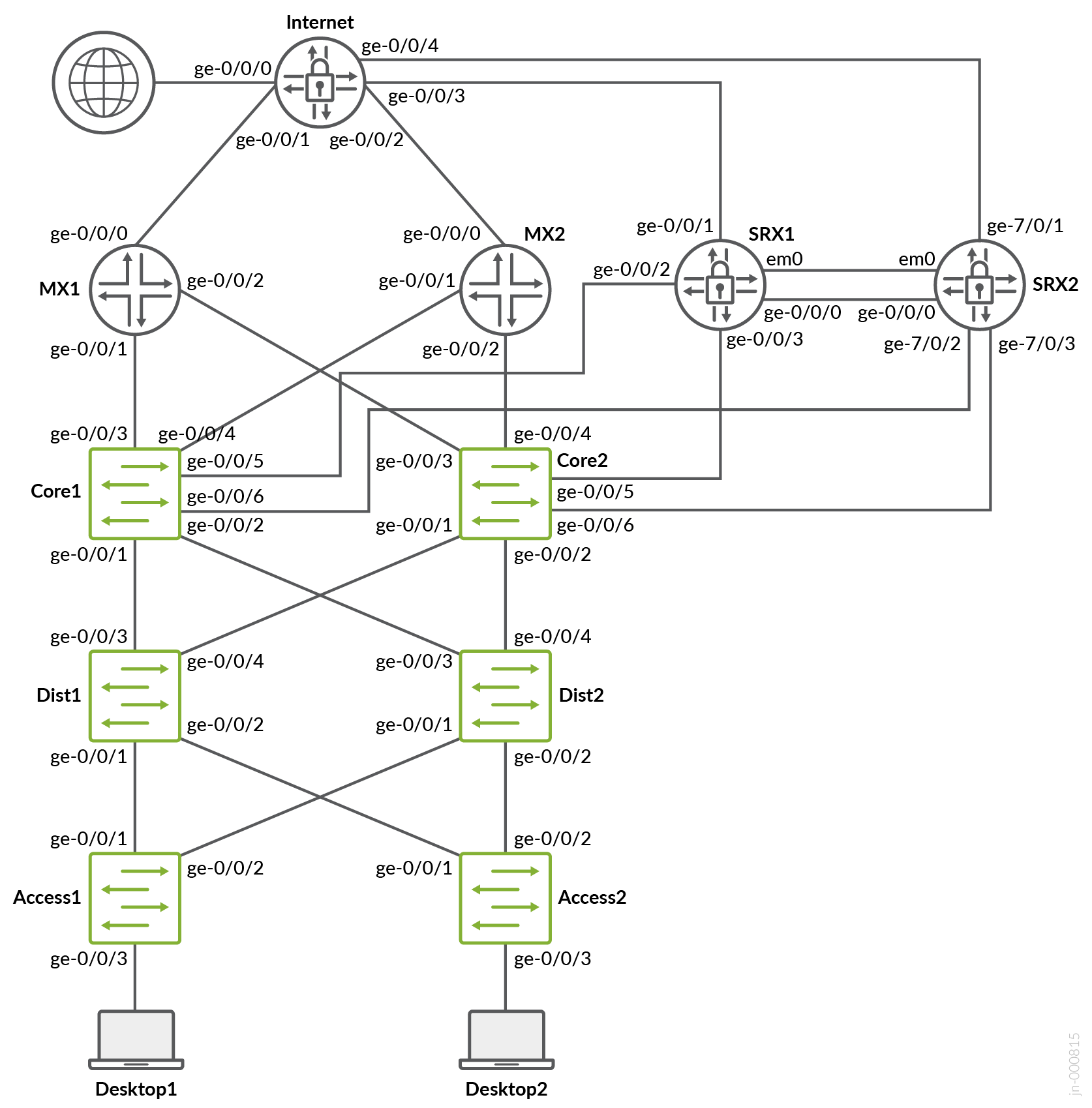
带延伸 VLAN 的 L2 出口
使用园区交换矩阵创建任何 VLAN 或 VRF 时,请记住以下最佳实践:
- 不要在生产环境中使用此方法 必须改用传输 VLAN 方法。
- 在交换机模板中创建所有 VLAN,然后在园区交换矩阵对话框中导入它们。在 Mist GUI 中的任何其他位置创建 VLAN 最终会导致不一致,从而难以解决问题。
- 如果需要,交换矩阵会创建任何所需的 VRF。请勿在 Mist GUI 中的其他位置手动创建 VRF。
- 我们建议您在交换机模板中创建端口配置文件,以便在交换矩阵中的所有交换机上同步任何更改。
以下配置是此交换矩阵中使用的交换机模板的导出版本。使用此选项可在导入时检查您的设置。如您所见,每个 VRF 只有一个 VLAN,因此需要扩展方法。
{
"additional_config_cmds": [],
"networks": {
"vlan1099": {
"vlan_id": 1099,
"subnet": "10.99.99.0/24"
},
"vlan1088": {
"vlan_id": 1088,
"subnet": "10.88.88.0/24"
},
"vlan1033": {
"vlan_id": 1033,
"subnet": "10.33.33.0/24"
}
},
"port_usages": {
"vlan1099": {
"mode": "access",
"disabled": false,
"port_network": "vlan1099",
"voip_network": null,
"stp_edge": false,
"mac_auth_protocol": null,
"all_networks": false,
"networks": null,
"port_auth": null,
"enable_mac_auth": null,
"mac_auth_only": null,
"guest_network": null,
"bypass_auth_when_server_down": null,
"speed": "auto",
"duplex": "auto",
"mac_limit": 0,
"persist_mac": false,
"poe_disabled": false,
"enable_qos": false,
"storm_control": {},
"mtu": null,
"description": "",
"disable_autoneg": false
},
"vlan1088": {
"mode": "access",
"disabled": false,
"port_network": "vlan1088",
"voip_network": null,
"stp_edge": false,
"mac_auth_protocol": null,
"all_networks": false,
"networks": null,
"port_auth": null,
"enable_mac_auth": null,
"mac_auth_only": null,
"guest_network": null,
"bypass_auth_when_server_down": null,
"speed": "auto",
"duplex": "auto",
"mac_limit": 0,
"persist_mac": false,
"poe_disabled": false,
"enable_qos": false,
"storm_control": {},
"mtu": null,
"description": "",
"disable_autoneg": false
},
"dynamic": {
"mode": "dynamic",
"reset_default_when": "link_down",
"rules": []
}
},
"switch_matching": {
"enable": true,
"rules": []
},
"switch_mgmt": {
"config_revert_timer": 10,
"root_password": "<password>",
"protect_re": {
"enabled": false
},
"tacacs": {
"enabled": false
}
},
"mist_nac": {
"enabled": true,
"network": null
},
"radius_config": {
"auth_servers": [],
"acct_servers": [],
"auth_servers_timeout": 5,
"auth_servers_retries": 3,
"fast_dot1x_timers": false,
"acct_interim_interval": 0,
"auth_server_selection": "ordered",
"coa_enabled": false,
"coa_port": ""
},
"vrf_config": {
"enabled": false
},
"remote_syslog": {
"enabled": false
},
"snmp_config": {
"enabled": false
},
"dhcp_snooping": {
"enabled": false
},
"dns_servers": [],
"dns_suffix": [],
"ntp_servers": [],
"acl_policies": [],
"port_mirroring": {},
"name": "campus-fabric"
}
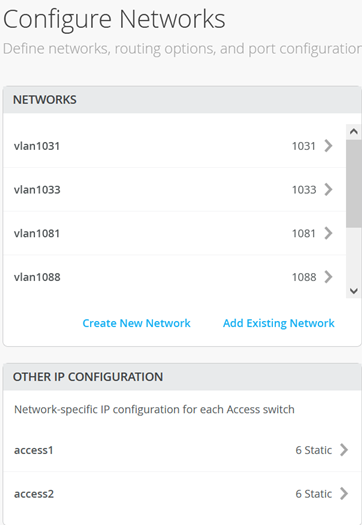
在“园区交换矩阵配置”对话框中有一个名为“配置网络”的页面。这是从交换机模板导入 VLAN 的位置。在本例中,请参阅图 1 了解结果。
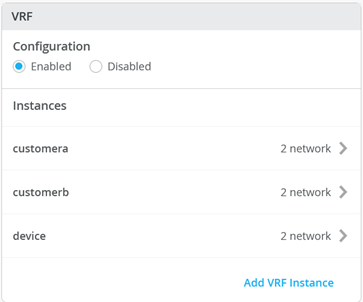
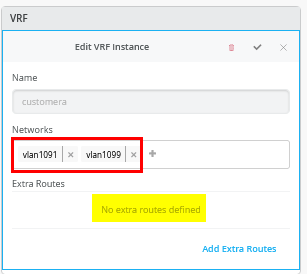
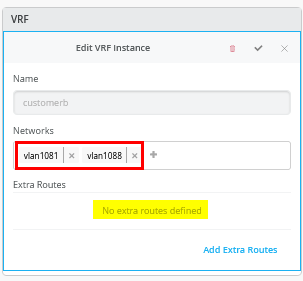
下一步是创建所有 3 个 VRF,并将其中一个网络连接到每个 VRF,如图 2 所示。
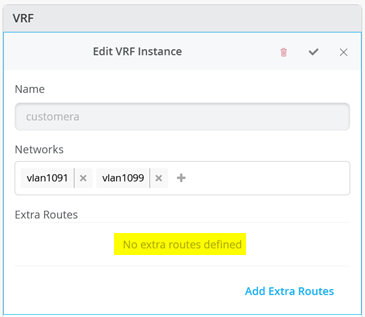
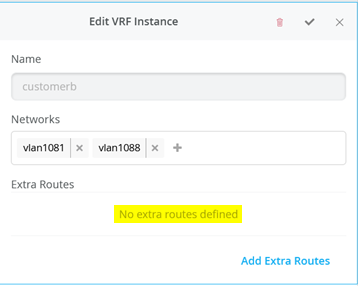
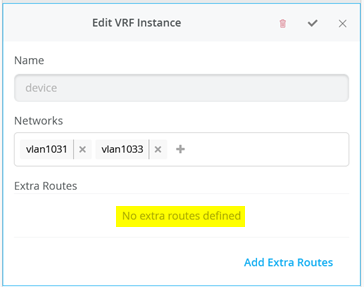
接下来,转到每个 VRF,并将手动路由添加到 WAN 路由器在每个子网中的 VIP。VRF 配置如以下三个图像所示。
继续“ 结构配置 ”对话框,直到开始构建结构。
Core1 和 Core2 交换机配置
服务块功能是虚拟的,并且位于核心交换机上,因此我们必须配置两个核心交换机。以下伪代码描述了在交换机 core1 和 core2 上要配置的内容:
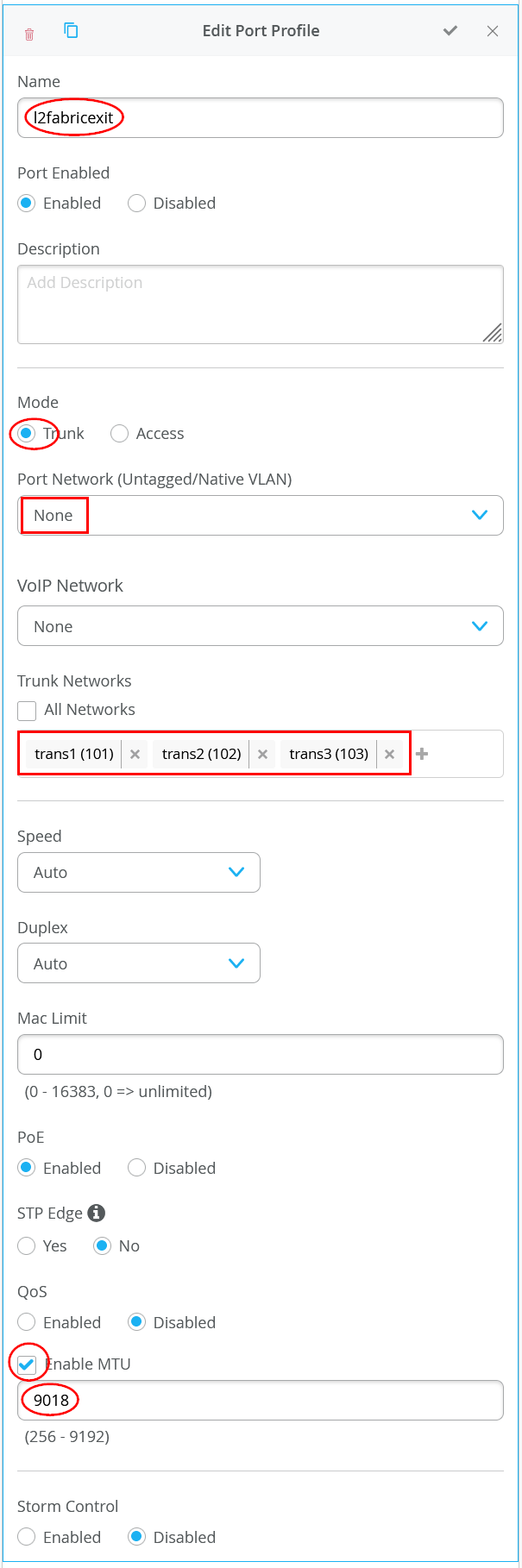
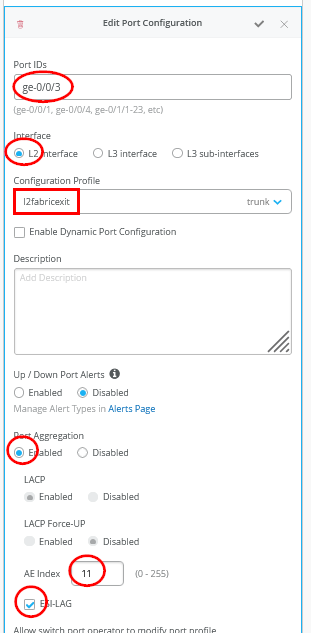
# Create a new local Port Profile called ‘l2fabricexit’ and configure: # Mode=’Trunk’ # Port Network (Untagged/Native VLAN)=’None’ # Add the following 3 Networks as Trunk Networks: # Network=vlan1099 # Network=vlan1088 # Network=vlan1033 # MTU=’9018’ # Create a new port configuration where: # Port Aggregation=Enable/Checked # AE Index=11 # ESI-LAG=Enable/Checked # Port IDs=ge-0/0/3 # Interface=L2 Interface # Configuration Profile=l2fabricexit # Create a new Port configuration where: # Port Aggregation=Enable/Checked # AE Index=12 # ESI-LAG=Enable/Checked # Port IDs=ge-0/0/4 # Interface=L2 Interface # Configuration Profile=l2fabricexit
以下三个屏幕截图显示了上述配置的主要部分。我们从端口配置文件开始。请记住,仅包括使用的延伸 VLAN。
 的上行链路
的上行链路
第二个上行链路配置非常相似。只有AE 指数 从11变为12。
必须确保每个服务块功能上的 AE 索引 彼此同步,朝向同一 WAN 路由器,并将每个索引定义为 ESI-LAG。还必须确保不会重用已在结构中的其他位置定义的 AE 索引。
作为 WAN 路由器的瞻博网络 MX
以下是接口的配置、VRRP 网关冗余和静态路由的示例。您可能需要添加默认路由和接口才能完成配置。
Set system host-name wanrouter1 set chassis aggregated-devices ethernet device-count 10 delete interfaces ae0 delete policy-options policy-statement fabric delete policy-options policy-statement internet delete routing-instances public-int set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all delete interfaces ge-0/0/1 set interfaces ge-0/0/1 gigether-options 802.3ad ae11 delete interfaces ge-0/0/2 set interfaces ge-0/0/2 gigether-options 802.3ad ae11 delete interfaces ae11 set interfaces ae11 mtu 9018 set interfaces ae11 aggregated-ether-options lacp active set interfaces ae11 aggregated-ether-options lacp admin-key 11 set interfaces ae11 unit 0 family bridge interface-mode trunk set interfaces ae11 unit 0 family bridge vlan-id-list 1099 set interfaces ae11 unit 0 family bridge vlan-id-list 1088 set interfaces ae11 unit 0 family bridge vlan-id-list 1033 set bridge-domains vlan1099 vlan-id 1099 set bridge-domains vlan1099 routing-interface irb.1099 set bridge-domains vlan1088 vlan-id 1088 set bridge-domains vlan1088 routing-interface irb.1088 set bridge-domains vlan1033 vlan-id 1033 set bridge-domains vlan1033 routing-interface irb.1033 set interfaces irb unit 1099 family inet address 10.99.99.253/24 vrrp-group 1 virtual-address 10.99.99.254 set interfaces irb unit 1099 family inet address 10.99.99.253/24 vrrp-group 1 priority 110 set interfaces irb unit 1099 family inet address 10.99.99.253/24 vrrp-group 1 accept-data set interfaces irb unit 1088 family inet address 10.88.88.253/24 vrrp-group 2 virtual-address 10.88.88.254 set interfaces irb unit 1088 family inet address 10.88.88.253/24 vrrp-group 2 priority 110 set interfaces irb unit 1088 family inet address 10.88.88.253/24 vrrp-group 2 accept-data set interfaces irb unit 1033 family inet address 10.33.33.253/24 vrrp-group 3 virtual-address 10.33.33.254 set interfaces irb unit 1033 family inet address 10.33.33.253/24 vrrp-group 3 priority 110 set interfaces irb unit 1033 family inet address 10.33.33.253/24 vrrp-group 3 accept-data set routing-options static route 172.16.193.0/24 next-hop 10.99.99.1 set routing-options static route 172.16.194.0/24 next-hop 10.88.88.1 set routing-options static route 172.16.195.0/24 next-hop 10.33.33.1
在第二个 WAN 路由器上,值得注意的配置更改通常是 AE 密钥、索引和静态 IP 地址。
Set system host-name wanrouter2 set chassis aggregated-devices ethernet device-count 10 delete interfaces ae0 delete policy-options policy-statement fabric delete policy-options policy-statement internet delete routing-instances public-int set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all delete interfaces ge-0/0/1 set interfaces ge-0/0/1 gigether-options 802.3ad ae12 delete interfaces ge-0/0/2 set interfaces ge-0/0/2 gigether-options 802.3ad ae12 delete interfaces ae12 set interfaces ae12 mtu 9018 set interfaces ae12 aggregated-ether-options lacp active set interfaces ae12 aggregated-ether-options lacp admin-key 12 set interfaces ae12 unit 0 family bridge interface-mode trunk set interfaces ae12 unit 0 family bridge vlan-id-list 1099 set interfaces ae12 unit 0 family bridge vlan-id-list 1088 set interfaces ae12 unit 0 family bridge vlan-id-list 1033 set bridge-domains vlan1099 vlan-id 1099 set bridge-domains vlan1099 routing-interface irb.1099 set bridge-domains vlan1088 vlan-id 1088 set bridge-domains vlan1088 routing-interface irb.1088 set bridge-domains vlan1033 vlan-id 1033 set bridge-domains vlan1033 routing-interface irb.1033 set interfaces irb unit 1099 family inet address 10.99.99.252/24 vrrp-group 1 virtual-address 10.99.99.254 set interfaces irb unit 1099 family inet address 10.99.99.252/24 vrrp-group 1 accept-data set interfaces irb unit 1088 family inet address 10.88.88.252/24 vrrp-group 2 virtual-address 10.88.88.254 set interfaces irb unit 1088 family inet address 10.88.88.252/24 vrrp-group 2 accept-data set interfaces irb unit 1033 family inet address 10.33.33.252/24 vrrp-group 3 virtual-address 10.33.33.254 set interfaces irb unit 1033 family inet address 10.33.33.252/24 vrrp-group 3 accept-data set routing-options static route 172.16.193.0/24 next-hop 10.99.99.1 set routing-options static route 172.16.194.0/24 next-hop 10.88.88.1 set routing-options static route 172.16.195.0/24 next-hop 10.33.33.1
您可能想知道 172.16.19x.0 范围内的那些静态路由。请记住,IP Clos 是任播交换矩阵。因此,您必须具有静态路由,以便为 DHCP 中继何时使用结构叠加网络中的 IP 地址做好准备。您可以看到图 6 中的定义:
这些叠加环路 IP 作为 /24 范围分配给交换机上的每个 VRF。您可以通过查看结构接入交换机来计算它们,如图 7 所示。您必须将它们映射回连接到 VRF 的任何其他 VLAN,以实现所需的可访问性。
使用传输 VLAN 的 L2 出口
使用园区交换矩阵创建任何 VLAN 或 VRF 时,请记住以下最佳实践:
- 在交换机模板中创建所有 VLAN,然后在 园区交换矩阵 对话框中将其导入。在 Mist GUI 中的任何其他位置创建 VLAN 最终会导致不一致,从而难以解决问题。
- 除服务块功能外,请勿在 “园区交换矩阵 ”对话框之外创建 VRF。
- 传输 VLAN 方法要求您在服务块功能上手动创建 VRF,并将传输 VLAN 和路由本地添加到 VRF。请勿在 “园区交换矩阵 ”对话框中创建 VRF 或路由。
- 我们建议您在交换机模板中创建端口配置文件,以便在结构中的所有交换机上同步任何更改。
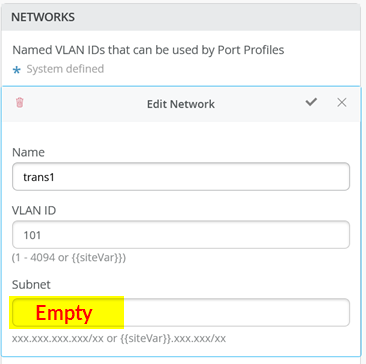
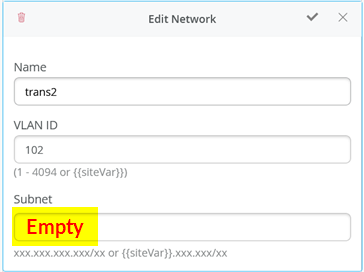
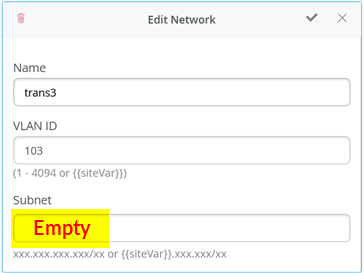
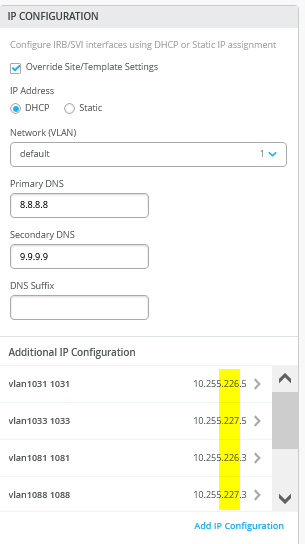
在交换机模板中定义传输 VLAN 时,请勿设置子网信息。稍后,您可以将此信息配置为每个服务块函数上的附加 IP 子网。参见图 8、 图 9 和图 10 。
 上的空子网配置
上的空子网配置
 上的空子网配置
上的空子网配置
 上的空子网配置
上的空子网配置
以下 CLI 配置显示了传输 VLAN 交换矩阵中使用的交换机模板的导出版本。这允许您在导入时查看我们的设置。如您所见,每个 VRF 至少有两个 VLAN,外加一个额外的传输 VLAN。
