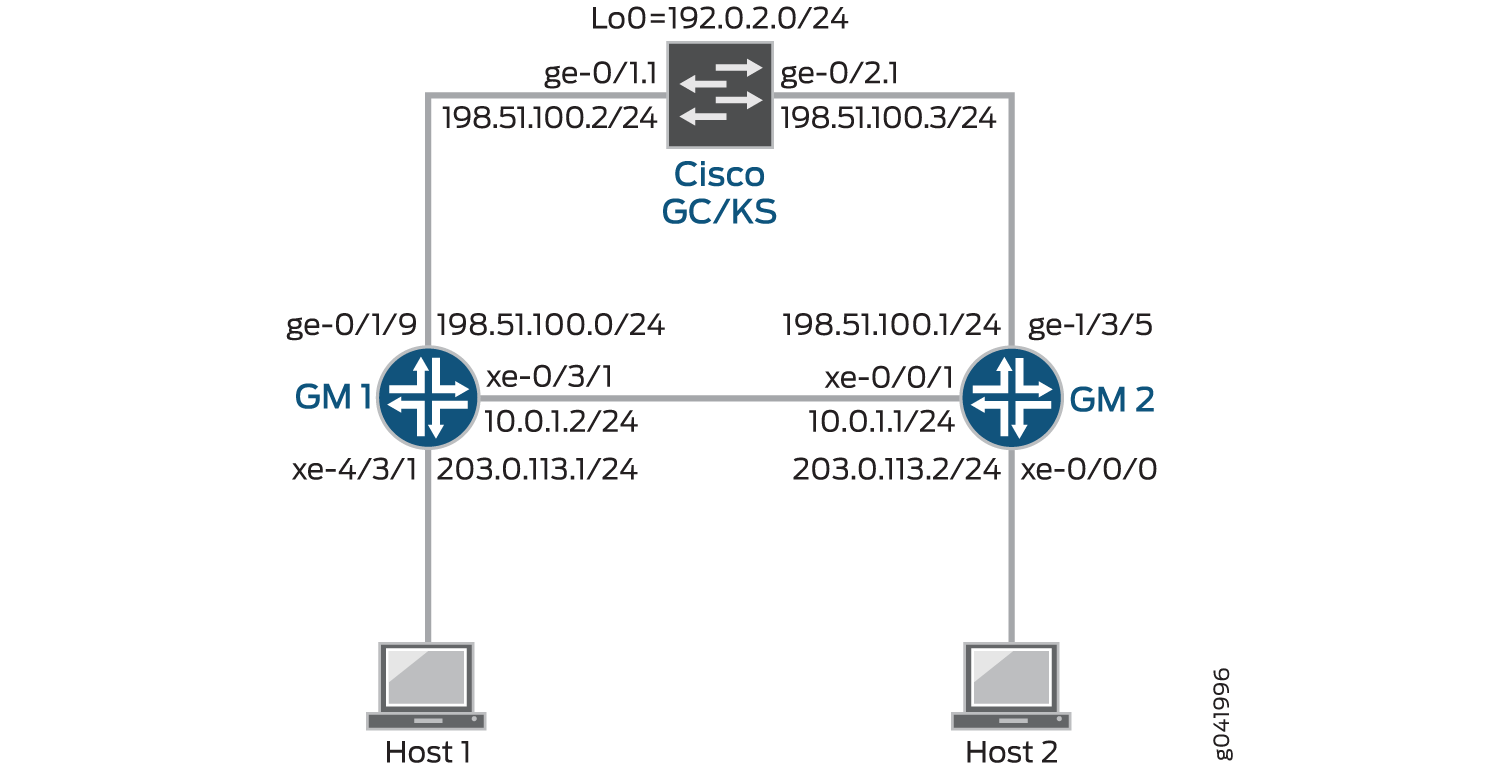
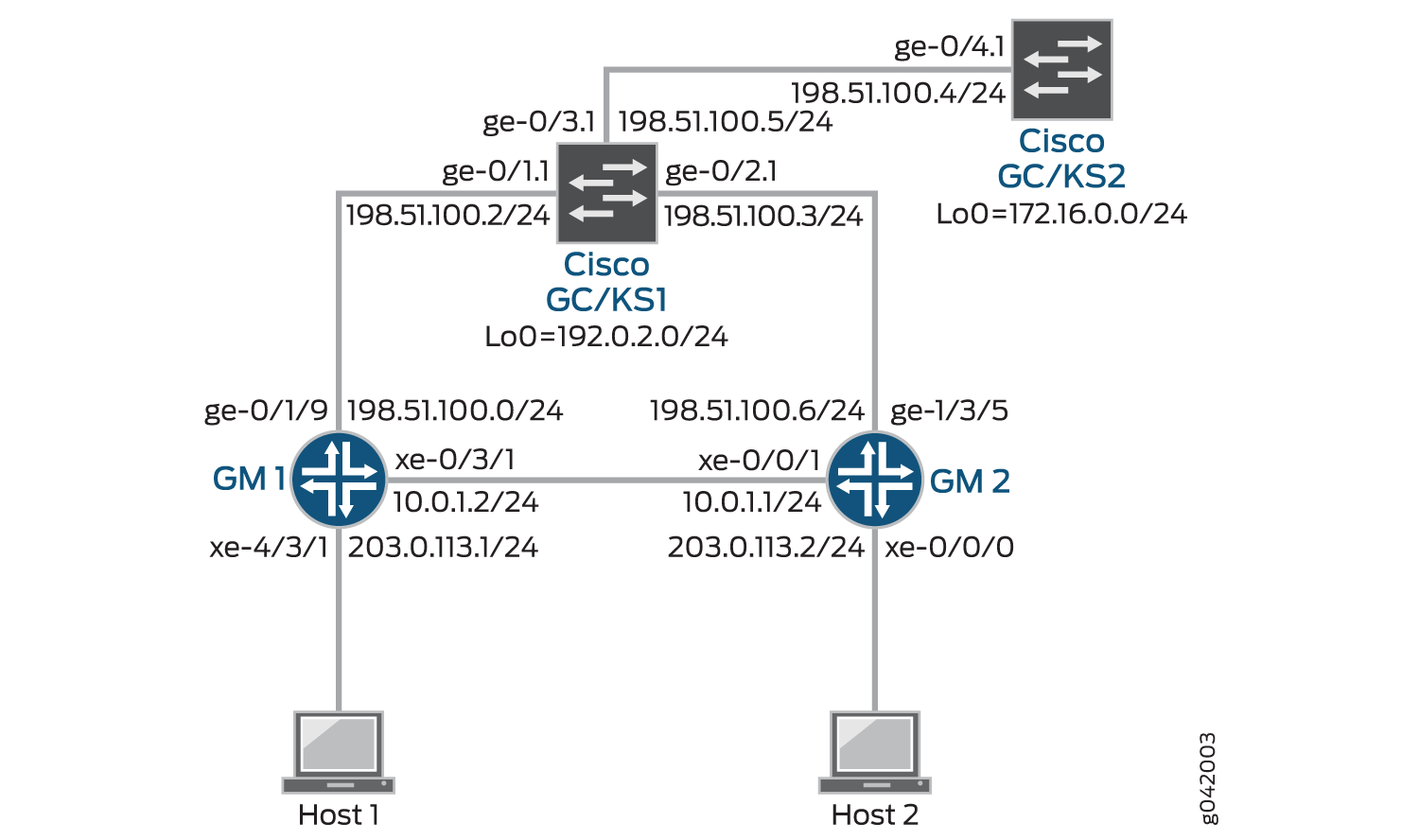
示例:在路由设备上的 VPNv2 中配置组 VPN
VPNv2 组是 MX5、MX10、MX40、MX80、MX104、MX240、MX480 和 MX960 路由器上的组 VPN 技术的名称。VPNv2 组不同于在 SRX 安全网关上实施的组 VPN 技术。本文中有时使用“组 VPN”一词来指代常规技术,而非 SRX 技术。
此示例说明如何在 VPNv2 组中配置组 VPN,以扩展 IP 安全 (IPsec) 架构,以支持由一组路由器共享的组安全关联 (GSA)。
要求
此示例使用以下硬件和软件组件:
两个带有 MS-MIC-16G 或 MS-MPC-PIC 线卡的 MX 系列 5G 通用路由平台
一个或多个 Cisco 组控制器或关键服务器 (GC/KS) 可访问性
在 MX 系列路由器上运行的 Junos OS 14.1 或更高版本
开始之前:
配置路由器以实现网络通信。
配置 Cisco GC/KS。
配置组成员设备接口。
概述
从 Junos OS 14.1 版开始,具有 MS-MIC-16G 和 MS-MPC-PIC 线卡的 MX 系列路由器可通过一个或多个 Cisco 组控制器或密钥服务器 (GC/KS) 提供组 VPNv2 成员功能支持。组成员最多可以连接到四个 Cisco GC/KS,与合作服务器的互操作性最低。
此功能还提供针对 VPNv2 组功能的系统日志记录支持,以及针对控制和数据流量的路由实例支持。
配置
使用单个 GC/KS 配置组 VPNv2
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层级的 [edit] CLI 中,然后 commit 进行配置。
GM1
set interfaces ms-4/0/0 unit 1 family inet set interfaces ge-0/1/9 vlan-tagging set interfaces ge-0/1/9 unit 1 vlan-id 11 set interfaces ge-0/1/9 unit 1 family inet address 198.51.100.0/24 set interfaces xe-0/3/1 vlan-tagging set interfaces xe-0/3/1 unit 1 vlan-id 1 set interfaces xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet address 10.0.1.2/24 set interfaces xe-4/3/1 unit 0 family inet address 203.0.113.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.2 set routing-options static route 203.0.113.0/24 next-hop 10.0.1.1 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.0 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
GM2
set interfaces ms-0/2/0 unit 1 family inet set interfaces xe-0/0/0 unit 0 family inet address 203.0.113.2/24 set interfaces xe-0/1/1 vlan-tagging set interfaces xe-0/1/1 unit 1 vlan-id 1 set interfaces xe-0/1/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet address 10.0.1.1/24 set interfaces ge-1/3/5 vlan-tagging set interfaces ge-1/3/5 unit 1 vlan-id 11 set interfaces ge-1/3/5 unit 1 family inet address 198.51.100.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.3 set routing-options static route 203.0.113.2/24 next-hop 10.0.1.2 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.0 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-0/2/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
逐步过程
以下示例要求您在配置层次结构中的各个级别上导航。有关导航 CLI 的信息,请参阅 在配置模式下使用 CLI 编辑器。
要配置 GM1:
配置路由器 GM1 接口。
