配置安全的本地分支机构连接
既然您已经验证了 LAN/WAN 连接,您就可以使用 Junos CLI 部署 VLAN 和相关策略来保护 LAN 和 WAN 连接。
SRX 平台都涉及安全性。这就是他们要做的。在当今时代,保护本地和互联网连接至关重要。我们将向您展示如何配置 SRX 以满足您的安全需求。
配置 VLAN 和安全策略
本地分支机构连接目标
图 1 详细介绍了这些过程中使用的本地分支办事处连接目标。
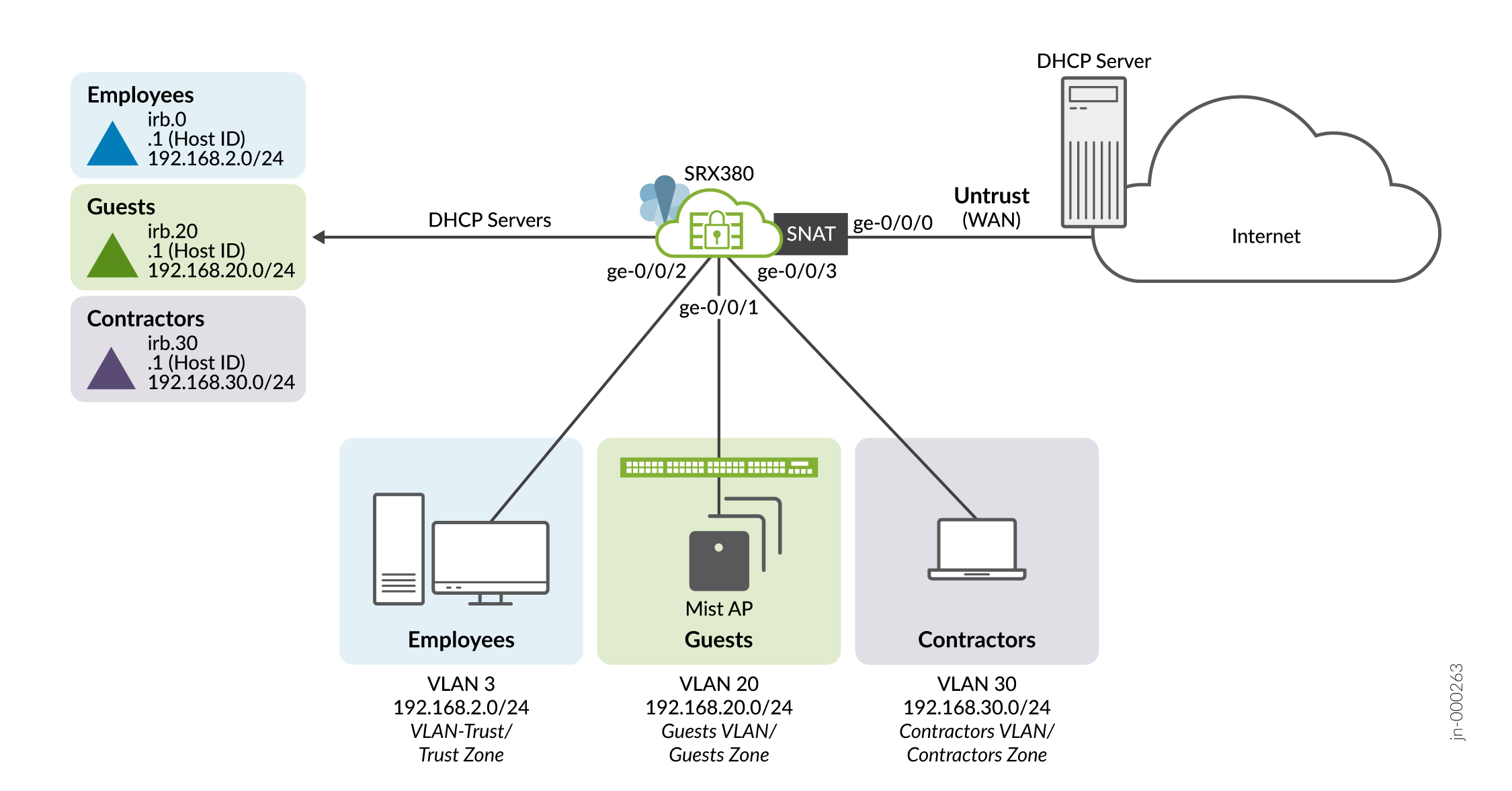
以下是我们将如何实现这些目标:
- 将员工置于信任 VLAN (vlan-trust)/trust 区域。允许他们完全访问互联网,并能够启动与区域内设备的 contractors 特定连接。
- 该分支机构负责处理零售销售,为顾客提供免费的 Wi-Fi 服务。将 guests VLAN 放置在该区域, guests 并允许有限的互联网访问。
- 承包商正在当地分支机构中开发基于 Web 的新业务应用程序。将承包商contractors置于 VLAN/区域,不允许他们接入互联网。承包商无法启动到或guests区域的trust通信。
下表汇总了 VLAN 连接要求:
| VLAN ID | 名称/区域 | 子网 | 互联网接入? | 安全策略 |
|---|---|---|---|---|
| 3 * | vlan-trust/trust * | 192.168.2.0/24 * | 完整 * |
|
| 20 | 客人 | 192.168.20.0/24 | 仅 HTTP 和 HTTPS |
|
| 30 | 承包商 | 192.168.30.0/24 | 不 |
|
标记为“*”的 vlan-trust 表中的条目已通过出厂默认配置到位。我们告诉您这很容易!出厂默认 trust 区段所需的全部是添加安全策略,允许指定的协议从 trust 区域到区域 contractors 。
允许信任承包商区域流量
要实现所述连接目标,请创建安全策略,以允许区域 trust 到 contractors 区域的特定流量(HTTP/HTTPS 和 ping)。作为安全设备,SRX 具有区域间流量的默认 拒绝所有 策略。在出厂默认配置中,仅允许从 trust 区域到 untrust 区域的流量。
set security policies from-zone trust to-zone contractors policy trust-to-contractors match source-address any set security policies from-zone trust to-zone contractors policy trust-to-contractors match destination-address any set security policies from-zone trust to-zone contractors policy trust-to-contractors match application junos-http set security policies from-zone trust to-zone contractors policy trust-to-contractors match application junos-https set security policies from-zone trust to-zone contractors policy trust-to-contractors match application junos-ping set security policies from-zone trust to-zone contractors policy trust-to-contractors then permit
在此示例中,我们将保持简单,并在任何源或目标 IP 地址上保持匹配。在这里,我们只需在源区域和目标区域进行策略控制即可。为了提高安全性,请考虑定义该分支办事处的trustcontractors地址簿条目,即 192.168.2.0/24 和 192.168.30.0/24 个前缀。通过一个地址簿条目,您可以匹配和 source-address trust destination-address contractors。
此外,您还可以添加主机特定地址簿条目,以控制允许在区域之间通信的特定 IP 地址。如果您在策略中使用主机特定 IP 地址,请确保将静态 IP 地址分配给相关主机。如果您还记得,我们在此示例中使用 DHCP。因此,如果租赁时间超过或客户端机器重新启动,客户端机器将自动被分配一个新的 IP 地址,除非您已将静态 IP 地址分配给相关主机。
配置来宾 VLAN、安全区域和安全策略
让我们让这些客人启动并运行。毕竟,他们有网络购物做!在高层次上,这项任务涉及以下关键部分:
- guest定义 VLAN 并将其与一个或多个 LAN 接口相关联
- 定义 VLAN 的集成路由和桥接 (IRB) 接口
- 配置 DHCP 服务器,为 VLAN 成员分配 IP 地址
- 根据 VLAN 的连接需求定义安全区域和策略
- 以 root 身份登录 SRX 设备。您可以使用控制台或 SSH 访问。启动 CLI 并进入配置模式。
login: branch_SRX (ttyu0) root@branch_SRX% cli root@branch_SRX> configure Entering configuration mode [edit] root@branch_SRX#
- guests定义 VLAN 并将其与 IRB 接口相关联。此 IRB 接口用作 VLAN 上设备的默认网关。
[edit] root@branch_SRX# set vlans guests vlan-id 20 root@branch_SRX# set vlans guests l3-interface irb.20
- 将 ge-0/0/1 接口放入 guests VLAN 中。在默认配置中,此接口与大多数接口一 trust 样属于 VLAN。首先要删除接口的当前 VLAN 关联,以便可以将其替换为更新 guests 的 VLAN。
