示例:ES PIC IKE 动态 SA 配置
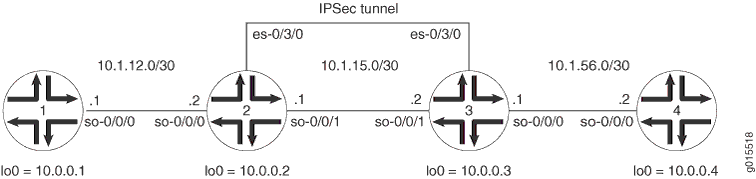
图 1 显示了与 ES PIC 手动 SA 示例中相同的 IPSec 拓扑。但是,这次的配置要求路由器 2 和 3 使用 IKE 动态 SA、增强型身份验证和更强加密来建立 IPSec 隧道。路由器 1 和 4 继续提供基本连接,并用于验证 IPSec 隧道是否正常运行。
在路由器 1 上,提供与路由器 2 的基本 OSPF 连接。
路由器 1
[edit]
interfaces {
so-0/0/0 {
description "To R2 so-0/0/0";
unit 0 {
family inet {
address 10.1.12.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.1/32;
}
}
}
}
routing-options {
router-id 10.0.0.1;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface lo0.0;
}
}
}
在路由器 2 上,启用 OSPF 作为连接到路由器 1 和 3 的底层路由协议。在[edit security ipsec security-association]层次结构级别配置称为 sa-dynamic 的双向 IKE 动态 SA。对于您的 IKE 策略和建议,请使用预共享密钥作为身份验证方法,使用 SHA-1 表示身份验证算法,使用 3DES-CBC 进行加密,将组 2 用于 Diffie-Hellman 组,主模式,3600 秒用于生存期,并使用瞻博网络的预共享密钥进行初始 IKE 协商。对于 IPSec 策略和建议,请使用 ESP 作为协议,HMAC-SHA1-96 用于身份验证,3DES-CBC 用于加密,28800 秒用于生存期,组 2 用于 PFS 组。
要将流量定向到 ES PIC 和 IPSec 隧道,请创建两个防火墙过滤器。 es-traffic 过滤器匹配来自路由器 1 发往路由器 4 的入站流量,而 es-return 过滤器匹配从路由器 4 到路由器 1 的返回路径。将 es-traffic 过滤器应用于 so-0/0/0 接口,然后将 es-return 过滤器和 sa-dynamic SA 应用于 es-0/3/0 接口。
路由器 2
[edit]
interfaces {
so-0/0/0 {
description "To R1 so-0/0/0";
unit 0 {
family inet {
filter {
input es-traffic; # Apply a filter that sends traffic to the IPSec tunnel here.
}
address 10.1.12.1/30;
}
}
}
so-0/0/1 {
description "To R3 so-0/0/1";
unit 0 {
family inet {
address 10.1.15.1/30;
}
}
}
es-0/3/0 {
unit 0 {
tunnel { # Specify the IPSec tunnel endpoints here.
source 10.1.15.1;
destination 10.1.15.2;
}
family inet {
ipsec-sa sa-dynamic; # Apply the dynamic SA here.
filter {
input es-return; # Apply the filter that matches return IPSec traffic here.
}
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.2/32;
}
}
}
}
routing-options {
router-id 10.0.0.2;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface so-0/0/1.0;
interface lo0.0;
}
}
}
security {
ipsec {
proposal es-ipsec-proposal { # Define your IPSec proposal specifications here.
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 28800;
}
policy es-ipsec-policy { # Define your IPSec policy specifications here.
perfect-forward-secrecy {
keys group2;
}
proposals es-ipsec-proposal; # Reference the IPSec proposal here.
}
security-association sa-dynamic { # Define your dynamic SA here.
mode tunnel;
dynamic {
ipsec-policy es-ipsec-policy; # Reference the IPSec policy here.
}
}
}
ike {
proposal es-ike-proposal { # Define your IKE proposal specifications here.
