适用于 GTP 的 NAT
网络地址转换 (NAT) 协议用于检查内部 GPRS 网络和互联网(外部网络)之间的 GTP 流量,反之亦然。
了解 GTP 的 NAT
通用分组无线服务 (GPRS) 接口在同一路由实例中同时支持 GPRS 隧道协议 (GTP) 检测和网络地址转换 (NAT)。在网络中检查使用静态 NAT 配置的 GTP 数据包时,只会转换 IP 报头中的地址。其有效负载内的地址不会转换。对于每个端点,相关的 GTP 会话必须属于同一区域和虚拟路由器。这意味着有效负载中的标头源 IP、C 隧道 IP 和 U 隧道 IP 均在数据包的相同范围内定义。
启用 NAT 时,只需转换外部 IP 数据包。嵌入的 IP 地址不会转换。
在 GTP 数据包流期间,源 IP 地址和目标 IP 地址不能同时转换为 NAT。删除或停用设备上的 NAT 规则配置时,将删除与 NAT 规则相关的 GSN 和 GTP 隧道。如果 NAT 规则相关的 GSN 编号和隧道编号较大,则此删除过程需要几分钟时间。
示例:在 NAT 中配置 GTP 检查
此示例说明如何配置 NAT 规则,以将专用 IP(网络内部不可路由的 IP)映射到公共 IP(网络外部且可路由的 IP)。此外,还展示了如何检测内部和外部网络之间的 GTP 流量。
要求
开始之前,必须在启用 GTP 后重新启动设备。默认情况下,设备上的 GTP 处于禁用状态。
概述
在此示例中,您将接口配置为 ge-0/0/0 和 ge-0/0/1,地址为 10.0.0.254/8 和 123.0.0.254/8。然后,配置安全区域和静态 NAT。您可以在安全策略中启用 GTP 服务以允许两个网络之间的双向流量,并检查内部和外部网络之间的流量。
配置
程序
CLI 快速配置
要快速配置示例的此部分,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层次结构级别的 CLI 中 [edit] ,然后从配置模式进入 commit 。
set interfaces ge-0/0/0 unit 0 family inet address 10.0.0.254/8 set interfaces ge-0/0/1 unit 0 family inet address 123.0.0.254/8 set security zones security-zone zone1 interfaces ge-0/0/0.0 host-inbound-traffic system-services all set security zones security-zone zone1 host-inbound-traffic protocols all set security zones security-zone other-zone interfaces ge-0/0/1.0 host-inbound-traffic system-services all set security zones security-zone other-zone host-inbound-traffic protocols all set security address-book global address gsn1 10.0.0.1/8 set security address-book global address other-gsn 20.0.0.1/8 set security nat static rule-set rs1 from zone other-zone set security nat static rule-set rs1 rule r1 match destination-address 123.0.0.1/32 set security nat static rule-set rs1 rule r1 then static-nat prefix 10.0.0.1/32 set security nat proxy-arp interface ge-0/0/0.0 address 123.0.0.1/32 set security gprs gtp profile gtp1 set security gprs gtp profile gtp1 timeout 1 set security gprs gtp profile gtp1 seq-number-validated set security policies from-zone zone1 to-zone other-zone policy out-gtp match source-address gsn1 set security policies from-zone zone1 to-zone other-zone policy out-gtp match destination-address other-gsn set security policies from-zone zone1 to-zone other-zone policy out-gtp match application junos-gprs-gtp set security policies from-zone zone1 to-zone other-zone policy out-gtp then permit application-services gprs-gtp-profile gtp1 set security policies from-zone other-zone to-zone zone1 policy in-gtp match source-address other-gsn set security policies from-zone other-zone to-zone zone1 policy in-gtp match destination-address gsn1 set security policies from-zone other-zone to-zone zone1 policy in-gtp match application junos-gprs-gtp set security policies from-zone other-zone to-zone zone1 policy in-gtp then permit application-services gprs-gtp-profile gtp1
逐步过程
在 NAT 中配置 GTP 检测:
配置接口。
[edit] user@host# set interfaces ge-0/0/0 unit 0 family inet address 10.0.0.254/8 user@host# set interfaces ge-0/0/1 unit 0 family inet address 123.0.0.254/8
配置和安全区域
