被动监控
了解被动监控
被动监控是一种网络监控,用于从监控接口被动捕获流量。启用被动监控后,设备会接受并监控接口上的流量,并将流量转发到 IDS 服务器和数据包分析器等监控工具,或者路由器或终端节点主机等其他设备。
被动监控的优势
-
提供过滤功能,用于监控附加安全网络的互联网接入点 (PoP) 的入口和出口流量。
被动监控配置准则
-
您只能在接口级别配置被动监控。不支持按 VLAN 或逻辑接口进行配置。
-
无源监控接口不能是聚合以太网 (AE) 接口。
-
监控工具或设备必须直接连接到交换机或路由器。
-
包含两个以上 MPLS 标签和两个以上 VLAN 标记的数据包将被删除。
-
异常数据包(如 IP 数据包选项、路由器警报和 TTL 到期数据包)被视为常规流量。
-
不支持以太网封装。
-
PTX10001-36MR、PTX10004 和 PTX10008 路由器支持 MPLS 系列。
-
连接到监控工具或设备的 AE 捆绑包不支持链路聚合控制协议 (LACP)。
示例:配置被动监控
此示例说明如何在 QFX10000 交换机上配置被动监控。
要求
此示例使用以下硬件和软件组件:
-
两个路由器(R1 和 R2)
-
一台 QFX10002 交换机
-
两个设备,直接连接到交换机
-
Junos OS 18.4R1 或更高版本
概述
此示例介绍如何在交换机上配置被动监控。
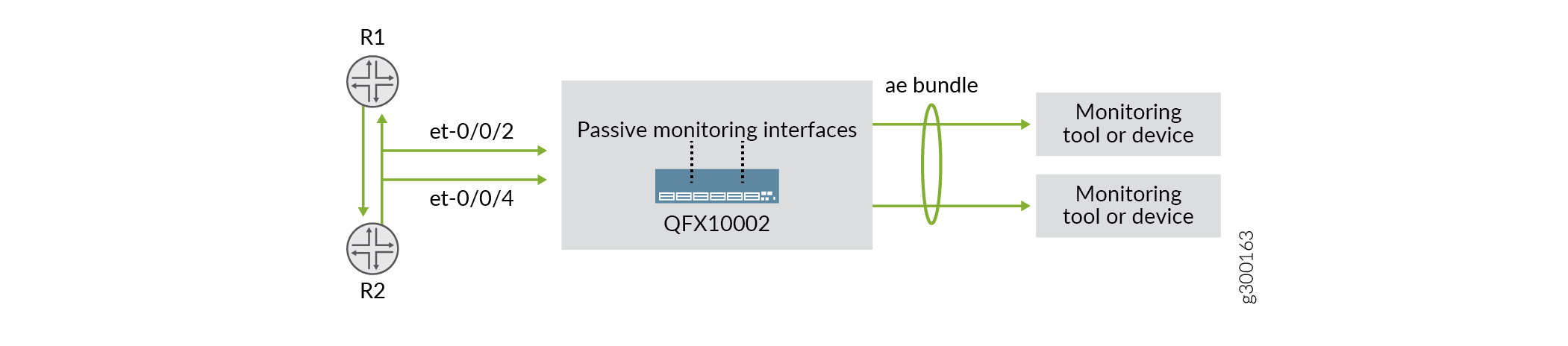
在 图 1 中, et-0/0/2 并 et-0/0/4 配置为无源监控接口。进入网络的数据包在路由器 1 (R1) 和路由器 2 (R2) 之间朝两个方向交换(R1 到 R2,R2 到 R1),并发送到受监控的接口。收到流量后,防火墙过滤器会将所有数据包传输到路由实例,并将数据包转发到监控工具。然后,这些接口分组为一个逻辑接口,称为链路聚合组 (LAG) 或 AE 束。这使得流量能够在监控工具中均匀分布,从而有效地增加上行链路带宽。如果一个接口发生故障,捆绑包将继续在剩余接口上传输流量。
或者,您还可以在无源监控接口上应用对称散列,以均衡流量到监控工具。这样,同一流的入口和出口流量可以通过同一受监控的接口发送出去。要配置对称散列,请在 no-incoming-port 层次结构下 [edit forwarding-options enhanced-hash-key] 添加选项。对称散列仅在全局级别启用和禁用。不支持按协议散列。
拓扑
配置
以下示例要求您在 CLI 层次结构中的各个级别上导航。有关导航 CLI 的信息,请参阅 在配置模式下使用 CLI 编辑器。
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层级的 [edit] CLI 中,然后从配置模式进入 commit 。
set interfaces et-0/0/2 passive-monitor-mode set interfaces et-0/0/2 unit 0 family inet filter input pm set interfaces et-0/0/4 passive-monitor-mode set interfaces et-0/0/4 unit 0 family inet filter input pm1 set firewall family inet filter pm1 term t1 from interface et-0/0/4.0 set firewall family inet filter pm1 term t1 then count c1 set firewall family inet filter pm1 term t1 then routing-instance pm_inst set firewall family inet filter pm term t1 from interface et-0/0/2.0 set firewall family inet filter pm term t1 then count c3 set firewall family inet filter pm term t1 then routing-instance pm_inst set routing-instances pm_inst instance-type virtual-router set routing-instances pm_inst interface ae0.0 set routing-instances pm_inst routing-options static route 0.0.0.0/0 next-hop 198.51.100.1 set interfaces xe-0/0/9:0 ether-options 802.3ad ae0 set interfaces xe-0/0/9:1 ether-options 802.3ad ae0 set interfaces ae0 unit 0 family inet address 198.51.100.2/24 arp 198.51.100.1 mac 00:10:94:00:00:05 set routing-instances pm_inst interface ae0.0 set forwarding-options enhanced-hash-key inet no-incoming-port
配置被动监控
逐步过程
要配置被动监控:
-
在交换机接口上配置被动监控模式:
[edit]] user@switch# set interfaces et-0/0/2 passive-monitor-mode set interfaces et-0/0/2 unit 0 family inet filter input pm set interfaces et-0/0/4 passive-monitor-mode set interfaces et-0/0/4 unit 0 family inet filter input pm1
-
family inet在被动监控接口上配置防火墙过滤器,将流量转发到路由实例。支持的过滤操作是accept, reject, count, routing-instance。[edit] user@switch# set firewall family inet filter pm1 term t1 from interface et-0/0/4.0 set firewall family inet filter pm1 term t1 then count c1 set firewall family inet filter pm1 term t1 then routing-instance pm_inst set firewall family inet filter pm term t1 from interface et-0/0/2.0 set firewall family inet filter pm term t1 then count c3 set firewall family inet filter pm term t1 then routing-instance pm_inst
