示例:配置 IS-IS 路由从 2 级区域泄漏到 1 级区域
此示例说明如何将 IS-IS 网络中的前缀从第 2 级区域泄漏到第 1 级区域。
要求
配置此示例之前,不需要除设备初始化之外的特殊配置。
概述
每个路由协议都会在路由层次结构中向上或向下传递路由信息。这种双向路由信息流称为路由泄漏。
默认情况下,IS-IS 协议会将路由信息从第 1 级区域泄露到第 2 级区域。但是,要将路由信息从 2 级区域泄露到第 1 级区域,必须显式配置导出策略。
拓扑学
在此示例中,设备 R3 和 R4 配置在第 2 级区域中。设备 R5、R6 和 R7 配置在第 1 级区域中。
图 1 显示了此示例中使用的拓扑。
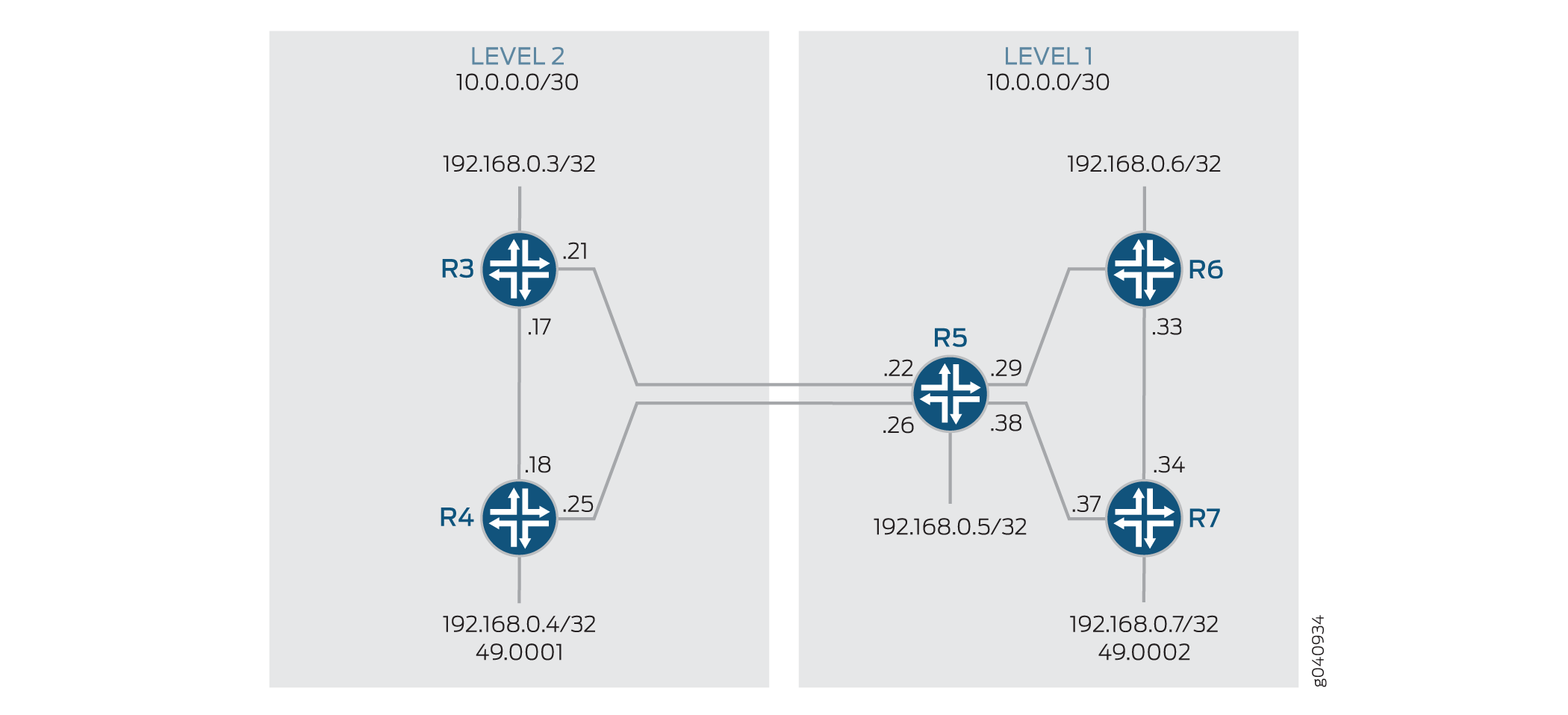 的路由泄漏
的路由泄漏
配置
配置从 2 级区域到 1 级区域的路由泄漏
CLI 快速配置
要快速配置从 2 级区域到 1 级区域的路由泄漏,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到层级的 CLI [edit] 中。
设备 R3
set interfaces fe-1/2/0 unit 0 description to-R4 set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.17/30 set interfaces fe-1/2/0 unit 0 family iso set interfaces fe-1/2/1 unit 0 description to-R5 set interfaces fe-1/2/1 unit 0 family inet address 10.0.0.21/30 set interfaces fe-1/2/1 unit 0 family iso set interfaces lo0 unit 0 family inet address 192.168.0.3/32 set interfaces lo0 unit 0 family iso address 49.0001.0192.0168.0003.00 set policy-options policy-statement leak-L2-to-L1 from route-filter 192.168.0.0/24 orlonger set policy-options policy-statement leak-L2-to-L1 from protocol isis set policy-options policy-statement leak-L2-to-L1 from level 2 set policy-options policy-statement leak-L2-to-L1 to protocol isis set policy-options policy-statement leak-L2-to-L1 to level 1 set policy-options policy-statement leak-L2-to-L1 then accept set protocols isis interface fe-1/2/0.0 level 1 disable set protocols isis interface fe-1/2/1.0 level 1 disable set protocols isis interface lo0.0 level 1 disable set protocols isis export leak-L2-to-L1
设备 R4
set interfaces fe-1/2/0 unit 0 description to-R3 set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.18/30 set interfaces fe-1/2/0 unit 0 family iso set interfaces fe-1/2/1 unit 0 description to-R5 set interfaces fe-1/2/1 unit 0 family inet address 10.0.0.25/30 set interfaces fe-1/2/1 unit 0 family iso set interfaces lo0 unit 0 family inet address 192.168.0.4/32 set interfaces lo0 unit 0 family iso address 49.0001.0192.0168.0004.00 set policy-options policy-statement leak-L2-to-L1 from route-filter 192.168.0.0/24 orlonger set policy-options policy-statement leak-L2-to-L1 from protocol isis set policy-options policy-statement leak-L2-to-L1 from level 2 set policy-options policy-statement leak-L2-to-L1 to protocol isis set policy-options policy-statement leak-L2-to-L1 to level 1 set policy-options policy-statement leak-L2-to-L1 then accept set protocols isis interface fe-1/2/0.0 level 1 disable set protocols isis interface fe-1/2/1.0 level 1 disable set protocols isis interface lo0.0 level 1 disable set protocols isis export leak-L2-to-L1
