本页内容
示例:为对等证书链验证配置设备
此示例说明如何为用于在 IKE 协商期间验证对等设备的证书链配置设备。
要求
开始之前,在提交本地证书请求时,获取证书颁发机构 (CA) 的地址及其所需的信息(如质询密码)。
概述
此示例说明如何为证书链配置本地设备,注册 CA 和本地证书,检查注册证书的有效性,以及检查对等设备的撤销状态。
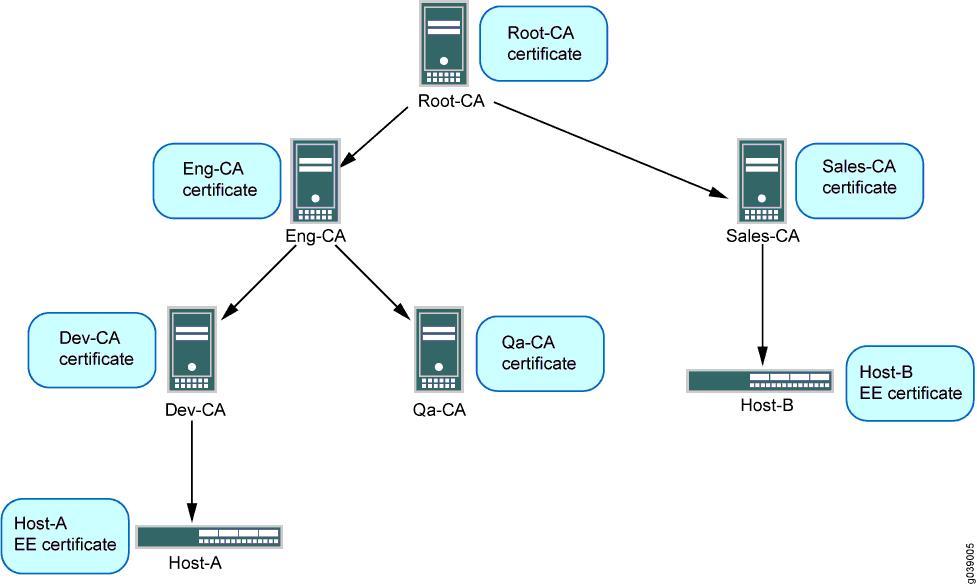
拓扑
此示例显示了 Host-A 上的配置和操作命令,如图 1 所示。系统会自动在 Host-A 上创建动态 CA 配置文件,以允许 Host-A 从 Sales-CA 下载 CRL 并检查 Host-B 证书的撤销状态。
此示例显示了主机 A 的第 1 阶段和第 2 阶段协商的 IPsec VPN 配置。必须正确配置对等设备 (Host-B),以便成功协商第 1 阶段和第 2 阶段选项并建立安全关联 (SA)。
配置
要为证书链配置设备:
配置 CA 配置文件
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层级的 [edit] CLI 中,然后从配置模式进入 commit 。
set security pki ca-profile Root-CA ca-identity CA-Root set security pki ca-profile Root-CA enrollment url http://10.157.88.230:8080/scep/Root/ set security pki ca-profile Root-CA revocation-check use-crl set security pki ca-profile Eng-CA ca-identity Eng-CA set security pki ca-profile Eng-CA enrollment url http://10.157.88.230:8080/scep/Eng/ set security pki ca-profile Eng-CA revocation-check use-crl set security pki ca-profile Dev-CA ca-identity Dev-CA set security pki ca-profile Dev-CA enrollment url http://10.157.88.230:8080/scep/Dev/ set security pki ca-profile Dev-CA revocation-check use-crl
逐步过程
以下示例要求您在配置层次结构中的各个级别上导航。有关如何操作的说明,请参阅 CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要配置 CA 配置文件:
为 Root-CA 创建 CA 配置文件。
[edit security pki] user@host# set ca-profile Root-CA ca-identity CA-Root user@host# set ca-profile Root-CA enrollment url http://10.157.88.230:8080/scep/Root/ user@host# set ca-profile Root-CA revocation-check use-crl
创建 Eng-CA 的 CA 配置文件。
[edit security pki] user@host# set ca-profile Eng-CA ca-identity Eng-CA user@host# set ca-profile Eng-CA enrollment url http://10.157.88.230:8080/scep/Eng/ user@host# set ca-profile Eng-CA revocation-check use-crl
创建 Dev-CA 的 CA 配置文件。
[edit security pki] user@host# set ca-profile Dev-CA ca-identity Dev-CA user@host# set ca-profile Dev-CA enrollment url http://10.157.88.230:8080/scep/Dev/ user@host# set ca-profile Dev-CA revocation-check use-crl
结果
在配置模式下,输入命令以确认 show security pki 您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url "http:/;/10.157.88.230:8080/scep/Root/";
}
revocation-check {
use-crl;
}
}
ca-profile Eng-CA {
ca-identity Eng-CA;
enrollment {
url "http:/;/10.157.88.230:8080/scep/Eng/";
}
revocation-check {
use-crl;
}
}
ca-profile Dev-CA {
ca-identity Dev-CA;
enrollment {
url "http:/;/10.157.88.230:8080/scep/Dev/";
}
revocation-check {
use-crl;
}
}
完成设备配置后,请从配置模式进入 commit 。
注册证书
逐步过程
要注册证书:
注册 CA 证书。
user@host> request security pki ca-certificate enroll ca-profile Root-CA
user@host> request security pki ca-certificate enroll ca-profile Eng-CA
user@host> request security pki ca-certificate enroll ca-profile Dev-CA
提示时键入 yes 以加载 CA 证书。
验证设备中是否已注册 CA 证书。
user@host> show security pki ca-certificate ca-profile Root-CA Certificate identifier: Root-CA Issued to: Root-CA, Issued by: C = us, O = juniper, CN = Root-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(2048 bits)user@host> show security pki ca-certificate ca-profile Eng-CA Certificate identifier: Eng-CA Issued to: Eng-CA, Issued by: C = us, O = juniper, CN = Root-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(2048 bits)user@host> show security pki ca-certificate ca-profile Dev-CA Certificate identifier: Dev-CA Issued to: Dev-CA, Issued by: C = us, O = juniper, CN = Eng-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(2048 bits)验证注册的 CA 证书的有效性。