[edit security] user@host# set zones security-zone zone1 interfaces ge-0/0/0.0 host-inbound-traffic system-services all user@host# set zones security-zone zone1 host-inbound-traffic protocols all user@host# set zones security-zone other-zone interfaces ge-0/0/1.0 host-inbound-traffic system-services all user@host# set zones security-zone other-zone host-inbound-traffic protocols all
定义地址簿。
[edit security] user@host# set address-book global address gsn1 10.0.0.1/8 user@host# set address-book global address other-gsn 20.0.0.1/8
定义 NAT 规则。
[edit security nat] user@host# set static rule-set rs1 from zone other-zone user@host# set static rule-set rs1 rule r1 match destination-address 123.0.0.1/32 user@host# set static rule-set rs1 rule r1 then static-nat prefix 10.0.0.1/32 user@host# set proxy-arp interface ge-0/0/0.0 address 123.0.0.1/32
启用 GTP 配置文件。
[edit security gprs gtp] user@host# set profile gtp1 user@host# set profile gtp1 timeout 1 user@host# set profile gtp1 seq-number-validated
检查 GTP 流量。
[edit security policies] user@host# set from-zone zone1 to-zone other-zone policy out-gtp match source-address gsn1 user@host# set from-zone zone1 to-zone other-zone policy out-gtp match destination-address other-gsn user@host# set from-zone zone1 to-zone other-zone policy out-gtp match application junos-gprs-gtp user@host# set from-zone zone1 to-zone other-zone policy out-gtp then permit application-services gprs-gtp-profile gtp1 user@host# set from-zone other-zone to-zone zone1 policy in-gtp match source-address other-gsn user@host# set from-zone other-zone to-zone zone1 policy in-gtp match destination-address gsn1 user@host# set from-zone other-zone to-zone zone1 policy in-gtp match application junos-gprs-gtp user@host# set from-zone other-zone to-zone zone1 policy in-gtp then permit application-services gprs-gtp-profile gtp1
结果
在配置模式下,输入命令以确认 show security 您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show security
gprs {
gtp {
profile gtp1 {
timeout 1;
seq-number-validated;
}
}
}
address-book {
global {
address gsn1 10.0.0.1/8;
address other-gsn 20.0.0.1/8;
}
}
nat {
static {
rule-set rs1 {
from zone other-zone;
rule r1 {
match {
destination-address 123.0.0.1/32;
}
then {
static-nat {
prefix {
10.0.0.1/32;
}
}
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
123.0.0.1/32;
}
}
}
}
policies {
from-zone zone1 to-zone other-zone {
policy out-gtp {
match {
source-address gsn1;
destination-address other-gsn;
application junos-gprs-gtp;
}
then {
permit {
application-services {
gprs-gtp-profile gtp1;
}
}
}
}
}
from-zone other-zone to-zone zone1 {
policy in-gtp {
match {
source-address other-gsn;
destination-address gsn1;
application junos-gprs-gtp;
}
then {
permit {
application-services {
gprs-gtp-profile gtp1;
}
}
}
}
}
}
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone zone1 {
host-inbound-traffic {
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone other-zone {
host-inbound-traffic {
protocols {
all;
}
}
interfaces {
ge-0/0/1.0 {
host-inbound-traffic {
system-services {
all;
}
}
}
}
}
}
完成设备配置后,请从配置模式进入 commit 。
了解网络地址转换-协议转换