{
“additional_config_cmds”: [],
“networks”: {
“vlan1099”: {
“vlan_id”: 1099,
“subnet”: “10.99.99.0/24”
},
“vlan1088”: {
“vlan_id”: 1088,
“subnet”: “10.88.88.0/24”
},
“vlan1033”: {
“vlan_id”: 1033,
“subnet”: “10.33.33.0/24”
},
“vlan1091”: {
“vlan_id”: 1091,
“subnet”: “10.99.91.0/24”
},
“vlan1081”: {
“vlan_id”: 1081,
“subnet”: “10.88.81.0/24”
},
“vlan1031”: {
“vlan_id”: 1031,
“subnet”: “10.33.31.0/24”
},
“trans1”: {
“vlan_id”: “101”,
“subnet”: “”
},
“trans2”: {
“vlan_id”: “102”,
“subnet”: “”
},
“trans3”: {
“vlan_id”: “103”,
“subnet”: “”
}
},
“port_usages”: {
“vlan1099”: {
“mode”: “access”,
“disabled”: false,
“port_network”: “vlan1099”,
“voip_network”: null,
“stp_edge”: false,
“mac_auth_protocol”: null,
“all_networks”: false,
“networks”: null,
“port_auth”: null,
“enable_mac_auth”: null,
“mac_auth_only”: null,
“guest_network”: null,
“bypass_auth_when_server_down”: null,
“speed”: “auto”,
“duplex”: “auto”,
“mac_limit”: 0,
“persist_mac”: false,
“poe_disabled”: false,
“enable_qos”: false,
“storm_control”: {},
“mtu”: null,
“description”: “”,
“disable_autoneg”: false
},
“vlan1088”: {
“mode”: “access”,
“disabled”: false,
“port_network”: “vlan1088”,
“voip_network”: null,
“stp_edge”: false,
“mac_auth_protocol”: null,
“all_networks”: false,
“networks”: null,
“port_auth”: null,
“enable_mac_auth”: null,
“mac_auth_only”: null,
“guest_network”: null,
“bypass_auth_when_server_down”: null,
“speed”: “auto”,
“duplex”: “auto”,
“mac_limit”: 0,
“persist_mac”: false,
“poe_disabled”: false,
“enable_qos”: false,
“storm_control”: {},
“mtu”: null,
“description”: “”,
“disable_autoneg”: false
},
“dynamic”: {
“mode”: “dynamic”,
“rules”: []
}
},
“switch_matching”: {
“enable”: true,
“rules”: []
},
“switch_mgmt”: {
“config_revert_timer”: 10,
“root_password”: “<password>”,
“protect_re”: {
“enabled”: false
},
“tacacs”: {
“enabled”: false
}
},
“mist_nac”: {
“enabled”: true,
“network”: null
},
“radius_config”: {
“auth_servers”: [],
“acct_servers”: [],
“auth_servers_timeout”: 5,
“auth_servers_retries”: 3,
“fast_dot1x_timers”: false,
“acct_interim_interval”: 0,
“auth_server_selection”: “ordered”,
“coa_enabled”: false,
“coa_port”: “”
},
“vrf_config”: {
“enabled”: false
},
“remote_syslog”: {
“enabled”: false
},
“snmp_config”: {
“enabled”: false
},
“dhcp_snooping”: {
“enabled”: false
},
“dns_servers”: [],
“dns_suffix”: [],
“ntp_servers”: [],
“acl_policies”: [],
“port_mirroring”: {},
“name”: “campus-fabric”
}
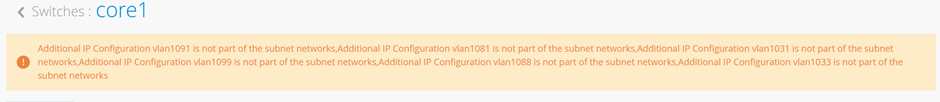
在 “园区交换矩阵配置 ”对话框中,有一个名为 “配置网络”的部分。您可以在此处从交换机模板导入 6 个接入 VLAN。完成后,配置应如图 11 所示,本例中的结果如下所示。由于这三个传输 VLAN 不属于接入层,因此不会在服务块功能中定义它们。
 的访问 VLAN 导入
的访问 VLAN 导入
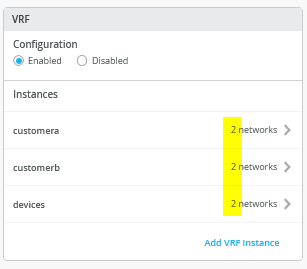
接下来,创建 3 个 VRF,并将其中两个接入网络连接到每个 VRF,如图 12 所示。
接下来,转到每个 VRF 并确认您只定义了没有默认路由的接入网络。稍后您将在服务块功能中定义传输 VLAN 和默认路由。请参阅图 13、 图 14 和图 15 。
 的 VLAN
的 VLAN
 的 VLAN
的 VLAN
 的 VLAN
的 VLAN
Core1 和 Core2 交换机配置
在传输 VLAN 连接示例中,服务块功能是虚拟的,并且位于核心交换机上。因此,您必须配置两个核心交换机。以下伪代码表示必须应用于 core1 和 core2 交换机的配置:
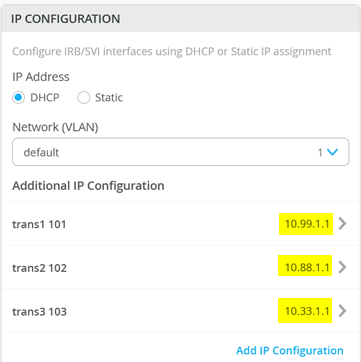
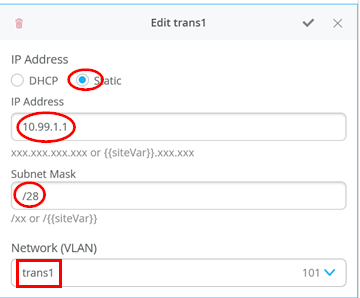
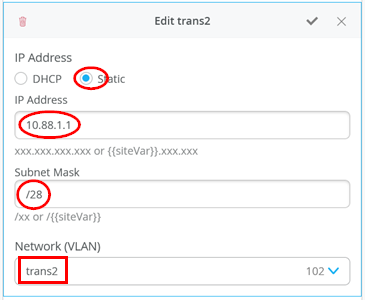
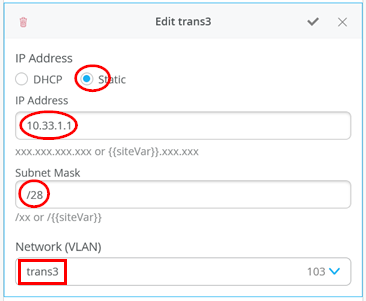
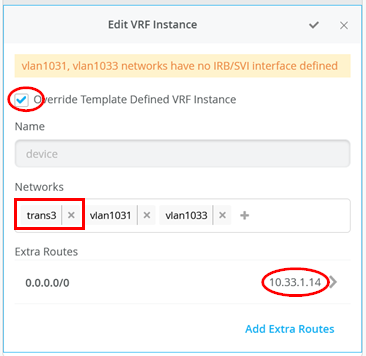
# configure the additional IP subnet 10.99.1.1/28 to network/VLAN:trans1 # configure the additional IP subnet 10.88.1.1/28 to network/VLAN:trans2 # configure the additional IP subnet 10.33.1.1/28 to network/VLAN:trans3 # Create a new local Port Profile called 'l2fabricexit' and configure: # Mode='Trunk' # Port Network (Untagged/Native VLAN)='None' # Add the following 3 Networks as Trunk Networks: # Network=trans1 # Network=trans2 # Network=trans3 # MTU='9018' # Create a new Port configuration where: # Port IDs=ge-0/0/3 # Interface=L2 Interface # Configuration Profile=l2fabricexit # Port Aggregation=Enable/Checked # AE Index=11 # ESI-LAG=Enable/Checked # Create a new Port configuration where: # Port IDs=ge-0/0/4 # Interface=L2 Interface # Configuration Profile=l2fabricexit # Port Aggregation=Enable/Checked # AE Index=12 # ESI-LAG=Enable/Checked # In VRF Configuration # Override Site/Template Settings=Checked # In Instance customera # Override Template Defined VRF Instance=Checked # Add the Network trans1 to the existing list of networks # Add the Extra Route 0.0.0.0/0 with via: 10.99.1.14 # In Instance customerb # Override Template Defined VRF Instance=Checked # Add the Network trans2 to the existing list of networks # Add the Extra Route 0.0.0.0/0 with via: 10.88.1.14 # In Instance device # Override Template Defined VRF Instance=Checked # Add the Network trans3 to the existing list of networks # Add the Extra Route 0.0.0.0/0 with via: 10.33.1.14
以下四个图像显示了由先前伪代码生成的 Mist GUI 配置,该配置从将本地 IP 地址分配给每个传输 VLAN 所需的其他 IP 配置开始。
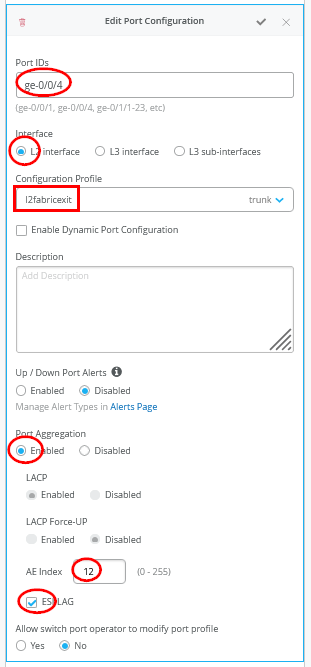
接下来,定义用于上行链路的 端口配置文件 。仅在中继网络定义中包含传输 VLAN 至关重要,因为只有这些 VLAN 才会被使用 WAN 路由器且可见。
 连接的 WAN 路由器的端口配置文件
连接的 WAN 路由器的端口配置文件
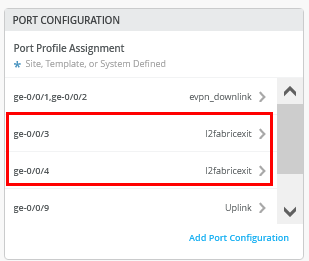
接下来,将端口配置文件分配给每个上行链路端口。
.png) 端口配置文件分配
端口配置文件分配
图 22 显示了到第一个 WAN 路由器的第一个上行链路的配置。
.png) 的第一个上行链路的端口配置
的第一个上行链路的端口配置
图 23 显示了到第一个 WAN 路由器的第二个上行链路的配置。
必须确保每个服务块功能上的 AE 索引 彼此同步,朝向同一 WAN 路由器,并将每个索引定义为 ESI-LAG。还必须确保不会重用已在结构服务块中的其他位置定义的 AE 索引。
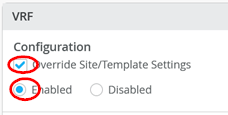
接下来,创建并修改本地 VRF。 请记住,这是仅针对传输 VLAN 退出方法的例外。通常,交换矩阵会自动创建 VRF。在这种情况下,我们必须在 VRF 配置中启用 覆盖站点/模板设置 复选框。 图 24 显示了 Mist GUI 中所需的配置。
 的模板设置
的模板设置
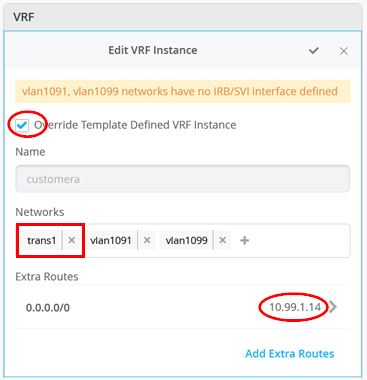
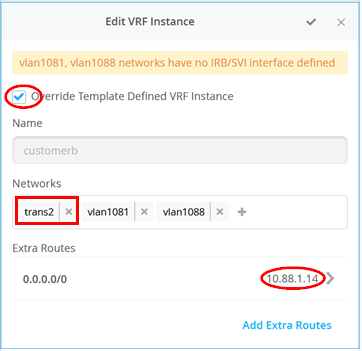
接下来,您必须在三个 VRS 实例中的每一个实例中执行以下三种配置:
- “启用 覆盖模板定义的 VRF 实例 ”复选框
- 将您的传输 VLAN 添加到预填充的接入 VLAN 列表中
- 添加一个默认路由,其中网关 IP 地址是 WAN 路由器的 VRRP-VIP 地址。
- 图 25、 图 26 和图 27 显示了三个 VRF 中每个 VRF 的覆盖配置。
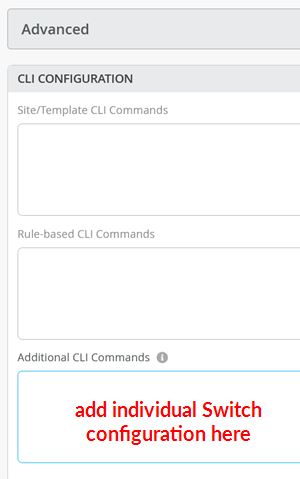
现在,您必须配置其他 CLI 来修改传输 VLAN,以使用 VGA 配置来帮助避免结构内流量的发夹路由过多。在每个服务块功能交换机的交换机配置中,找到 Mist GUI 中的 CLI 配置部分。您必须将所需的配置粘贴到图 28 中指示的字段中。
 的位置
的位置
以下代码块显示了 core1 交换机 的示例 CLI 配置。我们已将静态 IP 地址配置为虚拟网关 IP 地址 + 1 (10.99.1.2)。
# when service block function is a EX92xx change to VGA with the below delete groups top routing-instances evpn_vs protocols evpn default-gateway do-not-advertise set groups top routing-instances evpn_vs protocols evpn default-gateway no-gateway-community # on non-EX92xx switches change to VGA with the below # delete groups top protocols evpn default-gateway do-not-advertise # set groups top protocols evpn default-gateway no-gateway-community # modify our transport VLANs to VGA delete interfaces irb unit 101 family inet address 10.99.1.1/28 set interfaces irb unit 101 family inet address 10.99.1.2/28 virtual-gateway-address 10.99.1.1 set interfaces irb unit 101 virtual-gateway-accept-data set interfaces irb unit 101 virtual-gateway-v4-mac 00:00:5e:e4:05:01 delete interfaces irb unit 102 family inet address 10.88.1.1/28 set interfaces irb unit 102 family inet address 10.88.1.2/28 virtual-gateway-address 10.88.1.1 set interfaces irb unit 102 virtual-gateway-accept-data set interfaces irb unit 102 virtual-gateway-v4-mac 00:00:5e:e4:05:02 delete interfaces irb unit 103 family inet address 10.33.1.1/28 set interfaces irb unit 103 family inet address 10.33.1.2/28 virtual-gateway-address 10.33.1.1 set interfaces irb unit 103 virtual-gateway-accept-data set interfaces irb unit 103 virtual-gateway-v4-mac 00:00:5e:e4:05:03
对于 core2 交换机, 仅将传输 VLAN 的静态 IP 地址更改为虚拟网关 IP 地址 + 2 (10.88.1.3)。
# when service block function is a EX92xx change to VGA with the below delete groups top routing-instances evpn_vs protocols evpn default-gateway do-not-advertise set groups top routing-instances evpn_vs protocols evpn default-gateway no-gateway-community # on all non-EX92xx switches change to VGA with the below # delete groups top protocols evpn default-gateway do-not-advertise # set groups top protocols evpn default-gateway no-gateway-community # modify our transport VLANs to VGA delete interfaces irb unit 101 family inet address 10.99.1.1/28 set interfaces irb unit 101 family inet address 10.99.1.3/28 virtual-gateway-address 10.99.1.1 set interfaces irb unit 101 virtual-gateway-accept-data set interfaces irb unit 101 virtual-gateway-v4-mac 00:00:5e:e4:05:01 delete interfaces irb unit 102 family inet address 10.88.1.1/28 set interfaces irb unit 102 family inet address 10.88.1.3/28 virtual-gateway-address 10.88.1.1 set interfaces irb unit 102 virtual-gateway-accept-data set interfaces irb unit 102 virtual-gateway-v4-mac 00:00:5e:e4:05:02 delete interfaces irb unit 103 family inet address 10.33.1.1/28 set interfaces irb unit 103 family inet address 10.33.1.3/28 virtual-gateway-address 10.33.1.1 set interfaces irb unit 103 virtual-gateway-accept-data set interfaces irb unit 103 virtual-gateway-v4-mac 00:00:5e:e4:05:03
请记住,我们的测试实验室使用虚拟 EX9214 交换机作为核心交换机。在大多数生产环境中,您不会使用 EX92xx 交换机。因此,您必须取消注释上一个配置片段中注释掉的两行:
# delete groups top protocols evpn default-gateway do-not-advertise # set groups top protocols evpn default-gateway no-gateway-community
每个 VRF 使用的每个传输 VLAN 的服务块 您必须手动设置 IRB 接口上使用的虚拟网关地址的 MAC 地址。在我们的示例中,我们对每个传输 VLAN 使用了不同的 MAC 地址,因为它更易于调试。
作为 WAN 路由器的瞻博网络 MX
以下 CLI 代码段示例包含接口配置、VRRP 网关冗余以及第一个 WAN 路由器的静态路由。您可能需要添加默认路由和接口才能完成配置。