设备 R5
set interfaces fe-1/2/0 unit 0 description to-R3 set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.22/30 set interfaces fe-1/2/0 unit 0 family iso set interfaces fe-1/2/1 unit 0 description to-R4 set interfaces fe-1/2/1 unit 0 family inet address 10.0.0.26/30 set interfaces fe-1/2/1 unit 0 family iso set interfaces fe-1/2/2 unit 0 description to-R6 set interfaces fe-1/2/2 unit 0 family inet address 10.0.0.29/30 set interfaces fe-1/2/2 unit 0 family iso set interfaces fe-1/2/3 unit 0 description to-R7 set interfaces fe-1/2/3 unit 0 family inet address 10.0.0.38/30 set interfaces fe-1/2/3 unit 0 family iso set interfaces lo0 unit 0 family inet address 192.168.0.5/32 set interfaces lo0 unit 0 family iso address 49.0002.0192.0168.0005.00 set protocols isis interface fe-1/2/0.0 level 1 disable set protocols isis interface fe-1/2/1.0 level 1 disable set protocols isis interface fe-1/2/2.0 level 2 disable set protocols isis interface fe-1/2/3.0 level 2 disable set protocols isis interface lo0.0 level 1 disable
设备 R6
set interfaces fe-1/2/0 unit 0 description to-R5 set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.30/30 set interfaces fe-1/2/0 unit 0 family iso set interfaces fe-1/2/1 unit 0 description to-R7 set interfaces fe-1/2/1 unit 0 family inet address 10.0.0.33/30 set interfaces fe-1/2/1 unit 0 family iso set interfaces lo0 unit 0 family inet address 192.168.0.6/32 set interfaces lo0 unit 0 family iso address 49.0002.0192.0168.0006.00 set protocols isis interface fe-1/2/0.0 level 2 disable set protocols isis interface fe-1/2/1.0 level 2 disable set protocols isis interface lo0.0 level 2 disable
设备 R7
set interfaces fe-1/2/0 unit 0 description to-R6 set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.34/30 set interfaces fe-1/2/0 unit 0 family iso set interfaces fe-1/2/1 unit 0 description to-R5 set interfaces fe-1/2/1 unit 0 family inet address 10.0.0.37/30 set interfaces fe-1/2/1 unit 0 family iso set interfaces lo0 unit 0 family inet address 192.168.0.7/32 set interfaces lo0 unit 0 family iso address 49.0002.0192.0168.0007.00 set protocols isis interface fe-1/2/0.0 level 2 disable set protocols isis interface fe-1/2/1.0 level 2 disable set protocols isis interface lo0.0 level 2 disable