[edit interfaces]user@GM1# set ms-4/0/0 unit 1 family inet user@GM1# set ge-0/1/9 vlan-tagging user@GM1# set ge-0/1/9 unit 1 vlan-id 11 user@GM1# set ge-0/1/9 unit 1 family inet address 198.51.100.0/24 user@GM1# set xe-0/3/1 vlan-tagging user@GM1# set xe-0/3/1 unit 1 vlan-id 1 user@GM1# set xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet address 10.0.1.2/24 user@GM1# set interfaces xe-4/3/1 unit 0 family inet address 203.0.113.1/24配置静态路由以到达组服务器和成员 2。
[edit routing-options]user@GM1# set static route 192.0.2.0/24 next-hop 198.51.100.2 user@GM1# set static route 203.0.113.0/24 next-hop 10.0.1.1定义 IKE 提议。
[edit security]user@GM1# set group-vpn member ike proposal ike-proposal为 ike 提议配置第 1 阶段 SA。
[edit security]user@GM1# set group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys user@GM1# set group-vpn member ike proposal ike-proposal dh-group group2 user@GM1# set group-vpn member ike proposal ike-proposal authentication-algorithm sha1 user@GM1# set group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc定义 IKE 策略。
[edit security]user@GM1# set group-vpn member ike policy ike-policy mode main user@GM1# set group-vpn member ike policy ike-policy proposals ike-proposal user@GM1# set group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"为 gw-group1 设置远程网关。
[edit security]user@GM1# set group-vpn member ike gateway gw-group1 ike-policy ike-policy user@GM1# set group-vpn member ike gateway gw-group1 server-address 192.0.2.0 user@GM1# set group-vpn member ike gateway gw-group1 local-address 198.51.100.0为 gw-group1 配置组标识符和 IKE 网关。
[edit security]user@GM1# set group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 user@GM1# set group-vpn member ipsec vpn vpn-group1 group 1 user@GM1# set group-vpn member ipsec vpn vpn-group1 match-direction output为 gw 组 1 配置服务集。
[edit services]user@GM1# set service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 user@GM1# set service-set gvpn-service-set ipsec-group-vpn vpn-group1
结果
在配置模式下,输入 show interfaces、 show routing-options、 show security和 show services 命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明,以更正配置。
GM1
user@GM1# show interfaces
ge-0/1/9 {
vlan-tagging;
unit 1 {
vlan-id 11;
family inet {
address 198.51.100.0/24;
}
}
}
xe-0/3/1 {
vlan-tagging;
unit 1 {
vlan-id 1;
family inet {
service {
input {
service-set gvpn-service-set;
}
output {
service-set gvpn-service-set;
}
}
address 10.0.1.2/24;
}
}
}
ms-4/0/0 {
unit 1 {
family inet;
}
}
xe-4/3/1 {
unit 0 {
family inet {
address 203.0.113.1/24;
}
}
}
user@GM1# show routing-options
static {
route 192.0.2.0/24 next-hop 198.51.100.2;