set system host-name wanrouter1 set chassis aggregated-devices ethernet device-count 10 delete interfaces ae0 delete policy-options policy-statement fabric delete policy-options policy-statement internet delete routing-instances public-int set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all delete interfaces ge-0/0/1 set interfaces ge-0/0/1 gigether-options 802.3ad ae11 delete interfaces ge-0/0/2 set interfaces ge-0/0/2 gigether-options 802.3ad ae11 delete interfaces ae11 set interfaces ae11 mtu 9018 set interfaces ae11 aggregated-ether-options lacp active set interfaces ae11 aggregated-ether-options lacp admin-key 11 set interfaces ae11 unit 0 family bridge interface-mode trunk set interfaces ae11 unit 0 family bridge vlan-id-list 101 set interfaces ae11 unit 0 family bridge vlan-id-list 102 set interfaces ae11 unit 0 family bridge vlan-id-list 103 set bridge-domains trans1 vlan-id 101 set bridge-domains trans1 routing-interface irb.101 set bridge-domains trans2 vlan-id 102 set bridge-domains trans2 routing-interface irb.102 set bridge-domains trans3 vlan-id 103 set bridge-domains trans3 routing-interface irb.103 set interfaces irb unit 101 family inet address 10.99.1.13/28 vrrp-group 1 virtual-address 10.99.1.14 set interfaces irb unit 101 family inet address 10.99.1.13/28 vrrp-group 1 priority 110 set interfaces irb unit 101 family inet address 10.99.1.13/28 vrrp-group 1 accept-data set interfaces irb unit 102 family inet address 10.88.1.13/28 vrrp-group 2 virtual-address 10.88.1.14 set interfaces irb unit 102 family inet address 10.88.1.13/28 vrrp-group 2 priority 110 set interfaces irb unit 102 family inet address 10.88.1.13/28 vrrp-group 2 accept-data set interfaces irb unit 103 family inet address 10.33.1.13/28 vrrp-group 3 virtual-address 10.33.1.14 set interfaces irb unit 103 family inet address 10.33.1.13/28 vrrp-group 3 priority 110 set interfaces irb unit 103 family inet address 10.33.1.13/28 vrrp-group 3 accept-data set routing-options static route 10.99.91.0/24 next-hop 10.99.1.1 set routing-options static route 10.99.99.0/24 next-hop 10.99.1.1 set routing-options static route 172.16.193.0/24 next-hop 10.99.1.1 set routing-options static route 10.88.81.0/24 next-hop 10.88.1.1 set routing-options static route 10.88.88.0/24 next-hop 10.88.1.1 set routing-options static route 172.16.194.0/24 next-hop 10.88.1.1 set routing-options static route 10.33.31.0/24 next-hop 10.33.1.1 set routing-options static route 10.33.33.0/24 next-hop 10.33.1.1 set routing-options static route 172.16.195.0/24 next-hop 10.33.1.1
在第二个 WAN 路由器上,值得注意的配置更改是 AE 密钥和索引以及静态 IP 地址。
set system host-name wanrouter2 set chassis aggregated-devices ethernet device-count 10 set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all delete interfaces ge-0/0/1 set interfaces ge-0/0/1 gigether-options 802.3ad ae12 delete interfaces ge-0/0/2 set interfaces ge-0/0/2 gigether-options 802.3ad ae12 delete interfaces ae12 set interfaces ae12 mtu 9018 set interfaces ae12 aggregated-ether-options lacp active set interfaces ae12 aggregated-ether-options lacp admin-key 12 set interfaces ae12 unit 0 family bridge interface-mode trunk set interfaces ae12 unit 0 family bridge vlan-id-list 101 set interfaces ae12 unit 0 family bridge vlan-id-list 102 set interfaces ae12 unit 0 family bridge vlan-id-list 103 set bridge-domains trans1 vlan-id 101 set bridge-domains trans1 routing-interface irb.101 set bridge-domains trans2 vlan-id 102 set bridge-domains trans2 routing-interface irb.102 set bridge-domains trans3 vlan-id 103 set bridge-domains trans3 routing-interface irb.103 set interfaces irb unit 101 family inet address 10.99.1.12/28 vrrp-group 1 virtual-address 10.99.1.14 set interfaces irb unit 101 family inet address 10.99.1.12/28 vrrp-group 1 accept-data set interfaces irb unit 102 family inet address 10.88.1.12/28 vrrp-group 2 virtual-address 10.88.1.14 set interfaces irb unit 102 family inet address 10.88.1.12/28 vrrp-group 2 accept-data set interfaces irb unit 103 family inet address 10.33.1.12/28 vrrp-group 3 virtual-address 10.33.1.14 set interfaces irb unit 103 family inet address 10.33.1.12/28 vrrp-group 3 accept-data set routing-options static route 10.99.91.0/24 next-hop 10.99.1.1 set routing-options static route 10.99.99.0/24 next-hop 10.99.1.1 set routing-options static route 172.16.193.0/24 next-hop 10.99.1.1 set routing-options static route 10.88.81.0/24 next-hop 10.88.1.1 set routing-options static route 10.88.88.0/24 next-hop 10.88.1.1 set routing-options static route 172.16.194.0/24 next-hop 10.88.1.1 set routing-options static route 10.33.31.0/24 next-hop 10.33.1.1 set routing-options static route 10.33.33.0/24 next-hop 10.33.1.1 set routing-options static route 172.16.195.0/24 next-hop 10.33.1.1
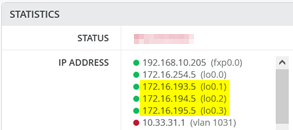
您可能想知道 172.16.19x.0 范围内的那些静态路由。请记住,IP Clos 是任播交换矩阵。因此,您必须有静态路由来准备 DHCP 中继何时使用结构叠加网络中的 IP 地址。有关示例定义,请参见图 29。
.png) 的环回
的环回
覆盖环路 IP 作为 /24 范围分配给交换机上的每个 VRF。您可以通过查看结构接入交换机来弄清楚它们,如图 30 所示。因此,您必须像连接到 VRF 的任何其他附加 VLAN 一样将它们映射回来,以实现所需的可访问性。
.png)
以下命令有助于调试 WAN 路由器 1 上的连接。
root@wanrouter1> show lldp neighbors
Local Interface Parent Interface Chassis Id Port info System Name
ge-0/0/0 - 4c:96:14:95:09:80 516 internet
ge-0/0/1 ae11 2c:6b:f5:3a:42:c0 ge-0/0/3 core1
ge-0/0/2 ae11 2c:6b:f5:7f:7d:c0 ge-0/0/3 core2
root@wanrouter1> show lacp interfaces
Aggregated interface: ae11
LACP state: Role Exp Def Dist Col Syn Aggr Timeout Activity
ge-0/0/1 Actor No No Yes Yes Yes Yes Fast Active
ge-0/0/1 Partner No No Yes Yes Yes Yes Fast Active
ge-0/0/2 Actor No No Yes Yes Yes Yes Fast Active
ge-0/0/2 Partner No No Yes Yes Yes Yes Fast Active
LACP protocol: Receive State Transmit State Mux State
ge-0/0/1 Current Fast periodic Collecting distributing
ge-0/0/2 Current Fast periodic Collecting distributing
root@wanrouter1> show vrrp
Interface State Group VR state VR Mode Timer Type Address
irb.101 up 1 master Active A 0.350 lcl 10.99.1.13
vip 10.99.1.14
irb.102 up 2 master Active A 0.625 lcl 10.88.1.13
vip 10.88.1.14
irb.103 up 3 master Active A 0.830 lcl 10.33.1.13
vip 10.33.1.14
以下命令可帮助您调试 WAN 路由器 2 上的连接。
root@wanrouter2> show lldp neighbors
Local Interface Parent Interface Chassis Id Port info System Name
ge-0/0/0 - 4c:96:14:95:09:80 517 internet
ge-0/0/1 ae12 2c:6b:f5:3a:42:c0 ge-0/0/4 core1
ge-0/0/2 ae12 2c:6b:f5:7f:7d:c0 ge-0/0/4 core2
root@wanrouter2> show lacp interfaces
Aggregated interface: ae12
LACP state: Role Exp Def Dist Col Syn Aggr Timeout Activity
ge-0/0/1 Actor No No Yes Yes Yes Yes Fast Active
ge-0/0/1 Partner No No Yes Yes Yes Yes Fast Active
ge-0/0/2 Actor No No Yes Yes Yes Yes Fast Active
ge-0/0/2 Partner No No Yes Yes Yes Yes Fast Active
LACP protocol: Receive State Transmit State Mux State
ge-0/0/1 Current Fast periodic Collecting distributing
ge-0/0/2 Current Fast periodic Collecting distributing
root@wanrouter2> show vrrp
Interface State Group VR state VR Mode Timer Type Address
irb.101 up 1 backup Active D 2.811 lcl 10.99.1.12
vip 10.99.1.14
mas 10.99.1.13
irb.102 up 2 backup Active D 3.303 lcl 10.88.1.12
vip 10.88.1.14
mas 10.88.1.13
irb.103 up 3 backup Active D 2.798 lcl 10.33.1.12
vip 10.33.1.14
mas 10.33.1.13
使用 eBGP 路由协议的 L3 出口
使用园区交换矩阵创建任何 VLAN 或 VRF 时,请记住以下最佳实践:
- 在交换机模板中创建所有 VLAN,然后将其导入园区 交换矩阵对话。在 Mist GUI 中的任何其他位置创建 VLAN 最终会导致不一致,从而难以解决问题。
- 如果需要,交换矩阵会创建任何所需的 VRF。请勿在 Mist GUI 中的其他位置手动创建 VRF。
- 我们建议您在交换机模板中创建端口配置文件,以便在交换矩阵中的所有交换机上同步任何更改。
在开始之前,您需要制定以下计划:
- 如何实现路由协议和路由交换
- 如何配置 P2P 链路
- 如何分配间接用于标识 VRF 的 VLAN 分配
即使 VRF 已存在于交换矩阵中的其他位置(例如 IP Clos 的接入交换机上),在执行 L3 出口时,系统也会在所有服务块功能上自动重新创建 VRF。
对于每个 WAN 路由器,您必须在 VRF 上重复使用 VLAN 名称,以帮助在服务块功能上自动创建 VRF。请记住,当您定义本地 P2P 链路并重用 VLAN 时,这些定义纯粹是本地定义,因此不会与叠加 VLAN 定义冲突。此外,您无需在此处定义特殊的传输 VLAN。但是,如果 P2P 链路更适合您的需求,您仍然可以使用 和定义特殊的传输 VLAN。
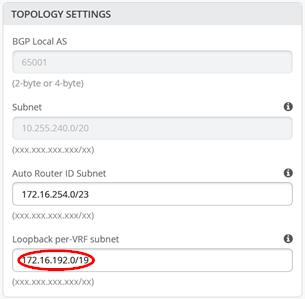
定义 P2P 链路时,必须确保它们不在结构使用的地址范围之内。结构用于这些链路的默认范围为 10.255.240.0/20。建议使用 /31 网络掩码。通过该计划,您可以将偶数 IP 地址用于 WAN 路由器端,奇数 IP 地址用于结构端。
系统要求您为物理电缆上的每个 P2P 链路使用 VLAN。这样,您就可以在一根上行链路电缆上多路复用多个 VRF。请记住,VLAN 在内部引用回 VRF。
对于 eBGP,还必须定义自己的专用 ASN 以进行对等互连。默认情况下,结构对 EVPN 控制平面使用 65000 ASN,并在 65001 处开始分配可配置的 ASN。之后,它为每个节点前进一位数字。因此,我们建议使用低于 65000 的 ASN 值,以避免与系统分配的 ASN 发生冲突。QFX 交换机仅允许 16 个本地 ASN。因此,我们建议您在所有 VRF 之间使用共享 ASN。但是,在我们的示例中,我们决定为每个 WAN 路由器使用不同的 ASN。
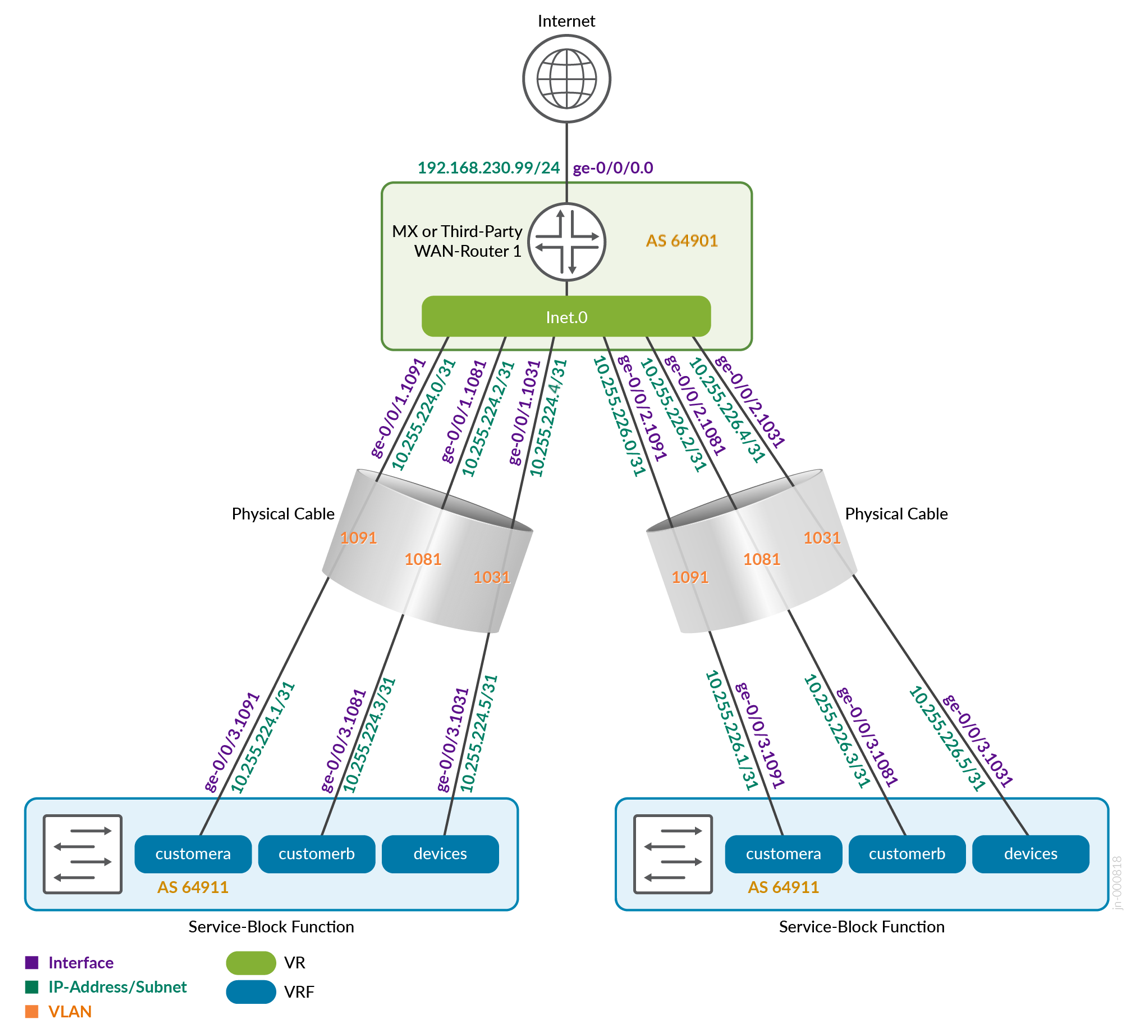
图 31 显示了交换矩阵的两个服务块功能如何连接到第一个 WAN 路由器。
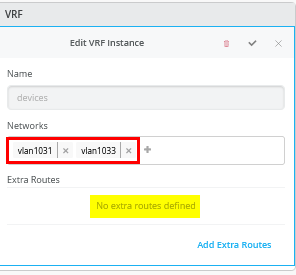
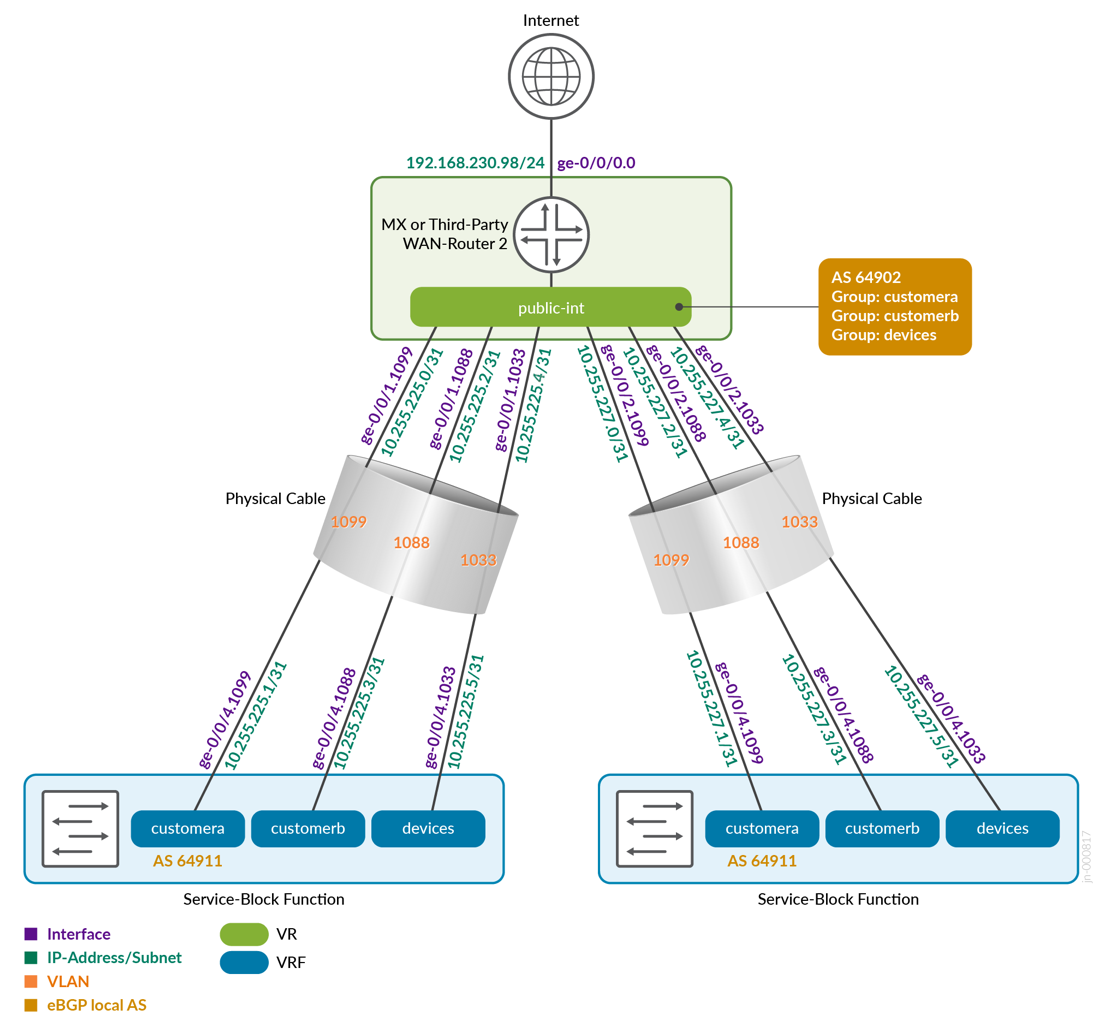
图 32 显示了交换矩阵的两个服务块功能如何连接到第二个 WAN 路由器。请注意,我们现在使用每个 VRF 中的第二个 VLAN 块。
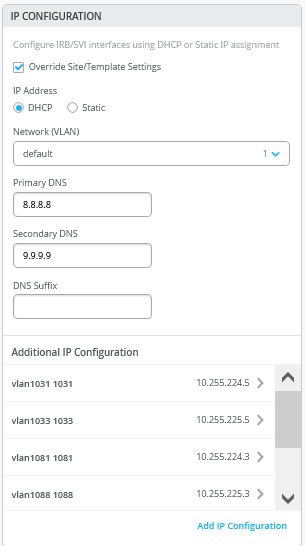
表 1 显示了作为服务块功能的 core1 和 core2 交换机与两个 WAN 路由器之间的完整配置。您还可以看到为 eBGP 选择的 ASN。
| 交换机 | 交换机 AS | VRF | 核心 P2P IP | 核心 | IF WAN 路由器 WAN | 路由器 P2P IP | WAN 路由器 AS | WAN 路由器 IF | VLAN ID |
|---|---|---|---|---|---|---|---|---|---|
| 核心1 | 64911 | 客户a | 10.255.224.1/31 | ge-0/0/3.1091 | 万路由器1 | 10.255.224.0/31 | 64901 | ge-0/0/1.1091 | 1091 |
| 核心1 | 64911 | 客户b | 10.255.224.3/31 | ge-0/0/3.1081 | 万路由器1 | 10.255.224.2/31 | 64901 | ge-0/0/1.1081 | 1081 |
| 核心1 | 64911 | 设备 | 10.255.224.5/31 | ge-0/0/3.1031 | 万路由器1 | 10.255.224.4/31 | 64901 | ge-0/0/1.1031 | 1031 |
| 核心1 | 64911 | 客户a | 10.255.225.1/31 | ge-0/0/4.1099 | 万路由器2 | 10.255.225.0/31 | 64902 | ge-0/0/1.1099 | 1099 |
| 核心1 | 64911 | 客户b | 10.255.225.3/31 | ge-0/0/4.1088 | 万路由器2 | 10.255.225.2/31 | 64902 | ge-0/0/1.1088 | 1088 |
| 核心1 | 64911 | 设备 | 10.255.225.5/31 | ge-0/0/4.1033 | 万路由器2 | 10.255.225.4/31 | 64902 | ge-0/0/1.1033 | 1033 |