-
使用指向设备的静态路由创建路由实例。
[edit] user@switch# set routing-instances pm_inst instance-type virtual-router set routing-instances pm_inst interface ae0.0 set routing-instances pm_inst routing-options static route 0.0.0.0/0 next-hop 198.51.100.1
-
在无源监控接口上配置 AE 捆绑包。
[edit] user@switch# set interfaces xe-0/0/9:0 ether-options 802.3ad ae0 set interfaces xe-0/0/9:1 ether-options 802.3ad ae0 set interfaces ae0 unit 0 family inet address 198.51.100.2/24 arp 198.51.100.1 mac 00:10:94:00:00:05 set routing-instances pm_inst interface ae0.0
-
(可选)配置对称散列。
[edit] user@switch# set forwarding-options enhanced-hash-key inet no-incoming-port
-
在配置模式下,输入命令以确认
show interfaces您的配置。如果命令输出未显示预期的配置,请重复此示例中的说明,以便进行更正。 -
完成接口配置后,请从配置模式进入
commit。
验证
确认配置工作正常。
验证被动监控配置
目的
验证被动监控是否正在接口上工作。如果接口输出显示 No-receive , No-transmit则表示被动监控工作。
行动
在操作模式下,输入 show interfaces 命令以查看被动监控接口。
user@host> show interfaces et-0/0/2
Physical interface: et-0/0/2, Enabled, Physical link is Up
Interface index: 146, SNMP ifIndex: 515
Link-level type: Ethernet, MTU: 1514, LAN-PHY mode, Speed: 40Gbps, BPDU Error: None, Loop Detect PDU Error: None, Ethernet-Switching Error: None, MAC-REWRITE Error: None,
Loopback: Disabled, Source filtering: Disabled, Flow control: Disabled, Media type: Fiber
Device flags : Present Running
Interface flags: SNMP-Traps No-receive No-transmit Internal: 0x4000
Link flags : None
CoS queues : 8 supported, 8 maximum usable queues
Current address: 3c:61:04:75:3c:5d, Hardware address: 3c:61:04:75:3c:5d
Last flapped : 2018-05-17 11:19:05 PDT (00:17:55 ago)
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Active alarms : None
Active defects : None
PCS statistics Seconds
Bit errors 0
Errored blocks 0
Ethernet FEC Mode : NONE
Ethernet FEC statistics Errors
FEC Corrected Errors 0
FEC Uncorrected Errors 0
FEC Corrected Errors Rate 0
FEC Uncorrected Errors Rate 0
PRBS Statistics : Disabled
Interface transmit statistics: Disabled
user@host show interfaces et-0/0/4
Physical interface: et-0/0/4, Enabled, Physical link is Up
Interface index: 146, SNMP ifIndex: 515
Link-level type: Ethernet, MTU: 1514, LAN-PHY mode, Speed: 40Gbps, BPDU Error: None, Loop Detect PDU Error: None, Ethernet-Switching Error: None, MAC-REWRITE Error: None,
Loopback: Disabled, Source filtering: Disabled, Flow control: Disabled, Media type: Fiber
Device flags : Present Running
Interface flags: SNMP-Traps No-receive No-transmit Internal: 0x4000
Link flags : None
CoS queues : 8 supported, 8 maximum usable queues
Current address: 3c:61:04:75:3c:5d, Hardware address: 3c:61:04:75:3c:5d
Last flapped : 2018-05-17 11:19:05 PDT (00:18:17 ago)
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Active alarms : None
Active defects : None