[edit] root@branch_SRX# delete interfaces ge-0/0/1 unit 0 root@branch_SRX# set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members guests
- 为 VLAN 配置 IRB 接口 guests 。此步骤会将 IP 子网分配给 VLAN。在此示例中,您可将 VLAN ID 与 IRB 单元号进行匹配,以便于记忆。此关联仅出于方便。您可以将任何未使用的单元号用于此步骤。
[edit] root@branch_SRX# set interfaces irb unit 20 family inet address 192.168.20.1/24
- 为 guests VLAN 配置 DHCP 服务器。请注意,VLAN 的 IRB 接口配置为 DHCP 服务器接口。此配置从指定范围分配 IP 地址,同时为客户端分配默认路由和公共 DNS 服务器地址。VLAN IRB 的默认路由点,作为所有非本地(VLAN 间和 LAN 到 WAN)流量的下一跳跃。
[edit] root@branch_SRX# set system services dhcp-local-server group GUEST-POOL interface irb.20 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet network 192.168.20.0/24 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet range GUEST-POOL-IP-RANGE low 192.168.20.10 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet range GUEST-POOL-IP-RANGE high 192.168.20.100 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet dhcp-attributes domain-name srx-branch.com root@branch_SRX# set access address-assignment pool GUEST-POOL family inet dhcp-attributes name-server 8.8.8.8 root@branch_SRX# set access address-assignment pool GUEST-POOL family inet dhcp-attributes router 192.168.20.1
- VLAN 成员 guests 可通过互联网访问。由于本地分支机构仅使用本地使用的 RFC-1918 IP 地址,因此互联网访问要求 SRX 对 WAN 接口 IP 地址执行源 NAT。互联网上只能使用全局可路由的 IP 地址。下面介绍如何定义 VLAN 的 guests 源 NAT 策略:
[edit] root@branch_SRX# set security nat source rule-set guests-to-untrust from zone guests root@branch_SRX# set security nat source rule-set guests-to-untrust to zone untrust root@branch_SRX# set security nat source rule-set guests-to-untrust rule guest-nat-rule match source-address 0.0.0.0/0 root@branch_SRX# set security nat source rule-set guests-to-untrust rule guest-nat-rule then source-nat interface
- 几乎完成了。接下来,您将创建 guests 安全区域。作为此流程的一部分,您可将相关 VLAN 的 IRB 放入新区域。区域定义的一部分是指定允许从该区域流向 SRX 设备控制平面的协议和服务。
例如,允许 VLAN 中的 guests 用户启动 DHCP 并将流量 ping 到本地控制平面。这允许访客使用 DHCP 请求 IP 地址,并用于调试其 VLAN 的 IRB,同时将所有其他服务和协议阻止到本地主机。因此,该区域中的 guest 用户无法将 Telnet 或 SSH 启动到分支机构 SRX。相比之下,该区域中的 trust 用户可以启动到 SRX 的 SSH 连接。
[edit] root@branch_SRX# set security zones security-zone guests interfaces irb.20 root@branch_SRX# set security zones security-zone guests host-inbound-traffic system-services dhcp root@branch_SRX# set security zones security-zone guests host-inbound-traffic system-services ping
- 最后一步是定义 VLAN 的安全策略 guests 。为了缩短配置语句,我们将自己“放在”层次结构中
[edit security policies]。为了限制互联网访问,您的策略仅为 HTTP、HTTPS、DNS 和 ping 提供支持。[edit security policies ] root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match source-address any root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match destination-address any root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-http root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-https root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-ping root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust match application junos-dns-udp root@branch_SRX# set from-zone guests to-zone untrust policy guests-to-untrust then permit