user@host> request security pki ca-certificate verify ca-profile Root-CA CA certificate Root-CA verified successfully
user@host> request security pki ca-certificate verify ca-profile Eng-CA CA certificate Eng-CA verified successfully
user@host> request security pki ca-certificate verify ca-profile Dev-CA CA certificate Dev-CA verified successfully
注册本地证书。
user@host> request security pki local-certificate enroll certificate-id Host-A ca-profile Dev-CA challenge-password juniper domain-name host-a.company.net email host-a@company.net subject DC=juniper,CN=Host-A, OU=DEV,O=PKI,L=Sunnyvale,ST=CA,C=US
验证设备中是否已注册本地证书。
user@host> show security pki local-certificate Issued to: Host-A, Issued by: C = us, O = juniper, CN = Dev-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(1024 bits)验证注册的本地证书的有效性。
user@host> request security pki local-certificate verify certificate-id Host-A Local certificate Host-A verification success
检查 CRL 下载中配置的 CA 配置文件。
user@host> show security pki crl CA profile: Root-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Root-CA Effective date: 09- 9-2015 13:08 Next update: 09-21-2015 02:55 CA profile: Eng-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Eng-CA Effective date: 08-22-2015 17:46 Next update: 10-24-2015 03:33 CA profile: Dev-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Dev-CA Effective date: 09-14-2015 21:15 Next update: 09-26-2012 11:02
配置 IPsec VPN 选项
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层级的 [edit] CLI 中,然后从配置模式进入 commit 。
set services ipsec-vpn ike proposal ike_cert_prop_01 authentication-method rsa-signatures set services ipsec-vpn ike proposal ike_cert_prop_01 dh-group group5 set services ipsec-vpn ike proposal ike_cert_prop_01 authentication-algorithm sha1 set services ipsec-vpn ike proposal ike_cert_prop_01 encryption-algorithm aes-256-cbc set services ipsec-vpn ike policy ike_cert_pol_01 mode main set services ipsec-vpn ike policy ike_cert_pol_01 proposals ike_cert_prop_01 set services ipsec-vpn ike policy ike_cert_pol_01 certificate local-certificate Host-A set services ipsec-vpn ipsec proposal ipsec_prop_01 protocol esp set services ipsec-vpn ipsec proposal ipsec_prop_01 authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec_prop_01 encryption-algorithm 3des-cbc set services ipsec-vpn ipsec proposal ipsec_prop_01 lifetime-seconds 300 set services ipsec-vpn ipsec policy ipsec_pol_01 proposals ipsec_prop_01 set services ipsec-vpn ipsec vpn ipsec_cert_vpn_01 ike ipsec-policy ipsec_pol_01
逐步过程
以下示例要求您在配置层次结构中的各个级别上导航。有关如何操作的说明,请参阅 CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要配置 IPsec VPN 选项:
配置第 1 阶段选项。
[edit services ipsec-vpn ike proposal ike_cert_prop_01] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit services ipsec-vpn ike policy ike_cert_pol_01] user@host# set mode main user@host# set proposals ike_cert_prop_01 user@host# set certificate local-certificate Host-A