| 核心2 | 64911 | 客户a | 10.255.226.1/31 | ge-0/0/3.1091 | 万路由器1 | 10.255.226.0/31 | 64901 | ge-0/0/2.1091 | 1091 |
| 核心2 | 64911 | 客户b | 10.255.226.3/31 | ge-0/0/3.1081 | 万路由器1 | 10.255.226.2/31 | 64901 | ge-0/0/2.1081 | 1081 |
| 核心2 | 64911 | 设备 | 10.255.226.5/31 | ge-0/0/3.1031 | 万路由器1 | 10.255.226.4/31 | 64901 | ge-0/0/2.1031 | 1031 |
| 核心2 | 64911 | 客户a | 10.255.227.1/31 | ge-0/0/4.1099 | 万路由器2 | 10.255.227.0/31 | 64902 | ge-0/0/2.1099 | 1099 |
| 核心2 | 64911 | 客户b | 10.255.227.3/31 | ge-0/0/4.1088 | 万路由器2 | 10.255.227.2/31 | 64902 | ge-0/0/2.1088 | 1088 |
| 核心2 | 64911 | 设备 | 10.255.227.5/31 | ge-0/0/4.1033 | 万路由器2 | 10.255.227.4/31 | 64902 | ge-0/0/2.1033 | 1033 |
下面的代码块显示了此交换矩阵中使用的交换机模板的导出版本。这允许您在导入时查看我们的设置。如您所见,每个 VRF 至少有两个 VLAN。请记住,L3 出口型号要求每个 WAN 路由器和 VRF 一个 VLAN)。
{
"additional_config_cmds": [],
"networks": {
"vlan1099": {
"vlan_id": 1099,
"subnet": "10.99.99.0/24"
},
"vlan1088": {
"vlan_id": 1088,
"subnet": "10.88.88.0/24"
},
"vlan1033": {
"vlan_id": 1033,
"subnet": "10.33.33.0/24"
},
"vlan1091": {
"vlan_id": 1091,
"subnet": "10.99.91.0/24"
},
"vlan1081": {
"vlan_id": 1081,
"subnet": "10.88.81.0/24"
},
"vlan1031": {
"vlan_id": 1031,
"subnet": "10.33.31.0/24"
}
},
"port_usages": {
"vlan1099": {
"mode": "access",
"disabled": false,
"port_network": "vlan1099",
"voip_network": null,
"stp_edge": false,
"mac_auth_protocol": null,
"all_networks": false,
"networks": null,
"port_auth": null,
"enable_mac_auth": null,
"mac_auth_only": null,
"guest_network": null,
"bypass_auth_when_server_down": null,
"speed": "auto",
"duplex": "auto",
"mac_limit": 0,
"persist_mac": false,
"poe_disabled": false,
"enable_qos": false,
"storm_control": {},
"mtu": null,
"description": "",
"disable_autoneg": false
},
"vlan1088": {
"mode": "access",
"disabled": false,
"port_network": "vlan1088",
"voip_network": null,
"stp_edge": false,
"mac_auth_protocol": null,
"all_networks": false,
"networks": null,
"port_auth": null,
"enable_mac_auth": null,
"mac_auth_only": null,
"guest_network": null,
"bypass_auth_when_server_down": null,
"speed": "auto",
"duplex": "auto",
"mac_limit": 0,
"persist_mac": false,
"poe_disabled": false,
"enable_qos": false,
"storm_control": {},
"mtu": null,
"description": "",
"disable_autoneg": false
},
"dynamic": {
"mode": "dynamic",
"reset_default_when": "link_down",
"rules": []
}
},
"switch_matching": {
"enable": true,
"rules": []
},
"switch_mgmt": {
"config_revert_timer": 10,
"root_password": "<password>",
"protect_re": {
"enabled": false
},
"tacacs": {
"enabled": false
}
},
"mist_nac": {
"enabled": true,
"network": null
},
"radius_config": {
"auth_servers": [],
"acct_servers": [],
"auth_servers_timeout": 5,
"auth_servers_retries": 3,
"fast_dot1x_timers": false,
"acct_interim_interval": 0,
"auth_server_selection": "ordered",
"coa_enabled": false,
"coa_port": ""
},
"vrf_config": {
"enabled": false
},
"remote_syslog": {
"enabled": false
},
"snmp_config": {
"enabled": false
},
"dhcp_snooping": {
"enabled": false
},
"dns_servers": [],
"dns_suffix": [],
"ntp_servers": [],
"acl_policies": [],
"port_mirroring": {},
"name": "campus-fabric"
}
在 “园区交换矩阵配置 ”对话框中,有一个名为 “配置网络”的页面。这是从交换机模板导入六个 VLAN 的位置。生成的配置如下图所示。
 实例连接 2 个网络
实例连接 2 个网络
然后,转到每个VRF并删除您可能拥有的所有手动路由。确保每个 VRF 至少连接了两个 VLAN,因为这些 VLAN 稍后将用于识别 VRF。
Core1 交换机配置
在此示例中,服务块功能是虚拟的,并且位于核心交换机上。因此,您必须配置两个核心交换机。以下伪代码块描述了您需要在 core1 交换机上进行配置的内容:
# configure the Additional IP-Subnet 10.255.224.1 255.255.255.254 to Network/VLAN:vlan1091 # configure the Additional IP-Subnet 10.255.224.3 255.255.255.254 to Network/VLAN:vlan1081 # configure the Additional IP-Subnet 10.255.224.5 255.255.255.254 to Network/VLAN:vlan1031 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/3 as L3-Sub-Interfaces with MTU=9018 # configure the Additional IP-Subnet 10.255.225.1 255.255.255.254 to Network/VLAN:vlan1099 # configure the Additional IP-Subnet 10.255.225.3 255.255.255.254 to Network/VLAN:vlan1088 # configure the Additional IP-Subnet 10.255.225.5 255.255.255.254 to Network/VLAN:vlan1033 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/4 as L3-Sub-Interfaces with MTU=9018 # Enable BGP and create an Export policy called 'export-vrfs' # Add to this export Policy the following Networks as: # - Add Term w. Name=vlan1091 Prefix=10.99.91.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1099 Prefix=10.99.99.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1081 Prefix=10.88.81.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1088 Prefix=10.88.88.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1031 Prefix=10.33.31.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1033 Prefix=10.33.33.0/24 Protocol=None Then=Accept # - Add Term w. Name=overlaylo0 Prefix=172.16.192.0/19-32 Protocol=None Then=Accept # Create an Export policy called 'import-default' # - Name=default Prefix=0.0.0.0/0 Protocol=BGP Action=Accept # Create a BGP Group with: # - Name=customera0 # - Type=External # - Network (VLAN)=vlan1091 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.224.0 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customerb0 # - Type=External # - Network (VLAN)=vlan1081 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.224.2 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=devices0 # - Type=External # - Network (VLAN)=vlan1031 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.224.4 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customera1 # - Type=External # - Network (VLAN)=vlan1099 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.225.0 Neighbor_AS=64902 Hold-Time=90 # Create a BGP Group with: # - Name=customerb1 # - Type=External # - Network (VLAN)=vlan1088 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.225.2 Neighbor_AS=64902 Hold-Time=90 # Create a BGP Group with: # - Name=devices1 # - Type=External # - Network (VLAN)=vlan1033 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.225.4 Neighbor_AS=64902 Hold-Time=90
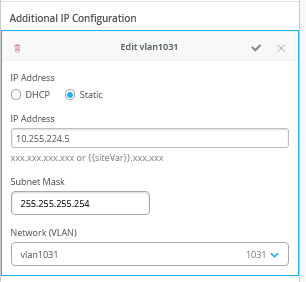
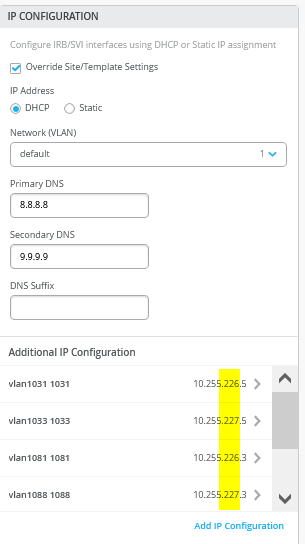
以下屏幕截图显示了转换为 Mist GUI 的先前配置。我们从额外的 IP 配置开始。请注意,VLAN IP 地址与这些 VLAN 最初在叠加网络中的 IP 地址不匹配。这是设计使然。您必须始终将 VLAN 作为 VRF 的参考。
 的六个 VLAN 之一
的六个 VLAN 之一
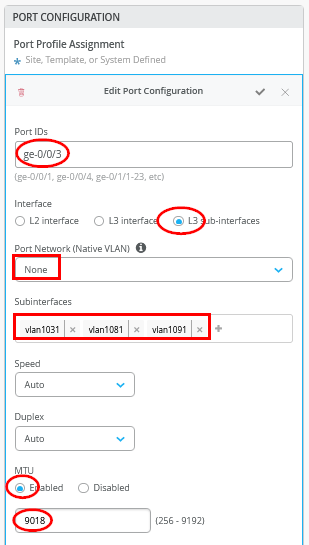
在 端口配置 窗口中,必须启用 L3 子接口 并分配定义的前 3 个子接口。
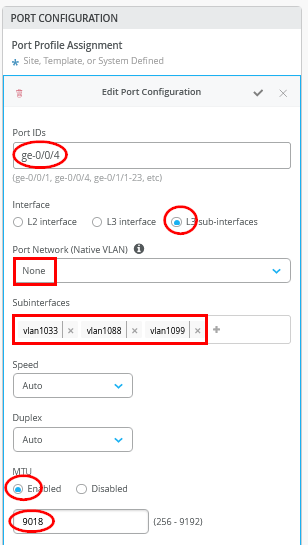
在第二个 端口配置 窗口中,针对另一个 WAN 路由器,分配定义的第二个 3 个子接口。
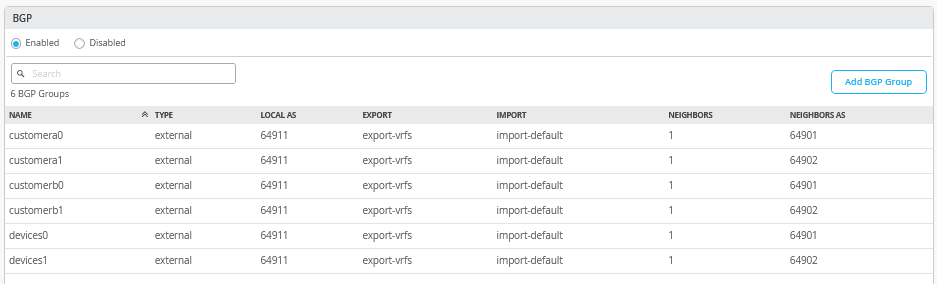
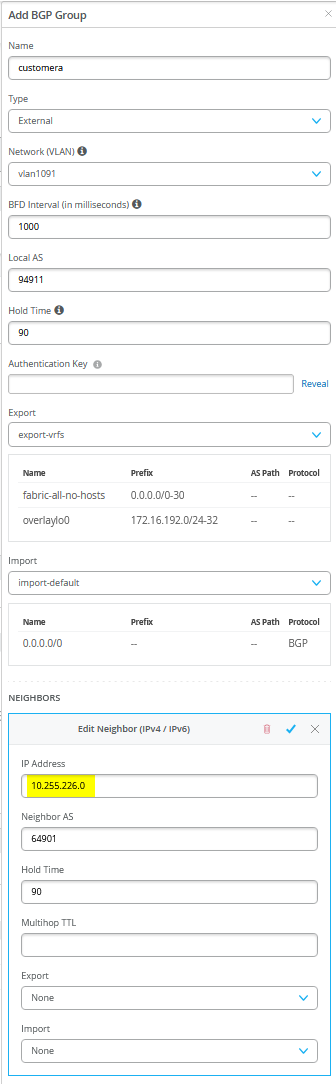
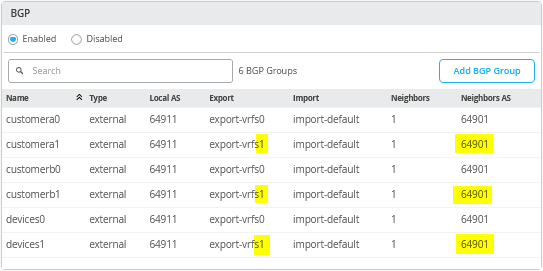
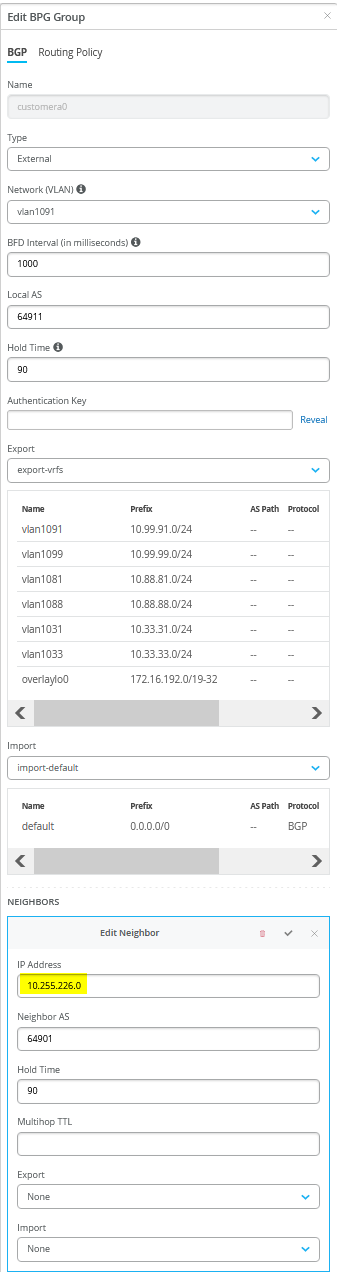
接下来,您必须输入包含所有六个对等方(三个 VRF 和两个 WAN 路由器)的整个 eBGP 配置。完成后,概述页应如图 40 所示。
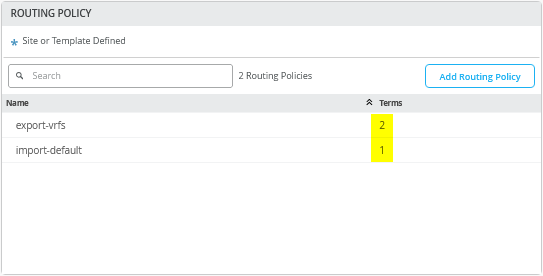
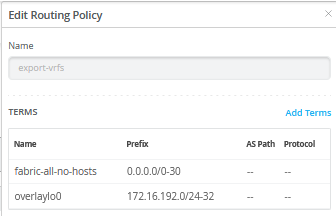
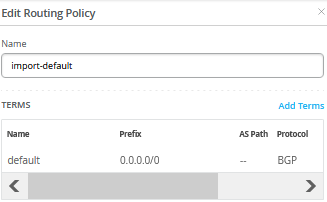
首先,定义两个路由策略,其摘要如上表所示。
导出路由策略包含 VRF 中每个 VLAN 的子网,以及作为初始交换矩阵对话框中定义的一部分的每 VRF 环回子网的定义。您可以用一个 0.0.0.0/0-32 前缀替换所有六个前缀。将前缀写入 0.0.0.0/0-32 是在 Junos OS 中定义 或延长 长度的一种方法。
导入策略从 WAN 路由器导入默认路由。
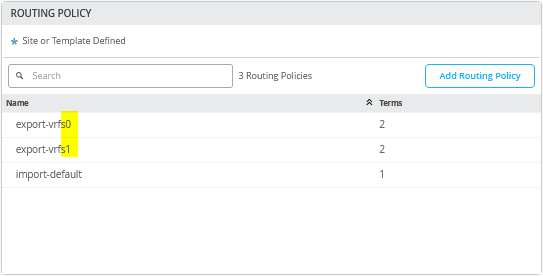
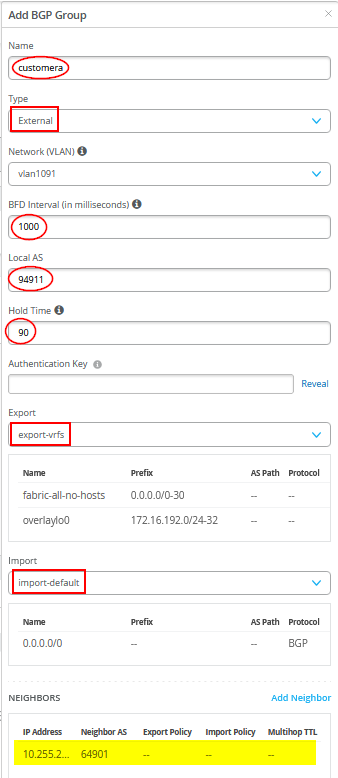
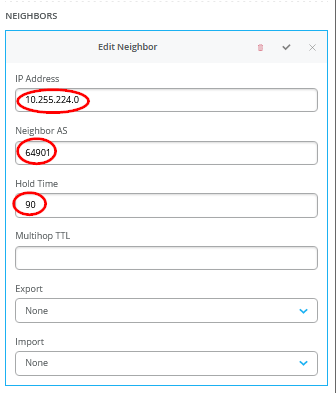
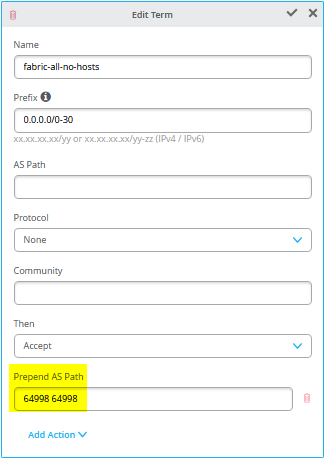
图 42 显示了单个 BGP 对等条目的配置,其中标注了所需的条目。
 示例
示例
您还必须将 WAN 路由器定义为 BGP 邻接方。
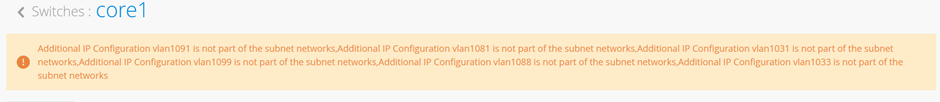
您可能会看到一条警告消息,如图 43 所示。忽略这些是安全的。
Core2 交换机配置
以下伪代码表示您必须应用于 core2 交换机的配置:
# configure the Additional IP-Subnet 10.255.226.1 255.255.255.254 to Network/VLAN:vlan1091 # configure the Additional IP-Subnet 10.255.226.3 255.255.255.254 to Network/VLAN:vlan1081 # configure the Additional IP-Subnet 10.255.226.5 255.255.255.254 to Network/VLAN:vlan1031 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/3 as L3-Sub-Interfaces with MTU=9018 # configure the Additional IP-Subnet 10.255.227.1 255.255.255.254 to Network/VLAN:vlan1099 # configure the Additional IP-Subnet 10.255.227.3 255.255.255.254 to Network/VLAN:vlan1088 # configure the Additional IP-Subnet 10.255.227.5 255.255.255.254 to Network/VLAN:vlan1033 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/4 as L3-Sub-Interfaces with MTU=9018 # Enable BGP and create an Export policy called 'export-vrfs' # Add to this export Policy the following Networks as: # - Add Term w. Name=vlan1091 Prefix=10.99.91.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1099 Prefix=10.99.99.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1081 Prefix=10.88.81.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1088 Prefix=10.88.88.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1031 Prefix=10.33.31.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1033 Prefix=10.33.33.0/24 Protocol=None Then=Accept # - Add Term w. Name=overlaylo0 Prefix=172.16.192.0/19-32 Protocol=None Then=Accept # Create an Export policy called 'import-default' # - Name=default Prefix=0.0.0.0/0 Protocol=BGP Action=Accept # Create a BGP Group with: # - Name=customera0 # - Type=External # - Network (VLAN)=vlan1091 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.226.0 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customerb0 # - Type=External # - Network (VLAN)=vlan1081 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.226.2 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=devices0 # - Type=External # - Network (VLAN)=vlan1031 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.226.4 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customera1 # - Type=External # - Network (VLAN)=vlan1099 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.227.0 Neighbor_AS=64902 Hold-Time=90 # Create a BGP Group with: # - Name=customerb1 # - Type=External # - Network (VLAN)=vlan1088 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.227.2 Neighbor_AS=64902 Hold-Time=90 # Create a BGP Group with: # - Name=devices1 # - Type=External # - Network (VLAN)=vlan1033 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.227.4 Neighbor_AS=64902 Hold-Time=90
除了 P2P 子网和 BGP 邻居之外,core2 交换机上的配置与 core1 交换机上的配置相同。