route 203.0.113.0/24 next-hop 10.0.1.1;
}
user@GM1# show security
group-vpn {
member {
ike {
proposal ike-proposal {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
}
policy ike-policy {
mode main;
pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"; ## SECRET-DATA
proposals ike-proposal;
}
gateway gw-group1 {
ike-policy ike-policy;
server-address 192.0.2.0;
local-address 198.51.100.0;
}
}
ipsec {
vpn vpn-group1 {
ike-gateway gw-group1;
group 1;
match-direction output;
}
}
}
}
user@GM1# show services
service-set gvpn-service-set {
interface-service {
service-interface ms-4/0/0.1;
}
ipsec-group-vpn vpn-group1;
}
使用多个 GC/KS 配置组 VPNv2
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层级的 [edit] CLI 中,然后 commit 进行配置。
GM1
set interfaces ms-4/0/0 unit 1 family inet set interfaces ge-0/1/9 vlan-tagging set interfaces ge-0/1/9 unit 1 vlan-id 11 set interfaces ge-0/1/9 unit 1 family inet address 198.51.100.0/24 set interfaces xe-0/3/1 vlan-tagging set interfaces xe-0/3/1 unit 1 vlan-id 1 set interfaces xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet address 10.0.1.2/24 set interfaces xe-4/3/1 unit 0 family inet address 203.0.113.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.2 set routing-options static route 203.0.113.0/24 next-hop 10.0.1.1 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 server-address 172.16.0.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.0 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
GM2
set interfaces ms-0/2/0 unit 1 family inet set interfaces xe-0/0/0 unit 0 family inet address 203.0.113.2/24 set interfaces xe-0/1/1 vlan-tagging set interfaces xe-0/1/1 unit 1 vlan-id 1 set interfaces xe-0/1/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet address 10.0.1.1/24 set interfaces ge-1/3/5 vlan-tagging set interfaces ge-1/3/5 unit 1 vlan-id 11 set interfaces ge-1/3/5 unit 1 family inet address 198.51.100.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.3 set routing-options static route 203.0.113.2/24 next-hop 10.0.1.2 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 server-address 172.16.0.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.1 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-0/2/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
逐步过程
以下示例要求您在配置层次结构中的各个级别上导航。有关导航 CLI 的信息,请参阅 在配置模式下使用 CLI 编辑器。
要配置 GM1:
配置路由器 GM1 接口。