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
lifetime-seconds 3600;
}
policy 10.1.15.2 { # Define your IKE policy specifications here.
mode main;
proposals es-ike-proposal; # Reference the IKE proposal here.
pre-shared-key ascii-text "$ABC123";
## The unencrypted preshared key for this example is juniper.
}
}
}
firewall {
filter es-traffic { # Define a filter that sends traffic to the IPSec tunnel here.
term to-es {
from {
source-address {
10.1.12.0/24;
}
destination-address {
10.1.56.0/24;
}
}
then {
count ipsec-tunnel;
ipsec-sa sa-dynamic;
}
}
term other {
then accept;
}
}
filter es-return { # Define a filter that matches return IPSec traffic here.
term return {
from {
source-address {
10.1.56.0/24;
}
destination-address {
10.1.12.0/24;
}
}
then accept;
}
}
}
在路由器 3 上,启用 OSPF 作为基础路由协议以连接到路由器 2 和 4。在[edit security ipsec security-association]层次结构级别配置称为 sa-dynamic 的双向 IKE 动态 SA。使用您在路由器 2 上使用的相同策略和建议。
对于您的 IKE 策略和建议,请使用预共享密钥作为身份验证方法,使用 SHA-1 表示身份验证算法,使用 3DES-CBC 进行加密,将组 2 用于 Diffie-Hellman 组,主模式,3600 秒用于生存期,并使用瞻 博网络的 预共享密钥进行初始 IKE 协商。对于 IPSec 策略和建议,请使用 ESP 作为协议,HMAC-SHA1-96 用于身份验证,3DES-CBC 用于加密,28800 秒用于生存期,组 2 用于 PFS 组。
要将流量定向到 ES PIC 和 IPSec 隧道,请创建两个防火墙过滤器。 es-traffic 过滤器匹配来自路由器 4 发往路由器 1 的入站流量,而 es-return 过滤器匹配从路由器 1 到路由器 4 的返回路径。将 es-流量 过滤器应用于 so-0/0/0 接口;然后将 ES 返回 滤波器和 SA 动态 SA 应用于 es-0/3/0 接口。
路由器 3
[edit]
interfaces {
so-0/0/0 {
description "To R4 so-0/0/0";
unit 0 {
family inet {
filter {
input es-traffic; # Apply a filter that sends traffic to the IPSec tunnel here.
}
address 10.1.56.1/30;
}
}
}
so-0/0/1 {
description "To R2 so-0/0/1";
unit 0 {
family inet {
address 10.1.15.2/30;
}
}
}
es-0/3/0 {
unit 0 {
tunnel { # Specify the IPSec tunnel endpoints here.
source 10.1.15.2;
destination 10.1.15.1;
}
family inet {
ipsec-sa sa-dynamic; # Apply the dynamic SA here.
filter {
input es-return; # Apply the filter that matches return IPSec traffic here.
}
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.3/32;
}
}
}
}
routing-options {
router-id 10.0.0.3;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface so-0/0/1.0;
interface lo0.0;
}
}
}
security {
ipsec {
proposal es-ipsec-proposal { # Define your IPSec proposal specifications here.
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 28800;
}
policy es-ipsec-policy { # Define your IPSec policy specifications here.
perfect-forward-secrecy {
keys group2;
}
proposals es-ipsec-proposal; # Reference the IPSec proposal here.
}
security-association sa-dynamic { # Define your dynamic SA here.
mode tunnel;
dynamic {
ipsec-policy es-ipsec-policy; # Reference the IPSec policy here.
}
}
}
ike {
proposal es-ike-proposal { # Define your IKE proposal specifications here.
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
lifetime-seconds 3600;
}
policy 10.1.15.1 { # Define your IKE policy specifications here.
mode main;
proposals es-ike-proposal; # Reference the IKE proposal here.
pre-shared-key ascii-text "$ABC123";
## The unencrypted preshared key for this example is juniper.
}
}
}
firewall {
filter es-traffic { # Define a filter that sends traffic to the IPSec tunnel here.
term to-es {
from {
source-address {
10.1.56.0/24;
}
destination-address {
10.1.12.0/24;
}
}
then {
count ipsec-tunnel;
ipsec-sa sa-dynamic;
}
}
term other {
then accept;
}
}
filter es-return { # Define a filter that matches return IPSec traffic here.