瞻博网络 MX 作为 WAN 路由器
以下几个代码块显示了 P2P 接口的 Junos OS CLI 配置、包含所有 BGP 邻居的整个 eBGP 配置以及每个 WAN 路由器的所有导入和导出路由策略。您可能需要添加默认路由和接口才能完成配置,因为这些路由和接口需要向交换矩阵发出信号,但我们不知道您的设备是如何知道这些路由和接口的。
第一个 WAN 路由器的 CLI 配置:
set system host-name wanrouter1 delete interfaces ge-0/0/1 set interfaces ge-0/0/1 flexible-vlan-tagging set interfaces ge-0/0/1 mtu 9014 set interfaces ge-0/0/1 unit 1091 description vlan1091 set interfaces ge-0/0/1 unit 1091 vlan-id 1091 set interfaces ge-0/0/1 unit 1091 family inet address 10.255.224.0/31 set interfaces ge-0/0/1 unit 1081 description vlan1081 set interfaces ge-0/0/1 unit 1081 vlan-id 1081 set interfaces ge-0/0/1 unit 1081 family inet address 10.255.224.2/31 set interfaces ge-0/0/1 unit 1031 description vlan1031 set interfaces ge-0/0/1 unit 1031 vlan-id 1031 set interfaces ge-0/0/1 unit 1031 family inet address 10.255.224.4/31 delete interfaces ge-0/0/2 set interfaces ge-0/0/2 flexible-vlan-tagging set interfaces ge-0/0/2 mtu 9014 set interfaces ge-0/0/2 unit 1091 description vlan1091 set interfaces ge-0/0/2 unit 1091 vlan-id 1091 set interfaces ge-0/0/2 unit 1091 family inet address 10.255.226.0/31 set interfaces ge-0/0/2 unit 1081 description vlan1081 set interfaces ge-0/0/2 unit 1081 vlan-id 1081 set interfaces ge-0/0/2 unit 1081 family inet address 10.255.226.2/31 set interfaces ge-0/0/2 unit 1031 description vlan1031 set interfaces ge-0/0/2 unit 1031 vlan-id 1031 set interfaces ge-0/0/2 unit 1031 family inet address 10.255.226.4/31 # needed in and export policy delete policy-options set policy-options policy-statement fabric term 1 from protocol bgp set policy-options policy-statement fabric term 1 from route-filter 0.0.0.0/0 orlonger set policy-options policy-statement fabric term 1 then accept set policy-options policy-statement fabric term 2 then reject set policy-options policy-statement internet term 1 from protocol static set policy-options policy-statement internet term 1 from route-filter 0.0.0.0/0 exact set policy-options policy-statement internet term 1 then accept set policy-options policy-statement internet term 2 then reject delete routing-instances public-int set routing-instances public-int instance-type virtual-router set routing-instances public-int interface ge-0/0/1.1091 set routing-instances public-int interface ge-0/0/1.1081 set routing-instances public-int interface ge-0/0/1.1031 set routing-instances public-int interface ge-0/0/2.1091 set routing-instances public-int interface ge-0/0/2.1081 set routing-instances public-int interface ge-0/0/2.1031 delete routing-instances public-int protocols bgp group customera set routing-instances public-int protocols bgp group customera type external set routing-instances public-int protocols bgp group customera family inet unicast set routing-instances public-int protocols bgp group customera multipath multiple-as set routing-instances public-int protocols bgp group customera local-as 64901 set routing-instances public-int protocols bgp group customera hold-time 90 set routing-instances public-int protocols bgp group customera import fabric set routing-instances public-int protocols bgp group customera export internet set routing-instances public-int protocols bgp group customera bfd-liveness-detection minimum-interval 1000 set routing-instances public-int protocols bgp group customera bfd-liveness-detection multiplier 3 set routing-instances public-int protocols bgp group customera bfd-liveness-detection session-mode automatic set routing-instances public-int protocols bgp group customera neighbor 10.255.224.1 peer-as 64911 set routing-instances public-int protocols bgp group customera neighbor 10.255.226.1 peer-as 64911 delete routing-instances public-int protocols bgp group customerb set routing-instances public-int protocols bgp group customerb type external set routing-instances public-int protocols bgp group customerb family inet unicast set routing-instances public-int protocols bgp group customerb multipath multiple-as set routing-instances public-int protocols bgp group customerb local-as 64901 set routing-instances public-int protocols bgp group customerb hold-time 90 set routing-instances public-int protocols bgp group customerb import fabric set routing-instances public-int protocols bgp group customerb export internet set routing-instances public-int protocols bgp group customerb bfd-liveness-detection minimum-interval 1000 set routing-instances public-int protocols bgp group customerb bfd-liveness-detection multiplier 3 set routing-instances public-int protocols bgp group customerb bfd-liveness-detection session-mode automatic set routing-instances public-int protocols bgp group customerb neighbor 10.255.224.3 peer-as 64911 set routing-instances public-int protocols bgp group customerb neighbor 10.255.226.3 peer-as 64911 delete routing-instances public-int protocols bgp group devices set routing-instances public-int protocols bgp group devices type external set routing-instances public-int protocols bgp group devices family inet unicast set routing-instances public-int protocols bgp group devices multipath multiple-as set routing-instances public-int protocols bgp group devices local-as 64901 set routing-instances public-int protocols bgp group devices hold-time 90 set routing-instances public-int protocols bgp group devices import fabric set routing-instances public-int protocols bgp group devices export internet set routing-instances public-int protocols bgp group devices bfd-liveness-detection minimum-interval 1000 set routing-instances public-int protocols bgp group devices bfd-liveness-detection multiplier 3 set routing-instances public-int protocols bgp group devices bfd-liveness-detection session-mode automatic set routing-instances public-int protocols bgp group devices neighbor 10.255.224.5 peer-as 64911 set routing-instances public-int protocols bgp group devices neighbor 10.255.226.5 peer-as 64911
第二个 WAN 路由器的配置:
set system host-name wanrouter2 delete interfaces ge-0/0/1 set interfaces ge-0/0/1 flexible-vlan-tagging set interfaces ge-0/0/1 mtu 9014 set interfaces ge-0/0/1 unit 1099 description vlan1099 set interfaces ge-0/0/1 unit 1099 vlan-id 1099 set interfaces ge-0/0/1 unit 1099 family inet address 10.255.225.0/31 set interfaces ge-0/0/1 unit 1088 description vlan1088 set interfaces ge-0/0/1 unit 1088 vlan-id 1088 set interfaces ge-0/0/1 unit 1088 family inet address 10.255.225.2/31 set interfaces ge-0/0/1 unit 1033 description vlan1033 set interfaces ge-0/0/1 unit 1033 vlan-id 1033 set interfaces ge-0/0/1 unit 1033 family inet address 10.255.225.4/31 delete interfaces ge-0/0/2 set interfaces ge-0/0/2 flexible-vlan-tagging set interfaces ge-0/0/2 mtu 9014 set interfaces ge-0/0/2 unit 1099 description vlan1099 set interfaces ge-0/0/2 unit 1099 vlan-id 1099 set interfaces ge-0/0/2 unit 1099 family inet address 10.255.227.0/31 set interfaces ge-0/0/2 unit 1088 description vlan1088 set interfaces ge-0/0/2 unit 1088 vlan-id 1088 set interfaces ge-0/0/2 unit 1088 family inet address 10.255.227.2/31 set interfaces ge-0/0/2 unit 1033 description vlan1033 set interfaces ge-0/0/2 unit 1033 vlan-id 1033 set interfaces ge-0/0/2 unit 1033 family inet address 10.255.227.4/31 # needed in and export policy delete policy-options set policy-options policy-statement fabric term 1 from protocol bgp set policy-options policy-statement fabric term 1 from route-filter 0.0.0.0/0 orlonger set policy-options policy-statement fabric term 1 then accept set policy-options policy-statement fabric term 2 then reject set policy-options policy-statement internet term 1 from protocol static set policy-options policy-statement internet term 1 from route-filter 0.0.0.0/0 exact set policy-options policy-statement internet term 1 then accept set policy-options policy-statement internet term 2 then reject delete routing-instances public-int set routing-instances public-int instance-type virtual-router set routing-instances public-int interface ge-0/0/1.1099 set routing-instances public-int interface ge-0/0/1.1088 set routing-instances public-int interface ge-0/0/1.1033 set routing-instances public-int interface ge-0/0/2.1099 set routing-instances public-int interface ge-0/0/2.1088 set routing-instances public-int interface ge-0/0/2.1033 delete routing-instances public-int protocols bgp group customera set routing-instances public-int protocols bgp group customera type external set routing-instances public-int protocols bgp group customera family inet unicast set routing-instances public-int protocols bgp group customera