[edit interfaces]user@GM1# set ms-4/0/0 unit 1 family inet user@GM1# set ge-0/1/9 vlan-tagging user@GM1# set ge-0/1/9 unit 1 vlan-id 11 user@GM1# set ge-0/1/9 unit 1 family inet address 198.51.100.0/24 user@GM1# set xe-0/3/1 vlan-tagging user@GM1# set xe-0/3/1 unit 1 vlan-id 1 user@GM1# set xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet address 10.0.1.2/24 user@GM1# set xe-4/3/1 unit 0 family inet address 203.0.113.1/24配置静态路由以到达组服务器和成员 2。
[edit routing-options]user@GM1# set static route 192.0.2.0/24 next-hop 198.51.100.2 user@GM1# set static route 203.0.1.0/24 next-hop 10.0.1.1定义 IKE 提议。
[edit security]user@GM1# set group-vpn member ike proposal ike-proposal为 ike 提议配置第 1 阶段 SA。
[edit security]user@GM1# set group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys user@GM1# set group-vpn member ike proposal ike-proposal dh-group group2 user@GM1# set group-vpn member ike proposal ike-proposal authentication-algorithm sha1 user@GM1# set group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc定义 IKE 策略。
[edit security]user@GM1# set group-vpn member ike policy ike-policy mode main user@GM1# set group-vpn member ike policy ike-policy proposals ike-proposal user@GM1# set group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"为 gw-group1 设置远程网关。
[edit security]user@GM1# set group-vpn member ike gateway gw-group1 ike-policy ike-policy user@GM1# set group-vpn member ike gateway gw-group1 server-address 192.0.2.0 user@GM1# set group-vpn member ike gateway gw-group1 server-address 172.16.0.0 user@GM1# set group-vpn member ike gateway gw-group1 local-address 198.51.100.0为 gw-group1 配置组标识符和 IKE 网关。
[edit security]user@GM1# set group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 user@GM1# set group-vpn member ipsec vpn vpn-group1 group 1 user@GM1# set group-vpn member ipsec vpn vpn-group1 match-direction output为 gw 组 1 配置服务集。
[edit services]user@GM1# set service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 user@GM1# set service-set gvpn-service-set ipsec-group-vpn vpn-group1
结果
在配置模式下,输入 show interfaces、 show routing-options、 show security和 show services 命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明,以更正配置。
GM1
user@GM1# show interfaces
ge-0/1/9 {
vlan-tagging;
unit 1 {
vlan-id 11;
family inet {
address 198.51.100.0/24;
}
}
}
xe-0/3/1 {
vlan-tagging;
unit 1 {
vlan-id 1;
family inet {
service {
input {
service-set gvpn-service-set;
}
output {
service-set gvpn-service-set;
}
}
address 10.0.1.2/24;
}
}
}
ms-4/0/0 {
unit 1 {