网络地址转换协议转换 (NAT-PT) 是一种协议转换机制,可在两个方向上完成:从 IPv4 地址格式到 IPv6 地址格式,反之亦然。NAT-PT 将 IPv6 网络中的地址与 IPv4 网络中的地址绑定,反之亦然,以便为在地址域之间遍历的数据报提供透明路由。
在每个方向上,静态 NAT 都会定义从一个 IP 子网到另一个 IP 子网的一对一映射。映射包括一个方向上的目标 IP 地址转换和相反方向的源 IP 地址转换。
NAT-PT 的主要优势在于,终端设备和网络可以运行 IPv4 地址或 IPv6 地址,流量可以从任意一端启动。
示例:通过通过 SCTP 多宿主在 IPv4 和 IPv6 端点之间配置 NAT-PT 来增强流量工程
此示例说明如何通过在 IPv4 端点和 IPv6 端点之间配置 NAT-PT 来增强流量工程。NAT-PT 是一种协议转换机制,允许通过 IPv4 和 IPv6 数据报与协议无关的转换,在仅 IPv6 节点和仅 IPv4 节点之间进行通信,不需要会话的状态信息。NAT-PT 将 IPv6 网络中的地址与 IPv4 网络中的地址绑定,反之亦然,以便为在地址域之间遍历的数据报提供透明路由。NAT-PT 的主要优势在于,终端设备和网络可以运行 IPv4 地址或 IPv6 地址,流量可以从任意一端启动。
要求
此示例使用以下硬件和软件组件:
-
SRX5400 设备
-
使用两个 IPv6 地址连接到 SRX5400 设备的端点 A
-
使用两个 IPv4 地址连接到 SRX5400 设备的端点 B
概述
在此示例中,在 IPv4 端点和 IPv6 端点之间配置 NAT-PT。端点 A 使用两个 IPv6 地址连接到 SRX5400 设备,端点 B 使用两个 IPv4 地址连接到 SRX5400 设备。
您可以配置 SRX5400 设备,在 IPv4 地址格式和 IPv6 地址格式之间转换 IP 报头和 IP 地址列表(位于 INIT/INT-ACK 消息中)。在各个方向上,静态 NAT 会定义一个从一个 IP 子网到另一个 IP 子网的一对一映射。映射包括一个方向上的目标 IP 地址转换和相反方向的源 IP 地址转换。
图 1 展示了此示例中使用的网络拓扑。
拓扑
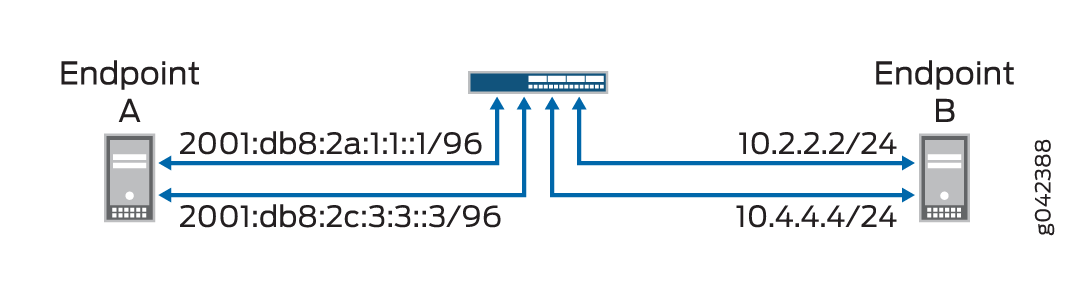 之间的 NAT-PT
之间的 NAT-PT
有关在 IPv4 和 IPv6 端点之间配置 NAT-PT 的详细信息,请参阅表 1。
| 端点 |
地址 1 |
地址 2 |
|---|---|---|
| A (IPv6) |
2001:db8:2a:1:1:1/96 |
2001:db8:2c:3:3:3/96 |
| B (IPv4) |
10.2.2.2/24 |
10.4.4.4/34 |
配置
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层级的 [edit] CLI 中,然后从配置模式进入 commit 。
set interfaces ge-4/0/0 unit 0 family inet address 10.1.1.100/24 set interfaces ge-4/0/0 unit 0 family inet6 address 2001:db8:2a:1:1::100/96 set interfaces ge-4/0/1 unit 0 family inet address 10.2.2.100/24 set interfaces ge-4/0/1 unit 0 family inet6 address 2001:db8:2b:2:2::100/96 set interfaces ge-4/0/2 unit 0 family inet address 10.3.3.100/24 set interfaces ge-4/0/2 unit 0 family inet6 address 2001:db8:2c:3:3::100/96 set interfaces ge-4/0/3 unit 0 family inet address 10.4.4.100/24 set interfaces ge-4/0/3 unit 0 family inet6 address 2001:db8:2d:4:4::100/96 set security zones security-zone sctp_zone1 host-inbound-traffic system-services all set security zones security-zone sctp_zone1 host-inbound-traffic protocols all set security zones security-zone sctp_zone1 interfaces ge-4/0/0.0 set security zones security-zone sctp_zone1 interfaces ge-4/0/2.0 set security zones security-zone sctp_zone2 host-inbound-traffic system-services all set security zones security-zone sctp_zone2 host-inbound-traffic protocols all set security zones security-zone sctp_zone2 interfaces ge-4/0/1.0 set security zones security-zone sctp_zone2 interfaces ge-4/0/3.0 set security nat static rule-set sctp-natpt-from-zone1 from zone sctp_zone1 set security nat static rule-set sctp-natpt-from-zone1 rule r1-dst match destination-address 2001:db8:2b:2:2::2/96 set security nat static rule-set sctp-natpt-from-zone1 rule r1-dst then static-nat prefix 10.2.2.2/32 set security nat static rule-set sctp-natpt-from-zone1 rule r3-dst match destination-address 2001:db8:2d:4:4::4/96 set security nat static rule-set sctp-natpt-from-zone1 rule r3-dst then static-nat prefix 10.4.4.4/32 set security nat static rule-set sctp-natpt-from-zone2 from zone sctp_zone2 set security nat static rule-set sctp-natpt-from-zone2 rule r2-dst match destination-address 10.1.1.1/32 set security nat static rule-set sctp-natpt-from-zone2 rule r2-dst then static-nat prefix 2001:db8:2a:1:1::1/96 set security nat static rule-set sctp-natpt-from-zone2 rule r4-dst match destination-address 10.3.3.3/32 set security nat static rule-set sctp-natpt-from-zone2 rule r4-dst then static-nat prefix 2001:db8:2c:3:3::3/96