快速配置
来宾 VLAN 快速配置
以下是以设置格式定义 guests VLAN 及其安全策略的完整配置。要快速启动并运行,只需根据环境需要编辑配置语句,然后将其粘贴到 SRX 中。
set vlans guests vlan-id 20 set vlans guests l3-interface irb.20 delete interfaces ge-0/0/1 unit 0 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members guests set interfaces irb unit 20 family inet address 192.168.20.1/24 set system services dhcp-local-server group GUEST-POOL interface irb.20 set access address-assignment pool GUEST-POOL family inet network 192.168.20.0/24 set access address-assignment pool GUEST-POOL family inet range GUEST-POOL---IP-RANGE low 192.168.20.10 set access address-assignment pool GUEST-POOL family inet range GUEST-POOL---IP-RANGE high 192.168.20.100 set access address-assignment pool GUEST-POOL family inet dhcp-attributes domain-name srx-branch.com set access address-assignment pool GUEST-POOL family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool GUEST-POOL family inet dhcp-attributes router 192.168.20.1 set security nat source rule-set guests-to-untrust from zone guests set security nat source rule-set guests-to-untrust to zone untrust set security nat source rule-set guests-to-untrust rule guest-nat-rule match source-address 0.0.0.0/0 set security nat source rule-set guests-to-untrust rule guest-nat-rule then source-nat interface set security zones security-zone guests interfaces irb.20 set security zones security-zone guests host-inbound-traffic system-services dhcp set security zones security-zone guests host-inbound-traffic system-services ping set security policies from-zone guests to-zone untrust policy guests-to-untrust match source-address any set security policies from-zone guests to-zone untrust policy guests-to-untrust match destination-address any set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-http set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-https set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-ping set security policies from-zone guests to-zone untrust policy guests-to-untrust match application junos-dns-udp set security policies from-zone guests to-zone untrust policy guests-to-untrust then permit
承包商 VLAN 快速配置
contractors VLAN 和相关安全区域与上述 guests VLAN 详细信息类似。我们通过直接跳入 VLAN 的contractors快速配置来保存一些纸张。
区域缺乏安全策略定义 contractors 是显著的。借助显式策略,默认 拒绝所有 策略将全面适用于从此区域启动的任何区域间流量!结果是,在该区域中 contractors 启动的所有信息流均被阻止进入所有其他区域。