family inet;
}
}
xe-4/3/1 {
unit 0 {
family inet {
address 203.0.113.1/24;
}
}
}
user@GM1# show routing-options
static {
route 192.0.2.0/24 next-hop 198.51.100.2;
route 203.0.113.0/24 next-hop 10.0.1.1;
}
user@GM1# show security
group-vpn {
member {
ike {
proposal ike-proposal {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
}
policy ike-policy {
mode main;
pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"; ## SECRET-DATA
proposals ike-proposal;
}
gateway gw-group1 {
ike-policy ike-policy;
server-address [ 192.0.2.0 172.16.0.0 ];
local-address 198.51.100.0;
}
}
ipsec {
vpn vpn-group1 {
ike-gateway gw-group1;
group 1;
match-direction output;
}
}
}
}
user@GM1# show services
service-set gvpn-service-set {
interface-service {
service-interface ms-4/0/0.1;
}
ipsec-group-vpn vpn-group1;
}
验证
确认配置工作正常。
验证组成员 IKE SA
目的
验证路由器 GM1 上的 IKE SA。
行动
在操作模式下,运行 show security group-vpn member ike security-associations detail 命令。
user@GM1> show security group-vpn member ike security-associations detail IKE peer 192.0.2.0, Index 2994970, Gateway Name: gw-group1 Role: Initiator, State: UP Initiator cookie: 7fad16089a123bcd, Responder cookie: 536b33ffe89799de Exchange type: Main, Authentication method: Pre-shared-keys Local: 198.51.100.0:848, Remote: 192.0.2.0:848 Lifetime: Expires in 175 seconds Peer ike-id: 192.0.2.0 Xauth user-name: not available Xauth assigned IP: 0.0.0.0 Algorithms: Authentication : hmac-sha1-96 Encryption : 3des-cbc Pseudo random function: hmac-sha1 Diffie-Hellman group : DH-group-2 Traffic statistics: Input bytes : 752 Output bytes : 716 Input packets: 5 Output packets: 5 Flags: IKE SA is created IPSec security associations: 0 created, 0 deleted Phase 2 negotiations in progress: 0
意义
路由器 GM1 已使用组的 GC/KS 建立了 IKE SA。
验证组成员 IPsec SA
目的
验证路由器 GM1 上的 IPsec SA。
行动
在操作模式下,运行 show security group-vpn member ipsec security-associations detail 命令。
user@GM1> show security group-vpn member ipsec security-associations detail
Virtual-system: root Group VPN Name: vpn-group1
Local Gateway: 198.51.100.1, GDOI Server: 192.0.2.0
Group Id: 1
Rule Match Direction: output, Tunnel-MTU: 1500
Routing Instance: default
DF-bit: clear
Stats:
Pull Succeeded : 18
Pull Failed : 0
Pull Timeout : 0
Pull Aborted : 0
Server Failover : 0
Delete Received : 0
Exceed Maximum Keys(4) : 0
Exceed Maximum Policies(1): 0
Unsupported Algo : 0
Flags:
Rekey Needed: no
List of policies received from server:
Tunnel-id: 10001