multipath multiple-as set routing-instances public-int protocols bgp group customera local-as 64902 set routing-instances public-int protocols bgp group customera hold-time 90 set routing-instances public-int protocols bgp group customera import fabric set routing-instances public-int protocols bgp group customera export internet set routing-instances public-int protocols bgp group customera bfd-liveness-detection minimum-interval 1000 set routing-instances public-int protocols bgp group customera bfd-liveness-detection multiplier 3 set routing-instances public-int protocols bgp group customera bfd-liveness-detection session-mode automatic set routing-instances public-int protocols bgp group customera neighbor 10.255.225.1 peer-as 64911 set routing-instances public-int protocols bgp group customera neighbor 10.255.227.1 peer-as 64911 delete routing-instances public-int protocols bgp group customerb set routing-instances public-int protocols bgp group customerb type external set routing-instances public-int protocols bgp group customerb family inet unicast set routing-instances public-int protocols bgp group customerb multipath multiple-as set routing-instances public-int protocols bgp group customerb local-as 64902 set routing-instances public-int protocols bgp group customerb hold-time 90 set routing-instances public-int protocols bgp group customerb import fabric set routing-instances public-int protocols bgp group customerb export internet set routing-instances public-int protocols bgp group customerb bfd-liveness-detection minimum-interval 1000 set routing-instances public-int protocols bgp group customerb bfd-liveness-detection multiplier 3 set routing-instances public-int protocols bgp group customerb bfd-liveness-detection session-mode automatic set routing-instances public-int protocols bgp group customerb neighbor 10.255.225.3 peer-as 64911 set routing-instances public-int protocols bgp group customerb neighbor 10.255.227.3 peer-as 64911 delete routing-instances public-int protocols bgp group devices set routing-instances public-int protocols bgp group devices type external set routing-instances public-int protocols bgp group devices family inet unicast set routing-instances public-int protocols bgp group devices multipath multiple-as set routing-instances public-int protocols bgp group devices local-as 64902 set routing-instances public-int protocols bgp group devices hold-time 90 set routing-instances public-int protocols bgp group devices import fabric set routing-instances public-int protocols bgp group devices export internet set routing-instances public-int protocols bgp group devices bfd-liveness-detection minimum-interval 1000 set routing-instances public-int protocols bgp group devices bfd-liveness-detection multiplier 3 set routing-instances public-int protocols bgp group devices bfd-liveness-detection session-mode automatic set routing-instances public-int protocols bgp group devices neighbor 10.255.225.5 peer-as 64911 set routing-instances public-int protocols bgp group devices neighbor 10.255.227.5 peer-as 64911
您可以使用以下 CLI 命令来帮助在 WAN 路由器 1 上进行调试。
root@wanrouter1> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 3 Peers: 6 Down peers: 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.255.224.1 64911 30 27 0 0 11:37 Establ
public-int.inet.0: 2/2/2/0
10.255.224.3 64911 29 27 0 0 11:31 Establ
public-int.inet.0: 2/2/2/0
10.255.224.5 64911 29 27 0 0 11:37 Establ
public-int.inet.0: 1/1/1/0
10.255.226.1 64911 30 27 0 0 11:30 Establ
public-int.inet.0: 2/2/2/0
10.255.226.3 64911 30 27 0 0 11:39 Establ
public-int.inet.0: 2/2/2/0
10.255.226.5 64911 29 27 0 0 11:38 Establ
public-int.inet.0: 1/1/1/0
root@wanrouter1> show route table public-int.inet.0
public-int.inet.0: 23 destinations, 25 routes (23 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:00:42
> to 192.168.230.1 via ge-0/0/0.0
10.88.88.0/24 *[BGP/170] 00:11:47, localpref 100
AS path: 64911 65002 65003 65005 I, validation-state: unverified
to 10.255.224.3 via ge-0/0/1.1081
> to 10.255.226.3 via ge-0/0/2.1081
[BGP/170] 00:11:47, localpref 100
AS path: 64911 65001 65003 65005 I, validation-state: unverified
> to 10.255.224.3 via ge-0/0/1.1081
10.99.99.0/24 *[BGP/170] 00:11:46, localpref 100, from 10.255.224.1
AS path: 64911 65001 65003 65005 I, validation-state: unverified
to 10.255.224.1 via ge-0/0/1.1091
> to 10.255.226.1 via ge-0/0/2.1091
[BGP/170] 00:11:46, localpref 100
AS path: 64911 65002 65003 65005 I, validation-state: unverified
> to 10.255.226.1 via ge-0/0/2.1091
10.255.224.0/31 *[Direct/0] 00:22:31
> via ge-0/0/1.1091
10.255.224.0/32 *[Local/0] 00:22:31
Local via ge-0/0/1.1091
10.255.224.2/31 *[Direct/0] 00:22:31
> via ge-0/0/1.1081
10.255.224.2/32 *[Local/0] 00:22:31
Local via ge-0/0/1.1081
10.255.224.4/31 *[Direct/0] 00:22:31
> via ge-0/0/1.1031
10.255.224.4/32 *[Local/0] 00:22:31
Local via ge-0/0/1.1031
10.255.226.0/31 *[Direct/0] 00:22:31
> via ge-0/0/2.1091
10.255.226.0/32 *[Local/0] 00:22:31
Local via ge-0/0/2.1091
10.255.226.2/31 *[Direct/0] 00:22:31
> via ge-0/0/2.1081
10.255.226.2/32 *[Local/0] 00:22:31
Local via ge-0/0/2.1081
10.255.226.4/31 *[Direct/0] 00:22:31
> via ge-0/0/2.1031
10.255.226.4/32 *[Local/0] 00:22:31
Local via ge-0/0/2.1031
172.16.193.1/32 *[BGP/170] 00:11:53, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.224.1 via ge-0/0/1.1091
172.16.193.2/32 *[BGP/170] 00:11:46, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.226.1 via ge-0/0/2.1091
172.16.194.1/32 *[BGP/170] 00:11:47, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.224.3 via ge-0/0/1.1081
172.16.194.2/32 *[BGP/170] 00:11:55, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.226.3 via ge-0/0/2.1081
172.16.195.1/32 *[BGP/170] 00:11:53, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.224.5 via ge-0/0/1.1031
172.16.195.2/32 *[BGP/170] 00:11:54, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.226.5 via ge-0/0/2.1031
192.168.230.0/24 *[Direct/0] 00:01:08
> via ge-0/0/0.0
192.168.230.99/32 *[Local/0] 00:01:08
Local via ge-0/0/0.0
您可以使用以下 CLI 命令来帮助在 WAN 路由器上进行调试2。
root@wanrouter2> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 3 Peers: 6 Down peers: 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.255.225.1 64911 36 33 0 0 14:29 Establ
public-int.inet.0: 2/2/2/0
10.255.225.3 64911 36 33 0 0 14:21 Establ
public-int.inet.0: 2/2/2/0
10.255.225.5 64911 35 34 0 0 14:31 Establ
public-int.inet.0: 1/1/1/0
10.255.227.1 64911 36 34 0 0 14:35 Establ
public-int.inet.0: 2/2/2/0
10.255.227.3 64911 36 34 0 0 14:35 Establ
public-int.inet.0: 2/2/2/0
10.255.227.5 64911 34 33 0 0 14:21 Establ
public-int.inet.0: 1/1/1/0
root@wanrouter2> show route table public-int.inet.0
public-int.inet.0: 23 destinations, 25 routes (23 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:00:24
> to 192.168.230.1 via ge-0/0/0.0
10.88.88.0/24 *[BGP/170] 00:14:35, localpref 100
AS path: 64911 65002 65003 65005 I, validation-state: unverified
to 10.255.225.3 via ge-0/0/1.1088
> to 10.255.227.3 via ge-0/0/2.1088
[BGP/170] 00:14:35, localpref 100
AS path: 64911 65001 65003 65005 I, validation-state: unverified
> to 10.255.225.3 via ge-0/0/1.1088
10.99.99.0/24 *[BGP/170] 00:14:43, localpref 100
AS path: 64911 65002 65003 65005 I, validation-state: unverified
to 10.255.225.1 via ge-0/0/1.1099
> to 10.255.227.1 via ge-0/0/2.1099
[BGP/170] 00:14:43, localpref 100
AS path: 64911 65001 65003 65005 I, validation-state: unverified
> to 10.255.225.1 via ge-0/0/1.1099
10.255.225.0/31 *[Direct/0] 00:25:19
> via ge-0/0/1.1099
10.255.225.0/32 *[Local/0] 00:25:19
Local via ge-0/0/1.1099
10.255.225.2/31 *[Direct/0] 00:25:19
> via ge-0/0/1.1088
10.255.225.2/32 *[Local/0] 00:25:19
Local via ge-0/0/1.1088
10.255.225.4/31 *[Direct/0] 00:25:19
> via ge-0/0/1.1033
10.255.225.4/32 *[Local/0] 00:25:19
Local via ge-0/0/1.1033
10.255.227.0/31 *[Direct/0] 00:25:19
> via ge-0/0/2.1099
10.255.227.0/32 *[Local/0] 00:25:19
Local via ge-0/0/2.1099
10.255.227.2/31 *[Direct/0] 00:25:19
> via ge-0/0/2.1088
10.255.227.2/32 *[Local/0] 00:25:19
Local via ge-0/0/2.1088
10.255.227.4/31 *[Direct/0] 00:25:19
> via ge-0/0/2.1033
10.255.227.4/32 *[Local/0] 00:25:19
Local via ge-0/0/2.1033
172.16.193.1/32 *[BGP/170] 00:14:43, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.225.1 via ge-0/0/1.1099
172.16.193.2/32 *[BGP/170] 00:14:49, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.227.1 via ge-0/0/2.1099
172.16.194.1/32 *[BGP/170] 00:14:35, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.225.3 via ge-0/0/1.1088
172.16.194.2/32 *[BGP/170] 00:14:49, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.227.3 via ge-0/0/2.1088
172.16.195.1/32 *[BGP/170] 00:14:45, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.225.5 via ge-0/0/1.1033
172.16.195.2/32 *[BGP/170] 00:14:35, localpref 100
AS path: 64911 I, validation-state: unverified
> to 10.255.227.5 via ge-0/0/2.1033
192.168.230.0/24 *[Direct/0] 00:00:24
> via ge-0/0/0.0
192.168.230.98/32 *[Local/0] 00:00:24
Local via ge-0/0/0.0
瞻博网络 SRX 系列防火墙作为 WAN 路由器
以下示例表和配置显示了在群集模式下使用 SRX 系列防火墙与将 MX 路由器用作 WAN 路由器之间的区别。在结构端,只有 SRX 集群的接口名称与 MX 路由器配置不同。由于 SRX 系列防火墙在主动/主动群集模式下运行,因此需要考虑只有一个 WAN 路由器配置和一个 ASN。该单一配置还包括群集管理和信任区域管理命令,这些命令在基于 MX 路由器的类似配置中不存在。