配置第 2 阶段选项。
[edit services ipsec-vpn ipsec proposal ipsec_prop_01] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm 3des-cbc user@host# set lifetime-seconds 300 [edit services ipsec-vpn ipsec policy ipsec_pol_01] user@host# set proposals ipsec_prop_01 [edit services ipsec-vpn ipsec vpn ipsec_cert_vpn_01] user@host# set ike ipsec-policy ipsec_pol_01
结果
在配置模式下,输入和 show security ipsec 命令以确认show security ike您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show services ipsec-vpn ike
proposal ike_cert_prop_01 {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy ike_cert_pol_01 {
mode main;
proposals ike_cert_prop_01;
certificate {
local-certificate Host-A;
}
}
[edit]
user@host# show services ipsec-vpn ipsec
proposal ipsec_prop_01 {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 300;
}
policy ipsec_pol_01 {
proposals ipsec_prop_01;
}
完成设备配置后,请从配置模式进入 commit 。
验证
如果在对等设备之间的 IKE 协商期间证书验证成功,将同时建立 IKE 和 IPsec 安全关联 (SA)。
验证 IKE 第 1 阶段状态
目的
验证 IKE 第 1 阶段状态。
行动
在 show services ipsec-vpn ike security-associations 操作模式下输入命令。
user@host> show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 192.0.2.0 Matured 63b3445edda507fb 2715ee5895ed244d Main
验证 IPsec 第 2 阶段状态
目的
验证 IPsec 第 2 阶段状态。
行动
在 show services ipsec-vpn ipsec security-associations 操作模式下输入命令。
user@host> show services ipsec-vpn ipsec security-associations
Service set: ips_ss1, IKE Routing-instance: default
Rule: vpn_rule_ms_2_2_01, Term: term11, Tunnel index: 1
Local gateway: 10.0.1.2, Remote gateway: 172.16.0.0
IPSec inside interface: ms-2/2/0.1, Tunnel MTU: 1500
UDP encapsulate: Disabled, UDP Destination port: 0
Direction SPI AUX-SPI Mode Type Protocol
inbound 2151932129 0 tunnel dynamic ESP
outbound 4169263669 0 tunnel dynamic ESP
已撤销证书的 IKE 和 IPsec SA 故障
检查撤销的证书
问题
如果在对等设备之间的 IKE 协商期间证书验证失败,请检查以确保对等方证书是否已被撤销。动态 CA 配置文件允许本地设备从对等方 CA 下载 CRL 并检查对等方证书的撤销状态。要启用动态 CA 配置文件, revocation-check crl 必须在父 CA 配置文件上配置选项。
解决 方案
检查对等方证书的撤销状态:
通过从操作模式输入 show security pki crl 命令,识别显示对等设备的 CRL 的动态 CA 配置文件。
user@host> show security pki crl CA profile: Root-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Root-CA Effective date: 09- 9-2012 13:08 Next update: 09-21-2012 02:55 CA profile: Eng-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Eng-CA Effective date: 08-22-2012 17:46 Next update: 10-24-2015 03:33 CA profile: Dev-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Dev-CA Effective date: 09-14-2012 21:15 Next update: 09-26-2012 11:02 CA profile: dynamic-001 CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Sales-CA Effective date: 09-14-2012 21:15 Next update: 09-26-2012 11:02会在主机 A 上自动创建 CA 配置文件
dynamic-001,以便 Host-A 可以从主机 B 的 CA (Sales-CA) 下载 CRL 并检查对等方证书的撤销状态。从操作模式输入命令,显示动态 CA 配置文件的 show security pki crl ca-profile dynamic-001 detail CRL 信息。
进入
user@host> show security pki crl ca-profile dynamic-001 detail CA profile: dynamic-001 CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Sub11 Effective date: 09-19-2012 17:29 Next update: 09-20-2012 01:49 Revocation List: Serial number Revocation date 10647C84 09-19-2012 17:29 UTCHost-B 的证书(序列号 10647084)已被撤销。