程序
逐步过程
要配置 IPv4 端点和 IPv6 端点之间的 NAT-PT:
-
配置接口。
[edit interfaces] user@host# set ge-4/0/0 unit 0 family inet address 10.1.1.100/24 user@host# set ge-4/0/0 unit 0 family inet6 address 2001:db8:2a:1:1::100/96 user@host# set ge-4/0/1 unit 0 family inet address 10.2.2.100/24 user@host# set ge-4/0/1 unit 0 family inet6 address 2001:db8:2b:2:2::100/96 user@host# set ge-4/0/2 unit 0 family inet address 10.3.3.100/24 user@host# set ge-4/0/2 unit 0 family inet6 address 2001:db8:2c:3:3::100/96 user@host# set ge-4/0/3 unit 0 family inet address 10.4.4.100/24 user@host# set ge-4/0/3 unit 0 family inet6 address 2001:db8:2d:4:4::100/96
-
配置区域。
[edit security zones] user@host# set security-zone sctp_zone1 host-inbound-traffic system-services all user@host# set security-zone sctp_zone1 host-inbound-traffic protocols all user@host# set security-zone sctp_zone1 interfaces ge-4/0/0.0 user@host# set security-zone sctp_zone1 interfaces ge-4/0/2.0 user@host# set security-zone sctp_zone2 host-inbound-traffic system-services all user@host# set security-zone sctp_zone2 host-inbound-traffic protocols all user@host# set security-zone sctp_zone2 interfaces ge-4/0/1.0 user@host# set security-zone sctp_zone2 interfaces ge-4/0/3.0
-
为第一个静态 NAT 区域配置规则。
[edit security nat] user@host# set static rule-set sctp-natpt-from-zone1 from zone sctp_zone1
-
指定来自区域 1 的流量的静态 NAT 规则匹配标准。
[edit security nat] user@host# set static rule-set sctp-natpt-from-zone1 rule r1-dst match destination-address 2001:db8:2b:2:2::2/128 user@host# set static rule-set sctp-natpt-from-zone1 rule r1-dst then static-nat prefix 10.2.2.2/32 user@host# set static rule-set sctp-natpt-from-zone1 rule r3-dst match destination-address 2001:db8:2d:4:4::4/128 user@host# set static rule-set sctp-natpt-from-zone1 rule r3-dst then static-nat prefix 10.4.4.4/32
-
为第二个静态 NAT 区域配置规则。
[edit security nat] user@host# set static rule-set sctp-natpt-from-zone2 from zone sctp_zone2
-
指定来自区域 2 的流量的静态 NAT 规则匹配标准。
[edit security nat] user@host# set static rule-set sctp-natpt-from-zone2 rule r2-dst match destination-address 10.1.1.1/32 user@host# set static rule-set sctp-natpt-from-zone2 rule r2-dst then static-nat prefix 2001:db8:2a:1:1::1/128 user@host# set static rule-set sctp-natpt-from-zone2 rule r4-dst match destination-address 10.3.3.3/32 user@host# set static rule-set sctp-natpt-from-zone2 rule r4-dst then static-nat prefix 2001:db8:2a:3:3::3/128
结果
在配置模式下,输入 、 show security zones和show security nat static命令,show interfaces以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show interfaces
ge-4/0/0 {
unit 0 {
family inet {
address 10.1.1.100/24;
}
family inet6 {
address 2001:db8:2a:1:1::100/96;
}
}
}
ge-4/0/1 {
unit 0 {
family inet {