term return {
from {
source-address {
10.1.12.0/24;
}
destination-address {
10.1.56.0/24;
}
}
then accept;
}
}
}
在路由器 4 上,提供与路由器 3 的基本 OSPF 连接。
路由器 4
[edit]
interfaces {
so-0/0/0 {
description "To R3 so-0/0/0";
unit 0 {
family inet {
address 10.1.56.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.4/32;
}
}
}
}
routing-options {
router-id 10.0.0.4;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface lo0.0;
}
}
}
验证您的工作
要验证基于 IKE 的动态 SA 在 ES PIC 上的操作是否正确,请使用以下命令:
-
乒
-
show ike security-associations (detail) -
show ipsec security-associations (detail) -
路由跟踪
以下部分显示了与配置示例一起使用的这些命令的输出:
路由器 1
在路由器 1 上,向路由器 4 的 so-0/0/0 接口发出ping命令,以通过 IPsec 隧道发送流量。
user@R1> ping 10.1.56.2 PING 10.1.56.2 (10.1.56.2): 56 data bytes 64 bytes from 10.1.56.2: icmp_seq=0 ttl=253 time=0.917 ms 64 bytes from 10.1.56.2: icmp_seq=1 ttl=253 time=0.881 ms 64 bytes from 10.1.56.2: icmp_seq=2 ttl=253 time=0.897 ms 64 bytes from 10.1.56.2: icmp_seq=3 ttl=253 time=0.871 ms 64 bytes from 10.1.56.2: icmp_seq=4 ttl=253 time=0.890 ms 64 bytes from 10.1.56.2: icmp_seq=5 ttl=253 time=0.858 ms 64 bytes from 10.1.56.2: icmp_seq=6 ttl=253 time=0.904 ms ^C --- 10.1.56.2 ping statistics --- 7 packets transmitted, 7 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.858/0.888/0.917/0.019 ms
您还可以发出命令来 traceroute 验证发往 10.1.56.2 的流量是否通过路由器 2 和路由器 3 之间的 IPsec 隧道传输。请注意,第二个跃点不引用 10.1.15.2 — 路由器 3 上的物理接口。相反,路由器 3 上的环路地址 10.0.0.3 显示为第二跃点。这表示 IPSec 隧道运行正常。
user@R1> traceroute 10.1.56.2 traceroute to 10.1.56.2 (10.1.56.2), 30 hops max, 40 byte packets 1 10.1.12.1 (10.1.12.1) 0.655 ms 0.549 ms 0.508 ms 2 10.0.0.3 (10.0.0.3) 0.833 ms 0.786 ms 0.757 ms
3 10.1.56.2 (10.1.56.2) 0.808 毫秒 0.741 毫秒 0.716 毫秒
路由器 2
验证匹配的流量是否正在转移到双向 IPsec 隧道的另一种方法是查看防火墙过滤器计数器。从路由器 1(七个数据包)发出 ping 命令后, es-traffic 防火墙过滤器计数器如下所示:
user@R2> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 588 7
ping从路由器 1(7 个数据包)和路由器 4(5 个数据包)发出命令后,es-traffic 防火墙过滤器计数器如下所示:
user@R2> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 1008 12
要验证路由器 2 和 3 之间的 IKE SA 协商是否成功,请发出 show ike security-associations detail 命令。请注意,SA 包含您指定的设置,例如 SHA-1 用于身份验证算法,3DES-CBC 用于加密算法。
user@R2> show ike security-associations detail IKE peer 10.1.15.2 Role: Initiator, State: Matured Initiator cookie: b5dbdfe2f9000000, Responder cookie: a24c868410000041 Exchange type: Main, Authentication method: Pre-shared-keys Local: 10.1.15.1:500, Remote: 10.1.15.2:500 Lifetime: Expires in 401 seconds Algorithms: Authentication : sha1 Encryption : 3des-cbc Pseudo random function: hmac-sha1 Traffic statistics: Input bytes : 1736 Output bytes : 2652 Input packets: 9 Output packets: 15 Flags: Caller notification sent IPSec security associations: 3 created, 0 deleted Phase 2 negotiations in progress: 0
要验证 IPsec 安全关联是否处于活动状态,请发出 show ipsec security-associations detail 命令。请注意,SA 包含您指定的设置,例如协议的 ESP、身份验证算法的 HMAC-SHA1-96 以及加密算法的 3DES-CBC。
user@R2> show ipsec security-associations detail
Security association: sa-dynamic, Interface family: Up
Local gateway: 10.1.15.1, Remote gateway: 10.1.15.2
Local identity: ipv4_subnet(any:0,[0..7]=10.1.12.0/24)