这种基于 SRX 系列防火墙的方法比在 MX 路由器上配置冗余以太网 (reth) 接口和链路聚合组 (LAG) 要简单得多。此外,结构端还需要额外的 CLI 来插入虚拟网关等。
表 2 显示了作为服务块功能的 core1 和 core2 交换机的配置信息,以及 SRX 群集的 WAN 路由器配置。我们已根据表 1 (对于 MX WAN 路由器,以粗体显示)标记了更改。
| 交换机 | 交换机 AS | VRF | 核心 P2P IP | 核心 | IF WAN 路由器 WAN | 路由器 P2P IP | WAN 路由器 AS | WAN 路由器 IF | VLAN ID |
|---|---|---|---|---|---|---|---|---|---|
| 核心1 | 64911 | 客户a | 10.255.224.1/31 | ge-0/0/5.1091 | 节点0 | 10.255.224.0/31 | 64901 | ge-0/0/2.1091 | 1091 |
| 核心1 | 64911 | 客户b | 10.255.224.3/31 | ge-0/0/5.1081 | 节点0 | 10.255.224.2/31 | 64901 | ge-0/0/2.1081 | 1081 |
| 核心1 | 64911 | 设备 | 10.255.224.5/31 | ge-0/0/5.1031 | 节点0 | 10.255.224.4/31 | 64901 | ge-0/0/2.1031 | 1031 |
| 核心1 | 64911 | 客户a | 10.255.225.1/31 | ge-0/0/6.1099 | 节点 1 | 10.255.225.0/31 | 64901 | ge-7/0/2.1099 | 1099 |
| 核心1 | 64911 | 客户b | 10.255.225.3/31 | ge-0/0/6.1088 | 节点 1 | 10.255.225.2/31 | 64901 | ge-7/0/2.1088 | 1088 |
| 核心1 | 64911 | 设备 | 10.255.225.5/31 | ge-0/0/6.1033 | 节点 1 | 10.255.225.4/31 | 64901 | ge-7/0/2.1033 | 1033 |
| 核心2 | 64911 | 客户a | 10.255.226.1/31 | ge-0/0/5.1091 | 节点0 | 10.255.226.0/31 | 64901 | ge-0/0/3.1091 | 1091 |
| 核心2 | 64911 | 客户b | 10.255.226.3/31 | ge-0/0/5.1081 | 节点0 | 10.255.226.2/31 | 64901 | ge-0/0/3.1081 | 1081 |
| 核心2 | 64911 | 设备 | 10.255.226.5/31 | ge-0/0/5.1031 | 节点0 | 10.255.226.4/31 | 64901 | ge-0/0/3.1031 | 1031 |
| 核心2 | 64911 | 客户a | 10.255.227.1/31 | ge-0/0/6.1099 | 节点 1 | 10.255.227.0/31 | 64901 | ge-7/0/3.1099 | 1099 |
| 核心2 | 64911 | 客户b | 10.255.227.3/31 | ge-0/0/6.1088 | 节点 1 | 10.255.227.2/31 | 64901 | ge-7/0/3.1088 | 1088 |
| 核心2 | 64911 | 设备 | 10.255.227.5/31 | ge-0/0/6.1033 | 节点 1 | 10.255.227.4/31 | 64901 | ge-7/0/3.1033 | 1033 |
以下伪代码描述了此示例中需要在 core1 交换机上配置的内容:
# configure the Additional IP-Subnet 10.255.224.1 255.255.255.254 to Network/VLAN:vlan1091 # configure the Additional IP-Subnet 10.255.224.3 255.255.255.254 to Network/VLAN:vlan1081 # configure the Additional IP-Subnet 10.255.224.5 255.255.255.254 to Network/VLAN:vlan1031 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/5 as L3-Sub-Interfaces with MTU=9018 # configure the Additional IP-Subnet 10.255.225.1 255.255.255.254 to Network/VLAN:vlan1099 # configure the Additional IP-Subnet 10.255.225.3 255.255.255.254 to Network/VLAN:vlan1088 # configure the Additional IP-Subnet 10.255.225.5 255.255.255.254 to Network/VLAN:vlan1033 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/6 as L3-Sub-Interfaces with MTU=9018 # Enable BGP and create an Export policy called 'export-vrfs' # Add to this export Policy the following Networks as: # - Add Term w. Name=vlan1091 Prefix=10.99.91.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1099 Prefix=10.99.99.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1081 Prefix=10.88.81.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1088 Prefix=10.88.88.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1031 Prefix=10.33.31.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1033 Prefix=10.33.33.0/24 Protocol=None Then=Accept # - Add Term w. Name=overlaylo0 Prefix=172.16.192.0/19-32 Protocol=None Then=Accept # Create an Export policy called 'import-default' # - Name=default Prefix=0.0.0.0/0 Protocol=BGP Action=Accept # Create a BGP Group with: # - Name=customera0 # - Type=External # - Network (VLAN)=vlan1091 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.224.1 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customerb0 # - Type=External # - Network (VLAN)=vlan1081 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.224.3 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=devices0 # - Type=External # - Network (VLAN)=vlan1031 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.224.5 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customera1 # - Type=External # - Network (VLAN)=vlan1099 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.225.1 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customerb1 # - Type=External # - Network (VLAN)=vlan1088 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.225.3 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=devices1 # - Type=External # - Network (VLAN)=vlan1033 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.225.5 Neighbor_AS=64901 Hold-Time=90
以下伪代码描述了此示例中需要在 core2 交换机上配置的内容:
# configure the Additional IP-Subnet 10.255.226.1 255.255.255.254 to Network/VLAN:vlan1091 # configure the Additional IP-Subnet 10.255.226.3 255.255.255.254 to Network/VLAN:vlan1081 # configure the Additional IP-Subnet 10.255.226.5 255.255.255.254 to Network/VLAN:vlan1031 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/5 as L3-Sub-Interfaces with MTU=9018 # configure the Additional IP-Subnet 10.255.227.1 255.255.255.254 to Network/VLAN:vlan1099 # configure the Additional IP-Subnet 10.255.227.3 255.255.255.254 to Network/VLAN:vlan1088 # configure the Additional IP-Subnet 10.255.227.5 255.255.255.254 to Network/VLAN:vlan1033 # Then bind these 3 Network/VLANs to Port Interface ge-0/0/6 as L3-Sub-Interfaces with MTU=9018 # Enable BGP and create an Export policy called 'export-vrfs' # Add to this export Policy the following Networks as: # - Add Term w. Name=vlan1091 Prefix=10.99.91.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1099 Prefix=10.99.99.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1081 Prefix=10.88.81.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1088 Prefix=10.88.88.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1031 Prefix=10.33.31.0/24 Protocol=None Then=Accept # - Add Term w. Name=vlan1033 Prefix=10.33.33.0/24 Protocol=None Then=Accept # - Add Term w. Name=overlaylo0 Prefix=172.16.192.0/19-32 Protocol=None Then=Accept # Create an Export policy called 'import-default' # - Name=default Prefix=0.0.0.0/0 Protocol=BGP Action=Accept # Create a BGP Group with: # - Name=customera0 # - Type=External # - Network (VLAN)=vlan1091 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.226.1 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customerb0 # - Type=External # - Network (VLAN)=vlan1081 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.226.3 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=devices0 # - Type=External # - Network (VLAN)=vlan1031 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.226.5 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customera1 # - Type=External # - Network (VLAN)=vlan1099 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.227.1 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=customerb1 # - Type=External # - Network (VLAN)=vlan1088 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.227.3 Neighbor_AS=64901 Hold-Time=90 # Create a BGP Group with: # - Name=devices1 # - Type=External # - Network (VLAN)=vlan1033 # - BFD interval=1000 # - Local AS=64911 # - Hold Time=90 # - Set Export=export-vrfs and Import=import-default # Add also the following Neighbor # - IP_Address=10.255.227.5 Neighbor_AS=64901 Hold-Time=90
配置完各个服务块功能(此处为 core1 和 core2 交换机)后,概览表应如图 46 所示。
图 46 概述了在为 core1 和 core2 交换机配置了各个服务块功能后,BGP 的外观。
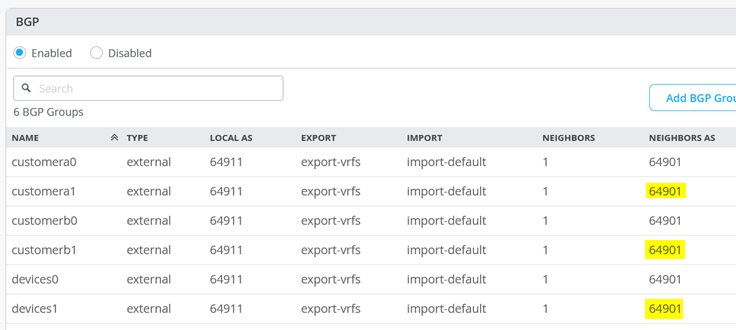 的 BGP 配置摘要
的 BGP 配置摘要
以下 Junos OS CLI 表示此示例中系列防火墙群集上所需的全部配置。
set groups node0 system host-name srx1_node0
set groups node1 system host-name srx2_node1
set apply-groups "${node}"
set chassis aggregated-devices ethernet device-count 10
set chassis cluster control-link-recovery
set chassis cluster reth-count 5
set chassis cluster initial-hold 60
set chassis cluster redundancy-group 1 node 0 priority 200
set chassis cluster redundancy-group 1 node 1 priority 100
set chassis cluster redundancy-group 1 gratuitous-arp-count 4
# Interface monitoring turned OFF for vSRX
# set chassis cluster redundancy-group 1 interface-monitor ge-0/0/2 weight 255
# set chassis cluster redundancy-group 1 interface-monitor ge-0/0/3 weight 255
# set chassis cluster redundancy-group 1 interface-monitor ge-7/0/2 weight 255
# set chassis cluster redundancy-group 1 interface-monitor ge-7/0/3 weight 255
set interfaces fab0 fabric-options member-interfaces ge-0/0/0
set interfaces fab1 fabric-options member-interfaces ge-7/0/0
# rebuild trust zone to clear old interfaces bound
delete security zones security-zone trust
set security zones security-zone trust tcp-rst
set security zones security-zone trust host-inbound-traffic system-services all
set security zones security-zone trust host-inbound-traffic protocols all
delete interfaces ge-0/0/2
set interfaces ge-0/0/2 flexible-vlan-tagging
set interfaces ge-0/0/2 mtu 9018
set interfaces ge-0/0/2 unit 1091 description vlan1091
set interfaces ge-0/0/2 unit 1091 vlan-id 1091
set interfaces ge-0/0/2 unit 1091 family inet address 10.255.224.0/31
set security zones security-zone trust interfaces ge-0/0/2.1091 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-0/0/2.1091 host-inbound-traffic system-services ping
set interfaces ge-0/0/2 unit 1081 description vlan1081
set interfaces ge-0/0/2 unit 1081 vlan-id 1081
set interfaces ge-0/0/2 unit 1081 family inet address 10.255.224.2/31
set security zones security-zone trust interfaces ge-0/0/2.1081 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-0/0/2.1081 host-inbound-traffic system-services ping