address 10.2.2.100/24;
}
family inet6 {
address 2001:db8:2b:2:2::100/96;
}
}
}
ge-4/0/2 {
unit 0 {
family inet {
address 10.3.3.100/24;
}
family inet6 {
address 2001:db8:2c:3:3::100/96;
}
}
}
ge-4/0/3 {
unit 0 {
family inet {
address 10.4.4.100/24;
}
family inet6 {
address 2001:db8:2d:4:4::100/96;
}
}
}
[edit]
user@host# show security zones
security-zone sctp_zone1 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-4/0/0.0;
ge-4/0/2.0;
}
}
security-zone sctp_zone2 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-4/0/1.0;
ge-4/0/3.0;
}
}
[edit]
user@host# show security nat static
rule-set sctp-natpt-from-zone1 {
from zone sctp_zone1;
rule r1-dst {
match {
destination-address 2001:db8:2b:2:2::2/128;
}
then {
static-nat {
prefix {
10.2.2.2/32;
}
}
}
}
rule r3-dst {
match {
destination-address 2001:db8:2d:4:4::4/128;
}
then {
static-nat {
prefix {
10.4.4.4/32;
}
}
}
}
}
rule-set sctp-natpt-from-zone2 {
from zone sctp_zone2;
rule r2-dst {
match {
destination-address 10.1.1.1/32;
}
then {
static-nat {
prefix {
2001:db8:2a:1:1::1/128;
}
}
}
}
rule r4-dst {
match {
destination-address 10.3.3.3/32;
}
then {
static-nat {
prefix {
2001:db8:2c:3:3::3/128;
}
}
}
}
}
完成设备配置后,请从配置模式进入 commit 。
验证
验证配置
目的
验证 IPv4 端点和 IPv6 端点之间的 NAT-PT 配置是否正确。
行动
在操作模式下,输入 show security zones 和 show security nat static rule all 命令。
user@host> show security zones
Security zone: sctp_zone1
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Interfaces bound: 2
Interfaces:
ge-4/0/0.0
ge-4/0/2.0
Security zone: sctp_zone2
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Interfaces bound: 2
Interfaces:
ge-4/0/1.0
ge-4/0/3.0
user@host> show security nat static rule all
Total static-nat rules: 4
Total referenced IPv4/IPv6 ip-prefixes: 4/4
Static NAT rule: r1-dst Rule-set: sctp-natpt-from-zone1
Rule-Id : 1
Rule position : 1
From zone : sctp_zone1
Destination addresses : 2001:db8:2b:2:2::2
Host addresses : 10.2.2.2
Netmask : 128
Host routing-instance : N/A
Translation hits : 0
Successful sessions : 0
Failed sessions : 0
Number of sessions : 0
Static NAT rule: r3-dst Rule-set: sctp-natpt-from-zone1
Rule-Id : 2
Rule position : 2
From zone : sctp_zone1
Destination addresses : 2001:db8:2d:4:4::4
Host addresses : 10.4.4.4
Netmask : 128
Host routing-instance : N/A
Translation hits : 0
Successful sessions : 0
Failed sessions : 0
Number of sessions : 0
Static NAT rule: r2-dst Rule-set: sctp-natpt-from-zone2
Rule-Id : 3
Rule position : 3
From zone : sctp_zone2
Destination addresses : 10.1.1.1
Host addresses : 2001:db8:2a:1:1::1
Netmask : 32
Host routing-instance : N/A
Translation hits : 0
Successful sessions : 0
Failed sessions : 0
Number of sessions : 0
Static NAT rule: r4-dst Rule-set: sctp-natpt-from-zone2
Rule-Id : 4
Rule position : 4
From zone : sctp_zone2
Destination addresses : 10.3.3.3
Host addresses : 2001:db8:2c:3:3::3
Netmask : 32
Host routing-instance : N/A
Translation hits : 0
Successful sessions : 0
Failed sessions : 0
Number of sessions : 0
意义
命令 show security zones 将显示配置的所有区域以及与区域关联的接口。命令 show security nat static rule all 将显示配置的所有静态 NAT 规则。