分步过程
配置从 2 级区域到 1 级区域的路由泄漏
分步过程
下面的示例要求您在各个配置层级中进行导航。有关 CLI 导航的信息,请参阅《Junos OS CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要配置从 2 级区域到 1 级区域的路由泄漏:
配置网络接口。
通过在每个接口上包含 ISO 地址族,在接口上启用 IS-IS。
[edit interfaces] user@R3# set fe-1/2/0 unit 0 description to-R4 user@R3# set fe-1/2/0 unit 0 family inet address 10.0.0.17/30 user@R3# set fe-1/2/0 unit 0 family iso user@R3# set fe-1/2/1 unit 0 description to-R5 user@R3# set fe-1/2/1 unit 0 family inet address 10.0.0.21/30 user@R3# set fe-1/2/1 unit 0 family iso
同样地,配置其他路由器。
配置两个环路接口地址。
一个地址用于 IPv4,另一个地址用于使路由器能够与该区域内的其他路由器形成邻接。
[edit interfaces lo0 unit 0] user@R3# set family inet address 192.168.0.3/32 user@R3# set family iso address 49.0001.0192.0168.0003.00
基于每个接口指定 IS-IS 级别。
[edit protocols isis interface] user@R3# set fe-1/2/0.0 level 1 disable user@R3# set fe-1/2/1.0 level 1 disable user@R3# set lo0.0 level 1 disable
在第 2 级区域中配置的路由器上配置路由泄漏策略,以将路由泄露到第 1 级区域。
[edit policy-options policy-statement leak-L2-to-L1] user@R3# set from route-filter 192.168.0.0/24 orlonger user@R3# set from protocol isis user@R3# set from level 2 user@R3# set to protocol isis user@R3# set to level 1 user@R3# set then accept
[edit protocols isis] user@R3# set export leak-L2-to-L1
同样,配置设备 R4。
结果
在配置模式下,输入show interfacesshow protocols isis、和show policy-options命令,以确认您的配置。
如果输出未显示预期的配置,请重复此示例中的说明以更正配置。
user@R3# show interfaces
fe-1/2/0 {
unit 0 {
description to-R4;
family inet {
address 10.0.0.17/30;
}
family iso;
}
}
fe-1/2/1 {
unit 0 {
description to-R5;
family inet {
address 10.0.0.21/30;
}
family iso;
}
}
lo0 {
unit 0 {
family inet {
address 192.168.0.3/32;
}
family iso {
address 49.0001.0192.0168.0003.00;
}
}
}
user@R3# show protocols isis
export leak-L2-to-L1;
interface fe-1/2/0.0 {
level 1 disable;
}
interface fe-1/2/1.0 {
level 1 disable;
}
interface lo0.0 {
level 1 disable;
}
user@R3# show policy-options
policy-statement leak-L2-to-L1 {
from {
protocol isis;
level 2;
route-filter 192.168.0.0/24 orlonger;
}
to {
protocol isis;
level 1;
}
then accept;
}
同样,确认所有其他路由器上的配置。如果完成路由器配置,请从配置模式输入 commit 。
验证