Source IP: ipv4_subnet(any:0,[0..7]=203.0.2.0/24)
Destination IP: ipv4_subnet(any:0,[0..7]=203.0.1.0/24)
Direction: bi-directional, SPI: e1c117c7
Protocol: ESP, Authentication: sha1, Encryption: 3des
Hard lifetime: Expires in 2526 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2366 seconds
Mode: Tunnel, Type: Group VPN, State: installed
Anti-replay service: N/A
意义
路由器 GM1 已使用 GC/KS 建立 IPsec SA。
验证组成员 IPsec 统计信息
目的
验证路由器 GM1 上的 IPsec 统计信息。
行动
在操作模式下,运行 show security group-vpn member ipsec statistics 命令。
user@GM1> show security group-vpn member ipsec statistics PIC: ms-0/2/0, Service set: gvpn-service-set ESP Statistics: Encrypted bytes: 264 Decrypted bytes: 264 Encrypted packets: 3 Decrypted packets: 3 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0 ESP authentication failures: 0 ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Replay before window drops: 0, Replayed pkts: 0 IP integrity errors: 0, Exceeds tunnel MTU: 0 Rule lookup failures: 0, No SA errors: 0 Flow errors: 0, Misc errors: 0
意义
ESP Statistics 显示数据包流已在组成员之间加密和解密。路由器 GM1 已加密 3 个数据包,并收到了来自路由器 GM2 的 3 个解密数据包。
故障 排除
要对 VPNv2 组配置进行故障排除,请参阅:
协商 IKE SA
问题
不会对组成员触发 IKE SA 协商。
和 show security group-vpn member ike security-associations 命令的show ike输出不显示 IKE 协商。
解决 方案
要排除 IKE 协商问题:
检查服务接口状态是否正常运行。
用于
show interfaces terse | match ms检查 MS 接口是否关闭。当 PIC 重新启动时,MS 接口关闭。在日志文件
/var/log/gkmd中查找Ignore gvpn vpn_name since it is inactive。检查配置中的任何服务集是否引用了组 VPN。
启用
security group-vpn member ike traceoptions。在追踪日志文件中查找以下系统日志消息:
Dec 2 16:09:54 GVPN:iked_pm_gvpn_trigger called for gvpn200Dec 2 16:09:54 GVPN:PM NULL for gvpn gvpn200Dec 2 16:09:54 GVPN:Ignore gvpn gvpn200 since it is inactive
这意味着服务集处于非活动状态或服务接口关闭
建立 IKE SA
问题
IKE SA 尚未通过 GC/KS 建立。
在这种情况下,命令输出中的 show security group-vpn member ike security-associations IKE SA 状态为关闭:
user@GM1> show security group-vpn member ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
5295626 DOWN 2d47c125d2a9805e 0000000000000000 Main 192.0.2.2
解决 方案
要对 IKE SA 问题进行故障排除:
检查下
[edit security group-vpn member ike gateway]配置的服务器地址是否正确且可访问。在
ping远程设备之间使用命令检查网络连接。检查配置中的
group-vpn本地地址是否也是配置中的任何物理接口上的配置地址。检查组成员与 GC/KS 之间的 IKE 提议是否匹配。
如果 IKE SA 协商配置错误,请执行以下操作:
启用
security group-vpn member ike traceoption。在跟踪日志文件中查找以下消息:
Dec 2 15:39:54 ikev2_fb_negotiation_done_isakmp: Entered IKE error code No proposal chosen (14), IKE SA 8dd7000 (neg 8dda800)。
在日志文件
/var/log/gkmd中查找No proposal chosen错误。