PCS statistics Seconds
Bit errors 0
Errored blocks 0
Ethernet FEC Mode : NONE
Ethernet FEC statistics Errors
FEC Corrected Errors 0
FEC Uncorrected Errors 0
FEC Corrected Errors Rate 0
FEC Uncorrected Errors Rate 0
PRBS Statistics : Disabled
Interface transmit statistics: Disabled
验证对称散列
目的
验证对称散列的输出。的传入端口字段inet,inet6L2应全部设置为“否”。
行动
在配置模式下,输入 show forwarding-options enhanced-hash-key 命令。
Slot 0
Seed value for Hash function 0: 3626023417
Seed value for Hash function 1: 3626023417
Seed value for Hash function 2: 3626023417
Seed value for Hash function 3: 3626023417
Inet settings:
--------------
IPV4 dest address: Yes
IPV4 source address: Yes
L4 Dest Port: Yes
L4 Source Port: Yes
Incoming port: No
Inet6 settings:
--------------
IPV6 dest address: Yes
IPV6 source address: Yes
L4 Dest Port: Yes
L4 Source Port: Yes
Incoming port: No
L2 settings:
------------
Dest Mac address: No
Source Mac address: No
Vlan Id: Yes
Inner-vlan Id: No
Incoming port: No
GRE settings:
-------------
Key: No
Protocol: No
MPLS settings:
--------------
MPLS Enabled: Yes
VXLAN settings:
---------------
VXLAN VNID: No
PTX10001-36MR、PTX10004 和 PTX10008 路由器的示例配置
以下是支持系列 mpls 的 PTX10001-36MR、PTX10004 和 PTX10008 路由器的示例配置。
set interfaces et-0/0/13 passive-monitor-mode set interfaces et-0/0/13 passive-monitor-mode set interfaces et-0/0/13 unit 0 family inet filter input ipv4pmFilter set interfaces et-0/0/13 unit 0 family inet6 filter input ipv6pmFilter set interfaces et-0/0/13 unit 0 family mpls filter input mplspmFilter set interfaces et-0/0/5 ether-options 802.3ad ae0 set interfaces et-0/0/7 ether-options 802.3ad ae0 set interfaces ae0 unit 0 family inet address 192.168.1.1/24 arp 192.168.1.10 mac 00:00:00:11:11:11 set interfaces ae0 unit 0 family inet6 address 2001:db8:1::1/64 ndp 2001:db8:1::10 mac 00:00:00:11:11:11 set routing-instances pm_inst routing-options rib pm_inst.inet6.0 static route 0::0/0 next-hop 2001:db8:1::10 set routing-instances pm_inst routing-options static route 0.0.0.0/0 next-hop 192.168.1.10 set routing-instances pm_inst instance-type virtual-router set routing-instances pm_inst interface ae0.0 set firewall family inet filter ipv4pmFilter term t1 then count C1 set firewall family inet filter ipv4pmFilter term t1 then routing-instance pm_inst set firewall family inet6 filter ipv6pmFilter term t2 then count C2 set firewall family inet6 filter ipv6pmFilter term t2 then routing-instance pm_inst set firewall family mpls filter ipv4pmfilter term t1 then count C1 set firewall family mpls filter ipv4pmfilter term t1 then routing-instance pm_inst set firewall family mpls filter ipv4pmfilter term t1 from ip-version ipv4 ip-protocol-except 255 set firewall family mpls filter ipv6pmfilter term t2 then count C2 set firewall family mpls filter ipv6pmfilter term t2 then routing-instance pm_inst set firewall family mpls filter ipv6pmfilter term t2 from ip-version ipv6 next-header-except 255