set interfaces ge-0/0/2 unit 1031 description vlan1031
set interfaces ge-0/0/2 unit 1031 vlan-id 1031
set interfaces ge-0/0/2 unit 1031 family inet address 10.255.224.4/31
set security zones security-zone trust interfaces ge-0/0/2.1031 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-0/0/2.1031 host-inbound-traffic system-services ping
delete interfaces ge-0/0/3
set interfaces ge-0/0/3 flexible-vlan-tagging
set interfaces ge-0/0/3 mtu 9018
set interfaces ge-0/0/3 unit 1091 description vlan1091
set interfaces ge-0/0/3 unit 1091 vlan-id 1091
set interfaces ge-0/0/3 unit 1091 family inet address 10.255.226.0/31
set security zones security-zone trust interfaces ge-0/0/3.1091 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-0/0/3.1091 host-inbound-traffic system-services ping
set interfaces ge-0/0/3 unit 1081 description vlan1081
set interfaces ge-0/0/3 unit 1081 vlan-id 1081
set interfaces ge-0/0/3 unit 1081 family inet address 10.255.226.2/31
set security zones security-zone trust interfaces ge-0/0/3.1081 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-0/0/3.1081 host-inbound-traffic system-services ping
set interfaces ge-0/0/3 unit 1031 description vlan1031
set interfaces ge-0/0/3 unit 1031 vlan-id 1031
set interfaces ge-0/0/3 unit 1031 family inet address 10.255.226.4/31
set security zones security-zone trust interfaces ge-0/0/3.1031 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-0/0/3.1031 host-inbound-traffic system-services ping
delete interfaces ge-7/0/2
set interfaces ge-7/0/2 flexible-vlan-tagging
set interfaces ge-7/0/2 mtu 9018
set interfaces ge-7/0/2 unit 1099 description vlan1099
set interfaces ge-7/0/2 unit 1099 vlan-id 1099
set interfaces ge-7/0/2 unit 1099 family inet address 10.255.225.0/31
set security zones security-zone trust interfaces ge-7/0/2.1099 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-7/0/2.1099 host-inbound-traffic system-services ping
set interfaces ge-7/0/2 unit 1088 description vlan1088
set interfaces ge-7/0/2 unit 1088 vlan-id 1088
set interfaces ge-7/0/2 unit 1088 family inet address 10.255.225.2/31
set security zones security-zone trust interfaces ge-7/0/2.1088 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-7/0/2.1088 host-inbound-traffic system-services ping
set interfaces ge-7/0/2 unit 1033 description vlan1033
set interfaces ge-7/0/2 unit 1033 vlan-id 1033
set interfaces ge-7/0/2 unit 1033 family inet address 10.255.225.4/31
set security zones security-zone trust interfaces ge-7/0/2.1033 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-7/0/2.1033 host-inbound-traffic system-services ping
delete interfaces ge-7/0/3
set interfaces ge-7/0/3 flexible-vlan-tagging
set interfaces ge-7/0/3 mtu 9018
set interfaces ge-7/0/3 unit 1099 description vlan1099
set interfaces ge-7/0/3 unit 1099 vlan-id 1099
set interfaces ge-7/0/3 unit 1099 family inet address 10.255.227.0/31
set security zones security-zone trust interfaces ge-7/0/3.1099 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-7/0/3.1099 host-inbound-traffic system-services ping
set interfaces ge-7/0/3 unit 1088 description vlan1088
set interfaces ge-7/0/3 unit 1088 vlan-id 1088
set interfaces ge-7/0/3 unit 1088 family inet address 10.255.227.2/31
set security zones security-zone trust interfaces ge-7/0/3.1088 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-7/0/3.1088 host-inbound-traffic system-services ping
set interfaces ge-7/0/3 unit 1033 description vlan1033
set interfaces ge-7/0/3 unit 1033 vlan-id 1033
set interfaces ge-7/0/3 unit 1033 family inet address 10.255.227.4/31
set security zones security-zone trust interfaces ge-7/0/3.1033 host-inbound-traffic protocols bgp
set security zones security-zone trust interfaces ge-7/0/3.1033 host-inbound-traffic system-services ping
# needed in and export policy
delete policy-options
set policy-options policy-statement fabric term 1 from protocol bgp
set policy-options policy-statement fabric term 1 from route-filter 0.0.0.0/0 orlonger
set policy-options policy-statement fabric term 1 then accept
set policy-options policy-statement fabric term 2 then reject
set policy-options policy-statement internet term 1 from protocol static
set policy-options policy-statement internet term 1 from route-filter 0.0.0.0/0 exact
set policy-options policy-statement internet term 1 then accept
set policy-options policy-statement internet term 2 then reject
delete routing-instances public-int
set routing-instances public-int instance-type virtual-router
set routing-instances public-int interface ge-0/0/2.1091
set routing-instances public-int interface ge-0/0/2.1081
set routing-instances public-int interface ge-0/0/2.1031
set routing-instances public-int interface ge-0/0/3.1091
set routing-instances public-int interface ge-0/0/3.1081
set routing-instances public-int interface ge-0/0/3.1031
set routing-instances public-int interface ge-7/0/2.1099
set routing-instances public-int interface ge-7/0/2.1088
set routing-instances public-int interface ge-7/0/2.1033
set routing-instances public-int interface ge-7/0/3.1099
set routing-instances public-int interface ge-7/0/3.1088
set routing-instances public-int interface ge-7/0/3.1033
delete routing-instances public-int protocols bgp group customera
set routing-instances public-int protocols bgp group customera type external
set routing-instances public-int protocols bgp group customera family inet unicast
set routing-instances public-int protocols bgp group customera multipath multiple-as
set routing-instances public-int protocols bgp group customera local-as 64901
set routing-instances public-int protocols bgp group customera hold-time 90
set routing-instances public-int protocols bgp group customera import fabric
set routing-instances public-int protocols bgp group customera export internet
set routing-instances public-int protocols bgp group customera bfd-liveness-detection minimum-interval 1000
set routing-instances public-int protocols bgp group customera bfd-liveness-detection multiplier 3
set routing-instances public-int protocols bgp group customera bfd-liveness-detection session-mode automatic
set routing-instances public-int protocols bgp group customera neighbor 10.255.224.1 peer-as 64911
set routing-instances public-int protocols bgp group customera neighbor 10.255.226.1 peer-as 64911
set routing-instances public-int protocols bgp group customera neighbor 10.255.225.1 peer-as 64911
set routing-instances public-int protocols bgp group customera neighbor 10.255.227.1 peer-as 64911
delete routing-instances public-int protocols bgp group customerb
set routing-instances public-int protocols bgp group customerb type external
set routing-instances public-int protocols bgp group customerb family inet unicast
set routing-instances public-int protocols bgp group customerb multipath multiple-as
set routing-instances public-int protocols bgp group customerb local-as 64901
set routing-instances public-int protocols bgp group customerb hold-time 90
set routing-instances public-int protocols bgp group customerb import fabric
set routing-instances public-int protocols bgp group customerb export internet
set routing-instances public-int protocols bgp group customerb bfd-liveness-detection minimum-interval 1000
set routing-instances public-int protocols bgp group customerb bfd-liveness-detection multiplier 3
set routing-instances public-int protocols bgp group customerb bfd-liveness-detection session-mode automatic
set routing-instances public-int protocols bgp group customerb neighbor 10.255.224.3 peer-as 64911
set routing-instances public-int protocols bgp group customerb neighbor 10.255.226.3 peer-as 64911
set routing-instances public-int protocols bgp group customerb neighbor 10.255.225.3 peer-as 64911
set routing-instances public-int protocols bgp group customerb neighbor 10.255.227.3 peer-as 64911
delete routing-instances public-int protocols bgp group devices
set routing-instances public-int protocols bgp group devices type external
set routing-instances public-int protocols bgp group devices family inet unicast
set routing-instances public-int protocols bgp group devices multipath multiple-as
set routing-instances public-int protocols bgp group devices local-as 64901
set routing-instances public-int protocols bgp group devices hold-time 90
set routing-instances public-int protocols bgp group devices import fabric
set routing-instances public-int protocols bgp group devices export internet
set routing-instances public-int protocols bgp group devices bfd-liveness-detection minimum-interval 1000
set routing-instances public-int protocols bgp group devices bfd-liveness-detection multiplier 3
set routing-instances public-int protocols bgp group devices bfd-liveness-detection session-mode automatic
set routing-instances public-int protocols bgp group devices neighbor 10.255.224.5 peer-as 64911
set routing-instances public-int protocols bgp group devices neighbor 10.255.226.5 peer-as 64911
set routing-instances public-int protocols bgp group devices neighbor 10.255.225.5 peer-as 64911
set routing-instances public-int protocols bgp group devices neighbor 10.255.227.5 peer-as 64911