验证从 2 级区域到 1 级区域的路由泄漏
目的
验证 IS-IS 是否泄漏了从 2 级区域到 1 级区域的路由。
行动
要验证是否发生了路由泄漏,请使用以下命令:
show isis adjacency (验证 IS-IS 网络是否已启动并已建立邻接关系)
show isis database detail (以验证是否存在泄漏的路由)
在设备 R3 上的作模式下,运行 show isis adjacency 命令。
user@R3> show isis adjacency Interface System L State Hold (secs) SNPA fe-1/2/0.0 R4 2 Up 7 0:5:85:8f:94:bd fe-1/2/1.0 R5 2 Up 7 0:5:85:8f:94:bd
输出验证设备 R3 上的接口是否已开启,并且已与路由器 R4 和 R5 上的连接接口建立邻接。如果您没有看到接口正常运行,请参阅 结果 部分,对配置进行故障排除。
在设备 R3 上的作模式下,运行 show isis database detail 命令。
user@R3> show isis database detail IS-IS level 1 link-state database: R3.00-00 Sequence: 0x19, Checksum: 0x3453, Lifetime: 1078 secs IP prefix: 192.168.0.4/32 Metric: 10 Internal Down IP prefix: 192.168.0.5/32 Metric: 10 Internal Down IP prefix: 192.168.0.6/32 Metric: 20 Internal Down IP prefix: 192.168.0.7/32 Metric: 20 Internal Down IS-IS level 2 link-state database: R3.00-00 Sequence: 0x1c, Checksum: 0xc657, Lifetime: 1078 secs IS neighbor: R4.02 Metric: 10 IS neighbor: R5.02 Metric: 10 IP prefix: 10.0.0.16/30 Metric: 10 Internal Up IP prefix: 10.0.0.20/30 Metric: 10 Internal Up IP prefix: 192.168.0.3/32 Metric: 0 Internal Up R4.00-00 Sequence: 0x19, Checksum: 0xea13, Lifetime: 1076 secs IS neighbor: R4.02 Metric: 10 IS neighbor: R5.03 Metric: 10 IP prefix: 10.0.0.16/30 Metric: 10 Internal Up IP prefix: 10.0.0.24/30 Metric: 10 Internal Up IP prefix: 192.168.0.4/32 Metric: 0 Internal Up R4.02-00 Sequence: 0x17, Checksum: 0xecab, Lifetime: 1076 secs IS neighbor: R3.00 Metric: 0 IS neighbor: R4.00 Metric: 0 R5.00-00 Sequence: 0x12, Checksum: 0xf4e5, Lifetime: 1076 secs IS neighbor: R5.02 Metric: 10 IS neighbor: R5.03 Metric: 10 IP prefix: 10.0.0.20/30 Metric: 10 Internal Up IP prefix: 10.0.0.24/30 Metric: 10 Internal Up IP prefix: 10.0.0.28/30 Metric: 10 Internal Up IP prefix: 10.0.0.32/30 Metric: 20 Internal Up IP prefix: 10.0.0.36/30 Metric: 10 Internal Up IP prefix: 192.168.0.5/32 Metric: 0 Internal Up IP prefix: 192.168.0.6/32 Metric: 10 Internal Up IP prefix: 192.168.0.7/32 Metric: 10 Internal Up R5.02-00 Sequence: 0xb, Checksum: 0x2d74, Lifetime: 1076 secs IS neighbor: R3.00 Metric: 0 IS neighbor: R5.00 Metric: 0 R5.03-00 Sequence: 0xb, Checksum: 0x6c32, Lifetime: 1076 secs IS neighbor: R4.00 Metric: 0 IS neighbor: R5.00 Metric: 0
关键
Down字标识已成功从 2 级区域泄漏到 1 级区域的路由。
意义
从 2 级泄漏到 1 级区域的路由按预期运行。