Remote identity: ipv4_subnet(any:0,[0..7]=10.1.56.0/24)
Direction: inbound, SPI: 2133029543, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 26212 seconds
Hard lifetime: Expires in 26347 seconds
Anti-replay service: Disabled
Direction: outbound, SPI: 1759450863, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 26212 seconds
Hard lifetime: Expires in 26347 seconds
Anti-replay service: Disabled
路由器 3
查看防火墙过滤器计数器以继续验证匹配的流量是否正在转移到双向 IPsec 隧道。从路由器 1(七个数据包)发出 ping 命令后, es-traffic 防火墙过滤器计数器如下所示:
user@R3> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 588 7
ping从路由器 1(7 个数据包)和路由器 4(5 个数据包)发出命令后,es-traffic 防火墙过滤器计数器如下所示:
user@R3> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 1008 12
要验证 IKE 安全关联是否成功,请发出 show ike security-associations detail 命令。请注意,路由器 3 上的 SA 包含您在路由器 2 上指定的相同设置。
user@R3> show ike security-associations detail IKE peer 10.1.15.1 Role: Responder, State: Matured Initiator cookie: b5dbdfe2f9000000, Responder cookie: a24c868410000041 Exchange type: Main, Authentication method: Pre-shared-keys Local: 10.1.15.2:500, Remote: 10.1.15.1:500 Lifetime: Expires in 564 seconds Algorithms: Authentication : sha1 Encryption : 3des-cbc Pseudo random function: hmac-sha1 Traffic statistics: Input bytes : 2652 Output bytes : 1856 Input packets: 15 Output packets: 10 Flags: Caller notification sent IPSec security associations: 3 created, 4 deleted Phase 2 negotiations in progress: 0
要验证 IPsec 安全关联是否处于活动状态,请发出 show ipsec security-associations detail 命令。请注意,路由器 3 上的 SA 包含您在路由器 2 上指定的相同设置。
user@R3> show ipsec security-associations detail
Security association: sa-dynamic, Interface family: Up
Local gateway: 10.1.15.2, Remote gateway: 10.1.15.1
Local identity: ipv4_subnet(any:0,[0..7]=10.1.56.0/24)
Remote identity: ipv4_subnet(any:0,[0..7]=10.1.12.0/24)
Direction: inbound, SPI: 1759450863, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 26427 seconds
Hard lifetime: Expires in 26517 seconds
Anti-replay service: Disabled
Direction: outbound, SPI: 2133029543, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 26427 seconds
Hard lifetime: Expires in 26517 seconds
Anti-replay service: Disabled
路由器 4
在路由器 4 上,向路由器 1 的 so-0/0/0 接口发出ping命令,以通过 IPsec 隧道发送流量。
user@R4> ping 10.1.12.2 user@R4> ping 10.1.12.2 PING 10.1.12.2 (10.1.12.2): 56 data bytes 64 bytes from 10.1.12.2: icmp_seq=0 ttl=253 time=13.528 ms 64 bytes from 10.1.12.2: icmp_seq=1 ttl=253 time=0.873 ms 64 bytes from 10.1.12.2: icmp_seq=2 ttl=253 time=32.145 ms 64 bytes from 10.1.12.2: icmp_seq=3 ttl=253 time=0.921 ms 64 bytes from 10.1.12.2: icmp_seq=4 ttl=253 time=0.899 ms ^C --- 10.1.12.2 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.873/9.673/32.145/12.255 ms
您还可以发出命令来 traceroute 验证发往 10.1.12.2 的流量是否通过路由器 3 和路由器 2 之间的 IPsec 隧道传输。请注意,第二个跃点不引用 10.1.15.1 — 路由器 2 上的物理接口。相反,路由器 2 上的环路地址 10.0.0.2 显示为第二个跃点。这表示 IPSec 隧道运行正常。
user@R4> traceroute 10.1.12.2 traceroute to 10.1.12.2 (10.1.12.2), 30 hops max, 40 byte packets 1 10.1.56.1 (10.1.56.1) 0.681 ms 0.624 ms 0.547 ms 2 10.0.0.2 (10.0.0.2) 0.800 ms 0.770 ms 0.737 ms 3 10.1.12.2 (10.1.12.2) 0.793 ms 0.742 ms 0.716 ms