下载 GDOI IPsec SA
问题
GDOI IPsec SA 不会从 GC/KS 下载。
在这种情况下,配置了 GC/KS 的 GDOI groupkey-pull 会失败, show security group-vpn member ipsec sa 命令输出不会显示任何内容。
解决 方案
要排除 GDOI IPsec SA 问题:
检查是否已使用 GC/KS 建立 IKE SA。
检查在 GC/KS 上配置的组 ID 是否与组成员匹配。
在日志文件
/var/log/gkmd中查找任何组 SA 安装失败或其他故障。请查找以下系统日志消息以确认使用不受支持的 GDOI SA 算法:
Dec 2 15:32:49 simpleman gkmd[1701]: Failed to install SA because of unsupported algo(encr: 3des-cbc, auth : (null)) for SPI 0x6645cdb5 from server 192.0.2.1Dec 2 15:32:49 simpleman gkmd[1701]: Member registration failed with key server 192.0.2.1 for group vpn gvpn200, reason SA unusable
请查找以下系统日志消息以确认使用了不受支持的 GDOI 策略:
Dec 2 15:34:34 simpleman gkmd[1701]: Failed to install SA because of too many(2) policies for SPI 0x6951550c from server 192.0.2.1Dec 2 15:34:34 simpleman gkmd[1701]: Member registration failed with key server 192.0.2.1 for group vpn gvpn200, reason SA unusable
流量加密和解密
问题
CLI 将显示 IPsec SA 已安装,但流量不会通过 SA。
在这种情况下,与从服务器接收的规则匹配的流量无法进行加密或解密。命令 show security group-vpn member ipsec statistics 输出显示加密和解密数据包计数的零值。
解决 方案
在 CLI 输出的错误部分中查找 Rule lookup failures 计数器。
系统日志消息故障排除
问题
系统会生成系统日志消息,以记录不同的组 VPNv2 事件。
解决 方案
要解释系统日志消息,请参阅以下内容:
Dec 2 15:29:10 simpleman gkmd[1701]: Member registration succeeded with key server 192.0.2.1 for group vpn gvpn200-GDOI 拉取成功。Dec 2 15:21:18 simpleman gkmd[1701]: Member registration failed with key server 192.0.2.1 for group vpn gvpn200, reason Timed out-GDOI 拉取失败。Dec 2 15:34:34 simpleman gkmd[1701]: Failed to install SA because of too many(2) policies for SPI 0x6951550c from server 192.0.2.1-GDOI SA 安装失败,因为策略太多。Dec 2 15:21:18 simpleman gkmd[1701]: Server 192.0.2.1 is unreachable for group vpn gvpn200-单个 GC/KS 失败(非 COOP)。Dec 2 15:51:49 simpleman gkmd[1701]: Current key server 192.0.2.1 is unreachable and will try registering with next Key Server 192.1.1.2 for group vpn gvpn200—特定 GC/KS 不响应 (COOP)。Dec 2 15:56:24 simpleman gkmd[1701]: All servers are unreachable for group vpn gvpn200—GC/KS 均未响应 (COOP)。Dec 2 16:01:43 simpleman gkmd[1701]: Member re-registering with Key Server 192.0.2.1 for group-vpn gvpn200— 成员在 GC/KS 中重新注册。Dec 2 16:01:43 simpleman gkmd[1701]: Creating TEK with SPI 0xb35200ac tunnel_id 10001 for group vpn gvpn200-GDOI SA TEK 创建成功。Dec 2 16:29:01 simpleman gkmd[1701]: Deleting TEK with SPI 0x6dba2a76 tunnel_id 10001 for group vpn gvpn200 and reason cleared from CLI-GDOI SA TEK 销毁成功是有道理的。GDOI SA TEK 销毁的不同原因如下:
已从 CLI 中清除
硬生存期已过期
TEK 太多
配置更改
SA 安装错误
SA 陈旧
接口关闭