set vlans contractors vlan-id 30 set vlans contractors l3-interface irb.30 delete interfaces ge-0/0/3 unit 0 set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members contractors set interfaces irb unit 30 family inet address 192.168.30.1/24 set system services dhcp-local-server group CONTRACTORS-POOL interface irb.30 set access address-assignment pool CONTRACTORS-POOL family inet network 192.168.30.0/24 set access address-assignment pool CONTRACTORS-POOL family inet range CONTRACTORS-POOL-IP-RANGE low 192.168.30.10 set access address-assignment pool CONTRACTORS-POOL family inet range CONTRACTORS-POOL-IP-RANGE high 192.168.30.100 set access address-assignment pool CONTRACTORS-POOL family inet dhcp-attributes domain-name srx-branch.com set access address-assignment pool CONTRACTORS-POOL family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool CONTRACTORS-POOL family inet dhcp-attributes router 192.168.30.1 set security zones security-zone contractors interfaces irb.30 set security zones security-zone contractors host-inbound-traffic system-services dhcp set security zones security-zone contractors host-inbound-traffic system-services ping
请务必提交配置以激活 SRX 设备上的更改。
结果
安全 VLAN 配置的结果以 Junos 光圈括号格式显示。出于简洁性,我们从下面省略了出厂默认配置。
root@branch_SRX# [edit]
root@branch-srx# show interfaces irb
. . .
unit 20 {
family inet {
address 192.168.20.1/24;
}
}
unit 30 {
family inet {
address 192.168.30.1/24;
}
}
[edit]
root@branch-srx# show vlans
contractors {
vlan-id 30;
l3-interface irb.30;
}
guests {
vlan-id 20;
l3-interface irb.20;
}
. . .
group CONTRACTORS-POOL {
interface irb.30;
}
group GUEST-POOL {
interface irb.20;
}
[edit]
root@branch-srx# show access address-assignment
. . .
pool CONTRACTORS-POOL {
family inet {
network 192.168.30.0/24;
range CONTRACTORS-POOL-IP-RANGE {
low 192.168.30.10;
high 192.168.30.100;
}
dhcp-attributes {
domain-name srx-branch.com;
name-server {
8.8.8.8;
}
router {
192.168.30.1;
}
}
}
}
pool GUEST-POOL {
family inet {
network 192.168.20.0/24;
range GUEST-POOL---IP-RANGE {
low 192.168.20.10;
high 192.168.20.100;
}
dhcp-attributes {
domain-name srx-branch.com;
name-server {
8.8.8.8;
}
router {
192.168.20.1;
}
}
}
}
. . .
nat {
source {
rule-set guests-to-untrust {
from zone guests;
to zone untrust;
rule guest-nat-rule {
match {
source-address 0.0.0.0/0;
}
then {
source-nat {
interface;
}
}
}
}
}
}
policies {
. . .
from-zone guests to-zone untrust {
policy guests-to-untrust {
match {
source-address any;
destination-address any;
application [ junos-http junos-https junos-ping junos-dns-udp ];
}
then {
permit;
}
}
}
}
zones {
. . .
security-zone contractors {
host-inbound-traffic {
system-services {
dhcp;
ping;
}
}
interfaces {
irb.30;
}
}
security-zone guests {
host-inbound-traffic {
system-services {
dhcp;
ping;
}
}
interfaces {
irb.20;
}
}
}
接下来,我们将向您展示如何验证您的配置是否正常工作,以确保本地分支机构通信的安全。
